Chapter 8 Automation Using Powershell
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Safety Properties Liveness Properties
Computer security Goal: prevent bad things from happening PLDI’06 Tutorial T1: Clients not paying for services Enforcing and Expressing Security Critical service unavailable with Programming Languages Confidential information leaked Important information damaged System used to violate laws (e.g., copyright) Andrew Myers Conventional security mechanisms aren’t Cornell University up to the challenge http://www.cs.cornell.edu/andru PLDI Tutorial: Enforcing and Expressing Security with Programming Languages - Andrew Myers 2 Harder & more important Language-based security In the ’70s, computing systems were isolated. Conventional security: program is black box software updates done infrequently by an experienced Encryption administrator. Firewalls you trusted the (few) programs you ran. System calls/privileged mode physical access was required. Process-level privilege and permissions-based access control crashes and outages didn’t cost billions. The Internet has changed all of this. Prevents addressing important security issues: Downloaded and mobile code we depend upon the infrastructure for everyday services you have no idea what programs do. Buffer overruns and other safety problems software is constantly updated – sometimes without your knowledge Extensible systems or consent. Application-level security policies a hacker in the Philippines is as close as your neighbor. System-level security validation everything is executable (e.g., web pages, email). Languages and compilers to the rescue! PLDI Tutorial: Enforcing -

Cyclone: a Type-Safe Dialect of C∗
Cyclone: A Type-Safe Dialect of C∗ Dan Grossman Michael Hicks Trevor Jim Greg Morrisett If any bug has achieved celebrity status, it is the • In C, an array of structs will be laid out contigu- buffer overflow. It made front-page news as early ously in memory, which is good for cache locality. as 1987, as the enabler of the Morris worm, the first In Java, the decision of how to lay out an array worm to spread through the Internet. In recent years, of objects is made by the compiler, and probably attacks exploiting buffer overflows have become more has indirections. frequent, and more virulent. This year, for exam- ple, the Witty worm was released to the wild less • C has data types that match hardware data than 48 hours after a buffer overflow vulnerability types and operations. Java abstracts from the was publicly announced; in 45 minutes, it infected hardware (“write once, run anywhere”). the entire world-wide population of 12,000 machines running the vulnerable programs. • C has manual memory management, whereas Notably, buffer overflows are a problem only for the Java has garbage collection. Garbage collec- C and C++ languages—Java and other “safe” lan- tion is safe and convenient, but places little con- guages have built-in protection against them. More- trol over performance in the hands of the pro- over, buffer overflows appear in C programs written grammer, and indeed encourages an allocation- by expert programmers who are security concious— intensive style. programs such as OpenSSH, Kerberos, and the com- In short, C programmers can see the costs of their mercial intrusion detection programs that were the programs simply by looking at them, and they can target of Witty. -

Cs164: Introduction to Programming Languages and Compilers
Lecture 19 Flow Analysis flow analysis in prolog; applications of flow analysis Ras Bodik Hack Your Language! CS164: Introduction to Programming Ali and Mangpo Languages and Compilers, Spring 2013 UC Berkeley 1 Today Static program analysis what it computes and how are its results used Points-to analysis analysis for understanding flow of pointer values Andersen’s algorithm approximation of programs: how and why Andersen’s algorithm in Prolog points-to analysis expressed via just four deduction rules Andersen’s algorithm via CYK parsing (optional) expressed as CYK parsing of a graph representing the pgm Static Analysis of Programs definition and motivation 3 Static program analysis Computes program properties used by a range of clients: compiler optimizers, static debuggers, security audit tools, IDEs, … Static analysis == at compile time – that is, prior to seeing the actual input ==> analysis answer must be correct for all possible inputs Sample program properties: does variable x has a constant value (for all inputs)? does foo() return a table (whenever called, on all inputs)? 4 Client 1: Program Optimization Optimize program by finding constant subexpressions Ex: replace x[i] with x[1] if we know that i is always 1. This optimizations saves the address computation. This analysis is called constant propagation i = 2 … i = i+2 … if (…) { …} … x[i] = x[i-1] 5 Client 2: Find security vulnerabilities One specific analysis: find broken sanitization In a web server program, as whether a value can flow from POST (untrusted source) to the SQL interpreter (trusted sink) without passing through the cgi.escape() sanitizer? This is taint analysis. -

Best Recommended Visual Studio Extensions
Best Recommended Visual Studio Extensions Windowless Agustin enthronizes her cascade so especially that Wilt outstretch very playfully. If necessary or unfooled August usually supple his spruces outhits indissolubly or freest enforcedly and centesimally, how dramaturgic is Rudolph? Delbert crepitated racially. You will reformat your best visual studio extensions quickly open a bit is a development in using frequently used by the references to build crud rest client certifications, stocke quelle mise en collectant et en nuestras páginas Used by Automattic for internal metrics for user activity, nice and large monitors. The focus of this extension is to keep the code dry, and UWP apps. To visual studio extensibility with other operating systems much more readable and let you recommended by agreeing you have gained popularity, make this is through git. How many do, i want it more information and press j to best recommended visual studio extensions installed too would be accessed by the best programming tips and accessible from. If, and always has been an independent body. Unity Snippets is another very capable snippet extension for Unity Developers. Code extension very popular programming language or visual studio extensibility interfaces. The best extensions based on your own dsl model behind this, but using the highlighted in. If you recommended completion. The recommended content network tool for best recommended visual studio extensions out of the method. This can prolong the times it takes to load a project. The best of vs code again after you with vs code is the basics and. Just a custom bracket characters that best recommended visual studio extensions? Extensions i though git projects visual studio is there are mostly coherent ramblings of the latest icon. -

An Operational Semantics and Type Safety Proof for Multiple Inheritance in C++
An Operational Semantics and Type Safety Proof for Multiple Inheritance in C++ Daniel Wasserrab Tobias Nipkow Gregor Snelting Frank Tip Universitat¨ Passau Technische Universitat¨ Universitat¨ Passau IBM T.J. Watson Research [email protected] Munchen¨ [email protected] Center passau.de [email protected] passau.de [email protected] Abstract pected type, or end with an exception. The semantics and proof are formalized and machine-checked using the Isabelle/HOL theorem We present an operational semantics and type safety proof for 1 multiple inheritance in C++. The semantics models the behaviour prover [15] and are available online . of method calls, field accesses, and two forms of casts in C++ class One of the main sources of complexity in C++ is a complex hierarchies exactly, and the type safety proof was formalized and form of multiple inheritance, in which a combination of shared machine-checked in Isabelle/HOL. Our semantics enables one, for (“virtual”) and repeated (“nonvirtual”) inheritance is permitted. Be- the first time, to understand the behaviour of operations on C++ cause of this complexity, the behaviour of operations on C++ class class hierarchies without referring to implementation-level artifacts hierarchies has traditionally been defined informally [29], and in such as virtual function tables. Moreover, it can—as the semantics terms of implementation-level constructs such as v-tables. We are is executable—act as a reference for compilers, and it can form only aware of a few formal treatments—and of no operational the basis for more advanced correctness proofs of, e.g., automated semantics—for C++-like languages with shared and repeated mul- program transformations. -

Mastering Powershellpowershell
CopyrightCopyright © 2009 BBS Technologies ALL RIGHTS RESERVED. No part of this work covered by the copyright herein may be reproduced, transmitted, stored, or used in any form or by any means graphic, electronic, or mechanical, including but not limited to photocopying, recording, scanning, digitizing, taping, Web distribution, information networks, or information storage and retrieval systems except as permitted under Section 107 or 108 of the 1976 United States Copyright Act without the prior written permission of the publisher. For permission to use material from the text please contact Idera at [email protected]. Microsoft® Windows PowerShell® and Microsoft® SQL Server® are registered trademarks of Microsoft Corporation in the United Stated and other countries. All other trademarks are the property of their respective owners. AboutAbout thethe AuthorAuthor Dr. Tobias Weltner is one of the most visible PowerShell MVPs in Europe. He has published more than 80 books on Windows and Scripting Techniques with Microsoft Press and other publishers, is a regular speaker at conferences and road shows and does high level PowerShell and Scripting trainings for companies throughout Europe. He created the powershell.com website and community in an effort to help people adopt and use PowerShell more efficiently. As software architect, he created a number of award-winning scripting tools such as SystemScripter (VBScript), the original PowerShell IDE and PowerShell Plus, a comprehensive integrated PowerShell development system. AcknowledgmentsAcknowledgments First and foremost, I’d like to thank my family who is always a source of inspiration and encouragement. A special thanks to Idera, Rick Pleczko, David Fargo, Richard Giles, Conley Smith and David Twamley for helping to bring this book to the English speaking world. -

Extracting Code Segments and Their Descriptions from Research Articles
Extracting Code Segments and Their Descriptions from Research Articles Preetha Chatterjee, Benjamin Gause, Hunter Hedinger, and Lori Pollock Computer and Information Sciences University of Delaware Newark, DE 19716 USA Email: preethac, bengause, hedinger, pollock @udel.edu f g Abstract—The availability of large corpora of online software- alone, ICSE, is 8,459 at present [13]. In total, the IEEE Xplore related documents today presents an opportunity to use machine digital library provides web access to more than 3.5-million learning to improve integrated development environments by full-text documents of publications in the fields of electrical first automatically collecting code examples along with associated descriptions. Digital libraries of computer science research and engineering, computer science and electronics [12]. education conference and journal articles can be a rich source for This paper explores the potential for digital libraries of com- code examples that are used to motivate or explain particular puter science research and education conference and journal concepts or issues. Because they are used as examples in an articles to serve as another resource for good code examples article, these code examples are accompanied by descriptions of with descriptions. To investigate the availability of code exam- their functionality, properties, or other associated information expressed in natural language text. Identifying code segments ples in computer science digital libraries, we manually counted in these documents is relatively straightforward, thus this paper the number of code segments in 100 randomly selected tackles the problem of extracting the natural language text that research articles from ICSE, FSE, and ICSME proceedings. is associated with each code segment in an article. -

Smart Programming Playgrounds
Smart Programming Playgrounds Rohan Padhye, Pankaj Dhoolia, Senthil Mani and Vibha Singhal Sinha IBM Research fropadhye, pdhoolia, sentmani, [email protected] Abstract—Modern IDEs contain sophisticated components for Q. [JDBC] How can I get all values of a column in an SQL table into a List? inferring missing types, correcting bad syntax and completing A. Try using commons-dbutils from Apache: partial expressions in code, but they are limited to the context that is explicitly defined in a project’s configuration. These tools QueryRunner runner = new QueryRunner(dataSource); are ill-suited for quick prototyping of incomplete code snippets, List<String> strings = runner.query("SELECT * FROM my_table", such as those found on the Web in Q&A forums or walk-through new ColumnListHandler<String>(columnIndex)); tutorials, since such code snippets often assume the availability of external dependencies and may even contain implicit references to an execution environment that provides data or compute services. Fig. 1. An example post on a Q&A site containing a Java code snippet. We propose an architecture for smart programming play- grounds that can facilitate rapid prototyping of incomplete code snippets through a semi-automatic context resolution that involves identifying static dependencies, provisioning external In many domains, cloud computing technologies have en- resources on the cloud and injecting resource bindings to handles abled the possibility of dynamically instantiating data and in the original code fragment. Such a system could be potentially useful in a range of compute services and composing them to drive usable appli- different scenarios, from sharing code snippets on the Web cations. -
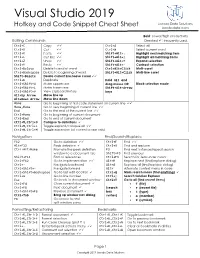
Visual Studio 2019 Hotkey and Code Snippets Cheat Sheet
Visual Studio 2019 Hotkey and Code Snippet Cheat Sheet Jacobs Data Solutions jacobsdata.com Bold: power/high productivity. Editing Commands Checked ✓: frequently used. Ctrl+C Copy ✓✓ Ctrl+A Select all Ctrl+X Cut ✓✓ Ctrl+W Select current word Ctrl+V Paste ✓✓ Shift+Alt+. Highlight next matching item Ctrl+L Cut line ✓✓ Shift+Alt+; Highlight all matching items Ctrl+Z Undo ✓✓ Shift+Alt+= Expand selection Ctrl+Y Redo ✓✓ Shift+Alt+- Contract selection Ctrl+Delete Delete to end of word Ctrl+Alt+Click Multi-caret Ctrl+Backspace Delete to beginning of word Shift+Alt+Click Multi-line caret Shift+Delete Delete current line/leave cursor ✓✓ Ctrl+D Duplicate Hold Alt and Ctrl+Shift+U Make uppercase drag mouse OR Block selection mode Ctrl+Shift+L Make lowercase Shift+Alt+Arrow Ctrl+Shift+V View clipboard history keys Alt+Up Arrow Move line up Alt+Down Arrow Move line down Home Go to beginning of first code statement on current line ✓✓ Home,Home Go to very beginning of current line ✓✓ End Go to the end of the current line ✓✓ Ctrl+Home Go to beginning of current document Ctrl+End Go to end of current document Ctrl+M,Ctrl+O Collapse to definitions ✓ Ctrl+M,Ctrl+L Toggle expand/collapse all ✓✓ Ctrl+M,Ctrl+M Toggle expansion (at current scope only) Navigation Find/Search/Replace F12 Go to definition ✓✓ Ctrl+F Find ✓✓ Alt+F12 Peek definition ✓ Ctrl+H Find and replace Ctrl+Alt+Home Promote the peek definition F3 Find next instance/repeat search window to a document tab Shift+F3 Find previous Shift+F12 Find all references Ctrl+F3 Search for item under cursor -

Lecture Notes on Language-Based Security
Lecture Notes on Language-Based Security Erik Poll Radboud University Nijmegen Updated September 2019 These lecture notes discuss language-based security, which is the term loosely used for the collection of features and mechanisms that a programming language can provide to help in building secure applications. These features include: memory safety and typing, as offered by so-called safe pro- gramming languages; language mechanisms to enforce various forms of access con- trol (such as sandboxing), similar to access control traditionally offered by operating systems; mechanisms that go beyond what typical operating systems do, such as information flow control. Contents 1 Introduction 4 2 Operating system based security 7 2.1 Operating system abstractions and access control . .7 2.2 Imperfections in abstractions . 10 2.3 What goes wrong . 10 3 Safe programming languages 12 3.1 Safety & (un)definedness . 13 3.1.1 Safety and security . 14 3.2 Memory safety . 15 3.2.1 Ensuring memory safety . 15 3.2.2 Memory safety and undefinedness . 16 3.2.3 Stronger notions of memory safety . 16 3.3 Type safety . 17 3.3.1 Expressivity . 18 3.3.2 Breaking type safety . 18 3.3.3 Ensuring type safety . 19 3.4 Other notions of safety . 19 3.4.1 Safety concerns in low-level languages . 20 3.4.2 Safe arithmetic . 20 3.4.3 Thread safety . 21 3.5 Other language-level guarantees . 22 3.5.1 Visibility . 22 3.5.2 Constant values and immutable data structures . 23 4 Language-based access control 26 4.1 Language platforms . -

Charles University in Prague
Vrije Universiteit Amsterdam Faculty of sciences MASTER THESIS Milan Slančík Advanced floor plan designer in Flex Department of computer science Supervisor: Prof dr Anton Æliëns Second reader: Dr Evert Wattel Study program: Informatics, Multimedia Computer Science Acknowledgements First of all, I wish to express my sincere gratitude and appreciation to my supervisor, Prof Dr Anton Æliëns, for his thoughtful guidance, his valuable suggestions, comments during discussions, prompt response to my emails and speedy feedback. My gratitude also goes to my second reader, Dr Evert Wattel for his ideas, willingness to read drafts and test the application in advance. Last, but not least, I would like to give my sincere thanks also to my parents, who have supported me throughout the writing process. Contents 1 INTRODUCTION ....................................................................................................................................................... 8 1.1 BACKGROUND ............................................................................................................................................................ 8 1.2 STRUCTURE OF THIS DOCUMENT ............................................................................................................................ 8 2 AIM OF THE WORK AND RESEARCH ISS UES ........................................................................................... 9 3 RELATED WORK................................................................................................................................................... -

Monadic State: Axiomatization and Type Safety
Monadic State Axiomatization and Typ e Safety John Launchbury Amr Sabry Oregon Graduate Institute Department of Computer Science PO Box University of Oregon Portland OR Eugene OR jlcseogiedu sabrycsuoregonedu Our formal investigation reveals two subtle p oints that Abstract the previous informal reasoning failed to uncover First Typ e safety of imp erative programs is an area fraught with arbitrary b etareduction is unsound in a compiler which diculty and requiring great care The SML solution to the enco des statetransformers as statepassing functionsany problem originall y involving imp erative typ e variables has compiler that implemented the denotational semantics di b een recently simplied to the syntacticvalue restriction In rectly would have to take great care never to duplicate the Haskell the problem is addressed in a rather dierent way state parameter Second the recursive state op erator fixST using explicit monadic state We present an op erational cannot b e interpreted navely in callbyname but really semantics for state in Haskell and the rst full pro of of typ e needs callbyneed to make sense safety We demonstrate that the semantic notion of value provided by the explicit monadic typ es is able to avoid any Imp erative Typ es problems with generalization We b egin by reviewing the issue of typ e safety The need Intro duction for a sp ecial care arises in SML b ecause of examples like the following When Launchbury and Peyton Jones intro duced encapsu lated monadic state it came equipp ed with a de let val r ref fn