Binary Search
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lecture 11: Heapsort & Its Analysis
Lecture 11: Heapsort & Its Analysis Agenda: • Heap recall: – Heap: definition, property – Max-Heapify – Build-Max-Heap • Heapsort algorithm • Running time analysis Reading: • Textbook pages 127 – 138 1 Lecture 11: Heapsort (Binary-)Heap data structure (recall): • An array A[1..n] of n comparable keys either ‘≥’ or ‘≤’ • An implicit binary tree, where – A[2j] is the left child of A[j] – A[2j + 1] is the right child of A[j] j – A[b2c] is the parent of A[j] j • Keys satisfy the max-heap property: A[b2c] ≥ A[j] • There are max-heap and min-heap. We use max-heap. • A[1] is the maximum among the n keys. • Viewing heap as a binary tree, height of the tree is h = blg nc. Call the height of the heap. [— the number of edges on the longest root-to-leaf path] • A heap of height k can hold 2k —— 2k+1 − 1 keys. Why ??? Since lg n − 1 < k ≤ lg n ⇐⇒ n < 2k+1 and 2k ≤ n ⇐⇒ 2k ≤ n < 2k+1 2 Lecture 11: Heapsort Max-Heapify (recall): • It makes an almost-heap into a heap. • Pseudocode: procedure Max-Heapify(A, i) **p 130 **turn almost-heap into a heap **pre-condition: tree rooted at A[i] is almost-heap **post-condition: tree rooted at A[i] is a heap lc ← leftchild(i) rc ← rightchild(i) if lc ≤ heapsize(A) and A[lc] > A[i] then largest ← lc else largest ← i if rc ≤ heapsize(A) and A[rc] > A[largest] then largest ← rc if largest 6= i then exchange A[i] ↔ A[largest] Max-Heapify(A, largest) • WC running time: lg n. -

CS321 Spring 2021
CS321 Spring 2021 Lecture 2 Jan 13 2021 Admin • A1 Due next Saturday Jan 23rd – 11:59PM Course in 4 Sections • Section I: Basics and Sorting • Section II: Hash Tables and Basic Data Structs • Section III: Binary Search Trees • Section IV: Graphs Section I • Sorting methods and Data Structures • Introduction to Heaps and Heap Sort What is Big O notation? • A way to approximately count algorithm operations. • A way to describe the worst case running time of algorithms. • A tool to help improve algorithm performance. • Can be used to measure complexity and memory usage. Bounds on Operations • An algorithm takes some number of ops to complete: • a + b is a single operation, takes 1 op. • Adding up N numbers takes N-1 ops. • O(1) means ‘on order of 1’ operation. • O( c ) means ‘on order of constant’. • O( n) means ‘ on order of N steps’. • O( n2) means ‘ on order of N*N steps’. How Does O(k) = O(1) O(n) = c * n for some c where c*n is always greater than n for some c. O( k ) = c*k O( 1 ) = cc * 1 let ccc = c*k c*k = c*k* 1 therefore O( k ) = c * k * 1 = ccc *1 = O(1) O(n) times for sorting algorithms. Technique O(n) operations O(n) memory use Insertion Sort O(N2) O( 1 ) Bubble Sort O(N2) O(1) Merge Sort N * log(N) O(1) Heap Sort N * log(N) O(1) Quicksort O(N2) O(logN) Memory is in terms of EXTRA memory Primary Notation Types • O(n) = Asymptotic upper bound. -
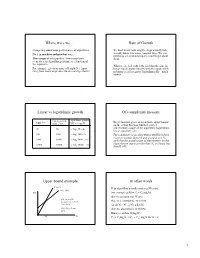
Rate of Growth Linear Vs Logarithmic Growth O() Complexity Measure
Where were we…. Rate of Growth • Comparing worst case performance of algorithms. We don't know how long the steps actually take; we only know it is some constant time. We can • Do it in machine-independent way. just lump all constants together and forget about • Time usage of an algorithm: how many basic them. steps does an algorithm perform, as a function of the input size. What we are left with is the fact that the time in • For example: given an array of length N (=input linear search grows linearly with the input, while size), how many steps does linear search perform? in binary search it grows logarithmically - much slower. Linear vs logarithmic growth O() complexity measure Linear growth: Logarithmic growth: Input size T(N) = c log N Big O notation gives an asymptotic upper bound T(N) = N* c 2 on the actual function which describes 10 10c c log 10 = 4c time/memory usage of the algorithm: logarithmic, 2 linear, quadratic, etc. 100 100c c log2 100 = 7c The complexity of an algorithm is O(f(N)) if there exists a constant factor K and an input size N0 1000 1000c c log2 1000 = 10c such that the actual usage of time/memory by the 10000 10000c c log 10000 = 16c algorithm on inputs greater than N0 is always less 2 than K f(N). Upper bound example In other words f(N)=2N If an algorithm actually makes g(N) steps, t(N)=3+N time (for example g(N) = C1 + C2log2N) there is an input size N' and t(N) is in O(N) because for all N>3, there is a constant K, such that 2N > 3+N for all N > N' , g(N) ≤ K f(N) Here, N0 = 3 and then the algorithm is in O(f(N). -

Comparing the Heuristic Running Times And
Comparing the heuristic running times and time complexities of integer factorization algorithms Computational Number Theory ! ! ! New Mexico Supercomputing Challenge April 1, 2015 Final Report ! Team 14 Centennial High School ! ! Team Members ! Devon Miller Vincent Huber ! Teacher ! Melody Hagaman ! Mentor ! Christopher Morrison ! ! ! ! ! ! ! ! ! "1 !1 Executive Summary....................................................................................................................3 2 Introduction.................................................................................................................................3 2.1 Motivation......................................................................................................................3 2.2 Public Key Cryptography and RSA Encryption............................................................4 2.3 Integer Factorization......................................................................................................5 ! 2.4 Big-O and L Notation....................................................................................................6 3 Mathematical Procedure............................................................................................................6 3.1 Mathematical Description..............................................................................................6 3.1.1 Dixon’s Algorithm..........................................................................................7 3.1.2 Fermat’s Factorization Method.......................................................................7 -

Quick Sort Algorithm Song Qin Dept
Quick Sort Algorithm Song Qin Dept. of Computer Sciences Florida Institute of Technology Melbourne, FL 32901 ABSTRACT each iteration. Repeat this on the rest of the unsorted region Given an array with n elements, we want to rearrange them in without the first element. ascending order. In this paper, we introduce Quick Sort, a Bubble sort works as follows: keep passing through the list, divide-and-conquer algorithm to sort an N element array. We exchanging adjacent element, if the list is out of order; when no evaluate the O(NlogN) time complexity in best case and O(N2) exchanges are required on some pass, the list is sorted. in worst case theoretically. We also introduce a way to approach the best case. Merge sort [4] has a O(NlogN) time complexity. It divides the 1. INTRODUCTION array into two subarrays each with N/2 items. Conquer each Search engine relies on sorting algorithm very much. When you subarray by sorting it. Unless the array is sufficiently small(one search some key word online, the feedback information is element left), use recursion to do this. Combine the solutions to brought to you sorted by the importance of the web page. the subarrays by merging them into single sorted array. 2 Bubble, Selection and Insertion Sort, they all have an O(N2) time In Bubble sort, Selection sort and Insertion sort, the O(N ) time complexity that limits its usefulness to small number of element complexity limits the performance when N gets very big. no more than a few thousand data points. -

Big-O Notation
The Growth of Functions and Big-O Notation Introduction Note: \big-O" notation is a generic term that includes the symbols O, Ω, Θ, o, !. Big-O notation allows us to describe the aymptotic growth of a function f(n) without concern for i) constant multiplicative factors, and ii) lower-order additive terms. By asymptotic growth we mean the growth of the function as input variable n gets arbitrarily large. As an example, consider the following code. int sum = 0; for(i=0; i < n; i++) for(j=0; j < n; j++) sum += (i+j)/6; How much CPU time T (n) is required to execute this code as a function of program variable n? Of course, the answer will depend on factors that may be beyond our control and understanding, including the language compiler being used, the hardware of the computer executing the program, the computer's operating system, and the nature and quantity of other programs being run on the computer. However, we can say that the outer for loop iterates n times and, for each of those iterations, the inner loop will also iterate n times for a total of n2 iterations. Moreover, for each iteration will require approximately a constant number c of clock cycles to execture, where the number of clock cycles varies with each system. So rather than say \T (n) is approximately cn2 nanoseconds, for some constant c that will vary from person to person", we instead use big-O notation and write T (n) = Θ(n2) nanoseconds. This conveys that the elapsed CPU time will grow quadratically with respect to the program variable n. -

13.7 Asymptotic Notation
“mcs” — 2015/5/18 — 1:43 — page 528 — #536 13.7 Asymptotic Notation Asymptotic notation is a shorthand used to give a quick measure of the behavior of a function f .n/ as n grows large. For example, the asymptotic notation of ⇠ Definition 13.4.2 is a binary relation indicating that two functions grow at the same rate. There is also a binary relation “little oh” indicating that one function grows at a significantly slower rate than another and “Big Oh” indicating that one function grows not much more rapidly than another. 13.7.1 Little O Definition 13.7.1. For functions f; g R R, with g nonnegative, we say f is W ! asymptotically smaller than g, in symbols, f .x/ o.g.x//; D iff lim f .x/=g.x/ 0: x D !1 For example, 1000x1:9 o.x2/, because 1000x1:9=x2 1000=x0:1 and since 0:1 D D 1:9 2 x goes to infinity with x and 1000 is constant, we have limx 1000x =x !1 D 0. This argument generalizes directly to yield Lemma 13.7.2. xa o.xb/ for all nonnegative constants a<b. D Using the familiar fact that log x<xfor all x>1, we can prove Lemma 13.7.3. log x o.x✏/ for all ✏ >0. D Proof. Choose ✏ >ı>0and let x zı in the inequality log x<x. This implies D log z<zı =ı o.z ✏/ by Lemma 13.7.2: (13.28) D ⌅ b x Corollary 13.7.4. -

COSC 311: ALGORITHMS HW1: SORTING Due Friday, September 22, 12Pm
COSC 311: ALGORITHMS HW1: SORTING Due Friday, September 22, 12pm In this assignment you will implement several sorting algorithms and compare their relative per- formance. The sorting algorithms you will consider are: 1. Insertion sort 2. Selection sort 3. Heapsort 4. Mergesort 5. Quicksort We will discuss all of these algorithms in class. You should run your experiments on the department servers, remus/romulus (if you would like to write your code on another machine that is fine, but make sure you run the actual tim- ing experiments on remus/romulus). Instructions for how to access the servers can be found on the CS department web page under “Computing Resources.” If you are a Five College stu- dent who has previously taken an Amherst CS course or who enrolled during preregistration last spring, you should have an account already set up (you may need to change your password; go to https://www.amherst.edu/help/passwords). If you don’t already have an account, you can request one at https://sysaccount.amherst.edu/sysaccount/CoursePetition.asp. It will take a day to create the new account, so please do this right away. Please type up your responses to the questions below. I recommend using LATEX, which is a type- setting language that makes it easy to make math look good. If you’re not already familiar with it, I encourage you to practice! Your tasks: 1) Theoretical predictions. Rank the five sorting algorithms in order of how you expect their run- times to compare (fastest to slowest). Your ranking should be based on the asymptotic analysis of the algorithms. -

Sorting Algorithms
Sorting Algorithms Next to storing and retrieving data, sorting of data is one of the more common algorithmic tasks, with many different ways to perform it. Whenever we perform a web search and/or view statistics at some website, the presented data has most likely been sorted in some way. In this lecture and in the following lectures we will examine several different ways of sorting. The following are some reasons for investigating several of the different algorithms (as opposed to one or two, or the \best" algorithm). • There exist very simply understood algorithms which, although for large data sets behave poorly, perform well for small amounts of data, or when the range of the data is sufficiently small. • There exist sorting algorithms which have shown to be more efficient in practice. • There are still yet other algorithms which work better in specific situations; for example, when the data is mostly sorted, or unsorted data needs to be merged into a sorted list (for example, adding names to a phonebook). 1 Counting Sort Counting sort is primarily used on data that is sorted by integer values which fall into a relatively small range (compared to the amount of random access memory available on a computer). Without loss of generality, we can assume the range of integer values is [0 : m], for some m ≥ 0. Now given array a[0 : n − 1] the idea is to define an array of lists l[0 : m], scan a, and, for i = 0; 1; : : : ; n − 1 store element a[i] in list l[v(a[i])], where v is the function that computes an array element's sorting value. -

The History of Algorithmic Complexity
City University of New York (CUNY) CUNY Academic Works Publications and Research Borough of Manhattan Community College 2016 The history of Algorithmic complexity Audrey A. Nasar CUNY Borough of Manhattan Community College How does access to this work benefit ou?y Let us know! More information about this work at: https://academicworks.cuny.edu/bm_pubs/72 Discover additional works at: https://academicworks.cuny.edu This work is made publicly available by the City University of New York (CUNY). Contact: [email protected] The Mathematics Enthusiast Volume 13 Article 4 Number 3 Number 3 8-2016 The history of Algorithmic complexity Audrey A. Nasar Follow this and additional works at: http://scholarworks.umt.edu/tme Part of the Mathematics Commons Recommended Citation Nasar, Audrey A. (2016) "The history of Algorithmic complexity," The Mathematics Enthusiast: Vol. 13: No. 3, Article 4. Available at: http://scholarworks.umt.edu/tme/vol13/iss3/4 This Article is brought to you for free and open access by ScholarWorks at University of Montana. It has been accepted for inclusion in The Mathematics Enthusiast by an authorized administrator of ScholarWorks at University of Montana. For more information, please contact [email protected]. TME, vol. 13, no.3, p.217 The history of Algorithmic complexity Audrey A. Nasar1 Borough of Manhattan Community College at the City University of New York ABSTRACT: This paper provides a historical account of the development of algorithmic complexity in a form that is suitable to instructors of mathematics at the high school or undergraduate level. The study of algorithmic complexity, despite being deeply rooted in mathematics, is usually restricted to the computer science curriculum. -

Sorting Algorithms Properties Insertion Sort Binary Search
Sorting Algorithms Properties Insertion Sort Binary Search CSE 3318 – Algorithms and Data Structures Alexandra Stefan University of Texas at Arlington 9/14/2021 1 Summary • Properties of sorting algorithms • Sorting algorithms – Insertion sort – Chapter 2 (CLRS) • Indirect sorting - (Sedgewick Ch. 6.8 ‘Index and Pointer Sorting’) • Binary Search – See the notation conventions (e.g. log2N = lg N) • Terminology and notation: – log2N = lg N – Use interchangeably: • Runtime and time complexity • Record and item 2 Sorting 3 Sorting • Sort an array, A, of items (numbers, strings, etc.). • Why sort it? – To use in binary search. – To compute rankings, statistics (min/max, top-10, top-100, median). – Check that there are no duplicates – Set intersection and union are easier to perform between 2 sorted sets – …. • We will study several sorting algorithms, – Pros/cons, behavior . • Insertion sort • If time permits, we will cover selection sort as well. 4 Properties of sorting • Stable: – It does not change the relative order of items whose keys are equal. • Adaptive: – The time complexity will depend on the input • E.g. if the input data is almost sorted, it will run significantly faster than if not sorted. • see later insertion sort vs selection sort. 5 Other aspects of sorting • Time complexity: worst/best/average • Number of data moves: copy/swap the DATA RECORDS – One data move = 1 copy operation of a complete data record – Data moves are NOT updates of variables independent of record size (e.g. loop counter ) • Space complexity: Extra Memory used – Do NOT count the space needed to hold the INPUT data, only extra space (e.g. -

1 Computational Complexity and Big-O Notation
1 Computational complexity and big-O notation References: [Ros11] The time that algorithms take to solve problems depends on the implementation, the software, the hardware, and a whole host of factors. We use big-O notation as a way of simplifying the running time of an algorithm based on the size of its input. The notation allows us to talk about algorithms at a higher level and estimate how implementations of algorithms will behave. We will use big-O notation extensively in this refresher course. We use big O notation as a way of expressing an asymptotic upper bound on a function. We say that a function f is O(g) if the rate of growth of f is less than or equal to the rate of growth of g (up to a constant). More formally: Definition 1.1. Let f, g: R ! R. We say that f is O(g) if there are positive constants c and N such that for x > N, jf(x)j ≤ cjg(x)j. Example 1.2. The number of multiplications and additions needed to multiply two n × n matrices together is n2(2n − 1), which is O(n3). To see Example 1.2, let f(n) = n2(2n − 1) and g(n) = n3. Choose N = 1 and c = 2. For n > N, f(n) = 2n3 − n2 < 2n3 = cg(n). A general advantage of big-O notation is that we can ignore the \lower order terms": k k Example 1.3. Let a0, a1, : : : ; ak be real numbers. Then f(x) = a0 + a1x + : : : akx is O(x ).