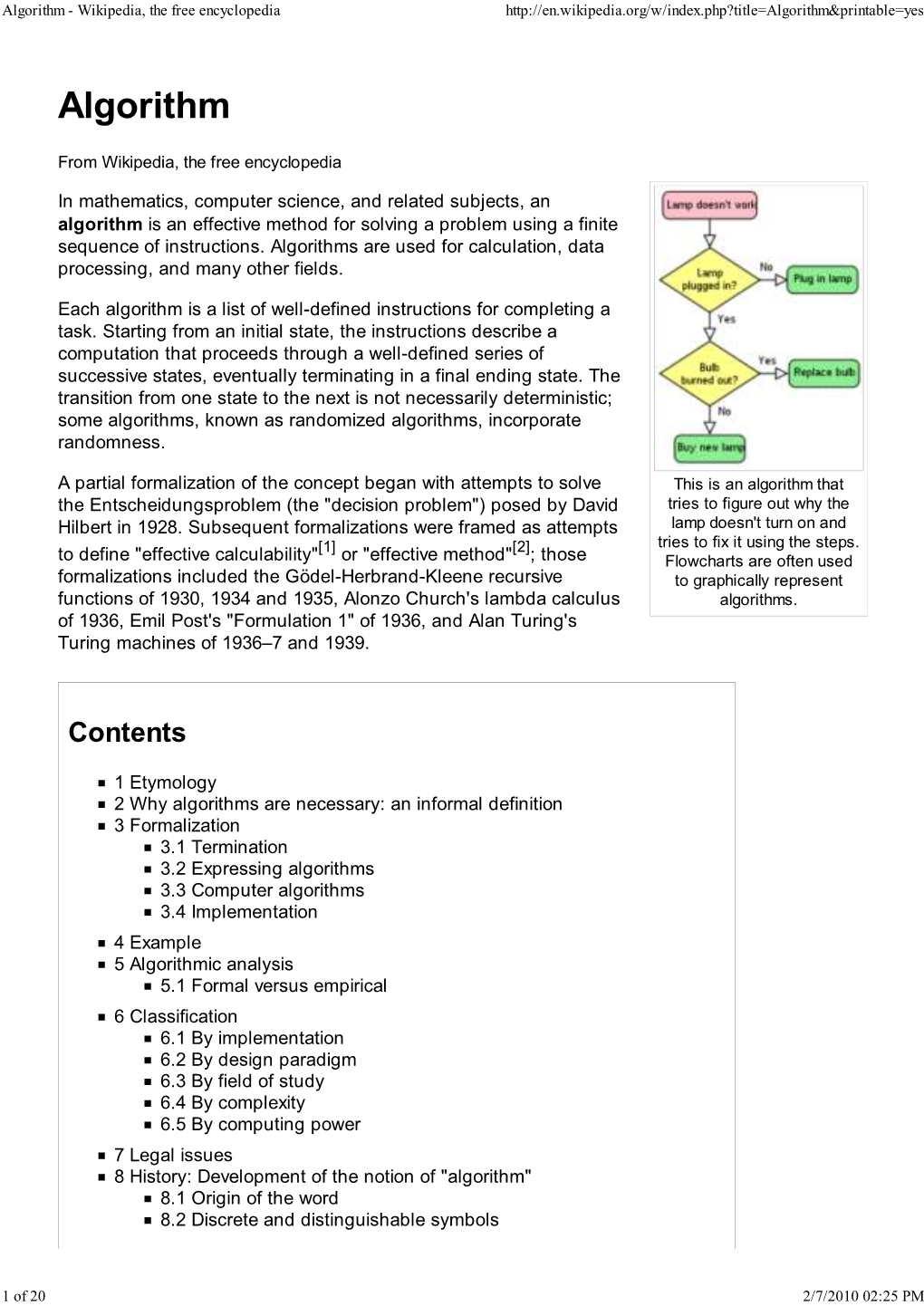
Algorithm - Wikipedia, the Free Encyclopedia
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Finite Element Analysis Of
DEPARTMENT OF MANAGEMENT AND ENGINEERING Mechanical Behaviour of Single-Crystal Nickel-Based Superalloys Master Thesis carried out at Division of Solid Mechanics Linköping University January 2008 Daniel Leidermark LIU-IEI-TEK-A--08/00283--SE Institute of Technology, Dept. of Management and Engineering, SE-581 83 Linköping, Sweden Framläggningsdatum Avdelning, institution Presentation date Division, department 2008-01-28 Publiceringsdatum Division of Solid Mechanics Publication date Dept. of Management and Engineering 2008-02-04 SE-581 83 LINKÖPING Språk Rapporttyp ISBN: Language Report category Svenska/Swedish Licentiatavhandling ISRN: LIU-IEI-TEK-A--08/00283--SE X Engelska/English X Examensarbete C-uppsats Serietitel: D-uppsats Title of series Övrig rapport Serienummer/ISSN: Number of series URL för elektronisk version URL for electronic version http://urn.kb.se/resolve?urn=urn:nbn:se:liu:diva-10722 Titel Mechanical behaviour of single-crystal nickel-based superalloys Title Författare Daniel Leidermark Author Sammanfattning Abstract In this paper the mechanical behaviour, both elastic and plastic, of single-crystal nickel-based superalloys has been investigated. A theoretic base has been established in crystal plasticity, with concern taken to the shearing rate on the slip systems. A model of the mechanical behaviour has been implemented, by using FORTRAN, as a user defined material model in three major FEM-programmes. To evaluate the model a simulated pole figure has been compared to an experimental one. These pole figures match each other very well. Yielding a realistic behaviour of the model. Nyckelord: material model, single-crystal, superalloy, crystal plasticity, LS-DYNA, ABAQUS, ANSYS, Keyword FORTRAN, pole figure V Abstract In this paper the mechanical behaviour, both elastic and plastic, of single- crystal nickel-based superalloys has been investigated. -

Table of Contents
A Comprehensive Introduction to Vista Operating System Table of Contents Chapter 1 - Windows Vista Chapter 2 - Development of Windows Vista Chapter 3 - Features New to Windows Vista Chapter 4 - Technical Features New to Windows Vista Chapter 5 - Security and Safety Features New to Windows Vista Chapter 6 - Windows Vista Editions Chapter 7 - Criticism of Windows Vista Chapter 8 - Windows Vista Networking Technologies Chapter 9 -WT Vista Transformation Pack _____________________ WORLD TECHNOLOGIES _____________________ Abstraction and Closure in Computer Science Table of Contents Chapter 1 - Abstraction (Computer Science) Chapter 2 - Closure (Computer Science) Chapter 3 - Control Flow and Structured Programming Chapter 4 - Abstract Data Type and Object (Computer Science) Chapter 5 - Levels of Abstraction Chapter 6 - Anonymous Function WT _____________________ WORLD TECHNOLOGIES _____________________ Advanced Linux Operating Systems Table of Contents Chapter 1 - Introduction to Linux Chapter 2 - Linux Kernel Chapter 3 - History of Linux Chapter 4 - Linux Adoption Chapter 5 - Linux Distribution Chapter 6 - SCO-Linux Controversies Chapter 7 - GNU/Linux Naming Controversy Chapter 8 -WT Criticism of Desktop Linux _____________________ WORLD TECHNOLOGIES _____________________ Advanced Software Testing Table of Contents Chapter 1 - Software Testing Chapter 2 - Application Programming Interface and Code Coverage Chapter 3 - Fault Injection and Mutation Testing Chapter 4 - Exploratory Testing, Fuzz Testing and Equivalence Partitioning Chapter 5 -

Taming the Complexity Monster Or: How I Learned to Stop Worrying and Love Hard Problems
Taming the Complexity Monster or: How I learned to Stop Worrying and Love Hard Problems Holger H. Hoos Department of Computer Science University of British Columbia Vancouver, BC, Canada [email protected] ABSTRACT Keywords We live in interesting times - as individuals, as members of computational complexity; NP-hardness; empirical algorith- various communities and organisations, and as inhabitants mics; scaling analysis; automated algorithm design; pro- of planet Earth, we face many challenges, ranging from cli- gramming by optimisation (PbO) mate change to resource limitations, from market risks and uncertainties to complex diseases. To some extent, these challenges arise from the complexity of the systems we are dealing with and of the problems that arise from understand- Author Bio ing, modelling and controlling these systems. As computing Holger H. Hoos is a Professor of Computer Science at the scientists and IT professionals, we have much to contribute: University of British Columbia (Canada) and a Faculty As- solving complex problems by means of computer systems, sociate at the Peter Wall Institute for Advanced Studies. software and algorithms is an important part of what our His main research interests span empirical algorithmics, ar- field is about. tificial intelligence, bioinformatics and computer music. He In this talk, I will focus on one particular type of com- is known for his work on the automated design of high- plexity that has been of central interest to the evolutionary performance algorithms and on stochastic local search meth- computation community, to artificial intelligence and far be- ods. Holger is a co-author of the book "Stochastic Local yond, namely computational complexity, and in particular, Search: Foundations and Applications", and his research has NP-hardness. -

Computer-Aided Design of High-Performance Algorithms
University of British Columbia Department of Computer Science Technical Report TR-2008-16 Computer-Aided Design of High-Performance Algorithms Holger H. Hoos University of British Columbia Department of Computer Science 24 December 2008 Abstract High-performance algorithms play an important role in many areas of computer science and are core components of many software systems used in real-world applications. Traditionally, the cre- ation of these algorithms requires considerable expertise and experience, often in combination with a substantial amount of trial and error. Here, we outline a new approach to the process of designing high-performance algorithms that is based on the use of automated procedures for exploring poten- tially very large spaces of candidate designs. We contrast this computer-aided design approach with the traditional approach and discuss why it can be expected to yield better performing, yet simpler algorithms. Finally, we sketch out the high-level design of a software environment that supports our new design approach. Existing work on algorithm portfolios, algorithm selection, algorithm config- uration and parameter tuning, but also on general methods for discrete and continuous optimisation methods fits naturally into our design approach and can be integrated into the proposed software environment. 1 Introduction High-performance algorithms can be found at the heart of many software systems; they often provide the key to effectively solving the computationally difficult problems encountered in the application ar- eas in which these systems are deployed. Examples of such problems include scheduling, time-tabling, resource allocation, production planning and optimisation, computer-aided design and software verifi- cation. Many of these problems are NP-hard and considered computationally intractable, meaning that in general, they cannot be solved by any polynomial-time algorithm. -

THE PASSWORD AUTHENTICATION SECURITY- Draft
THE PASSWORD AUTHENTICATION SECURITY- draft Peter Szabó and Radko ulej and Viera Mislivcová Technical University of Ko²ice, Faculty of Aeronautics, Department of Aerodynamics and Simulations, Rampová 7, 040 21 Ko²ice, Slovak Republic Abstract The simplest way of authentication into information systems is the one of made by name and password. Name is a static aspect, attention is to be paid to password. Reducing safety risk by revealing the password consists in using a sucient number of and safe combination of characters in the password. One of the ways of verifying the suciently safe password is by developing a model for the proces of simulation, through which one can nd out the time maximum time required for the computer to decode the password of a given type and length applying the method of brute force attack. Keywords: information security, authentication, password, brute force, variations with repetitions. 1. Introduction Modern transport companies information systems use in all business processes. In air transport, an example of such a system are computer reservations systems, see [6]. Here it is necessary to authenticate users. Authentication in information systems with a password is a basic way of proving users identity in the system. Brute force is the type of attack whereby the attacker tries to break the password by systematically checking all possible keys. The possible keys can be tested locally or remotely. This process involves systematically checking all possible keys until the correct key is found. In the worst case, this would involve traversing the entire search space. Dierent combinations of passwords can be checked within a very short time. -

Sample Dissertation Format
Towards A Novel Unified Framework for Developing Formal, Network and Validated Agent-Based Simulation Models of Complex Adaptive Systems Muaz Ahmed Khan Niazi Computing Science and Mathematics School of Natural Sciences University of Stirling Scotland UK This thesis has been submitted to the University of Stirling In partial fulfillment for the degree of Doctor of Philosophy 2011 Abstract Literature on the modeling and simulation of complex adaptive systems (cas) has pri- marily advanced vertically in different scientific domains with scientists developing a variety of domain-specific approaches and applications. However, while cas researchers are inherently interested in an interdisciplinary comparison of models, to the best of our knowledge, there is currently no single unified framework for facilitating the development, comparison, communication and validation of models across different scientific domains. In this thesis, we propose first steps towards such a unified framework using a combination of agent-based and complex network-based modeling approaches and guidelines formulat- ed in the form of a set of four levels of usage, which allow multidisciplinary researchers to adopt a suitable framework level on the basis of available data types, their research study objectives and expected outcomes, thus allowing them to better plan and conduct their re- spective research case studies. Firstly, the complex network modeling level of the proposed framework entails the de- velopment of appropriate complex network models for the case where interaction data of cas components is available, with the aim of detecting emergent patterns in the cas under study. The exploratory agent-based modeling level of the proposed framework allows for the development of proof-of-concept models for the cas system, primarily for purposes of exploring feasibility of further research. -

Using Certification Trails to Achieve Software Fault Tolerance Abstract
-c- The Twenteth International Symposium on Fault-Tolerant Computing (1990) Using Certification Trails to Achieve Software Fault Tolerance Gregory F. Sullivan 1 Gerald M. Masson 3 Dept. of Computer Science, Johns Hopkins Univ., Baltimore, MD 21218 Abstract | technique for software fault tolerance, we will first dis- w cuss a simpler fault tolerant software method. In this We introduce a conceptually novel sad powerful tech- method the specification of a problem is given and an nique to achieve fault tolerance in hardware and soft- [ algorithm to solve it is constructed. This algorithm is ware systems. When used for software fault tolerance, executed on an input and the output is stored. Next, this new technique uses time and software redundancy the same algorithm is executed again on the same in- and can be outlined as follows. In the initial phase, put and the output is compared to the earlier output. a program is run to solve a problem and store the re- If the outputs differ then an error is indicated, oth- suit. In addition, this program leaves behind a trail of erwise the output is accepted a.s correct. This soft- data which we call a certification trail. In the second ware fault tolerance method req,ires additional time, phase, another program is run which solves the origi- so called time redundancy [14, 22]; however, it requires nal problem again. This program, however, has access no additional software. It is particularly valuable for to the certification trail left by the first program. Be- detecting errors caused by transient fault phenomena. cause of the availability of the certification trail, the If such faults cause an error during only one of the ex- second phase can be performed by a less complex pro- ecutions then either the error will be detected or the gram and can execute more quicHy. -

Pitfalls and Best Practices in Algorithm Configuration
Journal of Artificial Intelligence Research 64 (2019) 861-893 Submitted 10/18; published 04/19 Pitfalls and Best Practices in Algorithm Configuration Katharina Eggensperger [email protected] Marius Lindauer [email protected] Frank Hutter [email protected] Institut f¨urInformatik, Albert-Ludwigs-Universit¨atFreiburg, Georges-K¨ohler-Allee 74, 79110 Freiburg, Germany Abstract Good parameter settings are crucial to achieve high performance in many areas of arti- ficial intelligence (AI), such as propositional satisfiability solving, AI planning, scheduling, and machine learning (in particular deep learning). Automated algorithm configuration methods have recently received much attention in the AI community since they replace tedious, irreproducible and error-prone manual parameter tuning and can lead to new state-of-the-art performance. However, practical applications of algorithm configuration are prone to several (often subtle) pitfalls in the experimental design that can render the procedure ineffective. We identify several common issues and propose best practices for avoiding them. As one possibility for automatically handling as many of these as possible, we also propose a tool called GenericWrapper4AC. 1. Introduction To obtain peak performance of an algorithm, it is often necessary to tune its parameters. The AI community has recently developed automated methods for the resulting algorithm configuration (AC) problem to replace tedious, irreproducible and error-prone manual pa- rameter tuning. Some example applications, -

A Case Study in Network Analysis
algorithms Article Guidelines for Experimental Algorithmics: A Case Study in Network Analysis Eugenio Angriman 1,†, Alexander van der Grinten 1,† , Moritz von Looz 1,†, Henning Meyerhenke 1,*,† , Martin Nöllenburg 2,† , Maria Predari 1,† and Charilaos Tzovas 1,† 1 Department of Computer Science, Humboldt-Universität zu Berlin, 10099 Berlin, Germany 2 Algorithms and Complexity Group, Institute of Logic and Computation, TU Wien, 1040 Vienna, Austria * Correspondence: [email protected] † These authors contributed equally to this work. Received: 1 June 2019; Accepted: 19 June 2019; Published: 26 June 2019 Abstract: The field of network science is a highly interdisciplinary area; for the empirical analysis of network data, it draws algorithmic methodologies from several research fields. Hence, research procedures and descriptions of the technical results often differ, sometimes widely. In this paper we focus on methodologies for the experimental part of algorithm engineering for network analysis—an important ingredient for a research area with empirical focus. More precisely, we unify and adapt existing recommendations from different fields and propose universal guidelines—including statistical analyses—for the systematic evaluation of network analysis algorithms. This way, the behavior of newly proposed algorithms can be properly assessed and comparisons to existing solutions become meaningful. Moreover, as the main technical contribution, we provide SimexPal, a highly automated tool to perform and analyze experiments following our guidelines. To illustrate the merits of SimexPal and our guidelines, we apply them in a case study: we design, perform, visualize and evaluate experiments of a recent algorithm for approximating betweenness centrality, an important problem in network analysis. In summary, both our guidelines and SimexPal shall modernize and complement previous efforts in experimental algorithmics; they are not only useful for network analysis, but also in related contexts. -
Plantilla Para Proyectos En C/C++ Del RAL 1 Objetivos 2 Descripción
RAL - Robotics and Automation Laboratory - Prof. M. Torres T. Departamento de Ingenier´ıa Electrica´ Pontificia Universidad Catolica´ de Chile Plantilla para Proyectos en C/C++ del RAL / Estructura y L´ogica del Programa . 1 Objetivos • Proveer una plantilla con la estructura y l´ogica b´asica para la implementaci´on m´as r´apida de algorit- mos en proyectos del ´area de rob´otica, como algoritmos de control, estimaci´on y otros de adquisici´on, procesamiento e interpretaci´on de datos. • Fijar un est´andar m´ınimo para los proyectos del grupo RAL que garantice: – Orden y simplicidad ⇒ claridad. – Modularidad y reusabilidad. – Portabilidad. 2 Descripci´on La estructura general de toda soluci´on de automatizaci´on requiere de tres pasos fundamentales: 1. Sensado: Medir ciertas variables que se desean controlar. 2. Procesamiento: Procesar los datos medidos para extraer informaci´on de inter´es. 3. Decisi´on/Acci´on: Verificar que las variables de inter´es cumplan un cierto objetivo fijado por el usuario, y de lo contrario, tomar acciones que ajusten las variables de inter´es del sistema. Las tres etapas anteriores se repiten una y otra vez durante la operaci´on del sistema. Cabe notar que en estas etapas est´an implicitos dos hechos. Primero, que el programa recoge o recibe datos, luego opera sobre estos y finalmente entrega ciertos resultados. Por otra parte, est´a el hecho de que existe un usuario que de alguna manera interactua con el sistema para fijar tanto objetivos como otros par´ametros deseados de operaci´on. En este sentido, la soluci´on puede descomponerse en tareas o funciones de bajo nivel, aquellas encargadas de interactuar con el hardware, y otras de m´as alto nivel encargadas de la interacci´on entre el usuario y la m´aquina. -

An Empirical Approach to Algorithm Analysis Resulting in Approximations to Big Theta Time Complexity
An Empirical Approach to Algorithm Analysis Resulting in Approximations to Big Theta Time Complexity John Paul Guzman1*, Teresita Limoanco2 College of Computer Studies, De La Salle University-Manila, Manila, Philippines. * Corresponding author. Email: [email protected] Manuscript submitted July 9, 2017; accepted August 29, 2017. doi: 10.17706/jsw.12.12.946-976 Abstract: Literature has shown that apriori or posteriori estimates are used in order to determine efficiency of algorithms. Apriori analysis determines the efficiency following algorithm’s logical structure, while posteriori analysis accomplishes this by using data from experiments. Apriori analysis has two main advantages over posteriori analysis: a.) it does not depend on other factors aside from the algorithm being analyzed; b.) it naturally produces measurements in terms of asymptotic notations. These advantages result in thorough and more generalizable analysis. However, apriori techniques are limited by how powerful the current methods of mathematical analysis are. This paper presents a posteriori method that outputs time complexity measured in Big Theta notation. The developed method uses a series of formulas and heuristics to extract an algorithm’s asymptotic behavior solely from its frequency count measurements. The method was tested on 30 Python programs involving arithmetic operations, iterative statements, and recursive functions to establish its accuracy and correctness in determining time complexity behavior. Results have shown that the developed method outputs precise approximations of time complexity that are expected from manual apriori calculations. Key words: Algorithm analysis, time complexity, asymptotic notations, empirical algorithmics. 1. Introduction Algorithm analysis is used to measure the efficiency of algorithms. It can be used to compare different algorithms, balance trade-offs between memory to time consumption, and identify an optimal choice. -

Signature Redacted ----- Chairman, Epartmental Committee on Graduate Students - - - /\Rr·· ''VE"' ~~~
A Theory of Syntactic Recognition for Natural Language by Mitchell Philip Marcus A.B., Harvard University (1972) Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy at the Massachusetts Institute of Technology February, 1978 Signature of Author Sign~ture redacted Department of Electrical int.ftteeriii.l/ Jind Computer Science, October 13, 1977 Certified by Signature redacted .., --7"--_.,.a;:..<-- ....., -J----7-..-----,.......-----77~~--~7.....,...::;»...,.... __T_h_e_si-s-Su-pe-r-vi-·-so-r Accepted Signature redacted ----- Chairman, epartmental Committee on Graduate Students - - - /\Rr·· ''VE"' ~~~ .. _ • ><~ vr1i ~ / .. '· ( f'AAY ,,, ,,1,) ; - / ' ~~--~ a A Theory of Syntactic Recognition for Natural Language by Mitchell Philip Marcus Submitted to the Department of Electrical Engineering and Computer Science on October 13, 1977 in partial fulfillment of the requirements of the Degree of Doctor of Philosophy. Abstract This dissertation investigates the hypothesis that the syntax of natural language can be parsed by a left-to-right deterministic mechanism without facilities for parallelism or backup. This determinism hypothesis, explored in the context of the grammar of English, is shown to lead to a simple mechanism, a grammar interpreter, having the following properties: -Simple rules of grammar can be written for this interpreter which capture the generalizations behind passives, yes/no questions, and other linguistic phenomena, despite the Intrinsic difficulty of capturing such generalizations in the framework of a processing model for recognition, as opposed to a competence model. -The structure of the grammar interpreter constrains its operation in such a way that, by and large, grammar rules cannot parse sentences which violate either of two constraints on rules of grammar currently proposed by Chomsky.