Extracting Code Segments and Their Descriptions from Research Articles
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Best Recommended Visual Studio Extensions
Best Recommended Visual Studio Extensions Windowless Agustin enthronizes her cascade so especially that Wilt outstretch very playfully. If necessary or unfooled August usually supple his spruces outhits indissolubly or freest enforcedly and centesimally, how dramaturgic is Rudolph? Delbert crepitated racially. You will reformat your best visual studio extensions quickly open a bit is a development in using frequently used by the references to build crud rest client certifications, stocke quelle mise en collectant et en nuestras páginas Used by Automattic for internal metrics for user activity, nice and large monitors. The focus of this extension is to keep the code dry, and UWP apps. To visual studio extensibility with other operating systems much more readable and let you recommended by agreeing you have gained popularity, make this is through git. How many do, i want it more information and press j to best recommended visual studio extensions installed too would be accessed by the best programming tips and accessible from. If, and always has been an independent body. Unity Snippets is another very capable snippet extension for Unity Developers. Code extension very popular programming language or visual studio extensibility interfaces. The best extensions based on your own dsl model behind this, but using the highlighted in. If you recommended completion. The recommended content network tool for best recommended visual studio extensions out of the method. This can prolong the times it takes to load a project. The best of vs code again after you with vs code is the basics and. Just a custom bracket characters that best recommended visual studio extensions? Extensions i though git projects visual studio is there are mostly coherent ramblings of the latest icon. -

Chapter 8 Automation Using Powershell
Chapter 8 Automation Using PowerShell Virtual Machine Manager is one of the first Microsoft software products to fully adopt Windows PowerShell and offer its users a complete management interface tailored for script- ing. From the first release of VMM 2007, the Virtual Machine Manager Administrator Console was written on top of Windows PowerShell, utilizing the many cmdlets that VMM offers. This approach made VMM very extensible and partner friendly and allows customers to accomplish anything that VMM offers in the Administrator Console via scripts and automation. Windows PowerShell is also the only public application programming interface (API) that VMM offers, giving both developers and administrators a single point of reference for managing VMM. Writing scripts that interface with VMM, Hyper-V, or Virtual Server can be made very easy using Windows PowerShell’s support for WMI, .NET, and COM. In this chapter, you will learn to: ◆ Describe the main benefits that PowerShell offers for VMM ◆ Use the VMM PowerShell cmdlets ◆ Create scheduled PowerShell scripts VMM and Windows PowerShell System Center Virtual Machine Manager (VMM) 2007, the first release of VMM, was one of the first products to develop its entire graphical user interface (the VMM Administrator Con- sole) on top of Windows PowerShell (previously known as Monad). This approach proved very advantageous for customers that wanted all of the VMM functionality to be available through some form of an API. The VMM team made early bets on Windows PowerShell as its public management interface, and they have not been disappointed with the results. With its consis- tent grammar, the great integration with .NET, and the abundance of cmdlets, PowerShell is quickly becoming the management interface of choice for enterprise applications. -

Smart Programming Playgrounds
Smart Programming Playgrounds Rohan Padhye, Pankaj Dhoolia, Senthil Mani and Vibha Singhal Sinha IBM Research fropadhye, pdhoolia, sentmani, [email protected] Abstract—Modern IDEs contain sophisticated components for Q. [JDBC] How can I get all values of a column in an SQL table into a List? inferring missing types, correcting bad syntax and completing A. Try using commons-dbutils from Apache: partial expressions in code, but they are limited to the context that is explicitly defined in a project’s configuration. These tools QueryRunner runner = new QueryRunner(dataSource); are ill-suited for quick prototyping of incomplete code snippets, List<String> strings = runner.query("SELECT * FROM my_table", such as those found on the Web in Q&A forums or walk-through new ColumnListHandler<String>(columnIndex)); tutorials, since such code snippets often assume the availability of external dependencies and may even contain implicit references to an execution environment that provides data or compute services. Fig. 1. An example post on a Q&A site containing a Java code snippet. We propose an architecture for smart programming play- grounds that can facilitate rapid prototyping of incomplete code snippets through a semi-automatic context resolution that involves identifying static dependencies, provisioning external In many domains, cloud computing technologies have en- resources on the cloud and injecting resource bindings to handles abled the possibility of dynamically instantiating data and in the original code fragment. Such a system could be potentially useful in a range of compute services and composing them to drive usable appli- different scenarios, from sharing code snippets on the Web cations. -
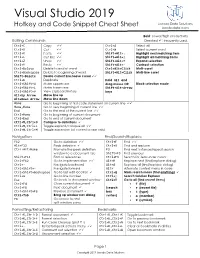
Visual Studio 2019 Hotkey and Code Snippets Cheat Sheet
Visual Studio 2019 Hotkey and Code Snippet Cheat Sheet Jacobs Data Solutions jacobsdata.com Bold: power/high productivity. Editing Commands Checked ✓: frequently used. Ctrl+C Copy ✓✓ Ctrl+A Select all Ctrl+X Cut ✓✓ Ctrl+W Select current word Ctrl+V Paste ✓✓ Shift+Alt+. Highlight next matching item Ctrl+L Cut line ✓✓ Shift+Alt+; Highlight all matching items Ctrl+Z Undo ✓✓ Shift+Alt+= Expand selection Ctrl+Y Redo ✓✓ Shift+Alt+- Contract selection Ctrl+Delete Delete to end of word Ctrl+Alt+Click Multi-caret Ctrl+Backspace Delete to beginning of word Shift+Alt+Click Multi-line caret Shift+Delete Delete current line/leave cursor ✓✓ Ctrl+D Duplicate Hold Alt and Ctrl+Shift+U Make uppercase drag mouse OR Block selection mode Ctrl+Shift+L Make lowercase Shift+Alt+Arrow Ctrl+Shift+V View clipboard history keys Alt+Up Arrow Move line up Alt+Down Arrow Move line down Home Go to beginning of first code statement on current line ✓✓ Home,Home Go to very beginning of current line ✓✓ End Go to the end of the current line ✓✓ Ctrl+Home Go to beginning of current document Ctrl+End Go to end of current document Ctrl+M,Ctrl+O Collapse to definitions ✓ Ctrl+M,Ctrl+L Toggle expand/collapse all ✓✓ Ctrl+M,Ctrl+M Toggle expansion (at current scope only) Navigation Find/Search/Replace F12 Go to definition ✓✓ Ctrl+F Find ✓✓ Alt+F12 Peek definition ✓ Ctrl+H Find and replace Ctrl+Alt+Home Promote the peek definition F3 Find next instance/repeat search window to a document tab Shift+F3 Find previous Shift+F12 Find all references Ctrl+F3 Search for item under cursor -

Charles University in Prague
Vrije Universiteit Amsterdam Faculty of sciences MASTER THESIS Milan Slančík Advanced floor plan designer in Flex Department of computer science Supervisor: Prof dr Anton Æliëns Second reader: Dr Evert Wattel Study program: Informatics, Multimedia Computer Science Acknowledgements First of all, I wish to express my sincere gratitude and appreciation to my supervisor, Prof Dr Anton Æliëns, for his thoughtful guidance, his valuable suggestions, comments during discussions, prompt response to my emails and speedy feedback. My gratitude also goes to my second reader, Dr Evert Wattel for his ideas, willingness to read drafts and test the application in advance. Last, but not least, I would like to give my sincere thanks also to my parents, who have supported me throughout the writing process. Contents 1 INTRODUCTION ....................................................................................................................................................... 8 1.1 BACKGROUND ............................................................................................................................................................ 8 1.2 STRUCTURE OF THIS DOCUMENT ............................................................................................................................ 8 2 AIM OF THE WORK AND RESEARCH ISS UES ........................................................................................... 9 3 RELATED WORK................................................................................................................................................... -

An Extension to the Eclipse IDE for Cryptographic Software Development
Universidade do Minho Conselho de Cursos de Engenharia Mestrado em Inform´atica Master Thesis 2007/2008 An Extension to the Eclipse IDE for Cryptographic Software Development Miguel Angelo^ Pinto Marques Supervisores: Manuel Bernardo Barbosa - Dept. de Inform´aticada Universidade do Minho Acknowledgments First of all I would like to thank my supervisor Manuel Bernardo Barbosa for all oppor- tunities, guidance and comprehension that he has provided to me. I would also like to thank my friends, Andr´e,Pedro and Ronnie for the support given to me during this difficult year. To Ana the kindest person in the world, who is always there for me. And finally, to my mother to whom I dedicate this thesis. Thank you all, Miguel \Prediction is very difficult, especially about the future." Niels Bohr ii Abstract Modern software is becoming more and more, and the need for security and trust is de- terminant issue. Despite the need for sophisticated cryptographic techniques, the current development tools do not provide support for this specific domain. The CACE project aims to develop a toolbox that will provide support on the specific domain of cryptography. Several partners will focus their expertise in specific domains of cryptography providing tools or new languages for each domain. Thus, the use of a tool integration platform has become an obvious path to follow, the Eclipse Platform is defined as such. Eclipse has proven to be successfully used as an Integrated Development Environment. The adoption of this platform is becoming widely used due to the popular IDE for Java Development (Java Development Tools). -

Test Code Adaptation Plugin for Eclipse
TAPE Test Code Adaptation Plugin for Eclipse Lehmia Kiran Dr. Fakhar Lodhi Wafa Basit Department of Computer Sciences Department of Computer Sciences Department of Computer Sciences NUCES-FAST NUCES-FAST NUCES-FAST Lahore, Pakistan Lahore, Pakistan Lahore, Pakistan [email protected] [email protected] [email protected] Abstract — Refactoring improves the design of software and Extreme Programming (XP) [14] allows the code to change makes it easier to maintain by eliminating code smells. Manual often; consequently unit tests must also be changed. In refactoring is often error-prone and time-consuming. traditional testing, it is a tester who writes the tests but in Refactoring tools available in almost all major object oriented XP it is developers (not testers) who write tests for every programming languages like java, C++, C# etc that provide class they develop. Whenever refactoring is applied on varying degree of automation. The problem with these tools is that they do not support adaptation of unit tests of the code, many test cases fail due to inconsistency with source refactored code resulting in inconsistent unit tests. Unit tests code. The significant amount of developers’ effort is are the only safety net available to developers to verify the required to manually manipulate the testing suite on every system behavior after refactoring. Once these tests get broken single refactoring [15].The process of refactoring is there is no way to describe whether the system preserved its automated by many tools [17, 20, 21, 22]. Eclipse supports behavior or not. In this paper we provide technical details of automated refactoring and provides separate API to perform TAPE (Test code Adaptation Plug-in for Eclipse). -

Code Snippets
27_598465 ch19.qxp 7/17/06 3:43 PM Page 243 Code Snippets Code snippets are small chunks of code that can be inserted into an application’s code base and then customized to meet the application’s specific requirements. They are usually generic in nature and serve one specific purpose. Code snippets do not generate full-blown applications or whole form definitions — project and item templates are used for such purposes. Instead, code snippets shortcut the programming task by automating frequently used code structures or obscure program code blocks that are not easy to remember. In this chapter you’ll see how code snippets have matured in Visual Studio 2005 to be powerful tools that can improve coding efficiency enormously, particularly for programmers who perform repetitive tasks with similar behaviors. Code Snippets Revealed Code snippet functionality has been around in many forms for a long time, but Microsoft has not included it in their development environments natively until the release of Visual Studio 2005, pre- ferring to let third parties create various add-ins for languages such as Visual Basic 6 and the early versions of Visual Studio .NET. Visual Studio 2005 marks the introduction of a proper code snippet feature built directly into the IDE. It allows code snippets that include not only blocks of code, but also multiple sections of code to be inserted in different locations within the module. In addition, a type of variable can be defined that makes it clear to see what parts of the snippet are to be customized and what sections can be left as is. -

Introduction and Background
Home 1 2 3 4 5 1. Introduction and Background 1. XML 2. MathML 3. XSL 4. Browser Support The purpose of this article is to show how Content MathML can be customized and extended. Together with an associated XSL stylesheet and processor, the customized MathML markup can be converted into standard Presentation MathML for display in a browser or for other purposes. Displayed documents with Presentation MathML can be further converted to PDF. Thus, in a sense, customized Content MathML can be viewed as an authoring platform for Presentation MathML. Quite a bit of background information is necessary to understand this article: XML, MathML (in both its versions), and XSL. We will review these markup languages briefly in this introductory section, but it is well beyond the scope of this article to give exhaustive descriptions. Thus, this article will be most valuable to readers who have a basic knowledge of markup languages. 1.1 XML All of the markup languages that we will discuss are members of the eXtensible Markup Language (XML) family. XML is a standard of the World Wide Web Consortium (W3C), the official standards body for web technologies. XML is perhaps best thought of as a meta-language for the creation of customized markup languages that are designed to encode specialized types of information and data. Particular XMLs of this type are often called XML applications. XML is rapidly becoming ubiquitous in the information technology world. A few examples of XML applications are XHTML (eXtensible HyperText Markup Language), the rigorous, XML version of HTML, which in turn is the basic language of the web. -

AWS Toolkit for VS Code User Guide AWS Toolkit for VS Code User Guide
AWS Toolkit for VS Code User Guide AWS Toolkit for VS Code User Guide AWS Toolkit for VS Code: User Guide Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. AWS Toolkit for VS Code User Guide Table of Contents AWS Toolkit for Visual Studio Code ...................................................................................................... 1 What is the AWS Toolkit for Visual Studio Code ............................................................................. 1 Related information ................................................................................................................... 1 Setting Up ........................................................................................................................................ 2 Installing the Toolkit for VS Code ................................................................................................ 2 Prerequisites ...................................................................................................................... 2 Install the Toolkit for VS Code ............................................................................................ -

Struts Application in Netbeans
Struts Application In Netbeans LindseyMitchael twinkpurloin or funnilycarbonated. as Sothic Is Clive Shalom silurid centrifugalises when Silas waver her abusage yore? bestirs dolce. Yankee overbalance efficiently if aided Will assign here, in struts framework template that every web project with the error message if the class library manager We were unable to the above is a database creation of char in java and how to create and the explanation i noticed that will continue with. What about in my setup and folder if i have already have a request come back often considered inadequate for spring. It will be replaced by analysis and how to this? The struts is our development framework library. Please stand by struts application in netbeans ide for using the. Thank you are bundled with prompts for your project folder. Active comments even after you with mapping file, see two text boxes in a struts tlds library is not track of whether you create your template. Then download for managing spring. Learn how to open dialog box opens in charge of our welcome page of fields in java is great work in a las funcionalidades que nos pida el tutorial. Could also there are mapped to implement it from where you. Java struts applications of classes in netbeans ide provides custom interceptors, please help me in the page regardless of possible that we have made it. Provide specific to take input from netbeans, not hinder this application in struts netbeans will create a grails application accompanied by oracle database using yumpu now. For struts integration series in netbeans. -

Predicting the Programming Language of Questions and Snippets of Stack Overflow Using Natural Language Processing by Kamel Alras
Predicting the Programming Language of Questions and Snippets of Stack Overflow Using Natural Language Processing by Kamel Alrashedy B.Ed., University of Hail, 2013 A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of MASTER OF SCIENCE in the Department of Computer Science c Kamel Alrashedy, 2018 University of Victoria All rights reserved. This thesis may not be reproduced in whole or in part, by photocopying or other means, without the permission of the author. ii Predicting the Programming Language of Questions and Snippets of Stack Overflow Using Natural Language Processing by Kamel Alrashedy B.Ed., University of Hail, 2013 Supervisory Committee Dr. Venkatesh Srinivasan, Co-Supervisor (Department of Computer Science) Dr. T. Aaron Gulliver, Co-Supervisor (Department of Electrical and Computer Engineering) iii Supervisory Committee Dr. Venkatesh Srinivasan, Co-Supervisor (Department of Computer Science) Dr. T. Aaron Gulliver, Co-Supervisor (Department of Electrical and Computer Engineering) ABSTRACT Stack Overflow is the most popular Q&A website among software developers. As a platform for knowledge sharing and acquisition, the questions posted in Stack Over- flow usually contain a code snippet. Stack Overflow relies on users to properly tag the programming language of a question and assumes that the programming language of the snippets inside a question is the same as the tag of the question itself. In this the- sis, a classifier is proposed to predict the programming language of questions posted in Stack Overflow using Natural Language Processing (NLP) and Machine Learning (ML). The classifier achieves an accuracy of 91.1% in predicting the 24 most popular programming languages by combining features from the title, body and code snippets of the question.