Sharebox: Designing a Physical System to Support Resource Exchange in Local Communities
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-
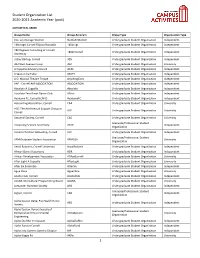
Student Organization List 2020-2021 Academic Year (Past)
Student Organization List 2020-2021 Academic Year (past) ALPHABETICAL ORDER Group Name Group Acronym Group Type Organization Type (not so) Average Women NotSoAvWomen Undergraduate Student Organization Independent 14Strings! Cornell Filipino Rondalla 14Strings Undergraduate Student Organization Independent 180 Degrees Consulting at Cornell 180dcCornell Undergraduate Student Organization Independent University 3 Day Startup, Cornell 3DS Undergraduate Student Organization Independent 302 Wait Avenue Co-op 302 Undergraduate Student Organization University A Cappella Advisory Council ACAC Undergraduate Student Organization Independent A Seat at the Table ASATT Undergraduate Student Organization Independent A.G. Musical Theatre Troupe AnythingGoes Undergraduate Student Organization Independent AAP - Cornell AAP ASSOCIATION ASSOCIATION Undergraduate Student Organization Independent Absolute A Cappella Absolute Undergraduate Student Organization Independent Absolute Zero Break Dance Club AZero Undergraduate Student Organization Independent Academy FC, Cornell (CAFC) AcademyFC Undergraduate Student Organization Independent Accounting Association, Cornell CAA Undergraduate Student Organization University ACE: The Ace/Asexual Support Group at ACE Undergraduate Student Organization University Cornell Actuarial Society, Cornell CAS Undergraduate Student Organization University Graduate/Professional Student Advancing Science And Policy ASAP Independent Organization Advent Christian Fellowship, Cornell ACF Undergraduate Student Organization Independent -

Collaborative Consumption: Sharing Our Way Towards Sustainability?
COLLABORATIVE CONSUMPTION: SHARING OUR WAY TOWARDS SUSTAINABILITY? by SAMUEL COUTURE-BRIÈRE A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS in THE FACULTY OF GRADUATE AND POSTDOCTORAL STUDIES (Political Science) THE UNIVERSITY OF BRITISH COLUMBIA (Vancouver) December 2014 © Samuel Couture-Brière, 2014 ABSTRACT Collaborative consumption (CC) refers to activities surrounding the sharing, swapping, or trading of goods and services within a collaborative consumption community. First, this MA thesis evaluates the factors contributing to the rapid increase of CC initiatives. These factors include technology, personal economics, environmental concerns, and social interaction. Second, the thesis explores the prospects and limits of CC in terms of sustainability. The most promising prospect is that CC seems to generate social capital and initiate a value shift away from ownership. However, institutional forces promoting growth limit this potential. The thesis concludes that CC itself is not enough to achieve sustainability, and therefore, more political solutions are needed. The paper ends with a critical discussion on the future of our growth-based economic model by suggesting that certain forms of CC could represent the roots of a “post- growth” economy. ii PREFACE This thesis is original, unpublished, independent work by the author, S. Couture-Brière. iii TABLE OF CONTENTS ABSTRACT ............................................................................................................................................... -

Employee Wellbeing at Cornell Re
Your guide to resources that support all the dimensions of your wellbeing. HR.CORNELL.EDU/WELLBEING 1 2 1.6.20 Dear Colleague, During your time with Cornell, we want you to be well and THRIVE. Cornell invests in benefits, programs, and services to support employee wellbeing. This guide features a wide range of university (and many community!) resources available to support you in various dimensions of your wellbeing. As you browse this guide, which is organized around Cornell’s Seven Dimensions of Wellbeing model pictured below, you’ll find many resources cross-referenced in multiple dimensions. This illustrates the multifaceted nature of wellbeing. It is often non-linear in nature, and our most important elements shift as our work and Mary Opperman personal lives evolve. CHRO and Vice President Division of Human Resources We experience wellbeing both personally and as members of our various communities, including our work community. We each have opportunities to positively contribute to Cornell’s culture of wellbeing as we celebrate our colleagues’ life events, support one another during difficult times, share resources, and find creative approaches to how, where, and when work gets done. Behind this page is a “quick start directory” of Cornell wellbeing-related contacts. Please save this page and reach out any time you need assistance! Although some of these resources are specific to Cornell’s Ithaca campus, we recognize and are continuing to focus on expanding offerings to our employees in all locations. Thank you for all of your contributions -

'54 Class Notes Names, Topics, Months, Years, Email: Ruth Whatever
Use Ctrl/F (Find) to search for '54 Class Notes names, topics, months, years, Email: Ruth whatever. Scroll up or down to May - Dec. '10 Jan. – Dec. ‘16 Carpenter Bailey: see nearby information. Click Jan. - Dec. ‘11 Jan. - Dec. ‘17 [email protected] the back arrow to return to the Jan. – Dec. ‘12 Jan. - Dec. ‘18 or Bill Waters: class site. Jan. – Dec ‘13 July - Dec. ‘19 [email protected] Jan. – Dec. ‘14 Jan. – Dec. ‘20 Jan. – Dec. ‘15 Jan. – Aug. ‘21 Class website: classof54.alumni.cornell.edu July 2021 – August 2021 Since this is the last hard copy class notes column we will write before CAM goes digital, it is only fitting that we received an e-mail from Dr Bill Webber (WCMC’60) who served as our class’s first correspondent from 1954 to 1959. Among other topics, Webb advised that he was the last survivor of the three “Bronxville Boys” who came to Cornell in 1950 from that village in Westchester County. They roomed together as freshmen, joined Delta Upsilon together and remained close friends through graduation and beyond. They even sat side by side in the 54 Cornellian’s group photo of their fraternity. Boyce Thompson, who died in 2009, worked for Pet Milk in St. Louis for a few years after graduation and later moved to Dallas where he formed and ran a successful food brokerage specializing in gourmet mixed nuts. Ever the comedian, his business phone number (after the area code) was 223-6887, which made the letters BAD-NUTS. Thankfully, his customers did not figure it out. -

Fast Forward Shortlisted for a National Jewish Book Award for Kim Azz Arelli ’93 of Jewish American Women
OWNED AND PUBLISHED BY THE CORNELL ALUMNI ASSOCIATION JANUARY | FEBRUARY 2016 $6.00 F ast Forward Four years on, it’s full speed ahead for Cornell Tech PLUS: Winter in ithaca: embracing the inevitable Change.org’s Jennifer Dulski ’93, MBA ’99 Danger: asteroids! c1-c1 CAM jf16 cover.indd 1 12/18/15 2:36 PM Only on Kiawah Island. THE OCEAN COURSE CASSIQUE AND RIVER COURSE AND BEACH CLUB SANCTUARY HOTEL OCEAN PARK 2012 PGA CHAMPIONSHIP SPORTS PAVILION FRESHFIELDS VILLAGE SASANQUA SPA HISTORIC CHARLESTON Kiawah Island has been named Condé Nast Traveler’s #1 island in the USA (and #2 in the world) for a myriad of reasons – 10 miles of uncrowded beach, iconic golf and resort, the allure of nearby Charleston, KiawahIsland.com | 866.312.1791 | 1 Kiawah Island Parkway | Kiawah Island, South Carolina and a superb private Club and community to name a few. For a recharge, for a holiday, or for a lifetime, KIAWAH’S EXCLUSIVE ONISLAND REAL ESTATE SALES OFFICES SINCE 1976 your discovery of Kiawah Island can be the rst day of the best of your life. homes • homesites • villas • cottages | from about $300,000 to over $20 million Obtain the Property Report required by Federal law and read it before signing anything. No Federal agency has judged the merits or value, if any, of this property. approval of the sale or lease or offer for sale or lease by the Department of State or any offi cer thereof, or that the Department of State has in any way passed upon Void where prohibited by law. -

Read the K–12 Program Profiles
PLUGGING IN PROFILES FROM NYC'S K–12 TECH AND STEAM SKILLS-BUILDING ECOSYSTEM nycfuture.org FEBRUARY 2020 Plugging In: Building NYC's Tech Education and Training Ecosystem 1 K–12 PROGRAM PROFILES Cornell Tech: Teachers in Residence 23 Genspace Biorocket Research Internship 24 Rockaway Waterfront Alliance Environmentor Internship 25 Girls Who Code: Summer Immersion Program 26 P-TECH / CUNY Early College Initiative 27 Code Nation 29 The Knowledge House: Exploring Technology 30 Schools That Can: Maker Fellows Program 31 BEAM (Bridge to Enter Advanced Mathematics) 32 NYC FIRST STEM Centers and Robotics Programs 34 STEM From Dance 35 Sunset Spark 36 City Parks Foundation: Green Girls 37 BioBus: Mobile Lab 38 CAMBA After School 39 ELiTE Education 40 Beam Center 42 American Museum of Natural History – BridgeUp: STEM 43 Genesys Works 44 DIVAS for Social Justice: STEAM for Social Change + STEAM Camp 46 HYPOTHEkids: HK Maker Lab 47 TEALS 48 New York Hall of Science: Science Career Ladder/Explainers 49 New York on Tech: TechFlex Leaders/360 Squad 51 New York Academy of Sciences: Scientist-in-Residence 52 Global Kids: Digital Learning & Leadership 53 Consortium for Research & Robotics (CRR) 54 CodeScty 55 Cooper Union STEM Saturdays 56 iMentor 57 Citizen Schools: Apprenticeships 58 STEM Kids NYC -- In School and After School Programs 60 Rocking the Boat 61 NYU Tandon: Innovative Technology Experiences for Students and Teachers 62 Upperline Code 63 Brooklyn STEAM Center 64 Verizon Innovative Learning Schools 65 22 K–12 Programs Cornell Tech: Teachers in Residence Teachers in Residence is a free professional development program offered by Cornell Tech that trains non-CS teachers in underserved elementary and middle schools in Manhattan, Queens, and the Bronx to integrate CS into their classrooms. -

University Policy 4.3, Sales Activities
CORNELL UNIVERSITY POLICY 4.3 POLICY LIBRARY Volume: 4, Governance/Legal Chapter: 3, Sales Activities On Campus Responsible Executive: Vice President for University Relations Responsible Office: University Sales Activities On Campus Relations Originally Issued: September, 1992 Last Full Review:January 24, 2017 Last Updated: August 6, 2021 POLICY STATEMENT For the convenience of its community, Cornell University allows limited sales to be conducted on its campus in ways that are consistent with the university’s mission, take account of off-campus businesses, and comply with applicable laws and regulations. ◆ Note: Units established to provide materials or specialized services to campus units (i.e., recharge operations, service facilities, and specialized service facilities) must be established in accordance with University Policy 3.10, Recharge Operations and Service Facilities. Please contact University Relations, where such a unit proposes to provide sales or services for personal use or to the general public, or that would be in competition with local commercial providers offering the same goods or services to determine whether this policy also applies to that operation REASON FOR POLICY Cornell regulates the use of its property for sales and other commercial activities in order to maintain a safe, attractive environment for instruction, research, and public service; to facilitate opportunities for its faculty, students, and staff to engage in course-related sales experiences; to encourage activities that support charitable endeavors; to promote off-campus local and regional economies; and to comply with all applicable regulations, including those governing the university’s tax-exempt status. ENTITIES AFFECTED BY THIS POLICY Ithaca-based locations Cornell Tech campus ☐ Weill Cornell Medicine campuses WHO SHOULD READ THIS POLICY ‒ All members of the university community, excluding those at the Weill Cornell Medicine. -

On the Crossroad of Self, Market and Society
On the crossroad of Self, Market, and Society By Mihăilescu Vintilă Mihail Submitted to Central European University Department of Sociology and Social Anthropology In partial fulfillment of the requirements for the degree of Master of Arts Supervisors: Professor Prem Kumar Rajaram Professor Jakob Rigi CEU eTD Collection Budapest, Hungary 2013 On the crossroad of Self, Market, and Society A (n)etnography of Freecycle in Romania By Mihăilescu Vintilă Mihail Submitted to Central European University Department of Sociology and Social Anthropology In partial fulfillment of the requirements for the degree of Master of Arts Supervisors: Professor Prem Kumar Rajaram CEU eTD Collection Professor Jakob Rigi Budapest, Hungary 2013 Abstract Somebody offers twenty books on mathematics. Someone else raises the stakes with a Walkman from the pre-digital era. Maybe you need some cat litter or a couch with signs of usage? Or a small counter or skis or clothes or functional or not so functional computers? A multitude of different objects. Why throw away an object when you can give it away as handout? The Freecycle Network comes with a pertinent response. All these offerings of objects do not take place in a mall or in a market somewhere at the end of town. They all happen in your email inbox. And in the inboxes of the other few thousand members of the Freecycle Network in Bucharest. Freecycle is a simple Yahoo group that makes connections between people who have objects for which they do not have a usage anymore and want to get rid of, and people who have a usage, if not even a need for those objects. -

How to Calibrate Your Adversary's Capabilities? Inverse Filtering for Counter-Autonomous Systems
1 How to Calibrate your Adversary’s Capabilities? Inverse Filtering for Counter-Autonomous Systems Vikram Krishnamurthy, Fellow IEEE and Muralidhar Rangaswamy, Fellow IEEE Manuscript dated July 9, 2019 Abstract—We consider an adversarial Bayesian signal process- wish to estimate the adversary’s sensor’s capabilities and ing problem involving “us” and an “adversary”. The adversary predict its future actions (and therefore guard against these observes our state in noise; updates its posterior distribution of actions). the state and then chooses an action based on this posterior. Given knowledge of “our” state and sequence of adversary’s actions observed in noise, we consider three problems: (i) How can the A. Problem Formulation adversary’s posterior distribution be estimated? Estimating the posterior is an inverse filtering problem involving a random The problem formulation involves two players; we refer to measure - we formulate and solve several versions of this the two players as “us” and “adversary”. With k = 1; 2;::: problem in a Bayesian setting. (ii) How can the adversary’s observation likelihood be estimated? This tells us how accurate denoting discrete time, the model has the following dynamics: the adversary’s sensors are. We compute the maximum likelihood x ∼ P = p(xjx ); x ∼ π estimator for the adversary’s observation likelihood given our k xk−1;x k−1 0 0 measurements of the adversary’s actions where the adversary’s yk ∼ Bx ;y = p(yjxk) k (1) actions are in response to estimating our state. (iii) How can π = T (π ; y ) the state be chosen by us to minimize the covariance of the k k−1 k estimate of the adversary’s observation likelihood? “Our” state ak ∼ Gπk;a = p(ajπk) can be viewed as a probe signal which causes the adversary to act; so choosing the optimal state sequence is an input Let us explain the notation in (1): p(·) denotes a generic design problem. -

International Expansion of Social Enterprises As a Catalyst for Scaling up Social Impact Across Borders
sustainability Article International Expansion of Social Enterprises as a Catalyst for Scaling up Social Impact across Borders Ignacio Bretos * , Millán Díaz-Foncea and Carmen Marcuello Department of Business Organization and Management, Faculty of Economics and Business, University of Zaragoza, Paseo de la Gran Vía 2, 50005 Zaragoza, Spain; [email protected] (M.D.-F.); [email protected] (C.M.) * Correspondence: [email protected] Received: 1 April 2020; Accepted: 15 April 2020; Published: 17 April 2020 Abstract: Scaling social impact and solutions beyond the local context is argued to embody a key mechanism for social enterprises (SEs) to contribute to the achievement of the sustainable development goals (SDGs) and to generate welfare-enhancing systemic change. In light of this, this article explores the potential of SE international expansion as a catalyst for scaling social impact across borders. From our reading of the literature, we discern three major typologies of cross-border scaling: Control-based, altruism-based, and hybrid. Drawing on a multiple-case study of nine international SEs, we examine why and how SEs deploy these scaling strategies on an international scale; the challenges to maximize social impact across borders associated with each of the scaling strategies, and the resources and actions that SEs can mobilize to manage such challenges associated with international expansion. Contrary to conventional wisdom and mainstream theory depicting SEs as small-sized organizations that suffer from different limitations to expand beyond their traditional national boundaries, our findings illustrate how these organizations can successfully operate on an international scale and simultaneously generate financial, social, and environmental value. Keywords: cooperatives; international expansion; organizational growth; scaling; social economy; social enterprise; social entrepreneurship; social impact; sustainable development 1. -

2020 Annual Security Report 2 West Loop Road New York, NY 10044
2020 Annual Security Report 2 West Loop Road New York, NY 10044 Published October 2020 Jeanne Clery Disclosure of Campus Security Policy and Campus Crime Statistics Act Contents Introduction 3 Safety and Security at Cornell Tech 3 Preparation of the Annual Security Report 4 Annual Fire Safety Report 5 Reporting Crime and Requesting Assistance 5 Missing Students 7 Access Control and Building Security 7 Emergency Notifications 8 Campus Safety and Crime Prevention Outreach Programs 9 Alcohol and Drug Use 10 Weapons Prohibition on Campus 11 Sexual Violence 11 Sexual Assault, Domestic Violence, Intimate Partner Violence, and Stalking 11 Seeking Medical Help 14 Reporting the Incident 14 Adjudication of a Complaint under Policy 6.4 15 Procedure for Formal Complaint Against Students 17 Procedure for Formal Complaint Against Employees 18 Privacy and Confidentiality 19 Resources for Victims 20 Prevention and Awareness Education 21 Sexual Offender Notice 23 Reporting Hate Crimes and Bias Incidents 23 Campus Code and Grievance Procedures 24 Office of the Judicial Administrator 24 Sanctions & Remedies Under Campus Code of Conduct 25 Grievance Procedures 26 Related University Policies 26 Crime Statistics 29 2020 Annual Security Report 2 Cornell Tech – 2 West Loop Rd, New York, New York Cornell Tech Introduction Cornell Tech produces pioneering leaders and technologies for the digital age. Cornell Tech brings together like-minded faculty, business leaders, tech entrepreneurs, and students in a catalytic environment to produce visionary ideas grounded in significant needs that will reinvent the way we live. It is also home to the Joan & Irwin Jacobs Technion-Cornell Institute, which embodies the academic partnership between the Technion-Israel Institute of Technology and Cornell University on the New York City campus. -

Reuse Explorations Guide Innovative Programs and Strategies
Reuse Explorations Guide Innovative Programs and Strategies Written by Athena Lee Bradley and Mary Ann Remolador Northeast Recycling Council, Inc. (NERC) With funding from the Rural Utility Services, United States Department of Agriculture NERC is an equal opportunity provider and employer. August 2016 Acknowledgements The Northeast Recycling Council, Inc. (NERC) is a nonprofit organization that conducts projects in the eleven Northeast states, as well as around the country. Its mission is to promote sustainable materials management by supporting traditional and innovative solid waste best practices, focusing on waste prevention, toxics reduction, reuse, recycling and organics recovery. NERC received a grant from the United States Department of Agriculture, Rural Utility Services for “Innovative Strategies & Best Management Practices for Implementing Reuse Programs in Rural Communities in New York State & the St. Regis Mohawk Nation.” Through the project NERC provided webinars, trainings, resources, and technical assistance. The following individuals and organizations provided invaluable and generous assistance in the development and implementation of the project. NERC would like to extend its appreciation to and acknowledge the following people who worked with NERC on reuse: • Jan M. Oatman, Regional Recycling Coordinator, Development Authority of the North Country • St. Lawrence County Reuse Partnership: John Tenbusch, St. Lawrence County Environmental Management Council; Larry Legault, Operations/Recycling Manager, St. Lawrence County Solid Waste Operations; Chelle Lindahl, Co-Coordinator, Local Living Venture; and, Jennifer Lauzon, New York Department of Environmental Conservation, Region 6 • Larry Thompson, Recycling Coordinator, Saint Regis Mohawk Tribe (Akwesasne) • Catherine (Katie) Liendecker & others with Lyons Falls, New York and Lyons Falls Alive • MaryEllen Etienne, The Reuse Institute • Diane Cohen, Executive Director, Finger Lakes ReUse, Inc.