Microsoft Windows FIPS 140 Validation Security Policy Document
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

QI Wireless Compatible Device List Apple Asus Blackberry CASIO
QI Wireless Compatible Device List Apple • iPhone 8 • iPhone 8 Plus • iPhone X • iPhone Xs • iPhone Xs Max • iPhone Xr Asus • Asus PadFone S BlackBerry • BlackBerry Passport • BlackBerry PRIV • BlackBerry Z30 CASIO • CASIO G'z One Commando Caterpillar • Cat S50 • Cat S50C DeWalt • Dewalt MD501 • Dewalt MIL810G Energy Sistem • Energy Phone Pro Qi Fujitsu • Fujitsu Arrows F-09D • Fujitsu Arrows Kiss F-03D • Fujitsu Arrows Kiss F-03E • Fujitsu Arrows X F-10D Google • Google Nexus 4 • Google Nexus 5 • Google Nexus 6 • Google Pixel 3 • Google Pixel 3 XL HP • HP Elite X3 HTC • HTC Droid DNA • HTC Windows Phone 8X Huawei • Huawei Mate20 Pro • Huawei Mate RS Porsche Design • Huawei P30 Pro Kyocera • Kyocera Brigadier • Kyocera DuraForce • Kyocera Hydro Elite • Kyocera Torque G02 • Kyocera Torque KC-S701 • Kyocera Urbano L01 • Kyocera Urbano L03 LG • LG G2 • LG G3 • LG G6 ¹ • LG G6 Plus ¹ • LG G7 • LG G7 ThinQ • LG Lucid 2 • LG Lucid 3 • LG Optimus F5 • LG Optimus G Pro • LG Optimus It L-05E • LG Spectrum 2 • LG Vu 2 • LG Vu 3 • LG V30 • LG V30 Plus • LG V40 ThinQ M.T.T. • M.T.T. Master 4G Meizu • Meizu Zero Microsoft • Microsoft Lumia 950 • Microsoft Lumia 950 Dual Sim • Microsoft Lumia 950 XL • Microsoft Lumia 950 XL Dual Sim Mlais • Mlais MX69W Motorola • Motorola Droid Maxx • Motorola Droid Mini • Motorola Droid Turbo • Motorola Droid Turbo 2 • Motorola Moto Maxx • Motorola Moto X Force mPhone • mPhone 8 NEC • NEC Medias PP N-01D • NEC Medias X N-04E Noa • Noa F10 Pro Nokia • Nokia Lumia 1520 • Nokia Lumia 735 • Nokia Lumia 830 • Nokia Lumia -

HR Kompatibilitätsübersicht
Kompatibilitätsübersicht HR-imotion HR-imotion Kompatibilität/Compatibility 2017 / 03 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview X3 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone SE Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus ZenFone AR Smartphone BlackBerry Classic Smartphone Blackberry DTEK 50 Smartphone Blackberry KEYOne Smartphone BlackBerry Passport Smartphone BlackBerry Priv Smartphone BlackBerry Z30 Smartphone BQ Aquaris X5 Smartphone BQ Aquaris X5 Plus Smartphone CAT B15 Smartphone Cubot P11 Smartphone Cubot S500 Smartphone Elephone P8000 Smartphone Emporia Pure Smartphone Gigaset GS160 Smartphone Gigaset ME Smartphone Gigaset ME Pro Smartphone Gigaset ME Pure Smartphone Google Nexus 5 Smartphone Google Nexus 5X Smartphone Google Nexus 6 Smartphone Google Nexus 6P Smartphone Google Pixel -

Załącznik Cenowy „Promocyjne Telefony Dla Taryf Jump”
Załącznik cenowy „Promocyjne telefony dla taryf Jump”. 1. W okresie od 02.09.2016 r. do wyczerpania zapasów zestawów objętych niniejszą promocją lub jej odwołania, operator T-Mobile Polska oferuje następujące aparaty telefoniczne w cenach (wysokość pierwszej raty). 2. Promocyjne telefony dla Zestawów (Start, Comfort, Relax, Multi, Max, Max + Premium +). Dotyczy Ofert Promocyjnych wymienionych w pkt od 2.1 do 2.2 Pola zaznaczone szarym kolorem dotyczą wyłącznie wariantu oferty bez rat. Pola niezaznaczone szarym kolorem dotyczą zarówno wariantu oferty z ratami jak i wariantu oferty bez rat. Wartości podane w tabelach (za wyjątkiem wierszy „Opłaty miesięczne”) wskazują wyrażoną w złotych polskich wysokość ceny (w przypadku, gdy model podlega sprzedaży bez rat) lub pierwszej raty tj. pierwszej wpłaty (w przypadku, gdy model podlega sprzedaży na raty). 2.1. Telefony w pełnej dostępności dotyczy „Oferta Jump z telefonem na 24 miesiące w T-Mobile” Taryfa / Zestaw Premium + Max + Max Multi Relax Comfort Start Opłaty abonamentowe 199,99 149,99 129,99 99,99 79,99 69,99 49,99 Huawei Y5 LTE 9 9 9 9 9 9 9 Huawei Y6 LTE 9 9 9 9 9 9 9 Microsoft Lumia 550 9 9 9 9 9 9 9 Maxcom MM720 9 9 9 9 9 9 9 Maxcom MM237 DualSIM 9 9 9 9 9 9 9 Alcatel 20.12 9 9 9 9 9 9 9 Nokia 230 Dual SIM 9 9 9 9 9 9 9 Alcatel ONETOUCH Pixi 3 (4.5) 9 9 9 9 9 9 9 Kazam Life R5 9 9 9 9 9 9 9 Kazam Life R6 9 9 9 9 9 9 9 Alcatel ONETOUCH POP 3 (5) 9 9 9 9 9 9 9 LG Leon (H340n) LTE 9 9 9 9 9 9 9 LG K3 Dual SIM (K100DS) 9 9 9 9 9 9 9 Kazam LIFE R6 9 9 9 9 9 9 9 Lenovo C2 9 9 9 9 9 9 99 -

HR-Imotion Kompatibilitätsübersicht So Vergleichen Sie Ob Ihr Smartphone Oder Tablet in Den Gerätehalter Passt
HR-imotion Kompatibilitätsübersicht So vergleichen Sie ob Ihr Smartphone oder Tablet in den Gerätehalter passt. 1. Überprüfen Sie die Artikel Nummer des Gerätehalter. Sie finden die Nummer auf der Unterseite der Verpackung über dem Strichcode Auf der Amazon Webseite im Produkttitel oder im Produktinformationsbereich 2. Suchen Sie nun Ihr Telefon oder Tablet in der auf der nächsten Seite startenden Geräteübersicht Sollte Ihr Tablet oder Smartphone nicht auftauchen, so messen Sie bitte die Länge und Breite des Smartphone oder Tablet ab und vergleichen Sie es mit den genannten Abmessungen in der Beschreibung / Stichpunkten. Leider können wir bei dem sich ständigen wechselnden Smartphone- und Tabletprodukten nicht alle Geräte in dieser Liste führen. 3. Schauen Sie nun in der Spalte mit der heraus gesuchten Artikelnummer ob Ihr Telefon oder Tablet passt: = Produkt passt in die Halterung = Produkt passt nicht in die Halterung Beispiel Sie besitzen ein Google Nexus 6P und möchten ent- weder wissen, welche Halterung Sie nutzen können oder ob die Quicky Lüftungshalterung (Art. Nr. 22110101) passt. Kompatibilitätsübersicht HR-imotion HR-imotion Kompatibilitätsübersicht Stand: 2016 / 3 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 Smartphone AEG Voxtel M250 Smartphone Alcatel Idol 4S Smartphone Allview X3 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone -

Introducing Microsoft Lumia with Windows 10
Introducing Microsoft Lumia with Windows 10. Your business. Mobile. 104901-054_MSG_Lumia_A5 Overview Brochure_Print_a1.indd 1 20/10/2015 14:42 Contents Your business. Mobile. ......................................................................... 4 Windows 10 for phone. ........................................................................ 8 Stay productive on the go. ................................................................. 10 Protection against modern security threats. ................................ 12 Centrally manage your mobile devices. ........................................ 14 Business apps made easy. .................................................................. 16 Capitalise on existing Microsoft investments. ............................. 20 Microsoft Lumia phones. Microsoft inside and out. .................. 22 The latest range of Microsoft Lumia phones. .............................. 24 Ongoing technical support. From day one. ................................. 26 Why choose Microsoft Lumia. ......................................................... 28 104901-054_MSG_Lumia_A5 Overview Brochure_Print_a1.indd 2-3 20/10/2015 14:42 4 | Microsoft Lumia with Windows 10 Your business. Mobile. Microsoft Lumia 950 XL The power, security and productivity of Windows 10 is here. And with Microsoft Lumia, it’s anywhere. Beyond the desktop. Beyond the office. Beyond expectations. Start a document in your office, make changes in a taxi. With Microsoft Lumia with Windows 10, your business travels wherever you go. Expect document-friendly -

Microsoft Windows Common Criteria Evaluation Security Target
Windows 10, Windows 10 Mobile Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 Microsoft Windows 10 Mobile Security Target Document Information Version Number 0.09 Updated On April 12, 2016 Microsoft © 2016 Page 1 of 161 Windows 10, Windows 10 Mobile Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Introducing Microsoft Lumia with Windows 10
Introducing Microsoft Lumia with Windows 10. Your business. Mobile. 2 | Microsoft Lumia with Windows 10 Contents Your business. Mobile. .......................................................................................................... 3 Windows 10 for phone. ......................................................................................................... 5 Stay productive on the go. .................................................................................................. 6 Protection against modern security threats. ................................................................. 7 Centrally manage your mobile devices. ......................................................................... 8 Business apps made easy. .................................................................................................... 9 Capitalise on existing Microsoft investments. ............................................................. 11 Microsoft Lumia phones. Microsoft inside and out. ................................................. 12 The latest range of Microsoft Lumia phones. ............................................................. 13 Ongoing technical support. From day one. ................................................................ 14 Why choose Microsoft Lumia. .......................................................................................... 15 3 | Microsoft Lumia with Windows 10 Your business. Mobile. The power, security and productivity of Expect document-friendly large Windows 10 is here. -

National Information Assurance Partnership Common Criteria
National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme ® TM Validation Report for Microsoft Windows 10 (Anniversary Update) Report Number: CCEVS-VR-10752-2017 Dated: April 12, 2017 Version: 1.0 National Institute of Standards and Technology National Security Agency Information Technology Laboratory Information Assurance Directorate 100 Bureau Drive 9800 Savage Road STE 6940 Gaithersburg, MD 20899 Fort George G. Meade, MD 20755-6940 VALIDATION REPORT Microsoft Windows 10 (Anniversary Update) ACKNOWLEDGEMENTS Validation Team Stelios Melachrinoudis Jean Petty Common Criteria Testing Laboratory Leidos, Inc. Columbia, MD ii VALIDATION REPORT Microsoft Windows 10 (Anniversary Update) Table of Contents 1 Executive Summary ...................................................................................................................1 2 Identification ..............................................................................................................................4 2.1 Threats...............................................................................................................................4 2.2 Organizational Security Policies .......................................................................................5 3 Architectural Information ..........................................................................................................6 4 Assumptions ...............................................................................................................................9 -

Microsoft Lumia Mit Windows 10
Microsoft Lumia mit Windows 10. Einscannen und das Beste für Ihr Business erleben. Ihr Business. Unterwegs. © 2016 Microsoft Corporation. Alle Rechte vorbehalten. Microsoft, Windows und das Microsoft-Logo sind Warenzeichen der Microsoft Firmengruppe. Andere hier erwähnte Produkt- oder Firmennamen können eingetragene Markenzeichen oder Produktbezeichnungen der jeweiligen Rechteinhaber sein. Stand: Februar 2016. Entdecken Sie alle Lumia Smartphones auf: Lumia for Business www.microsoft.com/mobile 2 | Microsoft Lumia mit Windows 10 Ihr Business. Unterwegs. Mit Windows 10. Windows 10 ist da und bietet Ihnen jetzt noch mehr Leistung, Sicherheit und Produktivität. Erstellen Sie ein Dokument in Ihrem Büro und bearbeiten Sie es im Taxi einfach weiter. Mit Microsoft Lumia und Windows 10 ist Ihr Business immer da wo Sie sind. Erleben Sie unser großartiges Betriebssystem mit dem besten Microsoft Office. Inklusive vertrauter Anwendungen wie Excel, Word, Ihr Windows-Erlebnis auf Outlook und Powerpoint – optimiert für eine einfache und komfortable Bedienung auf dem Smartphone. allen Geräten. Von der IT-Abteilung bis hin zu Ihren Außendienstmitarbeitern: Die Kombination Stellen Sie sich vor, neue Technik wäre Verbinden Sie das Lumia 950 oder Lumia aus Hardware, Betriebssystem und von Beginn an einfach zu bedienen. Mit 950 XL mit Hilfe des neuen Microsoft Display Anwendungen macht Microsoft zur besten Windows 10 ist das jetzt Realität. Es ist unser Docks mit Bildschirm, Maus und Tastatur Wahl für Ihr Business. bisher fortschrittlichstes Betriebssystem und schon können Sie komfortabel arbeiten und wurde entwickelt, um die Nutzung auf egal wo Sie gerade sind. Und das Beste: Ihr allen Geräten einheitlich zu gestalten. Egal Lumia lässt sich gleichzeitig ganz normal als ob auf dem PC, Tablet oder Smartphone1. -

Qi Enabled Phones with Wireless Charging – Compatible Devices
QI ENABLED PHONES WITH WIRELESS CHARGING – COMPATIBLE DEVICES Wireless charging is a relatively new technology that is rapidly making its’ way to our daily lives. You may have been using wireless charging for many years already if you possess an electrical toothbrush: you just put it on the holder and it starts charging. Nowadays already over 600 types of devices are in the market which can be charged wirelessly. All phones with wireless charging compatibilitycurrently on the market are listed on this page. Find out if your smartphone is or can be enabled with the Qi standard by viewing the list below. Does your car feature wireless phone charging? Whether as a standard- or optional feature, wireless phone charging for cars is available on a large scale already. What about your vehicle? Find out and view all cars with in-vehicle wireless charging compatibility currently on the market. ZENS is both tier 1, tier 2 and after- market supplier for OEMs in the automotive industry. More information about wireless charging? As a wireless charging expert, we’d like to explain more about the transfer of wireless power and its’ technology. How does wireless charging work? What is this Qi standard? Is wireless charging safe? Wireless Charging Furniture Integration for Offices, Workplaces & Desks, Restaurants, Kitchens & Bedrooms We at ZENS are continuously looking for new wireless charging applications for consumers and business solutions. Recently for instance we presented the world’s first integrated wireless charging system for laptops. If you’re thinking about applying the technology to your business environment, do not hesitate to contact us. -
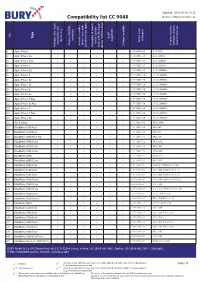
Compatibility List CC 9048 Device Software Version: 22
Updated: 2016-10-25 / V.22 Compatibility list CC 9048 Device software version: 22 No Type A2DP activation (Charger) supported device key Article code car kit / private connection with test/ Comments phone voice-dial software used to Phone‘s REDIAL Phone‘s REDIAL Version of phone Version Access to mobile Charger available Possibility to switch Activation Bluetooth function (voice tags) mode with Bluetooth device / phones keys 1 Apple iPhone 0-07-0258-0.07 3.0(7A341) 2 Apple iPhone 3G 0-07-0258-0.07 4.2.1 (8A306) 3 Apple iPhone 3GS 0-07-0258-0.07 6.1.2 (10B146) 4 Apple iPhone 4 0-07-0258-0.07 7.0.2 (11A501) 5 Apple iPhone 4S 0-07-0258-0.07 7.0.4 (11B554a) 6 Apple iPhone 5 0-07-0258-0.08 10.0.2 (14A456) 7 Apple iPhone 5c 0-07-0258-0.08 10.0.2 (14A456) 8 Apple iPhone 5s 0-07-0258-0.08 10.0.2 (14A456) 9 Apple iPhone 6 0-07-0258-0.08 10.0.2 (14A456) 10 Apple iPhone 6s 0-07-0258-0.08 10.0.2 (14A456) 11 Apple iPhone 6 Plus 0-07-0258-0.08 10.0.2 (14A456) 12 Apple iPhone 6s Plus 0-07-0258-0.08 10.0.2 (14A456) 13 Apple iPhone 7 0-07-0258-0.08 10.0.3 (14A551) 14 Apple iPhone 7 Plus 0-07-0258-0.08 10.0.3 (14A551) 15 Apple iPhone SE 0-07-0258-0.08 10.0.2 (14A456) 16 ASUS Solaris 0-07-0258-0.02 V4.2.2 WWE 17 BlackBerry 8100 Pearl 0-07-0258-0.02 V4.5.0.69 18 BlackBerry 8110 Pearl 0-07-0258-0.02 V4.5.0.55 19 BlackBerry 8220 Pearl Flip 0-07-0258-0.01 V4.6.0.94 20 BlackBerry 8300 Curve 0-07-0258-0.02 V4.5.0.182 21 BlackBerry 8310 Curve -

Asian Handset Supply Chain Research Analysts SECTOR REVIEW
25 February 2016 Asia Pacific Equity Research Electronic Equipment & Instruments (Technology Hardware & Equipment) Asian Handset Supply Chain Research Analysts SECTOR REVIEW Randy Abrams, CFA 886 2 2715 6366 [email protected] Mobile World Congress 2016: A long-term Jerry Su evolution in hardware 886 2 2715 6361 [email protected] Figure 1: Mediatek’s share price performance—historical trend around MWC Pauline Chen vs sales YoY 886 2 2715 6323 Mediatek stock performance entering/exiting MWC (T-30 as benchmark) [email protected] 20% 60% 10% 30% Keon Han 0% 0% 82 2 3707 3740 -10% -30% [email protected] -20% -60% Thompson Wu 2010 2011 2012 2013 2014 2015 2016 T-5 T+5 T+30 Sales YoY (%) 886 2 2715 6386 [email protected] Source. Company data, Bloomberg consensus, Credit Suisse estimates Mobile World Congress (MWC), the wireless industry’s largest annual event, took Sam Li place this week in Barcelona. Our team met chipset, component and device 852 2101 6775 [email protected] companies, spanning tier 1, branded Chinese, and whitebox vendors. In this note, we profile Samsung, Lenovo, Asustek and Mediatek, and their implications for the Derrick Yang 886 2 2715 6367 Asian supply chain. The following are the key summary points: [email protected] ■ Flagships led by Samsung’s fresh new look. Samsung’s unpacked event Kyna Wong set the tone for the MWC where peripherals (VR, 360 Degree Cameras) 852 2101 6950 shifted some focus from only modest upgrades to the flagship smartphone.