Big O Notation Comes From”
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

CS321 Spring 2021
CS321 Spring 2021 Lecture 2 Jan 13 2021 Admin • A1 Due next Saturday Jan 23rd – 11:59PM Course in 4 Sections • Section I: Basics and Sorting • Section II: Hash Tables and Basic Data Structs • Section III: Binary Search Trees • Section IV: Graphs Section I • Sorting methods and Data Structures • Introduction to Heaps and Heap Sort What is Big O notation? • A way to approximately count algorithm operations. • A way to describe the worst case running time of algorithms. • A tool to help improve algorithm performance. • Can be used to measure complexity and memory usage. Bounds on Operations • An algorithm takes some number of ops to complete: • a + b is a single operation, takes 1 op. • Adding up N numbers takes N-1 ops. • O(1) means ‘on order of 1’ operation. • O( c ) means ‘on order of constant’. • O( n) means ‘ on order of N steps’. • O( n2) means ‘ on order of N*N steps’. How Does O(k) = O(1) O(n) = c * n for some c where c*n is always greater than n for some c. O( k ) = c*k O( 1 ) = cc * 1 let ccc = c*k c*k = c*k* 1 therefore O( k ) = c * k * 1 = ccc *1 = O(1) O(n) times for sorting algorithms. Technique O(n) operations O(n) memory use Insertion Sort O(N2) O( 1 ) Bubble Sort O(N2) O(1) Merge Sort N * log(N) O(1) Heap Sort N * log(N) O(1) Quicksort O(N2) O(logN) Memory is in terms of EXTRA memory Primary Notation Types • O(n) = Asymptotic upper bound. -
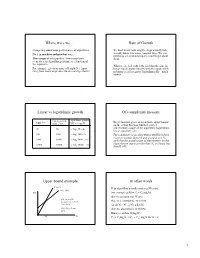
Rate of Growth Linear Vs Logarithmic Growth O() Complexity Measure
Where were we…. Rate of Growth • Comparing worst case performance of algorithms. We don't know how long the steps actually take; we only know it is some constant time. We can • Do it in machine-independent way. just lump all constants together and forget about • Time usage of an algorithm: how many basic them. steps does an algorithm perform, as a function of the input size. What we are left with is the fact that the time in • For example: given an array of length N (=input linear search grows linearly with the input, while size), how many steps does linear search perform? in binary search it grows logarithmically - much slower. Linear vs logarithmic growth O() complexity measure Linear growth: Logarithmic growth: Input size T(N) = c log N Big O notation gives an asymptotic upper bound T(N) = N* c 2 on the actual function which describes 10 10c c log 10 = 4c time/memory usage of the algorithm: logarithmic, 2 linear, quadratic, etc. 100 100c c log2 100 = 7c The complexity of an algorithm is O(f(N)) if there exists a constant factor K and an input size N0 1000 1000c c log2 1000 = 10c such that the actual usage of time/memory by the 10000 10000c c log 10000 = 16c algorithm on inputs greater than N0 is always less 2 than K f(N). Upper bound example In other words f(N)=2N If an algorithm actually makes g(N) steps, t(N)=3+N time (for example g(N) = C1 + C2log2N) there is an input size N' and t(N) is in O(N) because for all N>3, there is a constant K, such that 2N > 3+N for all N > N' , g(N) ≤ K f(N) Here, N0 = 3 and then the algorithm is in O(f(N). -

A Short Course on Approximation Theory
A Short Course on Approximation Theory N. L. Carothers Department of Mathematics and Statistics Bowling Green State University ii Preface These are notes for a topics course offered at Bowling Green State University on a variety of occasions. The course is typically offered during a somewhat abbreviated six week summer session and, consequently, there is a bit less material here than might be associated with a full semester course offered during the academic year. On the other hand, I have tried to make the notes self-contained by adding a number of short appendices and these might well be used to augment the course. The course title, approximation theory, covers a great deal of mathematical territory. In the present context, the focus is primarily on the approximation of real-valued continuous functions by some simpler class of functions, such as algebraic or trigonometric polynomials. Such issues have attracted the attention of thousands of mathematicians for at least two centuries now. We will have occasion to discuss both venerable and contemporary results, whose origins range anywhere from the dawn of time to the day before yesterday. This easily explains my interest in the subject. For me, reading these notes is like leafing through the family photo album: There are old friends, fondly remembered, fresh new faces, not yet familiar, and enough easily recognizable faces to make me feel right at home. The problems we will encounter are easy to state and easy to understand, and yet their solutions should prove intriguing to virtually anyone interested in mathematics. The techniques involved in these solutions entail nearly every topic covered in the standard undergraduate curriculum. -

Comparing the Heuristic Running Times And
Comparing the heuristic running times and time complexities of integer factorization algorithms Computational Number Theory ! ! ! New Mexico Supercomputing Challenge April 1, 2015 Final Report ! Team 14 Centennial High School ! ! Team Members ! Devon Miller Vincent Huber ! Teacher ! Melody Hagaman ! Mentor ! Christopher Morrison ! ! ! ! ! ! ! ! ! "1 !1 Executive Summary....................................................................................................................3 2 Introduction.................................................................................................................................3 2.1 Motivation......................................................................................................................3 2.2 Public Key Cryptography and RSA Encryption............................................................4 2.3 Integer Factorization......................................................................................................5 ! 2.4 Big-O and L Notation....................................................................................................6 3 Mathematical Procedure............................................................................................................6 3.1 Mathematical Description..............................................................................................6 3.1.1 Dixon’s Algorithm..........................................................................................7 3.1.2 Fermat’s Factorization Method.......................................................................7 -

February 2009
How Euler Did It by Ed Sandifer Estimating π February 2009 On Friday, June 7, 1779, Leonhard Euler sent a paper [E705] to the regular twice-weekly meeting of the St. Petersburg Academy. Euler, blind and disillusioned with the corruption of Domaschneff, the President of the Academy, seldom attended the meetings himself, so he sent one of his assistants, Nicolas Fuss, to read the paper to the ten members of the Academy who attended the meeting. The paper bore the cumbersome title "Investigatio quarundam serierum quae ad rationem peripheriae circuli ad diametrum vero proxime definiendam maxime sunt accommodatae" (Investigation of certain series which are designed to approximate the true ratio of the circumference of a circle to its diameter very closely." Up to this point, Euler had shown relatively little interest in the value of π, though he had standardized its notation, using the symbol π to denote the ratio of a circumference to a diameter consistently since 1736, and he found π in a great many places outside circles. In a paper he wrote in 1737, [E74] Euler surveyed the history of calculating the value of π. He mentioned Archimedes, Machin, de Lagny, Leibniz and Sharp. The main result in E74 was to discover a number of arctangent identities along the lines of ! 1 1 1 = 4 arctan " arctan + arctan 4 5 70 99 and to propose using the Taylor series expansion for the arctangent function, which converges fairly rapidly for small values, to approximate π. Euler also spent some time in that paper finding ways to approximate the logarithms of trigonometric functions, important at the time in navigation tables. -

Approximation Atkinson Chapter 4, Dahlquist & Bjork Section 4.5
Approximation Atkinson Chapter 4, Dahlquist & Bjork Section 4.5, Trefethen's book Topics marked with ∗ are not on the exam 1 In approximation theory we want to find a function p(x) that is `close' to another function f(x). We can define closeness using any metric or norm, e.g. Z 2 2 kf(x) − p(x)k2 = (f(x) − p(x)) dx or kf(x) − p(x)k1 = sup jf(x) − p(x)j or Z kf(x) − p(x)k1 = jf(x) − p(x)jdx: In order for these norms to make sense we need to restrict the functions f and p to suitable function spaces. The polynomial approximation problem takes the form: Find a polynomial of degree at most n that minimizes the norm of the error. Naturally we will consider (i) whether a solution exists and is unique, (ii) whether the approximation converges as n ! 1. In our section on approximation (loosely following Atkinson, Chapter 4), we will first focus on approximation in the infinity norm, then in the 2 norm and related norms. 2 Existence for optimal polynomial approximation. Theorem (no reference): For every n ≥ 0 and f 2 C([a; b]) there is a polynomial of degree ≤ n that minimizes kf(x) − p(x)k where k · k is some norm on C([a; b]). Proof: To show that a minimum/minimizer exists, we want to find some compact subset of the set of polynomials of degree ≤ n (which is a finite-dimensional space) and show that the inf over this subset is less than the inf over everything else. -

Big-O Notation
The Growth of Functions and Big-O Notation Introduction Note: \big-O" notation is a generic term that includes the symbols O, Ω, Θ, o, !. Big-O notation allows us to describe the aymptotic growth of a function f(n) without concern for i) constant multiplicative factors, and ii) lower-order additive terms. By asymptotic growth we mean the growth of the function as input variable n gets arbitrarily large. As an example, consider the following code. int sum = 0; for(i=0; i < n; i++) for(j=0; j < n; j++) sum += (i+j)/6; How much CPU time T (n) is required to execute this code as a function of program variable n? Of course, the answer will depend on factors that may be beyond our control and understanding, including the language compiler being used, the hardware of the computer executing the program, the computer's operating system, and the nature and quantity of other programs being run on the computer. However, we can say that the outer for loop iterates n times and, for each of those iterations, the inner loop will also iterate n times for a total of n2 iterations. Moreover, for each iteration will require approximately a constant number c of clock cycles to execture, where the number of clock cycles varies with each system. So rather than say \T (n) is approximately cn2 nanoseconds, for some constant c that will vary from person to person", we instead use big-O notation and write T (n) = Θ(n2) nanoseconds. This conveys that the elapsed CPU time will grow quadratically with respect to the program variable n. -

13.7 Asymptotic Notation
“mcs” — 2015/5/18 — 1:43 — page 528 — #536 13.7 Asymptotic Notation Asymptotic notation is a shorthand used to give a quick measure of the behavior of a function f .n/ as n grows large. For example, the asymptotic notation of ⇠ Definition 13.4.2 is a binary relation indicating that two functions grow at the same rate. There is also a binary relation “little oh” indicating that one function grows at a significantly slower rate than another and “Big Oh” indicating that one function grows not much more rapidly than another. 13.7.1 Little O Definition 13.7.1. For functions f; g R R, with g nonnegative, we say f is W ! asymptotically smaller than g, in symbols, f .x/ o.g.x//; D iff lim f .x/=g.x/ 0: x D !1 For example, 1000x1:9 o.x2/, because 1000x1:9=x2 1000=x0:1 and since 0:1 D D 1:9 2 x goes to infinity with x and 1000 is constant, we have limx 1000x =x !1 D 0. This argument generalizes directly to yield Lemma 13.7.2. xa o.xb/ for all nonnegative constants a<b. D Using the familiar fact that log x<xfor all x>1, we can prove Lemma 13.7.3. log x o.x✏/ for all ✏ >0. D Proof. Choose ✏ >ı>0and let x zı in the inequality log x<x. This implies D log z<zı =ı o.z ✏/ by Lemma 13.7.2: (13.28) D ⌅ b x Corollary 13.7.4. -

Binary Search
UNIT 5B Binary Search 15110 Principles of Computing, 1 Carnegie Mellon University - CORTINA Course Announcements • Sunday’s review sessions at 5‐7pm and 7‐9 pm moved to GHC 4307 • Sample exam available at the SCHEDULE & EXAMS page http://www.cs.cmu.edu/~15110‐f12/schedule.html 15110 Principles of Computing, 2 Carnegie Mellon University - CORTINA 1 This Lecture • A new search technique for arrays called binary search • Application of recursion to binary search • Logarithmic worst‐case complexity 15110 Principles of Computing, 3 Carnegie Mellon University - CORTINA Binary Search • Input: Array A of n unique elements. – The elements are sorted in increasing order. • Result: The index of a specific element called the key or nil if the key is not found. • Algorithm uses two variables lower and upper to indicate the range in the array where the search is being performed. – lower is always one less than the start of the range – upper is always one more than the end of the range 15110 Principles of Computing, 4 Carnegie Mellon University - CORTINA 2 Algorithm 1. Set lower = ‐1. 2. Set upper = the length of the array a 3. Return BinarySearch(list, key, lower, upper). BinSearch(list, key, lower, upper): 1. Return nil if the range is empty. 2. Set mid = the midpoint between lower and upper 3. Return mid if a[mid] is the key you’re looking for. 4. If the key is less than a[mid], return BinarySearch(list,key,lower,mid) Otherwise, return BinarySearch(list,key,mid,upper). 15110 Principles of Computing, 5 Carnegie Mellon University - CORTINA Example -

Function Approximation Through an Efficient Neural Networks Method
Paper ID #25637 Function Approximation through an Efficient Neural Networks Method Dr. Chaomin Luo, Mississippi State University Dr. Chaomin Luo received his Ph.D. in Department of Electrical and Computer Engineering at Univer- sity of Waterloo, in 2008, his M.Sc. in Engineering Systems and Computing at University of Guelph, Canada, and his B.Eng. in Electrical Engineering from Southeast University, Nanjing, China. He is cur- rently Associate Professor in the Department of Electrical and Computer Engineering, at the Mississippi State University (MSU). He was panelist in the Department of Defense, USA, 2015-2016, 2016-2017 NDSEG Fellowship program and panelist in 2017 NSF GRFP Panelist program. He was the General Co-Chair of 2015 IEEE International Workshop on Computational Intelligence in Smart Technologies, and Journal Special Issues Chair, IEEE 2016 International Conference on Smart Technologies, Cleveland, OH. Currently, he is Associate Editor of International Journal of Robotics and Automation, and Interna- tional Journal of Swarm Intelligence Research. He was the Publicity Chair in 2011 IEEE International Conference on Automation and Logistics. He was on the Conference Committee in 2012 International Conference on Information and Automation and International Symposium on Biomedical Engineering and Publicity Chair in 2012 IEEE International Conference on Automation and Logistics. He was a Chair of IEEE SEM - Computational Intelligence Chapter; a Vice Chair of IEEE SEM- Robotics and Automa- tion and Chair of Education Committee of IEEE SEM. He has extensively published in reputed journal and conference proceedings, such as IEEE Transactions on Neural Networks, IEEE Transactions on SMC, IEEE-ICRA, and IEEE-IROS, etc. His research interests include engineering education, computational intelligence, intelligent systems and control, robotics and autonomous systems, and applied artificial in- telligence and machine learning for autonomous systems. -

The History of Algorithmic Complexity
City University of New York (CUNY) CUNY Academic Works Publications and Research Borough of Manhattan Community College 2016 The history of Algorithmic complexity Audrey A. Nasar CUNY Borough of Manhattan Community College How does access to this work benefit ou?y Let us know! More information about this work at: https://academicworks.cuny.edu/bm_pubs/72 Discover additional works at: https://academicworks.cuny.edu This work is made publicly available by the City University of New York (CUNY). Contact: [email protected] The Mathematics Enthusiast Volume 13 Article 4 Number 3 Number 3 8-2016 The history of Algorithmic complexity Audrey A. Nasar Follow this and additional works at: http://scholarworks.umt.edu/tme Part of the Mathematics Commons Recommended Citation Nasar, Audrey A. (2016) "The history of Algorithmic complexity," The Mathematics Enthusiast: Vol. 13: No. 3, Article 4. Available at: http://scholarworks.umt.edu/tme/vol13/iss3/4 This Article is brought to you for free and open access by ScholarWorks at University of Montana. It has been accepted for inclusion in The Mathematics Enthusiast by an authorized administrator of ScholarWorks at University of Montana. For more information, please contact [email protected]. TME, vol. 13, no.3, p.217 The history of Algorithmic complexity Audrey A. Nasar1 Borough of Manhattan Community College at the City University of New York ABSTRACT: This paper provides a historical account of the development of algorithmic complexity in a form that is suitable to instructors of mathematics at the high school or undergraduate level. The study of algorithmic complexity, despite being deeply rooted in mathematics, is usually restricted to the computer science curriculum. -

A Rational Approximation to the Logarithm
A Rational Approximation to the Logarithm By R. P. Kelisky and T. J. Rivlin We shall use the r-method of Lanczos to obtain rational approximations to the logarithm which converge in the entire complex plane slit along the nonpositive real axis, uniformly in certain closed regions in the slit plane. We also provide error esti- mates valid in these regions. 1. Suppose z is a complex number, and s(l, z) denotes the closed line segment joining 1 and z. Let y be a positive real number, y ¿¿ 1. As a polynomial approxima- tion, of degree n, to log x on s(l, y) we propose p* G Pn, Pn being the set of poly- nomials with real coefficients of degree at most n, which minimizes ||xp'(x) — X|J===== max \xp'(x) — 1\ *e«(l.v) among all p G Pn which satisfy p(l) = 0. (This procedure is suggested by the observation that w = log x satisfies xto'(x) — 1=0, to(l) = 0.) We determine p* as follows. Suppose p(x) = a0 + aix + ■• • + a„xn, p(l) = 0 and (1) xp'(x) - 1 = x(x) = b0 + bix +-h bnxn . Then (2) 6o = -1 , (3) a,- = bj/j, j = 1, ■•-,«, and n (4) a0= - E Oj • .-i Thus, minimizing \\xp' — 1|| subject to p(l) = 0 is equivalent to minimizing ||«-|| among all i£P„ which satisfy —ir(0) = 1. This, in turn, is equivalent to maximiz- ing |7r(0) I among all v G Pn which satisfy ||ir|| = 1, in the sense that if vo maximizes |7r(0)[ subject to ||x|| = 1, then** = —iro/-7ro(0) minimizes ||x|| subject to —ir(0) = 1.