Part I: Internet Censorship in the Uk Today
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Content Regulation in the Digital
Content Regulation in the Digital Age Submission to the United Nations Special Rapporteur on the Right to Freedom of Opinion and Expression by the Association for Progressive Communications (APC) February 2018 Introduction 1 I. Company compliance with State laws 2 Terrorism-related and extremist content 3 False news, disinformation and propaganda 4 The “right to be forgotten” framework? 7 How should companies respond to State content regulation laws and measures that may be inconsistent with international human rights standards? 8 II. Other State Requests 9 State requests based on platform terms of service (ToS) and “shadow” requests 9 Non-transparent agreements with companies 10 III. Global removals 11 IV. Individuals at risk 12 V. Content regulation processes 15 VI. Bias and non-discrimination 16 VII. Appeals and remedies 17 VIII. Automation and content moderation 17 IX. Transparency 18 X. General recommendations from APC 19 Introduction The Association for Progressive Communications (APC) is an international network and non- profit organisation founded in 1990 that works to help ensure everyone has affordable access to a free and open internet to improve lives, realise human rights and create a more just world. We welcome this topic because it is current and integral to our work. On the one hand there is a lot of ‘noise’ in the mainstream media about so-called “fake news” and what appears to be a fairly rushed response from platforms consisting of increasing in-house regulation of content. On the other hand, human rights defenders and activists we work with express concern that 1 platforms are removing some of their content in a manner that suggests political bias and reinforcing of societal discrimination. -

Claiming and Reclaiming the Digital World As a Public Space
Claiming and Reclaiming the Digital World as a Public Space Experiences and insights from feminists in the Middle East and North Africa www.oxfam.org OXFAM DISCUSSION PAPER – NOVEMBER 2020 This paper seeks to highlight the experiences and aspirations of young women and feminist activists in the MENA region around digital spaces, safety and rights. It explores individual women’s experiences engaging with the digital world, the opportunities and challenges that women’s rights and feminist organizations find in these platforms, and the digital world as a space of resistance, despite restrictions on civic space. Drawing on interviews with feminist activists from the region, the paper sheds light on women’s online experiences and related offline risks, and illustrates patterns and behaviours that prevailed during the COVID-19 pandemic. © Oxfam International November 2020 This paper was written by Francesca El Asmar. Oxfam acknowledges the assistance of Hadeel Qazzaz, Manal Wardé, Neus Tirado Gual, Salma Jrad, Joane Cremesty, Suzan Al Ostaz, Fadi Touma and Mounia Semlali in its production, as well as the contributions of the interviewees who participated in the research process. It is part of a series of papers written to inform public debate on development and humanitarian policy issues. For further information on the issues raised in this paper please email [email protected] This publication is copyright but the text may be used free of charge for the purposes of advocacy, campaigning, education, and research, provided that the source is acknowledged in full. The copyright holder requests that all such use be registered with them for impact assessment purposes. -
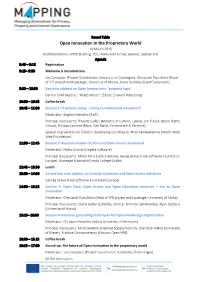
Open Innovation in the Proprietary World
Round Table Open Innovation in the Proprietary World 19 March 2015 DiploFoundation, WMO Building, 7bis, Avenue de la Paix, Geneva, Switzerland Agenda 8:45 – 9:15 Registration 9:15– 9:30 Welcome & Introductions Joe Cannataci (Project Coordinator; University of Groningen), Oleksandr Pastukhov (Head of IPR project work package; University of Malta), Jovan Kurbalija (DiploFoundation) 9:30 – 10:30 Key-note address on Open Innovation v. ‘property logic’ Darren Todd (Author, “Pirate Nation”; Editor, Evolved Publishing) 10:30 – 10:45 Coffee break 10:45 – 11:30 Session 1: IP policies today – failing to understand innovation? Moderator: Bogdan Manolea (ApTI) Principal discussants: Rihards Gulbis (Ministry of Culture, Latvia), Jim Killock (Open Rights Group), Philippe Laurent (Marx, Van Ranst, Vermeersch & Partners) Special intervention on F/OSS in developing countries by Nnenna Nwakanma (World Wide Web Foundation) 11:30 – 12:45 Session 2: Business models for the Free/Open Source movement Moderator: Pedro Gomez (Hoplite Software) Principal discussants: Mario Pena (Safe Creative), Georg Greve (Free Software Foundation Europe), Giuseppe Mazziotti (Trinity College Dublin) 12:45 – 13:30 Lunch 13:30 – 14:30 Second key-note address on Creative Commons and Open Access initiatives George Greve (Free Software Foundation Europe) 14:30 – 15:15 Session 3: Open Data, Open Access and Open Education resources – key to Open Innovation Moderator: Oleksandr Pastukhov (Head of IPR project work package; University of Malta) Principal discussants: Claire Gallon (Libertic), -

Intellectual Privacy and Censorship of the Internet
Georgetown University Law Center Scholarship @ GEORGETOWN LAW 1998 Intellectual Privacy and Censorship of the Internet Julie E. Cohen Georgetown University Law Center, [email protected] This paper can be downloaded free of charge from: https://scholarship.law.georgetown.edu/facpub/1963 8 Seton Hall Const. L.J. 693 (1997-1998) This open-access article is brought to you by the Georgetown Law Library. Posted with permission of the author. Follow this and additional works at: https://scholarship.law.georgetown.edu/facpub Part of the First Amendment Commons, and the Intellectual Property Law Commons 1998 INTERNET SYMPOSIUM INTELLECTUAL PRIVACY AND CENSORSHIP OF THE INTERNET ProfessorJulie E. Cohen Good morning. I would like to thank the Constitutional Law Journal for inviting me to be here today. I am not a First Amendment lawyer. I am not really a constitutional law- yer, so why am I here? I think that after having heard Dan Burk's presenta- tion, you should realize that intellectual property lawyers need to be First Amendment lawyers as well. You have all heard the aphorism that the Internet interprets censorship as a malfunction and routes around it.' You also may have heard that censorship on the Internet is a terrible thing; in particular, you may have heard this in the context of debates about pornography on the Inter- net or hate speech on the Internet. I would like to suggest to you today, how- ever, that the single most prevalent problem involving censorship on the Inter- net has to do with the protection of intellectual property. If you think about it, intellectual property protection, and particularly copy- right protection, is a form of censorship. -

Edition No. 3 March 2019
GDPR Today Edition No. 3 March 2019 European Commission urged to investigate Romanian GDPR implementation GDPR loopholes facilitate data exploitation by political parties Uber drivers demand their data After Brexit, the EU must decide if UK data protection is adequate 2 GDPR in Numbers 6 European Commission urged to investigate Romanian GDPR implementation 8 Spain: DPA limits the use of data in political campaigning 10 Netherlands: DPA rules websites must allow people to refuse tracking cookies 12 GDPR loopholes facilitate data exploitation by political parties 14 Privacy policies for Internet of Things devices must comply with GDPR 15 Uber drivers demand their data New evidence in AdTech complaint 15 EDPB: e-Privacy and GDPR work together 16 to protect people’s data 18 German competition regulator demands changes to Facebook’s use of personal data 20 After Brexit, the EU must decide if UK data protection is adequate 22 EDPS 2018 Annual Report highlights the power and limitation of data protection 24 GDPR Tools 25 EU National Data Protection Authority Contact Details Editorial Welcome to GDPR Today – your online hub for staying Not all is positive progress. It is disappointing that the tuned to the (real) life of EU data protection law. As you European Commission has still not yet taken action to know, every two months we publish statistics showing how ensure that Romania properly implements the GDPR. the GDPR is being applied across Europe. We also share There are also several countries which have yet to relevant news, from legal guidelines and decisions to publish any GDPR data. -

The Right to Privacy in the Digital Age
The Right to Privacy in the Digital Age April 9, 2018 Dr. Keith Goldstein, Dr. Ohad Shem Tov, and Mr. Dan Prazeres Presented on behalf of Pirate Parties International Headquarters, a UN ECOSOC Consultative Member, for the Report of the High Commissioner for Human Rights Our Dystopian Present Living in modern society, we are profiled. We accept the necessity to hand over intimate details about ourselves to proper authorities and presume they will keep this information secure- only to be used under the most egregious cases with legal justifications. Parents provide governments with information about their children to obtain necessary services, such as health care. We reciprocate the forfeiture of our intimate details by accepting the fine print on every form we sign- or button we press. In doing so, we enable second-hand trading of our personal information, exponentially increasing the likelihood that our data will be utilized for illegitimate purposes. Often without our awareness or consent, detection devices track our movements, our preferences, and any information they are capable of mining from our digital existence. This data is used to manipulate us, rob from us, and engage in prejudice against us- at times legally. We are stalked by algorithms that profile all of us. This is not a dystopian outlook on the future or paranoia. This is present day reality, whereby we live in a data-driven society with ubiquitous corruption that enables a small number of individuals to transgress a destitute mass of phone and internet media users. In this paper we present a few examples from around the world of both violations of privacy and accomplishments to protect privacy in online environments. -

Hizb Ut-Tahrir Ideology and Strategy
HIZB UT-TAHRIR IDEOLOGY AND STRATEGY “The fierce struggle… between the Muslims and the Kuffar, has been intense ever since the dawn of Islam... It will continue in this way – a bloody struggle alongside the intellectual struggle – until the Hour comes and Allah inherits the Earth...” Hizb ut-Tahrir The Centre for Social Cohesion Houriya Ahmed & Hannah Stuart HIZB UT-TAHRIR IDEOLOGY AND STRATEGY “The fierce struggle… between the Muslims and the Kuffar, has been intense ever since the dawn of Islam... It will continue in this way – a bloody struggle alongside the intellectual struggle – until the Hour comes and Allah inherits the Earth...” Hizb ut-Tahrir The Centre for Social Cohesion Houriya Ahmed & Hannah Stuart Hizb ut-Tahrir Ideology and Strategy Houriya Ahmed and Hannah Stuart 2009 The Centre for Social Cohesion Clutha House, 10 Storey’s Gate London SW1P 3AY Tel: +44 (0)20 7222 8909 Fax: +44 (0)5 601527476 Email: [email protected] www.socialcohesion.co.uk The Centre for Social Cohesion Limited by guarantee Registered in England and Wales: No. 06609071 © The Centre for Social Cohesion, November 2009 All the Institute’s publications seek to further its objective of promoting human rights for the benefit of the public. The views expressed are those of the author, not of the Institute. Hizb ut-Tahrir: Ideology and Strategy By Houriya Ahmed and Hannah Stuart ISBN 978-0-9560013-4-4 All rights reserved The map on the front cover depicts Hizb ut-Tahrir’s vision for its Caliphate in ‘Islamic Lands’ ABOUT THE AUTHORS Houriya Ahmed is a Research Fellow at the Centre for Social Cohesion (CSC). -

Annual Report 2017
101110101011101101010011100101110101011101101010011100 10111010101110110101001 10101110001010 EDRi EUROPEAN DIGITAL RIGHTS 110101011101101010011100101011101101010011100101 10101110110101000010010100EUROPEAN010 DIGITAL001 RIGHTS11011101110101011101101100000100101101000 DEFENDING RIGHTS AND FREEDOMS ONLINE 01000111011101110101 101011101101010000100101000100011101110111010101110110110000010010110100001000111011101110101 101110101010011100 101110101011101101010011100 101011101101010000100101000100011101 101011101101010000100101000100011101110111010101110110110000010010110100001000111011101110101 101110101010011100 101110101011101101010011100 1010111011010100001001010001000111011101110101011101101100000 101011101101010000100101000100011101110111010101110110110000010010110100001000111011101110101 101110101010011100 101110101011101101010011100 10101110110101000010010100010001110111011101010111011011000001001011010000100011101110111010 101011101101010000100101000100011101110111010101110110110000010010110100001000111011101110101 101110101010011100 101110101011101101010011100 101011101101010000100101000100011101110111010101110110110000010010110100001000111011101110101 101110101010011100 101110101011101101010011100 EUROPEAN DIGITAL RIGHTS EUROPEAN DIGITAL RIGHTS ANNUAL REPORT 2017 1011011101101110111010111011111011 January 2017 – December 2017 1011011101101110111011101100110111 101011101101010000100101000100011101110111010101110110110000010010110100001000111011101110101 101110101010011100 101110101011101101010011100 101011101101010000100101000100011101110111010101110110110000010010110100001000111011101110101 -

Piracy Versus Privacy: an Analysis of Values Encoded in the Piratebrowser
International Journal of Communication 9(2015), 818–838 1932–8036/20150005 Piracy Versus Privacy: An Analysis of Values Encoded in the PirateBrowser BALÁZS BODÓ University of Amsterdam, Institute for Information Law The Netherlands The PirateBrowser is a Web browser that uses Tor privacy-enhancing technology to circumvent nationally implemented Internet filters blocking access to The Pirate Bay. This article analyzes the possible consequences of a mass influx of copyright pirates into the privacy domain. The article addresses the effects of the uptake of strong privacy technologies by pirates on copyright enforcement and on free speech and privacy technology domains. Also discussed are the norms and values reflected in the specific design choices taken by the developers of the PirateBrowser. Keywords: piracy, privacy, Tor, privacy-enhancing technologies, policy Introduction Tor (The Onion Router), “endorsed by Egyptian activists, WikiLeaks, NSA, GCHQ, Chelsea Manning, Snowden” (Dingledine & Appelbaum, 2013), is a volunteer network of computers that relays Web traffic through itself to provide anonymous, unobserved, and uncensored access to the Internet. It has about 4,000 relays and about 1,000 exit nodes. Tor users connect to the network, and their Web traffic is channeled through the internal relays to reach its final destination through one of the exit nodes. This arrangement makes the identification and surveillance of Tor users difficult. Anonymity is promised by the difficulty of tracing the Web traffic that appears on the exit node back to the individual who initiated the traffic, as long as there is a sufficient number of internal hops in between. Protection from surveillance is granted by the fact that each link in the communication chain is encrypted. -

00047-82167.Pdf (548.01
CYVA Research Corporation Abstract Data Slave Trade An Argument for the Abolition of Digital Slavery: The Intrusive & Coercive Collection and Trafficking Of Personal Information for Profit and Power For a Better Union of Social, Economic and Political Liberty, Justice and Prosperity Recognize and Secure the Mutual Rights & Responsibilities of Human-digital Existence Contact: Kevin O’Neil Chairman & CEO 858 793 8100 [email protected] This Abstract (“Abstract”) and the contents herein are owned by CYVA Research Corporation (“CYVA”, “we”, “our”, “us”, or the “Company”) and are being furnished solely for informational purposes. The information contained herein is intended to assist interested parties in making their own evaluations of CYVA. This Abstract does not purport to contain all information that a prospective investor might need or desire in properly evaluating the Company. In all cases, interested parties should conduct their own investigation and analysis of the Company. By accepting this Abstract, each recipient agrees to keep confidential the information contained herein or made available in connection with further investigation of the Company. Each recipient agrees not to reproduce or disclose any such information, in whole or part, to any individual or entity, without the prior written consent of the Company. DRAFT Abstract DRAFT Table of Contents Document Audience, Structure and Purpose 4 Preface 5 Slave Trade Metaphor 5 Network Community 6 1. Introduction: The Data Slave Trade 7 1.1. Our Human Dignity - What Dignity? 7 1.2. Data Protection Laws: Unending Catch-up Game 8 1.3. Awakening: Informational Self-determination 8 1.4. Privacy and Human Dignity Taking a Back Seat to Profits and Power: Recognition and Resistance 9 1.5. -

Culture, Media and Sport Committee
House of Commons Culture, Media and Sport Committee Future of the BBC Fourth Report of Session 2014–15 Report, together with formal minutes relating to the report Ordered by the House of Commons to be printed 10 February 2015 HC 315 INCORPORATING HC 949, SESSION 2013-14 Published on 26 February 2015 by authority of the House of Commons London: The Stationery Office Limited £0.00 The Culture, Media and Sport Committee The Culture, Media and Sport Committee is appointed by the House of Commons to examine the expenditure, administration and policy of the Department for Culture, Media and Sport and its associated public bodies. Current membership Mr John Whittingdale MP (Conservative, Maldon) (Chair) Mr Ben Bradshaw MP (Labour, Exeter) Angie Bray MP (Conservative, Ealing Central and Acton) Conor Burns MP (Conservative, Bournemouth West) Tracey Crouch MP (Conservative, Chatham and Aylesford) Philip Davies MP (Conservative, Shipley) Paul Farrelly MP (Labour, Newcastle-under-Lyme) Mr John Leech MP (Liberal Democrat, Manchester, Withington) Steve Rotheram MP (Labour, Liverpool, Walton) Jim Sheridan MP (Labour, Paisley and Renfrewshire North) Mr Gerry Sutcliffe MP (Labour, Bradford South) The following Members were also a member of the Committee during the Parliament: David Cairns MP (Labour, Inverclyde) Dr Thérèse Coffey MP (Conservative, Suffolk Coastal) Damian Collins MP (Conservative, Folkestone and Hythe) Alan Keen MP (Labour Co-operative, Feltham and Heston) Louise Mensch MP (Conservative, Corby) Mr Adrian Sanders MP (Liberal Democrat, Torbay) Mr Tom Watson MP (Labour, West Bromwich East) Powers The Committee is one of the Departmental Select Committees, the powers of which are set out in House of Commons Standing Orders, principally in SO No 152. -

The Radio 1 Breakfast Show with Nick Grimshaw Industries
AS and A LEVEL MEDIA STUDIES Factsheet Industries and audiences factsheet: The Radio 1 Breakfast Show with Nick Grimshaw Industries Production and distribution • The Radio 1 Breakfast Show with Nick Grimshaw is broadcast weekdays from 06.30-10.00 am. • The Breakfast Show has been running since 1967, but Nick Grimshaw took over as the 15th presenter in 2012. • BBC Radio 1 is broadcast on FM, DAB, Freeview, Freesat, Virgin, Sky, or online via BBC Radio Player (including via the phone or tablet app) where it can be heard live or streamed for 30 days. • It is produced by the BBC from its own studios at Broadcasting House in London. • There’s a useful BBC Academy podcast (with transcript) about how the programme is produced http://www.bbc. co.uk/academy/articles/art20170619095219011 • You can also hear what one of the producers (Fiona Hanlon) thinks when she talks about what it’s like to work on the programme: https://www.shu.ac.uk/learn-more/radio-1- breakfast-show • The music is largely playlisted – what is going to be played on daytime Radio 1 is decided by a committee; they choose around 40 records each week for repeated daytime play (A-list records get 25 plays a week, B-list 15, and C-list eight to 10). It’s explained here: http://www.bbc.co.uk/ programmes/articles/SYYQz3WNpBJFs6MrRcs0B5/how-do-i- get-my-music-played-on-radio-1 . Choices are partly guided by what’s already popular with young people online; many older artists are not included as the network is trying to keep an under-30 audience.