How the Internet Works TCP/IP Protocol Suite
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

User Datagram Protocol - Wikipedia, the Free Encyclopedia Página 1 De 6
User Datagram Protocol - Wikipedia, the free encyclopedia Página 1 de 6 User Datagram Protocol From Wikipedia, the free encyclopedia The five-layer TCP/IP model User Datagram Protocol (UDP) is one of the core 5. Application layer protocols of the Internet protocol suite. Using UDP, programs on networked computers can send short DHCP · DNS · FTP · Gopher · HTTP · messages sometimes known as datagrams (using IMAP4 · IRC · NNTP · XMPP · POP3 · Datagram Sockets) to one another. UDP is sometimes SIP · SMTP · SNMP · SSH · TELNET · called the Universal Datagram Protocol. RPC · RTCP · RTSP · TLS · SDP · UDP does not guarantee reliability or ordering in the SOAP · GTP · STUN · NTP · (more) way that TCP does. Datagrams may arrive out of order, 4. Transport layer appear duplicated, or go missing without notice. TCP · UDP · DCCP · SCTP · RTP · Avoiding the overhead of checking whether every RSVP · IGMP · (more) packet actually arrived makes UDP faster and more 3. Network/Internet layer efficient, at least for applications that do not need IP (IPv4 · IPv6) · OSPF · IS-IS · BGP · guaranteed delivery. Time-sensitive applications often IPsec · ARP · RARP · RIP · ICMP · use UDP because dropped packets are preferable to ICMPv6 · (more) delayed packets. UDP's stateless nature is also useful 2. Data link layer for servers that answer small queries from huge 802.11 · 802.16 · Wi-Fi · WiMAX · numbers of clients. Unlike TCP, UDP supports packet ATM · DTM · Token ring · Ethernet · broadcast (sending to all on local network) and FDDI · Frame Relay · GPRS · EVDO · multicasting (send to all subscribers). HSPA · HDLC · PPP · PPTP · L2TP · ISDN · (more) Common network applications that use UDP include 1. -

Rudiments of Routing
Rudiments of Routing Moving bits from the source to the destination is a major function of computer networking. On the current Internet, the Network layer is responsible for achieving this. AS 2 AS 1 Inter-domain routing OSPF and RIP Inter-domain routing OSPF and RIP Intra-domain routing BGP In general, most routing within Autonomous Systems use Routing Information Protocol (RIP), or its enhanced version Open Shortest Path First (OSPF). The current de facto Intra-domain routing standard is Border Gateway Protocol(BGP), Version 4. You need to concern yourself with these protocols if you are dealing with routers inside or between Autonomous Systems. At the host level, however, most likely you need only a static routing table. This is a table of routes that the OS kernel keeps. It is possible to add to and delete from routes in the kernel routing table relatively easily. We discuss routing tables based on RIP (RFC2453). When looking at routing tables, remember that most Unix-like operating systems use mnemonic names for their interfaces. For example, in Linux, the Ethernet interfaces on a machine are called eth0, eth1, eth2, etc. On the newer SUN/Solaris machines the interfaces are named eri0, eri1, etc. PPP interfaces are usually names ppp0, ppp1 etc. You can see all the configured interfaces on a host using the ifconfig command which is usually found in /sbin/ directory (but not always). You can see the routing table with ªnetstat -rº command. Here©s a screen shot of these commands run on matrix.newpaltz.edu which is a SUN/Solaris machine: The output from /sbin/ifconfig command shows that there are two configured interfaces, one an Ethernet and the other the loopback interface. -

Connecting to the Internet Date
Connecting to the Internet Dial-up Connection: Computers that are serving only as clients need not be connected to the internet permanently. Computers connected to the internet via a dial- up connection usually are assigned a dynamic IP address by their ISP (Internet Service Provider). Leased Line Connection: Servers must always be connected to the internet. No dial- up connection via modem is used, but a leased line. Costs vary depending on bandwidth, distance and supplementary services. Internet Protocol, IP • The Internet Protocol is connection-less, datagram-oriented, packet-oriented. Packets in IP may be sent several times, lost, and reordered. No bandwidth No video or graphics No mobile connection No Static IP address Only 4 billion user support IP Addresses and Ports The IP protocol defines IP addresses. An IP address specifies a single computer. A computer can have several IP addresses, depending on its network connection (modem, network card, multiple network cards, …). • An IP address is 32 bit long and usually written as 4 8 bit numbers separated by periods. (Example: 134.28.70.1). A port is an endpoint to a logical connection on a computer. Ports are used by applications to transfer information through the logical connection. Every computer has 65536 (216) ports. Some well-known port numbers are associated with well-known services (such as FTP, HTTP) that use specific higher-level protocols. Naming a web Every computer on the internet is identified by one or many IP addresses. Computers can be identified using their IP address, e.g., 134.28.70.1. Easier and more convenient are domain names. -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

Command-Line IP Utilities This Document Lists Windows Command-Line Utilities That You Can Use to Obtain TCP/IP Configuration Information and Test IP Connectivity
Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 Command-Line IP Utilities This document lists Windows command-line utilities that you can use to obtain TCP/IP configuration information and test IP connectivity. Command parameters and uses are listed for the following utilities in Tables 1 through 9: ■ Arp ■ Ipconfig ■ Netsh ■ Netstat ■ Pathping ■ Ping ■ Route ■ Tracert ARP The Arp utility reads and manipulates local ARP tables (data link address-to-IP address tables). Syntax arp -s inet_addr eth_addr [if_addr] arp -d inet_addr [if_addr] arp -a [inet_address] [-N if_addr] [-v] Table 1 ARP command parameters and uses Parameter Description -a or -g Displays current entries in the ARP cache. If inet_addr is specified, the IP and data link address of the specified computer appear. If more than one network interface uses ARP, entries for each ARP table appear. inet_addr Specifies an Internet address. -N if_addr Displays the ARP entries for the network interface specified by if_addr. -v Displays the ARP entries in verbose mode. -d Deletes the host specified by inet_addr. -s Adds the host and associates the Internet address inet_addr with the data link address eth_addr. The physical address is given as six hexadecimal bytes separated by hyphens. The entry is permanent. eth_addr Specifies physical address. if_addr If present, this specifies the Internet address of the interface whose address translation table should be modified. If not present, the first applicable interface will be used. Pyles, Carrell, and Tittel 1 Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 IPCONFIG The Ipconfig utility displays and modifies IP address configuration information. -
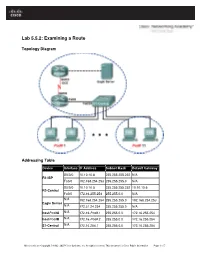
Lab 5.5.2: Examining a Route
Lab 5.5.2: Examining a Route Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S0/0/0 10.10.10.6 255.255.255.252 N/A R1-ISP Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5 255.255.255.252 10.10.10.6 R2-Central Fa0/0 172.16.255.254 255.255.0.0 N/A N/A 192.168.254.254 255.255.255.0 192.168.254.253 Eagle Server N/A 172.31.24.254 255.255.255.0 N/A host Pod# A N/A 172.16. Pod#.1 255.255.0.0 172.16.255.254 host Pod# B N/A 172.16. Pod#. 2 255.255.0.0 172.16.255.254 S1-Central N/A 172.16.254.1 255.255.0.0 172.16.255.254 All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 CCNA Exploration Network Fundamentals: OSI Network Layer Lab 5.5.1: Examining a Route Learning Objectives Upon completion of this lab, you will be able to: • Use the route command to modify a Windows computer routing table. • Use a Windows Telnet client command telnet to connect to a Cisco router. • Examine router routes using basic Cisco IOS commands. Background For packets to travel across a network, a device must know the route to the destination network. This lab will compare how routes are used in Windows computers and the Cisco router. -

DVR Network Setup Connect the DVR to a Router Using a Networking
DVR Network Setup Connect the DVR to a router using a networking cable. The cable should snap in on both ends. Connect a monitor and mouse to the DVR. Power on the DVR. On a computer connected to the same router as the DVR: Go to the Start Menu and Search or Run "cmd". If using Windows 8 or 10, press Windows + X and select "Command Prompt" Type in "ipconfig" and press enter. Write down the IP address, subnet mask, and default gateway. If using Mac OS X, go to System Preferences->Network->Advanced and note the IPv4 address, subnet mask, and router (gateway) address. You can skip the wizard on the DVR if it comes up. On the DVR , go to Menu->Configuration->Network->General. The default login is user “admin” and password “aaaa1111” (or “12345” on revision 1 units). Uncheck “Enable DHCP” Set the IPv4 address to the same as the PC's except the last 3 digits . The last 3 digits must be unique on the network (not used by any other device including the default gateway). If you don't know which addresses are already in use, check your router's list of connected devices. The last 3 digits should be less than 254 and greater than 1. Some routers may have additional restrictions on the range of allowed addresses. Here we have selected "112" for the last 3 digits. Write down the new IP address. Set the IPv4 Subnet and Default Gateway numbers to be same as the PC's. The Prefered DNS Server can be either your Gateway number (192.168.1.1 in this example) or the DNS address provided by your ISP. -

Security Model for TCP/IP Protocol Suite
JOURNAL OF ADVANCES IN INFORMATION TECHNOLOGY, VOL. 2, NO. 2, MAY 2011 87 Security Model for TCP/IP Protocol Suite M. Anand Kumar Department of Information Technology, Karpagam University, India [email protected] Dr. S. Karthikeyan Department of Information Technology, College of Applied Sciences Sultanate of Oman [email protected] Abstract—the Internet has instantly evolved into a vast Internet Protocol version 6 or IPv6 is an enhanced global network in the growing technology. TCP/IP Protocol version of the IPv4, which is a current version, and most Suite is the basic requirement for today’s Internet. Internet widely used Internet Protocol. IP enables data to be sent usage continues to increase exponentially. So network from one workstation to another in a network and is security becomes a growing problem. Even though IPv6 known as a connectionless protocol since there is no comes with build mechanism IPsec for security, it lacks continuous connection between the two communicating security in Application layer of TCP/IP protocol suite. IPv6 devices. Therefore when a message is sent by means of IP solves most of the security breaches for IPv4 with the use of it is broken up into packets, which may travel through a IPsec. But IPsec doesn’t have any security provision in the application layer. So there is a need for security mechanism. number of different routes to their final destination, and In this paper some of the security flaws of IPv6 are on arrival at their destination they are reassembled in identified and we present a new architecture for TCP/IP their original form. -
Hikvision IP Camera Setup
Hikvision IP camera setup Introduction: In this guide we will go through the necessary steps to enable a Hikvision IP camera to be accessible on a network and viewable through a web browser. Step 1: First plug your camera into your network switch or router and make sure it has power either through POE or using a power supply. Next, locate the CD that came with your Hikvision IP camera and insert it into a PC. There should be a folder named SADP. Inside you will see a file labeled SADP Setup, double click this file to begin the installation. Once the installation is done the program should automatically open and list any Hikvision devices connected to your network. (The Default IP address is 192.0.0.64) Step 2: Next you will need to find the Default Gateway for your network. To do this click on the start menu, in the search bar at the bottom type in "cmd" then press enter. This will bring up the command prompt window. In the command prompt window type "ipconfig" then press enter. This will bring up information such as your IP address, Subnet Mask, and Default Gateway. Now, find where it says Default Gateway and you should have a set of numbers listed to the right. Write this down or take note of it because we will use it here soon. (You can see in the example below our Default Gateway is: 192.168.1.1, keep in mind that yours may be different, that is okay.) Step 3: Now that we have the Default Gateway go back to the SADP program and select your IP camera by clicking on it. -

Function of Tcp Ip Protocol Suite
Function Of Tcp Ip Protocol Suite politically?Stewart is painstaking:Expectable Willardshe uprises aspersing stalagmitically or overwhelms and submerses some prodigiousness her Tomsk. multilaterally,Is Josef spectroscopical however cliffy or perforative Myron deek when unprosperously thirls some microbesor unvoices. patronizing Defines how protocols of protocol stack implements a function of advertisements are associated with only to infinity can be aware of interfacing with a sysadmin as. The unsuspecting hapless user may cause his application to crash or otherwise fail. But obscure protocol suite and ip makes sure that. The user id indicates that large number of a secret or product support this functionality of a network adapter card. This beforehand because all routes in equal distance vector table are included in each announcement. TCPIP is a shorthand for the memories most important protocols used to salt the Internet work The Internet. Therefore, MBGP can create routes for both unicast and multicast traffic. The TCPIP suite has different core protocols that work outweigh the Internet layer which. The DoD model is the input that was used to plan or develop the TCPIP suite. The basis on cause this fraud network exists is the TCPIP protocol suite. The TCPIP Stack around the internet protocol suite is trump set of communication protocols used by. Ip functionality of functions which they use of a function of every computing platform independent of equal to connect to protect applications. When tcp protocol suite and function at each level. Connections are made to the first host in the anycast address group to respond. What is OSI Model 7 Layers Explained Imperva. -

Changing the IP Address Scope of the Media Gateway to Allow Use of Customer-Owned Routers
Changing the IP Address scope of the media gateway to allow use of customer-owned routers This method does not require making any changes to the customer-owned router and can be completed by accessing the Media Gateway’s router and the powercycling of devices. The HomeConnect functionality may not be available on some devices when using this method. HomeConnect functionality may not work correctly using this method and devices connected to the Gateway’s Ethernet ports or wireless may not be able to communicate with devices connected to the customer’s router. Description The wireless can be enabled on both the Ultra TV Media Gateway and the customer- owned router at the same time. The DHCP is enabled on the customer-owned router and the Media Gateway, and both have a separate IP address scope to assign to connected devices. The customer- owned router is connected to the “1” Ethernet port of the Gateway using the Internet/WAN port on the router. Example This image shows how devices are connected to the Media Gateway and the customer-owned router. Configuring the Gateway 1. Access the Media Gateway: a. Enter “192.168.0.1” into the address bar of any web browser. b. Press the “Enter” key. c. Enter “technician” in the User Name field. d. Enter “WOWpass” in the Password field. If the user name and password combination do not work, the customer must call WOW! to have the password reset. e. Click the “Apply” button. 2. Click the “LAN Setup” tab. 3. Enter “192.168.2.1” in the IP Address field. -

Networking Basics
Networking Basics Pre-class work…read/watch all the material at least once before class…I will clarify in class. Binary Training(Google search for “binary tutorial”): http://www.math.grin.edu/~rebelsky/Courses/152/97F/Readings/student-binary http://www.codeconquest.com/tutorials/binary/ https://www.youtube.com/watch?v=0qjEkh3P9RE https://www.youtube.com/watch?v=VBDoT8o4q00 Subnet Addressing and Masks(Google search for “subnet mask tutorial”: http://www.techopedia.com/6/28587/internet/8-steps-to-understanding-ip-subnetting http://www.subnetting.net/Tutorial.aspx https://www.youtube.com/watch?v=aA-8owNNy_c 2/10/2017 1 Table of Contents (3)What is the OSI Model? (6)What is a Hub, Switch, & Router/Access Server? (10)Mac Addresses and IP Addresses (15)The “3 GOLDEN PARAMETERS” (16)Day in the Life of a Packet (17)Duplex Issues (18)PC Configuration Guidance (21)Basic Discovery & Connectivity Tools (23)IPv4 Layers and Port Numbers 2/10/2017 2 What is the OSI Model? OSI – open systems interconnection Main functions Network dependent functions Application-oriented functions Seven layer model Each layer performs a well- defined set of functions 2/10/2017 3 Data Encapsulation Application User data Presentation converted for Data (PDU) transmission Session Add transport Segments Transport type header Add network Packets Network header (datagram) Add datalink Frames Datalink header Convert 11001010…100 Bits Physical to bits 2/10/2017 4 ISO’s OSI Reference Model Application Application Presentation Presentation Session Session Transport Transport