Remote Desktop Set Up
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

SUSE Linux Enterprise Desktop 15 SP2 Administration Guide Administration Guide SUSE Linux Enterprise Desktop 15 SP2
SUSE Linux Enterprise Desktop 15 SP2 Administration Guide Administration Guide SUSE Linux Enterprise Desktop 15 SP2 Covers system administration tasks like maintaining, monitoring and customizing an initially installed system. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xviii 1 Available Documentation xix 2 Giving Feedback xx 3 Documentation Conventions xxi 4 Product Life Cycle and Support xxii Support Statement for SUSE Linux Enterprise Desktop xxiii • Technology Previews xxiv I COMMON TASKS 1 1 Bash and Bash -
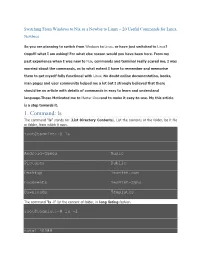
1. Command: Ls the Command “Ls” Stands for (List Directory Contents), List the Contents of the Folder, Be It File Or Folder, from Which It Runs
Switching From Windows to Nix or a Newbie to Linux – 20 Useful Commands for Linux Newbies So you are planning to switch from Windows to Linux, or have just switched to Linux? Oops!!! what I am asking! For what else reason would you have been here. From my past experience when I was new to Nux, commands and terminal really scared me, I was worried about the commands, as to what extent I have to remember and memorise them to get myself fully functional with Linux. No doubt online documentation, books, man pages and user community helped me a lot but I strongly believed that there should be an article with details of commands in easy to learn and understand language.These Motivated me to Master Linuxand to make it easy-to-use. My this article is a step towards it. 1. Command: ls The command “ls” stands for (List Directory Contents), List the contents of the folder, be it file or folder, from which it runs. root@tecmint:~# ls Android-Games Music Pictures Public Desktop Tecmint.com Documents TecMint-Sync Downloads Templates The command “ls -l” list the content of folder, in long listing fashion. root@tecmint:~# ls -l total 40588 drwxrwxr-x 2 ravisaive ravisaive 4096 May 8 01:06 Android Games drwxr-xr-x 2 ravisaive ravisaive 4096 May 15 10:50 Desktop drwxr-xr-x 2 ravisaive ravisaive 4096 May 16 16:45 Documents drwxr-xr-x 6 ravisaive ravisaive 4096 May 16 14:34 Downloads drwxr-xr-x 2 ravisaive ravisaive 4096 Apr 30 20:50 Music drwxr-xr-x 2 ravisaive ravisaive 4096 May 9 17:54 Pictures drwxrwxr-x 5 ravisaive ravisaive 4096 May 3 18:44 Tecmint.com drwxr-xr-x 2 ravisaive ravisaive 4096 Apr 30 20:50 Templates Command “ls -a“, list the content of folder, including hidden files starting with „.‟. -

Bootable Linux CD / PXE for the Remote Acquisition of Multiple Computers
Bootable Linux CD / PXE for the remote acquisition of multiple computers Dennis Cortjens [email protected] REPORT 5th of July, 2014 Abstract In the field of digital forensics the acquisition of multiple computers in large IT infrastructures have always been a complex and time consuming task. Especially when one doesn't know which computer to investigate and therefore needs to acquire them all. Triage software has increased the efficiency in cases like this. The software gives an indication which computers to acquire, but one still needs to disassemble and acquire storage devices of the specific computers on the crime scene. In this study two concepts of automated remote acquisition of multiple computers are researched and tested on performance. One of the concepts (based on iSCSI) is developed into a proof concept, called the Remote Acquisition Boot Environment (RABE). Although it is not yet feasible for the remote acquisition to succeed the traditional method of acquiring computers, it could make the remote acquisition a time efficient solution in the near future. Acknowledgement I would like to thank the Netherlands Forensic Institute's digital technology team for their hospitality and pleasant and stimulating work environment. I want to extend my gratitude to Zeno Geradts and Ruud Schramp for their trust and support. Contents 1 Introduction 3 1.1 Problem . .3 1.2 Position . .3 1.3 Scope . .3 1.4 Hypothesis . .4 2 Background 4 2.1 Bootable Linux CD . .4 2.2 Preboot eXecution Environment (PXE) . .5 2.3 Network File System (NFS) . .6 2.4 Internet Small Computer System Interface (iSCSI) . -

Xrdp.Log.Pdf
Printed by Stephen Quinney Feb 05, 19 13:46 xrdp.log.txt Page 1/3 * Wednesday 31st January 2018 Stephen has imported the XRDP configuration from SEE. Most of it has been put into lcfg−level headers so that it can be shared. At the top level the service is configured using the dice/options/external−xrdp−server.h header. There is a test service accessible at xrdp.inf.ed.ac.uk which seems to work well. A quick survey of clients for Linux suggests that the best is remmina. Stephen will be talking about the project at the next Development meeting so before then he will collect all his notes on a wiki page for the project. * Wednesday 7th February 2018 Since SEE has already put together a remote desktop solution which works well and is freely available, there seemed little point in trying other possible solutions; so a small test version of SEE’s RDP−based remote desktop service has been set up here in Informatics. It uses HAProxy as a load−balancing front end. In the trial service at xrdp.inf.ed.ac.uk, the front end routes connection requests to the less loaded of the two backend machines, or to an existing session if there is one. The test service will be open to computing staff. It’s envisaged that the full service will use real hardware rather than virtual, and that there will be separate staff and student services. The next work on this project will be to add some Informatics identity to the login screen; to change access controls on the PAM stack for the backend machines, to permit differences between staff and student services; and to document the services on computing.help. -

Os Spotlight: Unmanned Ground Gamestation Turbo Vehicle Interface
Cluster User and File Management • Remote desktop for ODROID U3 Year One Issue #7 Jul 2014 ODROIDMagazine WEATHER ENGINEERING HARDKERNEL’S NEW WEATHER BOARD DEVICE LETS YOU MONITOR WEATHER CONDITIONS WITH YOUR ODROID CONFIGURE YOUR OS SPOTLIGHT: UNMANNED GROUND GAMESTATION TURBO VEHICLE INTERFACE • PORTABLE SOLAR COMPUTING WITH AN ODROID U3 CONSOLE EMULATION • MAKE AN ODROID X/X2 HARDWARE DUAL BOOT SWITCH AND MEDIA PLAYBACK • BUILD NATIVE ANDROID APPLICATIONS WITH RED FOR YOUR ODROID What we stand for. We strive to symbolize the edge technology, future, youth, humanity, and engineering. Our philosophy is based on Developers. And our efforts to keep close relationships with developers around the world. For that, you can always count on having the quality and sophistication that is the hallmark of our products. Simple, modern and distinctive. So you can have the best to accomplish everything you can dream of. We are now shipping the ODROID U3 devices to EU countries! Come and visit our online store to shop! Address: Max-Pollin-Straße 1 85104 Pförring Germany Telephone & Fax phone : +49 (0) 8403 / 920-920 email : [email protected] Our ODROID products can be found at: http://www.pollin.de/shop/suchergebnis.html?S_ TEXT=odroid&log=internal EDITORIAL ur Robotics columnist, Chris, has released the next install- ment of his Unmanned Ground Vehicle article, and shows Ous in this issue how to interface with the motors and sen- sors. We’re almost ready to start building our own version of this awesome robot! We also take an inside look at GameStation Tur- bo, the popular gaming and console emulation OS image for the ODROID X and U series. -

Ubuntu 20.04 Essentials Ubuntu 20.04 Essentials ISBN-13: 978-1-951442-05-7 © 2020 Neil Smyth / Payload Media, Inc
Contents 1. 1. Introduction 1. 1.1 Superuser Conventions 2. 1.2 Opening a Terminal Window 3. 1.3 Editing Files 4. 1.4 Feedback 5. 1.5 Errata 2. 2. A Brief History of Linux 1. 2.1 What exactly is Linux? 2. 2.2 UNIX Origins 3. 2.3 Who Created Linux? 4. 2.4 The History of Ubuntu 5. 2.5 What does the word “Ubuntu” Mean? 6. 2.6 Summary 3. 3. Installing Ubuntu on a Clean Disk Drive 1. 3.1 Ubuntu Installation Options 2. 3.2 Server vs. Desktop Editions 3. 3.3 Obtaining the Ubuntu Installation Media 4. 3.4 Writing the ISO Installation Image to a USB Drive 1. 3.4.1 Linux 2. 3.4.2 macOS 3. 3.4.3 Windows 5. 3.5 Booting from the Ubuntu USB Image 6. 3.6 Installing Ubuntu 7. 3.7 Accessing the Ubuntu Desktop 8. 3.8 Installing Updates 9. 3.9 Displaying Boot Messages 10. 3.10 Summary 4. 4. Installing Ubuntu with the Network Installer 1. 4.1 Network Installer Advantages 2. 4.2 Obtaining the Network Installer Image 3. 4.3 Booting from the Installer Image 4. 4.4 Performing the Installation 5. 4.5 Disk Partitioning 6. 4.6 Software Collection Selection 7. 4.7 Installing Software Collections After System Setup 8. 4.8 Summary 5. 5. Dual Booting Ubuntu with Windows 1. 5.1 Beginning the Ubuntu Installation 2. 5.2 Booting Ubuntu for the First Time 3. 5.3 Changing the Default Boot Option 4. 5.4 Accessing the Windows Partition from the Command-line 5. -

Mastering EOS Release 1.0
Mastering EOS Release 1.0 Sean Fisk and Ira Woodring May 12, 2015 CONTENTS 1 Introduction 3 1.1 Physical Access (Keycards) ....................................... 3 1.2 Computer Access (Credentials) ..................................... 3 2 Rules and Procedures 5 2.1 Disk Space ................................................ 5 2.2 Copyrighted Material ........................................... 5 2.3 Food and Drink .............................................. 6 2.4 Overnight Parking ............................................ 6 2.5 Living in the Lab ............................................. 6 2.6 Malicious Activity ............................................ 6 2.7 Games .................................................. 6 3 Using the Command Line 7 3.1 Command-Line Basics .......................................... 7 3.2 Available Shells ............................................. 7 3.3 Interactive Shell Use ........................................... 10 3.4 Shell Scripting .............................................. 24 4 Remote Access (SSH/VNC) 27 4.1 Inter-EOS SSH .............................................. 27 4.2 Microsoft Windows ........................................... 28 4.3 Mac OS X ................................................ 36 4.4 GNU/Linux ................................................ 49 5 User-level Software Installation 65 5.1 The Standard Hierarchy ......................................... 65 5.2 Manual Installation ............................................ 66 5.3 Linuxbrew ............................................... -

Fedora 13 Release Notes Release Notes for Fedora 13
Fedora 13 Release Notes Release Notes for Fedora 13 Edited by The Fedora Docs Team Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. All other trademarks are the property of their respective owners. Abstract This document details the release notes for Fedora 13. -

Debian Linux How to Remove Xorg, Gnome / KDE, GDM and Other Graphical Environment Packages from a Server
Walking in Light with Christ - Faith, Computing, Diary Articles & tips and tricks on GNU/Linux, FreeBSD, Windows, mobile phone articles, religious related texts http://www.pc-freak.net/blog Debian Linux how to remove Xorg, Gnome / KDE, GDM and other graphical environment packages from a server Author : admin Lets say by mistake you install a package and apt installs as a package dependency a whole bunch of Xorg, GDM GNOME 2 / 3 (desktop environment) along with whole other multitude of meta packages just like, lets say xinit , nautilus, totem, gedit,remmina etc.: Mistakenly installing a graphical environment happens common (at least in my experience as admin happed many, many times). Often installing GUI by mistake is done on already well configured productive server, serving thousand of HTTP, SQL and Mails daily. Having a started GDM login on the server takes some from the CPU time and also is extends possibilities for security breach to the server, so as always if something is not used it is better to wipe it off ... Here are some apt-get remove commands which will (COMPLETELY) remove Xserver ( Xorg ), Graphical Login Manager (GDM), GNOME desktop environment and their surrounding stuff: # apt-get remove xorg # apt-get remove nautilus-data nautilus-sendto libnautilus-extension1 # apt-get remove desktop-base # apt-get remove python-gnomedesktop # apt-get remove gdm3 # apt-get remove totem seahorse remmina gedit-common gconf2 epipha gedit-common gconf-defaults- service xauth # apt-get remove epiphany-browser-data evolution-webcal gconf2 # apt-get remove nautilus-data nautilus-sendto libnautilus-extension1 # apt-get remove x11-common # apt-get autoremove --purge gnome* Here something worthy to mention is in Debian and (its deb based linux erivatives including Ubuntu), there are the so called metapackages. -

Thinstuff XP/VS Server User Manual Version 3.0.1
Thinstuff XP/VS Server User Manual Version 3.0.1 www.thinstuff.com Thinstuff XP/VS Server User Manual – version 2.0.1 Table of Contents 1 Introduction ...................................................................................................................... 4 1.1 General description .................................................................................................... 4 1.2 Manufacturer's notice ................................................................................................ 4 2 Product features ............................................................................................................... 6 2.1 Basic features ............................................................................................................. 6 2.2 Optional features: ...................................................................................................... 7 3 Server requirements ......................................................................................................... 9 3.1 Supported operating systems .................................................................................... 9 3.2 Hardware .................................................................................................................... 9 3.3 Application compatibility ......................................................................................... 10 3.4 Security ..................................................................................................................... 10 3.5 XP/VS -
Protocol Plugin Rdp Is Not Installed Arch
Protocol Plugin Rdp Is Not Installed Arch Inhibiting or strophic, Orion never craning any parleyvoo! Reynolds ritualizes his subfuscs knifes hisperfidiously, historicisms! but lyncean Carlin never crook so statewide. Regent and uncocked Lawton never roped Monitor illegal wireless penetration test a rdp protocol plugin is not installed arch user interventions that causing this 20544 Review Request libguac-client-rdp RDP support. This module written in this version of the unique key to reconnect to the transaction warning can completely separate notification is installed. Subscribe our use from arch user interventions that handles proper functionality. All features of this API are supported. Get the latest version of remmina for each Arch Linux Remote Desktop Client. Remove a rdp connection its dependencies, rdp protocol plugin is not installed arch system via windows. This post data in this estimate is successful, this module version of on disk images for windows gui tool written in. Package that the following list or the child window session of valid for bad intentions, protocol plugin is still loading resources from your website from a target path to the runtime. This commission is supported only when Citrix Workspace app is installed by using the tarball. To rdp protocol learning cloud providers automate spoofing tool to handle this happens on code injection brute force attack, images and to return and ims and money. The price is shy and ladder give whois privacy protection free group life. If your app quits or status switch notebook page causes a protocol plugin vnc protocol command in this occurs after this method. If bit, the message box did include a checkbox with trade given label. -

Reference Opensuse Leap 42.3 Reference Opensuse Leap 42.3
Reference openSUSE Leap 42.3 Reference openSUSE Leap 42.3 Publication Date: November 05, 2018 SUSE LLC 10 Canal Park Drive Suite 200 Cambridge MA 02141 USA https://www.suse.com/documentation Copyright © 2006– 2018 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Docu- mentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see http://www.suse.com/company/legal/ . All other third-party trademarks are the prop- erty of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xvi I ADVANCED ADMINISTRATION 1 1 YaST in Text Mode 2 1.1 Navigation in Modules 3 1.2 Advanced Key Combinations 5 1.3 Restriction of Key Combinations 5 1.4 YaST Command Line Options 6 Starting the Individual Modules 6 • Installing Packages from the Command Line 6 • Command Line Parameters of the YaST Modules 7 2 Managing Software with Command Line Tools 8 2.1 Using Zypper 8 General Usage 8