Bootable Linux CD / PXE for the Remote Acquisition of Multiple Computers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

An User & Developer Perspective on Immutable Oses
An User & Developer Perspective on Dario Faggioli Virtualization SW. Eng. @ SUSE Immutable OSes [email protected] dariof @DarioFaggioli https://dariofaggioli.wordpress.com/ https://about.me/dario.faggioli About Me What I do ● Virtualization Specialist Sw. Eng. @ SUSE since 2018, working on Xen, KVM, QEMU, mostly about performance related stuff ● Daily activities ⇒ how and what for I use my workstation ○ Read and send emails (Evolution, git-send-email, stg mail, ...) ○ Write, build & test code (Xen, KVM, Libvirt, QEMU) ○ Work with the Open Build Service (OBS) ○ Browse Web ○ Test OSes in VMs ○ Meetings / Video calls / Online conferences ○ Chat, work and personal ○ Some 3D Printing ○ Occasionally play games ○ Occasional video-editing ○ Maybe scan / print some document 2 ● Can all of the above be done with an immutable OS ? Immutable OS: What ? Either: ● An OS that you cannot modify Or, at least: ● An OS that you will have an hard time modifying What do you mean “modify” ? ● E.g., installing packages ● ⇒ An OS on which you cannot install packages ● ⇒ An OS on which you will have an hard time installing packages 3 Immutable OS: What ? Seriously? 4 Immutable OS: Why ? Because it will stay clean and hard to break ● Does this sound familiar? ○ Let’s install foo, and it’s dependency, libfoobar_1 ○ Let’s install bar (depends from libfoobar_1, we have it already) ○ Actually, let’s add an external repo. It has libfoobar_2 that makes foo work better! ○ Oh no... libfoobar_2 would break bar!! ● Yeah. It happens. Even in the best families distros -

Downloads." the Open Information Security Foundation
Performance Testing Suricata The Effect of Configuration Variables On Offline Suricata Performance A Project Completed for CS 6266 Under Jonathon T. Giffin, Assistant Professor, Georgia Institute of Technology by Winston H Messer Project Advisor: Matt Jonkman, President, Open Information Security Foundation December 2011 Messer ii Abstract The Suricata IDS/IPS engine, a viable alternative to Snort, has a multitude of potential configurations. A simplified automated testing system was devised for the purpose of performance testing Suricata in an offline environment. Of the available configuration variables, seventeen were analyzed independently by testing in fifty-six configurations. Of these, three variables were found to have a statistically significant effect on performance: Detect Engine Profile, Multi Pattern Algorithm, and CPU affinity. Acknowledgements In writing the final report on this endeavor, I would like to start by thanking four people who made this project possible: Matt Jonkman, President, Open Information Security Foundation: For allowing me the opportunity to carry out this project under his supervision. Victor Julien, Lead Programmer, Open Information Security Foundation and Anne-Fleur Koolstra, Documentation Specialist, Open Information Security Foundation: For their willingness to share their wisdom and experience of Suricata via email for the past four months. John M. Weathersby, Jr., Executive Director, Open Source Software Institute: For allowing me the use of Institute equipment for the creation of a suitable testing -

Multi Software Product Lines in the Wild
AperTO - Archivio Istituzionale Open Access dell'Università di Torino Multi software product lines in the wild This is the author's manuscript Original Citation: Availability: This version is available http://hdl.handle.net/2318/1667454 since 2020-07-06T10:51:50Z Publisher: Association for Computing Machinery Published version: DOI:10.1145/3168365.3170425 Terms of use: Open Access Anyone can freely access the full text of works made available as "Open Access". Works made available under a Creative Commons license can be used according to the terms and conditions of said license. Use of all other works requires consent of the right holder (author or publisher) if not exempted from copyright protection by the applicable law. (Article begins on next page) 27 September 2021 Multi Software Product Lines in the Wild Michael Lienhardt Ferruccio Damiani [email protected] [email protected] Università di Torino Università di Torino Italy Italy Simone Donetti Luca Paolini [email protected] [email protected] Università di Torino Università di Torino Italy Italy ABSTRACT 1 INTRODUCTION Modern software systems are often built from customizable and A Software Product Line (SPL) is a set of similar programs, called inter-dependent components. Such customizations usually define variants, with a common code base and well documented variabil- which features are offered by the components, and may depend ity [1, 6, 19]. Modern software systems are often built as complex on backend components being configured in a specific way. As assemblages of customizable components that out-grow the expres- such system become very large, with a huge number of possible siveness of SPLs. -

Indicators for Missing Maintainership in Collaborative Open Source Projects
TECHNISCHE UNIVERSITÄT CAROLO-WILHELMINA ZU BRAUNSCHWEIG Studienarbeit Indicators for Missing Maintainership in Collaborative Open Source Projects Andre Klapper February 04, 2013 Institute of Software Engineering and Automotive Informatics Prof. Dr.-Ing. Ina Schaefer Supervisor: Michael Dukaczewski Affidavit Hereby I, Andre Klapper, declare that I wrote the present thesis without any assis- tance from third parties and without any sources than those indicated in the thesis itself. Braunschweig / Prague, February 04, 2013 Abstract The thesis provides an attempt to use freely accessible metadata in order to identify missing maintainership in free and open source software projects by querying various data sources and rating the gathered information. GNOME and Apache are used as case studies. License This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported (CC BY-SA 3.0) license. Keywords Maintenance, Activity, Open Source, Free Software, Metrics, Metadata, DOAP Contents List of Tablesx 1 Introduction1 1.1 Problem and Motivation.........................1 1.2 Objective.................................2 1.3 Outline...................................3 2 Theoretical Background4 2.1 Reasons for Inactivity..........................4 2.2 Problems Caused by Inactivity......................4 2.3 Ways to Pass Maintainership.......................5 3 Data Sources in Projects7 3.1 Identification and Accessibility......................7 3.2 Potential Sources and their Exploitability................7 3.2.1 Code Repositories.........................8 3.2.2 Mailing Lists...........................9 3.2.3 IRC Chat.............................9 3.2.4 Wikis............................... 10 3.2.5 Issue Tracking Systems...................... 11 3.2.6 Forums............................... 12 3.2.7 Releases.............................. 12 3.2.8 Patch Review........................... 13 3.2.9 Social Media............................ 13 3.2.10 Other Sources.......................... -

SUSE Linux Enterprise Desktop 15 SP2 Administration Guide Administration Guide SUSE Linux Enterprise Desktop 15 SP2
SUSE Linux Enterprise Desktop 15 SP2 Administration Guide Administration Guide SUSE Linux Enterprise Desktop 15 SP2 Covers system administration tasks like maintaining, monitoring and customizing an initially installed system. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xviii 1 Available Documentation xix 2 Giving Feedback xx 3 Documentation Conventions xxi 4 Product Life Cycle and Support xxii Support Statement for SUSE Linux Enterprise Desktop xxiii • Technology Previews xxiv I COMMON TASKS 1 1 Bash and Bash -

Gstreamer Past – Present - Future
GStreamer Past – Present - Future Wim Taymans ([email protected]) 26 oct 2010 – GStreamer Conference Cambridge, UK Overview Past ● Started in early 1999 by Eric Walthinsen – Based on OGI reseach – Ideas from DirectShow – C, G(tk)Object ● State of multimedia on linux was very poor back then – Xanim† (vlc 1999, Ogle† 1999, xine† 2000, mplayer 2000, ffmpeg 2000, ...) – No codec libraries ● Make something that can compete with Quicktime (1991) /DirectShow†(1996) Use cases ● Music players (Rhythmbox, Songbird,..) ● Video players (Totem, Webkit,...) ● Streaming servers (Axis, UbiCast, Flumotion, RTSP, DLNA server...) ● Transcoding (Arista, Transmageddon, …) ● Media capture (Cheese, N900, …) ● Audio editing (Jokosher, ..) ● Video editing (PiTiVi, …) ● VoIP (Empathy, Tandberg, ...) ● Desktop, embedded History ● 0.0.1 – Jun 1999 (POC) ● 0.1.0 – Jan 2001 ● 0.2.0 – Jun 2001 ● 0.3.0 – Dec 2001 ● 0.4.0 – Jul 2002 (in gnome, very rough) ● 0.6.0 – Feb 2003 (audio works ok) ● 0.8.0 – Mar 2004 (video works okish) ● 0.10.0 – Dec 2005 (redesign, maturity) – Currently 0.10.30 ● 1.0 - ??? Stats ● large community – 30+ core developers – 200+ contributers ● Core 205K LOC ● Plugins +1M LOC ● Estimated cost +$60M ● Many contributers work for companies nowadays – Many fulltime Overall commits per month Core commits per month plugins-good commits per month overall lines of code Core lines of code Plugins-good lines of code Some Features ● Fully multithreaded ● Advanced trick mode playback ● Video editing support ● Top notch RTP/streaming support ● Extensive, -

Make the Switch: Novell's Guide to the Novell® Linux® Desktop
Make the Switch: Novell's Guide to the Novell® Linux® Desktop Novell Training Services www.novell.com COURSE 3056 AUTHORIZED COURSEWARE 106-001301-001 Make the Switch Novell Linux Desktop (c) 2004 Novell Inc. Proprietary Statement Copyright 2004 Novell, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted without the express prior consent of the publisher. This manual, and any portion thereof, may not be copied without the express written permission of Novell, Inc. Novell, Inc. 1800 South Novell Place Provo, UT 84606 Disclaimer Novell, Inc. makes no representations or warranties with respect to the contents or use of this manual, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to revise this publication and to make changes in its content at any time, without obligation to notify any person or entity of such revisions or changes. Further, Novell, Inc. makes no representations or warranties with respect to any of its software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to make changes to any and all parts of its software at any time, without obligation to notify any person or entity of such changes. This Novell Training Manual is published solely to instruct students in the use of Novell networking software. Although third-party application software packages are used in Novell training courses, this is for demonstration purposes only and shall not constitute an endorsement of any of these software applications. -

Pipewire Slides
PipeWire Wim Taymans Principal Software Engineer FOSDEM 2019 1 PipeWire | Wim Taymans What is it Multimedia sharing and processing engine 6 PipeWire | Wim Taymans The multimedia stack App Browser Skype GStreamer VLC Ardour Pulseaudio JACK wayland V4l2 bluetooth alsa va-api DRM Kernel 7 PipeWire | Wim Taymans PipeWire App Session Manager GStreamer VLC App1 App2 JACK Wayland PipeWire Daemon V4l2 bluetooth alsa va-api DRM Kernel 8 PipeWire | Wim Taymans Features ● Exchange media with devices and other apps ● Zero copy, shared memory, memfd, dmabuf, eventfd ● Security per application ● Visible objects (R), methods (WX), .. ● RT capable, low latency (<1.5ms) ● All media types + generic control streams ● Simple JACK-like scheduler + feedback loops ● Extensible: types, protocol, ... ● External session manager implements policy 21 PipeWire | Wim Taymans Session manager ● Setup of devices ● DSP processing, effects, mixers, .. ● Security of clients ● What they can see, default permissions ● Management of links/nodes in the graph ● What nodes and effects to link to (profiles, roles, ..) ● Suspend of idle devices, volume restore, … ● The things you want to configure 22 PipeWire | Wim Taymans V4l2 capture/sharing Client1 Client2 ... To screen PipeWire-0 V4l2 bluetooth alsa va-api DRM Kernel 23 PipeWire | Wim Taymans Video capture ● Systemd socket activation in Fedora 29 ● Gstreamer pipewiresrc ● Device Monitor ● Autovideosrc → Should work in cheese 24 PipeWire | Wim Taymans 25 PipeWire | Wim Taymans Wayland screen sharing Mutter Screen Recording Remote -

Debian and Ubuntu
Debian and Ubuntu Lucas Nussbaum lucas@{debian.org,ubuntu.com} lucas@{debian.org,ubuntu.com} Debian and Ubuntu 1 / 28 Why I am qualified to give this talk Debian Developer and Ubuntu Developer since 2006 Involved in improving collaboration between both projects Developed/Initiated : Multidistrotools, ubuntu usertag on the BTS, improvements to the merge process, Ubuntu box on the PTS, Ubuntu column on DDPO, . Attended Debconf and UDS Friends in both communities lucas@{debian.org,ubuntu.com} Debian and Ubuntu 2 / 28 What’s in this talk ? Ubuntu development process, and how it relates to Debian Discussion of the current state of affairs "OK, what should we do now ?" lucas@{debian.org,ubuntu.com} Debian and Ubuntu 3 / 28 The Ubuntu Development Process lucas@{debian.org,ubuntu.com} Debian and Ubuntu 4 / 28 Linux distributions 101 Take software developed by upstream projects Linux, X.org, GNOME, KDE, . Put it all nicely together Standardization / Integration Quality Assurance Support Get all the fame Ubuntu has one special upstream : Debian lucas@{debian.org,ubuntu.com} Debian and Ubuntu 5 / 28 Ubuntu’s upstreams Not that simple : changes required, sometimes Toolchain changes Bugfixes Integration (Launchpad) Newer releases Often not possible to do work in Debian first lucas@{debian.org,ubuntu.com} Debian and Ubuntu 6 / 28 Ubuntu Packages Workflow lucas@{debian.org,ubuntu.com} Debian and Ubuntu 7 / 28 Ubuntu Packages Workflow Ubuntu Karmic Excluding specific packages language-(support|pack)-*, kde-l10n-*, *ubuntu*, *launchpad* Missing 4% : Newer upstream -
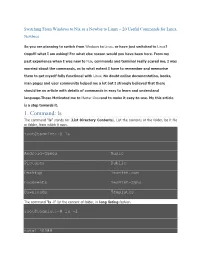
1. Command: Ls the Command “Ls” Stands for (List Directory Contents), List the Contents of the Folder, Be It File Or Folder, from Which It Runs
Switching From Windows to Nix or a Newbie to Linux – 20 Useful Commands for Linux Newbies So you are planning to switch from Windows to Linux, or have just switched to Linux? Oops!!! what I am asking! For what else reason would you have been here. From my past experience when I was new to Nux, commands and terminal really scared me, I was worried about the commands, as to what extent I have to remember and memorise them to get myself fully functional with Linux. No doubt online documentation, books, man pages and user community helped me a lot but I strongly believed that there should be an article with details of commands in easy to learn and understand language.These Motivated me to Master Linuxand to make it easy-to-use. My this article is a step towards it. 1. Command: ls The command “ls” stands for (List Directory Contents), List the contents of the folder, be it file or folder, from which it runs. root@tecmint:~# ls Android-Games Music Pictures Public Desktop Tecmint.com Documents TecMint-Sync Downloads Templates The command “ls -l” list the content of folder, in long listing fashion. root@tecmint:~# ls -l total 40588 drwxrwxr-x 2 ravisaive ravisaive 4096 May 8 01:06 Android Games drwxr-xr-x 2 ravisaive ravisaive 4096 May 15 10:50 Desktop drwxr-xr-x 2 ravisaive ravisaive 4096 May 16 16:45 Documents drwxr-xr-x 6 ravisaive ravisaive 4096 May 16 14:34 Downloads drwxr-xr-x 2 ravisaive ravisaive 4096 Apr 30 20:50 Music drwxr-xr-x 2 ravisaive ravisaive 4096 May 9 17:54 Pictures drwxrwxr-x 5 ravisaive ravisaive 4096 May 3 18:44 Tecmint.com drwxr-xr-x 2 ravisaive ravisaive 4096 Apr 30 20:50 Templates Command “ls -a“, list the content of folder, including hidden files starting with „.‟. -

Xrdp.Log.Pdf
Printed by Stephen Quinney Feb 05, 19 13:46 xrdp.log.txt Page 1/3 * Wednesday 31st January 2018 Stephen has imported the XRDP configuration from SEE. Most of it has been put into lcfg−level headers so that it can be shared. At the top level the service is configured using the dice/options/external−xrdp−server.h header. There is a test service accessible at xrdp.inf.ed.ac.uk which seems to work well. A quick survey of clients for Linux suggests that the best is remmina. Stephen will be talking about the project at the next Development meeting so before then he will collect all his notes on a wiki page for the project. * Wednesday 7th February 2018 Since SEE has already put together a remote desktop solution which works well and is freely available, there seemed little point in trying other possible solutions; so a small test version of SEE’s RDP−based remote desktop service has been set up here in Informatics. It uses HAProxy as a load−balancing front end. In the trial service at xrdp.inf.ed.ac.uk, the front end routes connection requests to the less loaded of the two backend machines, or to an existing session if there is one. The test service will be open to computing staff. It’s envisaged that the full service will use real hardware rather than virtual, and that there will be separate staff and student services. The next work on this project will be to add some Informatics identity to the login screen; to change access controls on the PAM stack for the backend machines, to permit differences between staff and student services; and to document the services on computing.help.