DIGITAL SWITCHING and TELECOM NETWORKS PEEC5404 7Th Semester, ETC
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-
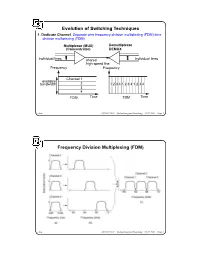
Evolution of Switching Techniques Frequency Division Multiplexing
Evolution of Switching Techniques 1. Dedicate Channel. Separate wire frequency division multiplexing (FDM) time division multiplexing (TDM) Multiplexor (MUX) Demultiplexor (Concentrator) DEMUX individual lines shared individual lines high speed line Frequency Frequency Channel 1 available bandwidth 2 1 2 3 4 1 2 3 4 1 2 3 4 3 4 FDM Time TDM Time chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 1 Frequency Division Multiplexing (FDM) chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 2 Wavelength Division Multiplexing chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 3 Impact of WDM z Many big organizations are starting projects to design WDM system or DWDN (Dense Wave Division Mutiplexing Network). We may see products appear in next three years.In Fujitsu and CCL/Taiwan, 128 different wavelengthes on the same strand of fiber was reported working in the lab. z We may have optical routers between end systems that can take one wavelenght signal, covert to different wavelenght, send it out on different links. Some are designing traditional routers that covert optical signal to electronical signal, and use time slot interchange based on high speed memory to do the switching, the convert the electronic signal back to optical signal. z With this type of optical networks, we will have a virtual circuit network, where each connection is assigned some wave length. Each connection can have 2.4 gbps tremedous bandwidth. z With inital 128 different wavelength, we can have about 10 end users. If each pair of end users needs to communicate simultaneously, it will use 10*10=100 different wavelength. -

National Numbering Plan – a Revised Approach Suggested by TRAI for Achieving Greater Transparency and Efficiency
Telecom Regulatory Authority of India (TRAI) National Numbering Plan – a revised approach suggested by TRAI for achieving greater transparency and efficiency March 2009 Mahanagar Doorsanchar Bhawan Jawahar Lal Nehru Marg New Delhi-110002 Web: www.trai.gov.in Preface Telecommunications sector in the country is undergoing a transformation brought about by rapid growth and technological developments. New paradigms are emerging as telecommunications, IT and broadcasting industries converge. Being conscious of the fact that some of these developments would have a profound impact on the National Numbering Plan, the Authority constituted an internal Research Team to suggest a revised approach to the numbering plan for achieving greater transparency and efficiency. The following issues have been analyzed in the Research Paper in detail: 1. Measures that can be taken for optimal utilization of numbers, short codes and IN SCP Codes 2. Pricing of numbers 3. Long term suitability of numbering plan keeping in view the growth of traditional and development of IP networks 4. Impact of Mobile Number Portability (MNP) and Carrier Selection on the numbering plan 5. Review of SDCA based Numbering Scheme The research paper has been placed on the TRAI's website (www.trai.gov.in). Written comments on the issues raised in the paper may please be furnished th to Principal Advisor (FN), TRAI by 20 March, 2009. The comments may be sent in writing and also preferably be sent in electronic form e-mail: [email protected], [email protected], Tel.: 011-23216930, Fax: -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

SIGNALING in TELECOM NETWORK and SSTP (Date of Creation: 01-04-2011)
E2-E3/CFA/ Signalling in telecomN/W & SSTP Rev date: 01-04-2011 E2-E3 CONSUMER FIXED ACCESS CHAPTER-9 SIGNALING IN TELECOM NETWORK AND SSTP (Date of Creation: 01-04-2011) BSNL, India For Internal Circulation Only Page: 1 E2-E3/CFA/ Signalling in telecomN/W & SSTP Rev date: 01-04-2011 Signaling In Telecom Network And SSTP 1 .0 Introduction Communication networks generally connect two subscriber terminating equipment units together via several line sections and switches for exchange of user information (e.g. speech, data, text or images). The term “signaling” consists of a word signal, which means “indication” about some information. The procedure for transfer of the signal between two nodes or points in telecom network is known as signaling. The signaling is used to transfer control information between the exchanges for call control and for the use of facilities. There are three basic phases in a communication viz setup, conversation and release. Diagram shows a simple telecom network and indicates the component of network and type of signaling used therein. Subscriber Trunk Subscriber Signalling Signalling Signalling EXCH-1 EXCH-2 FIG.1.1 Subscriber Signaling Signaling systems used between the exchange and subscriber equipment, such as terminals and PBX (Private Branch exchanges), are called subscriber signaling systems. Subscriber signaling must not be confused with line signaling. Subscriber signaling can be transported over lines and subscriber trunks. Trunk Signaling Trunk signaling are signals used between public exchanges. They are used to connect exchanges in order to build up a circuit. The signals can be divided in supervision and address signaling. -
Circuit-Switched Coherence
Circuit-Switched Coherence ‡Natalie Enright Jerger, ‡Mikko Lipasti, and ?Li-Shiuan Peh ‡Electrical and Computer Engineering Department, University of Wisconsin-Madison ?Department of Electrical Engineering, Princeton University Abstract—Circuit-switched networks can significantly lower contention, overall system performance can degrade by 20% the communication latency between processor cores, when or more. This latency sensitivity coupled with low link uti- compared to packet-switched networks, since once circuits are set up, communication latency approaches pure intercon- lization motivates our exploration of circuit-switched fabrics nect delay. However, if circuits are not frequently reused, the for CMPs. long set up time and poorer interconnect utilization can hurt Our investigations show that traditional circuit-switched overall performance. To combat this problem, we propose a hybrid router design which intermingles packet-switched networks do not perform well, as circuits are not reused suf- flits with circuit-switched flits. Additionally, we co-design a ficiently to amortize circuit setup delay. This observation prediction-based coherence protocol that leverages the exis- motivates a network with a hybrid router design that sup- tence of circuits to optimize pair-wise sharing between cores. The protocol allows pair-wise sharers to communicate di- ports both circuit and packet switching with very fast circuit rectly with each other via circuits and drives up circuit reuse. reconfiguration (setup/teardown). Our preliminary results Circuit-switched coherence provides overall system perfor- show this leading to up to 8% improvement in overall system mance improvements of up to 17% with an average improve- performance over a packet-switched fabric. ment of 10% and reduces network latency by up to 30%. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

F. Circuit Switching
CSE 3461: Introduction to Computer Networking and Internet Technologies Circuit Switching Presentation F Study: 10.1, 10.2, 8 .1, 8.2 (without SONET/SDH), 8.4 10-02-2012 A Closer Look At Network Structure: • network edge: applications and hosts • network core: —routers —network of networks • access networks, physical media: communication links d. xuan 2 1 The Network Core • mesh of interconnected routers • the fundamental question: how is data transferred through net? —circuit switching: dedicated circuit per call: telephone net —packet-switching: data sent thru net in discrete “chunks” d. xuan 3 Network Layer Functions • transport packet from sending to receiving hosts application transport • network layer protocols in network data link network physical every host, router network data link network data link physical data link three important functions: physical physical network data link • path determination: route physical network data link taken by packets from source physical to dest. Routing algorithms network network data link • switching: move packets from data link physical physical router’s input to appropriate network data link application router output physical transport network data link • call setup: some network physical architectures require router call setup along path before data flows d. xuan 4 2 Network Core: Circuit Switching End-end resources reserved for “call” • link bandwidth, switch capacity • dedicated resources: no sharing • circuit-like (guaranteed) performance • call setup required d. xuan 5 Circuit Switching • Dedicated communication path between two stations • Three phases — Establish (set up connection) — Data Transfer — Disconnect • Must have switching capacity and channel capacity to establish connection • Must have intelligence to work out routing • Inefficient — Channel capacity dedicated for duration of connection — If no data, capacity wasted • Set up (connection) takes time • Once connected, transfer is transparent • Developed for voice traffic (phone) g. -

A Study Paper on Communication Network and Overview of Packet Switching Technology
Council for Innovative Research International Journal of Computers & Technology www.cirworld.com Volume 3 No. 3, Nov-Dec, 2012 A Study Paper on Communication Network and overview of Packet Switching Technology Sandeep panwar Amit garg Naresh kumar Abstract— In this paper,we highlight some of the principal paths between any two points; and second, dividing events that led up to the revolution in communications complete user messages into what he called message blocks among information processing systems. We devote most of then third, delivery of these messages by store and forward this presentation to a brief summary of the communication switching.[12] networks experience, emphasizing the description, Baran's work was similar to the research performed functions, analysis, design and performance measurement independently by Donald Davies at the National Physical of packet-switching networks. We also discuss some recent Laboratory, UK. In 1965, Davies developed the concept of advances in radio packet switching for long-haul. packet-switched networks and proposed development of a .Index Terms— ARPANET, communication networks, UK wide network.. A member of Davies' team met computer networks, networks, packet switching. Lawrence Roberts at the 1967 ACM Symposium on I. INTRODUCTION Operating System Principles, bringing the two groups together.[11] It is widely assumed that, for reasons of efficiency, the various communication networks (Internet, telephone, TV, Interestingly, Davies had chosen some of the same radio, ...) will merge into one ubiquitous, packet switched parameters for his original network design as Baran, such as network that carries all forms of communications. This view a packet size of 1024 bits. In 1966 Davies proposed that a of the future is particularly prevalent among the Internet network should be built at the laboratory to serve the needs community, where it is assumed that packet-switched IP is of NPL and prove the feasibility of packet switching. -

Features of the Internet History the Norwegian Contribution to the Development PAAL SPILLING and YNGVAR LUNDH
Features of the Internet history The Norwegian contribution to the development PAAL SPILLING AND YNGVAR LUNDH This article provides a short historical and personal view on the development of packet-switching, computer communications and Internet technology, from its inception around 1969 until the full- fledged Internet became operational in 1983. In the early 1990s, the internet backbone at that time, the National Science Foundation network – NSFNET, was opened up for commercial purposes. At that time there were already several operators providing commercial services outside the internet. This presentation is based on the authors’ participation during parts of the development and on literature Paal Spilling is studies. This provides a setting in which the Norwegian participation and contribution may be better professor at the understood. Department of informatics, Univ. of Oslo and University 1 Introduction Defense (DOD). It is uncertain when DoD really Graduate Center The concept of computer networking started in the standardized on the entire protocol suite built around at Kjeller early 1960s at the Massachusetts Institute of Technol- TCP/IP, since for several years they also followed the ogy (MIT) with the vision of an “On-line community ISO standards track. of people”. Computers should facilitate communica- tions between people and be a support for human The development of the Internet, as we know it today, decision processes. In 1961 an MIT PhD thesis by went through three phases. The first one was the Leonard Kleinrock introduced some of the earliest research and development phase, sponsored and theoretical results on queuing networks. Around the supervised by ARPA. Research groups that actively same time a series of Rand Corporation papers, contributed to the development process and many mainly authored by Paul Baran, sketched a hypotheti- who explored its potential for resource sharing were cal system for communication while under attack that permitted to connect to and use the network. -

Public Switched Telephone Network (PSTN II/II) Topics Today in PSTN
Public Switched Telephone Network (PSTN II/II) Topics today in PSTN Trunk Network Node 1 Node 2 Access Access Node 3 Terminals Terminals ! A: Switching types ! Connectionless/ connection oriented ! Packet/circuit ! B: PSNT exchanges and interfaces ! interface Q.512 ! using access and trunk networks ! signaling ! network management ! internetworking - Digital Circuit Multiplexing Equipment DCME (G.763) 2 Switching in public networks X.21 Cell switching (fixed - works with cells (packets) having a fixed size : length) offers bounded delay guarantees (QoS compatible, long packets won’t stuck cells) CSPDN: Circuit switched public data net* PSPDN: Packet switched public data net** DQDB: Distributed queue dual bus * Used by European Telecom’s that use X.21 in circuit switched nets 3 **Used by British Telecom’s Packet-switched Service (PSS), Data Pac (Canada) ... Circuit switching - dedicated path Circuit switching - constant delay/bandwidth -voice/data - paid by time - examples: PSTN, GSM? Time switch - Makes switching between time slots - In the figure incoming slot 3 is switched to outgoing slot 3 for one voice direction - Each coming timeslot stored in Speech Store (SS) - Control store (CS) determines the order the slot are read from SS - The info in CS is determined during setup phase of the call Space switch - makes switching between PCM lines - works with electronic gates controlled by CS Cross-pointCross-point controlledcontrolled byby CS CS TDMA 4 Packet switching example Packet structure Seq: sequence number Op code: message/control -

NSL Network Note NN-6 the DECWRL Mail Gateway
F E B R U A R Y 1 9 9 3 NSL Network Note NN-6 The DECWRL Mail Gateway Brian Reid Issued: February, 1993 d i g i t a l Network Systems Laboratory 250 University Avenue Palo Alto, California 94301 USA The Network Systems Laboratory (NSL), begun in August 1989, is a research laboratory devoted to components and tools for building and managing real-world net- works. Current activity is primarily focused on TCP/IP internetworks and issues of heterogeneous networks. NSL also offers training and consulting for other groups within Digital. NSL is also a focal point for operating Digital’s internal IP research network (CRAnet) and the DECWRL gateway. Ongoing experience with practical network operations provides an important basis for research on network management. NSL’s involvement with network operations also provides a test bed for new tools and network components. We publish the results of our work in a variety of journals, conferences, research reports, and notes. We also produce a number of video documents. This document is a Network Note. We use Network Notes to encompass a broad range of technical material. This includes course material, technical guidelines, example configurations, product and market position reviews, etc. Research reports and technical notes may be ordered from us. You may mail your order to: Technical Report Distribution Digital Equipment Corporation Network Systems Laboratory - WRL-1 250 University Avenue Palo Alto, California 94301 USA Reports and notes may also be ordered by electronic mail. Use one of the following addresses: Digital E-net: DECWRL::NSL-TECHREPORTS Internet: [email protected] UUCP: decwrl!nsl-techreports To obtain more details on ordering by electronic mail, send a message to one of these addresses with the word ‘‘help’’ in the Subject line; you will receive detailed instruc- tions. -

National Numbering Plan
NATIONAL NUMBERING PLAN GOVERNMENT OF INDIA DEPARTMENT OF TELECOMMUNICATIONS MINISTRY OF COMMUNICATIONS AND INFORMATION TECHNOLOGY APRIL 2003 INDEX Sl. No. CONTENTS PAGE No. 1 List of Abbreviations 1 2 National Numbering Plan (2003) - Introduction 3 3 National Numbering Scheme 5 4 Annex I: Linked numbering scheme for 13 PSTN 5 Annex II: List of SDCA Codes 18 6 Annex III: List of Spare codes 81 7 Annex IV: Numbers for Special Services 87 (Level 1 Allocation) 8 Annex V: List of codes allotted to Voice Mail 94 Service providers 9 Annex VI: List of codes allotted to ISPs 97 10 Annex VII: List of Codes allotted to Paging 109 Operators 11 Annex VIII: Numbering for Cellular Mobile 111 Network National Numbering Plan (2003) LIST OF ABBREVIATIONS 1 ACC Account Card Calling 2 AN Andaman & Nicobar 3 AP Andhra Pradesh 4 AS Assam 5 BR Bihar 6 BSNL Bharat Sanchar Nigam Limited 7 BSO Basic Service Operator 8 BY Mumbai 9 CAC Carrier Access Code 10 CC Country Code 11 CIC Carrier Identity Code 12 CMTS Cellular Mobile Telephone Service 13 DEL Direct Exchange Line 14 DOT Department of Telecommunications 15 DSPT Digital Satellite Phone Terminal 16 FPH Free Phone 17 GJ Gujrat 18 GMPCS Global Mobile Personal Communication Service 19 HA Haryana 20 HP Himachal Pradesh 21 HVNET High-speed VSAT Network 22 ICIC International Carrier Identification Codes 23 ILD International Long Distance 24 ILDO International Long Distance Operator 25 IN Intelligent Network 26 INET Data Network of BSNL 27 INMARSAT International Maritime Satellite 28 ISDN Integrated Services Digital