Senior Edition 2019 @Buffalobuzzz
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Virtual Currencies and Terrorist Financing : Assessing the Risks And
DIRECTORATE GENERAL FOR INTERNAL POLICIES POLICY DEPARTMENT FOR CITIZENS' RIGHTS AND CONSTITUTIONAL AFFAIRS COUNTER-TERRORISM Virtual currencies and terrorist financing: assessing the risks and evaluating responses STUDY Abstract This study, commissioned by the European Parliament’s Policy Department for Citizens’ Rights and Constitutional Affairs at the request of the TERR Committee, explores the terrorist financing (TF) risks of virtual currencies (VCs), including cryptocurrencies such as Bitcoin. It describes the features of VCs that present TF risks, and reviews the open source literature on terrorist use of virtual currencies to understand the current state and likely future manifestation of the risk. It then reviews the regulatory and law enforcement response in the EU and beyond, assessing the effectiveness of measures taken to date. Finally, it provides recommendations for EU policymakers and other relevant stakeholders for ensuring the TF risks of VCs are adequately mitigated. PE 604.970 EN ABOUT THE PUBLICATION This research paper was requested by the European Parliament's Special Committee on Terrorism and was commissioned, overseen and published by the Policy Department for Citizens’ Rights and Constitutional Affairs. Policy Departments provide independent expertise, both in-house and externally, to support European Parliament committees and other parliamentary bodies in shaping legislation and exercising democratic scrutiny over EU external and internal policies. To contact the Policy Department for Citizens’ Rights and Constitutional Affairs or to subscribe to its newsletter please write to: [email protected] RESPONSIBLE RESEARCH ADMINISTRATOR Kristiina MILT Policy Department for Citizens' Rights and Constitutional Affairs European Parliament B-1047 Brussels E-mail: [email protected] AUTHORS Tom KEATINGE, Director of the Centre for Financial Crime and Security Studies, Royal United Services Institute (coordinator) David CARLISLE, Centre for Financial Crime and Security Studies, Royal United Services Institute, etc. -

Serving Career and Technical Education Students in Pennsylvania
Career and Technical Student Organizations Serving Career and Technical Education Students in Pennsylvania 1 Dear CTSO Leaders, As the leader of a statewide trade association dedicated to the growth and development of the technology industry in Pennsylvania, I am keenly aware of the need for a highly-skilled, well-trained, and motivated workforce. At the Technology Council of Pennsylvania, we are strong advocates for advancements in and the promotion of S.T.E.M. education, as well as career and technical training, in order to prepare our young people to succeed in the 21st Century, global economy. That is why we support the work of Pennsylvania’s Career and Technical Student Organizations (CTSOs) and the critical role they play in today’s education community. For nearly 70 years, CTSOs have been able to extend teaching and learning through a variety of targeted programs, public-private partnerships and leadership development initiatives that produce technically advanced, employable students to meet the needs of this country’s diverse employer base. Today, the work of CTSOs has never been more valuable as our economy demands workers with a strong understanding of science, technology, engineering and math concepts as well as hands-on technical expertise. The co-curricular approach of CTSOs uniquely positions these organizations to enhance student skill sets and better prepare them to excel in their chosen careers. In order for Pennsylvania and the United States to not only compete, but succeed on a global stage, we need to ensure that the very technology and innovation companies that are driving this global economy have the availability of a well-qualified workforce. -

Compromised Connections
COMPROMISED CONNECTIONS OVERCOMING PRIVACY CHALLENGES OF THE MOBILE INTERNET The Universal Declaration of Human Rights, the International Covenant on Civil and Political Rights, and many other international and regional treaties recognize privacy as a fundamental human right. Privacy A WORLD OF INFORMATION underpins key values such as freedom of expression, freedom of association, and freedom of speech, IN YOUR MOBILE PHONE and it is one of the most important, nuanced and complex fundamental rights of contemporary age. For those of us who care deeply about privacy, safety and security, not only for ourselves but also for our development partners and their missions, we need to think of mobile phones as primary computers As mobile phones have transformed from clunky handheld calling devices to nifty touch-screen rather than just calling devices. We need to keep in mind that, as the storage, functionality, and smartphones loaded with apps and supported by cloud access, the networks these phones rely on capability of mobiles increase, so do the risks to users. have become ubiquitous, ferrying vast amounts of data across invisible spectrums and reaching the Can we address these hidden costs to our digital connections? Fortunately, yes! We recommend: most remote corners of the world. • Adopting device, data, network and application safety measures From a technical point-of-view, today’s phones are actually more like compact mobile computers. They are packed with digital intelligence and capable of processing many of the tasks previously confined -

Downloaded on 2017-02-12T12:57:58Z TITLE: 'Muchos Méxicos': Widening the Lens in Rulfo's Cinematic Texts
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Cork Open Research Archive Title 'Muchos Méxicos': widening the lens in Rulfo's cinematic texts Author(s) Brennan, Dylan Joseph Publication date 2015 Original citation Brennan, D. J. 2015. 'Muchos Méxicos': widening the lens in Rulfo's cinematic texts. PhD Thesis, University College Cork. Type of publication Doctoral thesis Rights © 2014, Dylan J. Brennan. http://creativecommons.org/licenses/by-nc-nd/3.0/ Embargo information No embargo required Item downloaded http://hdl.handle.net/10468/1960 from Downloaded on 2017-02-12T12:57:58Z TITLE: 'Muchos Méxicos': Widening the Lens in Rulfo's Cinematic Texts. AUTHOR: Dylan Joseph Brennan, M.A. QUALIFICATION SOUGHT: PhD INSTITUTION: National University of Ireland, Cork. (University College Cork) DEPARTMENT: Centre for Mexican Studies, Department of Hispanic Studies. MONTH AND YEAR OF SUBMISSION: Originally submitted July, 2014— resubmitted after Minor Changes in February 2015 HEAD OF DEPARTMENT: Prof. Nuala Finnegan, Director of Centre for Mexican Studies. SUPERVISOR: Prof. Nuala Finnegan, Director of Centre for Mexican Studies. TABLE OF CONTENTS 1. Widening the Focus in Rulfo's Cinematic Texts – An Introduction P.1 1.1 Texts for Cinema? – Rationale and Paramaters P.1 1.2 Methodology P.7 1.3 Muchos Méxicos P.10 1.4 Widening (not shifting) the Focus P.15 1.5 Objectives P.18 2. Inframundos and Fractured Visions – El despojo and La fórmula secreta P.22 2.1 Conception and Synopsis: An Introduction to El despojo -

2017 Scholarship Application and Information
Scholarship Application The Orrstown Bank Foundation annually awards scholarships to eligible high school seniors attending secondary schools within the core communities that Orrstown Bank serves: Pennsylvania: • Cumberland, Franklin, Lancaster, or Perry Counties – All School Districts • Dauphin County: Central Dauphin School District Derry Township School District Lower Dauphin School District Harrisburg City School District Middletown Area School District Steelton-Highspire School District Susquehanna Township School District Maryland • Washington County – All School Districts General Instructions: Complete the application in its entirety. Submit the application, along with a personal letter of introduction, three letters of recommendation, and an official high school transcript with a school seal to: Scholarship Program, c/o Orrstown Bank, 77 E. King Street, Shippensburg PA 17257, or submit electronically to: [email protected]. Applications must be postmarked or received electronically no later than Friday, March 31, 2017. STUDENT INFORMATION (Please print clearly) Student's Full Name: Mr./Ms./Mrs. First Name M.I. Last Name Address: Street # and Name City State Zip Email Address: County of Residence: Date of Birth: Telephone number: Social Security #: Name of Parent or Guardian: www.orrstown.com 1 Complete Home Address (if different from application) SCHOOL INFORMATION (Please print clearly) High School Name: Date of High School Graduation: High School Address: Street City State Zip County List academic honors: (Include an additional page, if required) The Institution(s) to which I am applying for admission: Desired major/ area of interest: SIGNATURE AND DATE (required) By signing this document, I hereby submit my application to the Orrstown Bank Foundation for a scholarship. I have read the Orrstown Bank Foundation Scholarship Guidelines and understand the terms and conditions upon which a scholarship is granted. -

Download Article (PDF)
Proceedings of the 2nd International Conference on Computer Science and Electronics Engineering (ICCSEE 2013) Trust in Cyberspace: New Information Security Paradigm R. Uzal, D. Riesco, G. Montejano N. Debnath Universidad Nacional de San Luis Department of Computer Science San Luis, Argentina Winona State University [email protected] USA {driesco, gmonte}@unsl.edu.ar [email protected] Abstract—This paper is about the differences between grids and infrastructure for destruction [3]. It is evident we traditional and new Information Security paradigms, the are facing new and very important changes in the traditional conceptual difference between “known computer viruses” and Information Security paradigm. Paradigm shift means a sophisticated Cyber Weapons, the existence of a Cyber fundamental change in an individual's or a society's view of Weapons “black market”, the differences between Cyber War, how things work in the cyberspace. For example, the shift Cyber Terrorism and Cyber Crime, the new Information from the geocentric to the heliocentric paradigm, from Security paradigm characteristics and the author’s conclusion “humors” to microbes as causes of disease, from heart to about the new Information Security paradigm to be faced. brain as the center of thinking and feeling [4]. Criminal Authors remark that recently discovered Cyber Weapons can hackers could detect some of those placed “military logic be easily described as one of the most complex IT threats ever bombs” and use them for criminal purposes. This is not a discovered. They are big and incredibly sophisticated. They pretty much redefine the notion of Information Security. theory. It is just a component of current and actual Considering the existence of a sort of Cyber Weapon black Information Security new scenarios. -

Course Selection Guide
WEST PERRY HIGH SCHOOL COURSE SELECTION GUIDE 2021-2022 1 TABLE OF CONTENTS Introduction Pages Directory 4 General Information 5 On-line Courses 8 CPAVTS Information 9 Course Areas Agriculture Education 10 Community Service Work-Based Learning 14 Driver Education 15 English 15 Foreign Language 22 Health/Physical Education 23 Mathematics 24 Science 30 Social Studies 35 Electives 42 Preparing for College 57 College Guidance College Planning Timetable Graduation Plan Template 58 2 Dear Parents and Students: The purpose of this planning guide is to provide basic information and guidance about the educational offerings available for the 2021-2022 school year at West Perry High School along with essential information to ensure our students are matriculating their way through all graduation requirements, including Keystone Exams and Chapter 339 which focuses on career exploration experiences. In addition to preparing students for Keystone Exams, the primary goal of our curriculum is to provide each student with a solid academic program that opens a variety of options beyond high school. The West Perry School District provides a diverse and comprehensive list of courses to prepare students for academic proficiency, challenging scholastic investigation, the exploration of personal interests, and rewarding careers. Both parents and students need to carefully review this planning guide and discuss all options before selecting courses. We encourage each student to make the most of the outstanding opportunities afforded by this school district and to take courses that best challenge abilities while keeping career options open. Because the course selection process can be very complex, this booklet is just one resource used to select the best program of studies. -

Alerta Integrada De Seguridad Digital N° 198-2020-PECERT
Lima, 19 de octubre de 2020 La presente Alerta Integrada de Seguridad Digital corresponde a un análisis técnico periódico realizado por el Comando Conjunto de las Fuerzas Armadas, el Ejército del Perú, la Marina de Guerra del Perú, la Fuerza Aérea del Perú, la Dirección Nacional de Inteligencia, la Policía Nacional del Perú, la Asociación de Bancos del Perú y la Secretaría de Gobierno Digital de la Presidencia del Consejo de Ministros, en el marco del Centro Nacional de Seguridad Digital. El objetivo de esta Alerta es informar a los responsables de la Seguridad de la Información de las entidades públicas y las empresas privadas sobre las amenazas en el ciberespacio para advertir las situaciones que pudieran afectar la continuidad de sus servicios en favor de la población. Las marcas y logotipos de empresas privadas y/o entidades públicas se reflejan para ilustrar la información que los ciudadanos reciben por redes sociales u otros medios y que atentan contra la confianza digital de las personas y de las mismas empresas de acuerdo a lo establecido por el Decreto de Urgencia 007-2020. La presente Alerta Integrada de Seguridad Digital es información netamente especializada para informar a las áreas técnicas de entidades y empresas. Esta información no ha sido preparada ni dirigida a ciudadanos. PECERT │Equipo de Respuestas ante Incidentes de Seguridad Digital Nacional www.gob.pe [email protected] Contenido Vulnerabilidad de ejecución remota de código de Microsoft SharePoint .................................................... 3 Campaña de phishing que utilizan Basecamp ............................................................................................... 4 Nuevo archivo adjunto Windows Update del malware Emotet. .................................................................. 5 El malware Windows “GravityRAT” ahora también se dirige a Android, macOS ......................................... -

Course Selection Guide
WEST PERRY HIGH SCHOOL COURSE SELECTION GUIDE 2017-2018 1 TABLE OF CONTENTS Introduction Pages Directory 4 General Information 5 On-line Courses 8 CPAVTS Information 9 Course Areas Agriculture Education 10 Community Service Work-Based Learning 14 Driver Education 15 English 15 Foreign Language 21 Health/Physical Education 22 Mathematics 23 Science 29 Social Studies 33 Electives 40 Preparing for College 54 College Guidance College Planning Timetable Graduation Plan Template 55 2 Dear Parents and Students: The purpose of this planning guide is to provide basic information and guidance about the educational offerings available for the 2017-2018 school year at West Perry High School along with essential information to ensure our students are matriculating their way through all graduation requirements, including Keystone Exams. In addition to preparing students for Keystone Exams, the primary goal of our curriculum is to provide each student with a solid academic program that opens a variety of options beyond high school. The West Perry School District provides a diverse and comprehensive list of courses to prepare students for academic proficiency, challenging scholastic investigation, the exploration of personal interests, and rewarding careers. Both parents and students need to carefully review this planning guide and discuss all options before selecting courses. We encourage each student to make the most of the outstanding opportunities afforded by this school district and to take courses that best challenge abilities while keeping career options open. Because the course selection process can be very complex, this booklet is just one resource used to select the best program of studies. Please take advantage of all available resources, such as our guidance counselors, teachers, and administrators. -
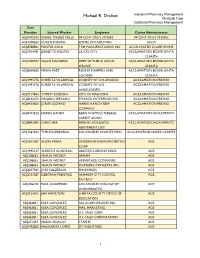
Additional Case Information
Michael R. Drobot Industrial Pharmacy Management MediLab Corp California Pharmacy Management Case Number Injured Worker Employer Claims Administrator ADJ7472102 ISMAEL TORRES VALLE 99 CENT ONLY STORES 99 CENT ONLY STORES ADJ1308567 CURTIS RIGGINS EMPIRE DISTRIBUTORS ACCA ADJ8768841 MARTIN AVILA TRM MANUFACTURING INC ACCELERATED CLAIMS IRVINE ADJ7014781 JEANETTE WILSON LA COUNTY ACCLAMATION 802108 SANTA CLARITA ADJ7200937 SUSAN NAVARRO DEPT OF PUBLIC SOCIAL ACCLAMATION 802108 SANTA SERVICE CLARITA ADJ8009655 MARIA PAEZ RUSKIN DAMPERS AND ACCLAMATION 802108 SANTA LOUVERS CLARITA ADJ1993776 ROBERTA VILLARREAL COUNTY OF LOS ANGELES ACCLAMATION FRESNO ADJ1993776 ROBERTA VILLARREAL COUNTY OF LOS ACCLAMATION FRESNO ANGELES/DPSS ADJ7117844 TOMMY ROBISON CITY OF MARICOPA ACCLAMATION FRESNO ADJ8162473 ONORIO SERRANO ESPARZA ENTERPRISES INC ACCLAMATION FRESNO ADJ8420600 JORGE LOZANO HARRIS RANCH BEEF ACCLAMATION FRESNO COMPANY ADJ8473212 DAREN HANDY KERN SCHOOLS FEDERAL ACCLAMATION SACRAMENTO CREDIT UNION ADJ8845092 CHAO HER FRESNO MOSQUITO ACCLAMATION SACRAMENTO ABATEMENT DIST ADJ1361532 THELMA JENNINGS LOS ANGELES COUNTY/DPSS ACCLAMATION SANTA CLARITA ADJ1611037 ALICIA MORA ANDERSON BARROWS METALS ACE CORP ADJ1995137 ALBERTO GUNDRAN ABLESTIK LABORATORIES ACE ADJ208633 SHAUN WIDNEY AMPAM ACE ADJ208633 SHAUN WIDNEY AMPAM RCR COMPANIES ACE ADJ208633 SHAUN WIDNEY PLUMBING CONCEPTS INC ACE ADJ2237965 JOSE CALDERON FMI EXPRESS ACE ADJ2353287 DEBORAH PRENTICE ANAHEIM CITY SCHOOL ACE DISTRICT ADJ246218 PAUL LIGAMMARI LOS ANGELES COLLEGE OF ACE CHIROPRACTIC -

MEXICAN FILM BULLETIN, Vol
THE MEXICAN FILM BULLETIN, Vol. 12 No. 8 (December 2006) The Mexican Film Bulletin Volume 12, Number 8 DeceDecembermber 2006 Miguel Aceves Mejía 19151915----20062006 Miguel Aceves Mejía is survived by his wife and son. Miguel Aceves Mejía died of pneumonia and Filmography bronchitis on 6 November 2006. Aceves Mejía, whose 1940: Rancho alegre (as part of the Trío Los Porteños) trademarks were a streak of white in his black hair and the 1947: De pecado en pecado (dubs José Pulido's singing), vocal style which earned him the nickname of "El Falsete Pecadora de Oro" or "El Rey del Falsete," was born in Chihuahua in 1950: Donde nacen los pobres November 1915 (some sources cite 1917), and first began 1951: Ella y yo, Por querer a una mujer, Nosotras las singing professionally in the 1930s in northern Mexico. sirvientas Towards the end of 1952: La mentira, Cartas a Ufemia the decade, he and 1953: Camelia two other men 1954: A los cuatro vientos formed the "Trío Los 1955: Música de siempre, Hay ángeles con espuelas, El Porteños," Águila Negra en El Vengador Solitario, Tú y las nubes, performing various Historia de un amor genres of music (the 1956: Música de siempre, Tú y la mentira, Que seas feliz!, team appeared in Que me toquen Las Golodrinas Rancho alegre in 1957: El Ciclón, Cuatro copas, Bajo el cielo de México, 1940, Aceves Rogaciano el huapangero, Guitarras de medianoche, La Mejía's film debut). feria de San Marcos, El gallo colorado, Amor se dice In the mid-1940s cantando Aceves Mejía 1958: Échame a mi la culpa!, Mi niño, mi caballo, -

Pegaso Revista Mensual M 'Ntkvideo— Uruguay
PEGASO REVISTA MENSUAL M 'NTKVIDEO— URUGUAY DIRECTOREBt Rabia de Breele-Joe* Baria Salgada m « i$2i. Nta. xxa.-Afc ni. Tres mil siglos de modas femeninas ■ Conferencia con proyecciones luminosa», leída a la Sociedad aEntre Nous», el 22 de Junio de 1MB Rompiendo el ciclo brillante de los oradores de alto vuelo que han dado a ustedes el hábito do oir :a frase; .galana que engarza el pensar profundo, y tal vez, como entremés preparatorio de temas trascendentales, un amable pedido de “ Entre Nous’’, explica la excepción qu e, significa esta charla, que deseo corta por temor de no hacerla amena., Condensar en breves momentos la evolución de la moda femenina, remontándose a través de los tiempos desdo las creaciones de Mad&me Paquin, hasta el traje... que no era traje, es seguramente ardua tarea, y las dificultades crecen si se detienen ustedes un instante a pensar en la fragilidad y sutileza del tema. L a moda, j Quién se atrevería a definirla 1 Muoho he temido que mis rudas manos de cirujano, maculasen las aterciopeladas alas de tan brillante mariposa; grande es, pues, mi audacia, pero a tenerla me han inducido la amistosa presión moral de sus actuales direotrices, y la esperanza de despertar en. ustedes el más encan tador de los defectos, femeninos: la curiosidad- i No me perdonarán ustedes, acaso, «er pesado, tal vez en demasía, si les doy la ocasión de reirse un rato de las cosas feas, con que de tiempo en tiempo la mujer transformó su divina silueta, o de admirar las creacio nes que subrayando su belleza oliéronle más anuas para vencer al hombre en esa desigual lucliá entre nuestra iusticidad y su viveza, entre la maza de Hércules y el abanico de Ninón de Léñelos? ¡Pobreeitos los hombres 1 Mientras el mundo dure, entre el cejijunto y barbudo Padre Eterno y la rubia Anadiomena retorciendo su caibeillera al nacer entre jas espumas del mar Egeo, sólo vacilarán los Bienaven turados a quienes se asegura el primer puesto en el reino de los cielos.