Bachelor Thesis Bachelor's Programme in IT-Forensics and Information Security
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Infotainment System Guide
2k16_CS6_Misc_Equinox_Terrain_Den_Infotain_23462387B.ai 1 9/8/2015 7:57:22 AM C M Y CM MY CY CMY K Chevrolet/GMC Equinox/Terrain/Terrain Denali Infotainment System (GMNA- Localizing-U.S/Canada-9234774) - 2016 - crc - 6/1/15 Contents Introduction . 2 Radio . 14 Audio Players . 33 OnStar System . 41 Navigation . 42 Voice Recognition . 66 Bluetooth Phone/ Devices . 73 Trademarks and License Agreements . 83 Index . 88 Chevrolet/GMC Equinox/Terrain/Terrain Denali Infotainment System (GMNA- Localizing-U.S/Canada-9234774) - 2016 - crc - 8/7/15 2 Introduction Introduction trademarks and/or service marks of Overview General Motors LLC, its subsidiaries, affiliates, or licensors. Read the following pages to Infotainment become familiar with the For vehicles first sold in Canada, infotainment system features. substitute the name “General Motors of Canada Limited” for Chevrolet Motor Division wherever it { Warning appears in this manual. Taking your eyes off the road for The information in this manual too long or too often while using supplements the owner manual. any infotainment feature can This manual describes features that cause a crash. You or others may or may not be on the vehicle could be injured or killed. Do not because of optional equipment that give extended attention to was not purchased on the vehicle, infotainment tasks while driving. model variants, country Limit your glances at the vehicle specifications, features/applications displays and focus your attention that may not be available in your on driving. Use voice commands The names, logos, emblems, region, or changes subsequent to whenever possible. slogans, vehicle model names, and the printing of this manual. -

Market for Parking Access Services
ITS America The Intelligent Transportation Society of America (ITS America) Connected Vehicle Insights Fourth Generation Wireless Vehicle and Highway Gateways to the Cloud An evaluation of Long Term Evolution (LTE) and other wireless technologies’ impact to the transportation sector Steven H. Bayless Technology Scan Series 2011-2012 0 Connected Vehicle Insights: 4G Wireless: Vehicle and Highway Gateways to the Cloud ITS America INTRODUCTION With Fourth Generation cellular (4G), we will see the complete extension of the internet suite of protocols to the wireless environment. 4G likely represents the end of the traditional siloed telecommunications approach that has been the result of decades of investment in single-application “purpose built” wireless technologies (e.g. radio, TV, land mobile, and cellular) and regulatory practice. Current investment patterns in infrastructure provide a strong indication of what will be available and provided in what quantities, quality, and cost beyond 2015 for both terminal devices and network infrastructure. This paper examines how next generation wide-area cellular such as 4G will be able to support vehicular applications, and how transportation infrastructure may mesh with wireless networks. Specifically, it suggests that automotive electronics engineers will need to be cognizant of how application data is treated by 4G Long Term Evolution (LTE) networks, and how innovations such as self-organizing femto-cells, “traffic shaping” and heterogeneous or “vertical roaming” across different radio access technologies may improve the performance of off-board or “cloud” -based vehicular applications Furthermore, the paper suggests that over the long term, vehicles will serve as wireless gateways that manage and collect data a number of devices or sensors deployed in vehicles and highway infrastructure, utilizing 4G cellular as the last-mile wide-area connection to the cloud. -

2013 Chevrolet Tahoe/Suburban Owner Manual M
Chevrolet Tahoe/Suburban Owner Manual - 2013 - crc2 - 8/14/12 Black plate (1,1) 2013 Chevrolet Tahoe/Suburban Owner Manual M In Brief . 1-1 Storage . 4-1 Trademarks and License Instrument Panel . 1-2 Storage Compartments . 4-1 Agreements . 7-55 Initial Drive Information . 1-4 Additional Storage Features . 4-2 Vehicle Features . 1-20 Roof Rack System . 4-3 Climate Controls . 8-1 Performance and Climate Control Systems . 8-1 Maintenance . 1-26 Instruments and Controls . 5-1 Air Vents . 8-12 Controls . 5-2 Keys, Doors, and Warning Lights, Gauges, and Driving and Operating . 9-1 Windows . 2-1 Indicators . 5-10 Driving Information . 9-2 Keys and Locks . 2-1 Information Displays . 5-26 Starting and Operating . 9-19 Doors . 2-9 Vehicle Messages . 5-34 Engine Exhaust . 9-27 Vehicle Security. 2-12 Vehicle Personalization . 5-44 Automatic Transmission . 9-28 Exterior Mirrors . 2-15 Universal Remote System . 5-52 Drive Systems . 9-33 Interior Mirrors . 2-19 Brakes . 9-40 Windows . 2-20 Lighting . 6-1 Ride Control Systems . 9-42 Roof . 2-22 Exterior Lighting . 6-1 Cruise Control . 9-46 Interior Lighting . 6-7 Object Detection Systems . 9-48 Seats and Restraints . 3-1 Lighting Features . 6-8 Fuel . 9-55 Head Restraints . 3-2 Towing. 9-61 Front Seats . 3-3 Infotainment System . 7-1 Conversions and Add-Ons . 9-78 Rear Seats . 3-9 Introduction . 7-1 Safety Belts . 3-16 Radio . 7-10 Airbag System . 3-26 Audio Players . 7-16 Child Restraints . 3-41 Rear Seat Infotainment . 7-36 Phone . -

Municipal Spec Guide
About This Publication This catalog is not updated during the model year and should not be used for This catalog is not updated during the model year and should not be used for ordering purposes. It is intended as a source of basic information. All illustrations ordering purposes. It is intended as a source of basic information. All illustrations and specifications in this literature are based on the latest product information and specifications in this literature are based on the latest product information available at the time of publication. General Motors reserves the right to make available at the time of publication. General Motors reserves the right to make changes at any time without notice. For further details, consult your local dealer. changes at any time without notice. For further details, consult your local dealer. Care must be taken during customer installation of equipment and wiring to ensure Care must be taken during customer installation of equipment and wiring to that all holes drilled in the body are corrosion protected, properly sealed and that ensure that all holes drilled in the body are corrosion protected, properly sealed vehicle wiring harnesses, piping or other components have not been displaced and that vehicle wiring harnesses, piping or other components have not been or damaged. Wiring connection or splice changes are to be removed before displaced or damaged. Aftermarket equipment installers must be mindful of the vehicle is returned to civilian use. Aftermarket equipment installers must be applicable Federal Motor Vehicle Safety Standards. This information can be mindful of applicable Federal Motor Vehicle Safety Standards. -

History of Intelligent Transportation Systems Publication Number
HISTORY OF INTELLIGENT TRANSPORTATION SYSTEMS WWW.ITS.DOT.GOV/INDEX.HTM PUBLICATION NUMBER WWW.ITS.DOT.GOV/INDEX.HTM PUBLICATION NUMBER: FHWA-JPO-16-329 U.S. DEPARTMENT OF TRANSPORTATION INTELLIGENT TRANSPORTATION SYSTEMS JOINT PROGRAM OFFICE B U.S. DEPARTMENT OF TRANSPORTATION INTELLIGENT TRANSPORTATION SYSTEMS JOINT PROGRAM OFFICE Produced by Booz Allen Hamilton U.S. Department of Transportation Intelligent Transportation Systems Joint Program Office Notice This document is disseminated under the sponsorship of the Department of Transportation in the interest of information exchange. The United States Government assumes no liability for its contents or use thereof. The U.S. Government is not endorsing any manufacturers, products, or services cited herein and any trade name that may appear in the work has been included only because it is essential to the contents of the work. C U.S. DEPARTMENT OF TRANSPORTATION INTELLIGENT TRANSPORTATION SYSTEMS JOINT PROGRAM OFFICE Technical Report Documentation Page 1. Report No. 2. Government Accession No. 3. Recipient’s Catalog No. FHWA-JPO-16-329 4. Title and Subtitle 5. Report Date History of Intelligent Transportation Systems May 2016 6. Performing Organization Code 7. Author(s) 8. Performing Organization Report No. Ashley Auer, Shelley Feese, and Stephen Lockwood 9. Performing Organization Name And Address 10. Work Unit No. (TRAIS) Booz Allen Hamilton 8283 Greensboro Drive 11. Contract or Grant No. McLean, VA 22102 12. Sponsoring Agency Name and Address 13. Type of Report and Period Covered U.S. Department of Transportation Intelligent Transportation Systems Joint Program Office 1200 New Jersey Ave SE 14. Sponsoring Agency Code Washington, DC 20590 15. -

Onstar Services – User Terms Last Updated: June 1, 2014 These User
OnStar Services – User Terms Last Updated: June 1, 2014 These User Terms are between you and General Motors of Canada Limited and its affiliates ("OnStar" or "we"). They apply to your use of OnStar Services. THESE USER TERMS ARE LEGALLY BINDING. Refer to Section 3 below for definitions of the capitalized terms. Summary of User Terms When you accept the User Terms during our sign-up process or when you access or use the Services, you agree to the following: • You will only use the Services when it is safe to do so, and you will only use them in compliance with the law and these User Terms; • If others use the Services through your user account or vehicle, you will ensure that they only use the Services when it is safe to do so, and in compliance with the law and these User Terms; • We may suspend or discontinue your access to some or all of the Services; • We may access, modify, update, or upgrade the software used to deliver the Services or used by your vehicle operating system, or used in any pre-installed mobile app without additional notice or consent; • You will notify us by pressing the blue OnStar button in your vehicle or by calling us at 1- 888-4-OnStar when o you plan to sell, dispose of or otherwise transfer possession of your vehicle, or o you want to cancel the Services; • We have certain rights to use and share the information or materials you provide us, as defined in these User Terms; • If you access or use any third party products or services, the terms associated with those third party products or services will also apply, and you will not hold OnStar responsible for your access or use; • The Services are provided "as is" and are limited by matters outside our control. -

Working Together to Save Lives for Over 20 Years
WORKING TOGETHER TO SAVE LIVES FOR OVER 20 YEARS INTRODUCING THE ONSTAR GUARDIAN APP A powerful new way to work together In a crash or emergency situation, getting the right help to the right place is essential. Emergency Communications Centers (ECCs) are challenged with determining the location of a 911 emergency call made from a smartphone. The new OnStar Guardian™ app is designed to help. In addition to key OnStar® safety services for crashes, emergencies and vehicle problems, the app uses GPS information that can provide you with a caller’s location — more precise location information than a cellphone tower ping. OnStar Guardian gives Members a little peace of mind in the palm of their hands — and it provides public safety professionals with a powerful location tool. HOW ONSTAR GUARDIAN WORKS The OnStar Guardian app is designed to give Members key OnStar safety services in or out of any vehicle. Wherever they take their smartphone, they have OnStar. MOBILE CRASH RESPONSE The OnStar Guardian app is designed to work with a smartphone’s built-in sensors. It can recognize the distinct shock caused by most vehicle crashes. To prevent false positives, the app uses a unique algorithm that ensures it is measuring a vehicle in motion — a consistent speed threshold for a consistent amount of time. When that pattern is disrupted by a shock, a crash is detected. The way Mobile Crash Response functions depends on the mobile operating system on which it is running. Android™ phones: When a crash is detected, OnStar Guardian automatically connects to OnStar. An Emergency-Certified Advisor can take the call and start communicating with the Member over the phone’s speaker or connected Bluetooth® device Apple® phones: When a crash is detected, OnStar Guardian automatically connects to OnStar. -

Service Bulletin INFORMATION
Bulletin No.: 03-08-46-004W Service Bulletin Date: January, 2020 INFORMATION Subject: Part Restriction and Ordering Process Information for OnStar® Vehicle Communication Interface Modules (VCIM) (GMNA Only) Models: 2020 Buick Enclave 2020 Cadillac CT4, CT5, CT6, XT4, XT5, XT6 2020 Chevrolet Blazer, Bolt EV, Camaro, Colorado, Equinox, Malibu, Silverado 1500, Silverado 2500HD/3500HD, Spark, Traverse 2020 GMC Acadia, Sierra 1500, Sierra 2500HD/3500HD, Terrain Equipped with OnStar® (RPO UE1) and Infotainment System RPO IOR, IOS, IOT or IOU This bulletin has been revised to update the Model Years and Models. Please discard Corporate Bulletin Number 03-08-46-004V. Vehicle Communication Interface The TAC agent will no longer provide a part number back to the dealership when a VCIM is to be ordered. Module (VCIM) Functional Name The replacement VCIM that the dealership will receive Variations may have a different part number than the one currently installed in the vehicle. Depending on the Model Year and Vehicle, the VCIM May be Identified in the Service Information and on 1. If a replacement VCIM is deemed necessary, the TAC agent will no longer order the replacement the Scan Tool by Different Component Functional part. Instead the dealer MUST use the ONE-TIME Names USE authorization number provided by TAC to Review the following list in order to become familiar order a replacement part through an Electronic with the different component functional names: Service Center (ESC). " Vehicle Communication Interface Module (VCIM) The ONE-TIME USE authorization number will be " Communication Interface Module linked to the vehicle identification number (VIN) and CANNOT be used to order a replacement unit " Telematics Communication Interface Control Module for any other VIN. -

2021 Gmc Canyon Contents
CANYON 2021 GMC CANYON CONTENTS INTRODUCTION AT4 DENALI ELEVATION CAPABILITY TRAILERING CARGO BED SAFETY AND TECHNOLOGY CONNECTIVITY FEATURES AND OPTIONS ACCESSORIES 3 LIVE LIKE A PRO Pros know that true adventure is rarely paved. Because beyond the pavement lie millions of miles waiting to be explored, conquered and claimed. And now, the New 2021 Canyon is ready to take you there. It seamlessly combines rugged capability, distinctive design, premium accommodations and the relentless power necessary to keep up with the fiercely adventurous. Experience the midsize pickup built to go beyond—the 2021 GMC Canyon. Canyon AT4 images shown throughout include available accessories. INTRODUCTION AT4 DENALI ELEVATION CAPABILITY TRAILERING CARGO BED SAFETY AND TECHNOLOGY CONNECTIVITY FEATURES AND OPTIONS ACCESSORIES 4 DRIVE LIKE YOU MEAN IT CAPABLE REFINED I 308 HP WITH AVAILABLE 3.6L V6 I DENALI-EXCLUSIVE 5" CHROME ASSIST STEPS I 369 LB-FT OF TORQUE WITH AVAILABLE DURAMAX I DENALI-EXCLUSIVE INTERIOR WITH FRONT HEATED 2.8L I4 TURBO DIESEL AND VENTILATED LEATHER-APPOINTED SEATING I OFF-ROAD SUSPENSION PACKAGE AND I BOSE® PREMIUM AUDIO SYSTEM IS AVAILABLE ADVANCED HILL DESCENT CONTROL ON AT4 I SPRAY-ON BEDLINER WITH DENALI LOGO IS AVAILABLE I ACCESSORY FRONT AND MID SKID PLATES ARE AVAILABLE SMART I 31" GOODYEAR® WRANGLER DURATRAC® TIRES ON AT4 I IN-VEHICLE APPS1 SUCH AS THE WEATHER CHANNEL I AUTOMATIC LOCKING REAR DIFFERENTIAL IS AVAILABLE AND AMAZON ALEXA BUILT-IN2 ARE AVAILABLE I APPLE CARPLAY™3 COMPATIBILITY I ANDROID AUTO™4 COMPATIBILITY I WIRELESS CHARGING5 IS STANDARD ON DENALI AND AVAILABLE ON AT4 The New 2021 Canyon is designed and engineered to achieve demanding tasks and keep pace with you. -

Final Summary Report
ENTERPRISE Transportation Pooled Fund Study TPF-5 (231) Assessment of Telematics Service Provider Data Feeds PROJECT SUMMARY REPORT April 2014 Prepared by April 2014 Acknowledgements This document was prepared for the ENTERPRISE Transportation Pooled Fund TPF-5(231) Program.1 With agencies from North America and Europe, the main purpose of ENTERPRISE is to use the pooled resources of its members, private sector partners and the United States federal government to develop, evaluate and deploy Intelligent Transportation Systems (ITS). Special thanks to OnStar, Ford, Idaho Transportation Department, Idaho Department of Health and Welfare, Oregon Department of Transportation and Castle Rock Consultants for the information they contributed to this report. Photos in this report are used courtesy of Idaho Department of Health and Welfare, OnStar, Ford, Hyundai and State Farm. Project Champion Angie Kremer, Michigan Department of Transportation, was ENTERPRISE Project Champion for this effort. Members of ENTERPRISE Pooled Fund Arizona Department of Transportation Federal Highway Administration Georgia Department of Transportation Idaho Transportation Department Illinois Department of Transportation Iowa Department of Transportation Kansas Department of Transportation Maricopa County, Arizona Michigan Department of Transportation Minnesota Department of Transportation Mississippi Department of Transportation Oklahoma Department of Transportation Ministry of Transportation Ontario Pennsylvania Department of Transportation Dutch Ministry of Transport -
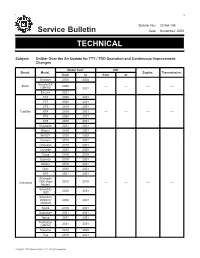
Service Bulletin TECHNICAL
Bulletin No.: 20-NA-196 Service Bulletin Date: November, 2020 TECHNICAL Subject: OnStar Over the Air Update for TTY / TDD Operation and Continuous Improvement Changes Model Year: VIN: Brand: Model: Engine: Transmission: from to from to Enclave 2019 2020 Encore GX Buick 2020 ———— (VIN M) 2021 Encore 2021 CT4 2020 2021 CT5 2020 2021 CT6 2019 2021 Cadillac XT4 2019 2021 ———— XT5 2020 2021 XT6 2020 2021 Escalade 2021 2021 Blazer 2019 2021 Bolt EV 2020 2020 Camaro 2019 2021 Colorado 2019 2021 Corvette 2020 2020 Cruze 2019 2019 Equinox 2019 2021 Malibu 2019 2021 Onix 2020 2021 S10 2021 2021 Silverado Chevrolet 1500 (New 2019 2019 Model) ———— Silverado 2020 2021 1500 Silverado 2500HD/ 2020 2021 3500HD Spark 2019 2021 Suburban 2021 2021 Tahoe 2021 2021 Trailblazer 2021 2021 (VIN M) Traverse 2019 2020 Trax 2019 2021 Copyright 2020 General Motors LLC. All Rights Reserved. Page 2 November, 2020 Bulletin No.: 20-NA-196 Model Year: VIN: Brand: Model: Engine: Transmission: from to from to Acadia 2020 2020 Canyon 2019 2021 Sierra 1500 2019 2019 (New Model) Sierra 1500 2020 2021 GMC ———— Sierra 2500HD/ 2020 2021 3500HD Terrain 2019 2021 Yukon 2021 2021 North America, Middle East, Argentina, Brazil, Bolivia, Chile, Colombia, Ecuador, Peru, Involved Region or Country Uruguay Equipped with OnStar® (UE1), or Mobile Internet Connectivity (VV4) and without Additional Options (RPOs) Deactivated Vehicle Communication System (UDA) Some customers may inquire about continued OnStar functionality after the 3G network is sunset. Some OnStar modules and services rely on the 3G network for functionality. This includes some TTY/TDD functionalities in certain vehicles. -

Interworking of DSRC and Cellular Network Technologies for V2X Communications: a Survey
Interworking of DSRC and Cellular Network Technologies for V2X Communications: A Survey Khadige Abboud, Hassan Aboubakr Omar, and Weihua Zhuang, Fellow, IEEE Abstract—Vehicle-to-anything (V2X) communications refer to caused highway users in the U.S. to spend extra unnecessary information exchange between a vehicle and various elements of 6.9 billion hours on roads to consume additional 3.1 billion the intelligent transportation system, including other vehicles, gallons of fuel, adding up to an annual economical loss of pedestrians, Internet gateways, and transport infrastructure (such as traffic lights and signs). The technology has a great $160 billion [2]. The statistical highway data from 1982 to potential of enabling a variety of novel applications for road 2014 show that these problems will continue to increase safety, passenger infotainment, car manufacturer services, and unless drastic new policy and technological measures are vehicle traffic optimization. Today, V2X communications is based taken [2]. To address these problems, there have been world- on one of two main technologies: dedicated short range com- wide efforts from auto companies, academic institutions, and munications (DSRC) and cellular networks. However, in the near future, it is not expected that a single technology can government agencies to provide the vehicles and the transport support such a variety of expected V2X applications for a large infrastructure with communication capabilities, thus enabling number of vehicles. Hence, interworking between DSRC and vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), and cellular network technologies for efficient V2X communications vehicle-to-pedestrian communications, which are collectively is proposed. This paper surveys potential DSRC and cellular referred to as vehicle-to-x (V2X) communications, as recently interworking solutions for efficient V2X communications.