38 Toward Engineering a Secure Android Ecosystem: a Survey of Existing Techniques
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Kernel Report
The kernel report (ELC 2012 edition) Jonathan Corbet LWN.net [email protected] The Plan Look at a year's worth of kernel work ...with an eye toward the future Starting off 2011 2.6.37 released - January 4, 2011 11,446 changes, 1,276 developers VFS scalability work (inode_lock removal) Block I/O bandwidth controller PPTP support Basic pNFS support Wakeup sources What have we done since then? Since 2.6.37: Five kernel releases have been made 59,000 changes have been merged 3069 developers have contributed to the kernel 416 companies have supported kernel development February As you can see in these posts, Ralink is sending patches for the upstream rt2x00 driver for their new chipsets, and not just dumping a huge, stand-alone tarball driver on the community, as they have done in the past. This shows a huge willingness to learn how to deal with the kernel community, and they should be strongly encouraged and praised for this major change in attitude. – Greg Kroah-Hartman, February 9 Employer contributions 2.6.38-3.2 Volunteers 13.9% Wolfson Micro 1.7% Red Hat 10.9% Samsung 1.6% Intel 7.3% Google 1.6% unknown 6.9% Oracle 1.5% Novell 4.0% Microsoft 1.4% IBM 3.6% AMD 1.3% TI 3.4% Freescale 1.3% Broadcom 3.1% Fujitsu 1.1% consultants 2.2% Atheros 1.1% Nokia 1.8% Wind River 1.0% Also in February Red Hat stops releasing individual kernel patches March 2.6.38 released – March 14, 2011 (9,577 changes from 1198 developers) Per-session group scheduling dcache scalability patch set Transmit packet steering Transparent huge pages Hierarchical block I/O bandwidth controller Somebody needs to get a grip in the ARM community. -

Virtual Currencies and Terrorist Financing : Assessing the Risks And
DIRECTORATE GENERAL FOR INTERNAL POLICIES POLICY DEPARTMENT FOR CITIZENS' RIGHTS AND CONSTITUTIONAL AFFAIRS COUNTER-TERRORISM Virtual currencies and terrorist financing: assessing the risks and evaluating responses STUDY Abstract This study, commissioned by the European Parliament’s Policy Department for Citizens’ Rights and Constitutional Affairs at the request of the TERR Committee, explores the terrorist financing (TF) risks of virtual currencies (VCs), including cryptocurrencies such as Bitcoin. It describes the features of VCs that present TF risks, and reviews the open source literature on terrorist use of virtual currencies to understand the current state and likely future manifestation of the risk. It then reviews the regulatory and law enforcement response in the EU and beyond, assessing the effectiveness of measures taken to date. Finally, it provides recommendations for EU policymakers and other relevant stakeholders for ensuring the TF risks of VCs are adequately mitigated. PE 604.970 EN ABOUT THE PUBLICATION This research paper was requested by the European Parliament's Special Committee on Terrorism and was commissioned, overseen and published by the Policy Department for Citizens’ Rights and Constitutional Affairs. Policy Departments provide independent expertise, both in-house and externally, to support European Parliament committees and other parliamentary bodies in shaping legislation and exercising democratic scrutiny over EU external and internal policies. To contact the Policy Department for Citizens’ Rights and Constitutional Affairs or to subscribe to its newsletter please write to: [email protected] RESPONSIBLE RESEARCH ADMINISTRATOR Kristiina MILT Policy Department for Citizens' Rights and Constitutional Affairs European Parliament B-1047 Brussels E-mail: [email protected] AUTHORS Tom KEATINGE, Director of the Centre for Financial Crime and Security Studies, Royal United Services Institute (coordinator) David CARLISLE, Centre for Financial Crime and Security Studies, Royal United Services Institute, etc. -

Parks, Recreation and Open Space Plan
CITY OF KENMORE PARKS, RECREATION AND OPEN SPACE PLAN February 24, 2020 Resolution 20-334 VIA EMAIL March 9, 2020 Lauri Anderson Principal Planner City of Kenmore Re: RCO grant program planning eligibility Dear Ms. Anderson: Thank you for submitting the City of Kenmore 2020 Parks, Recreation & Open Space Plan to the Recreation and Conservation Office (RCO). I am pleased to inform you that the Plan meets the planning requirements as specified in Manual 2, Planning Policies and Guidelines. This includes grant program planning eligibility in the following categories: • Land and Water Conservation Fund • Washington Wildlife and Recreation Program: Habitat conservation and recreation grants • Boating Facilities Program • Nonhighway and Off-Road Vehicle Activities Program: Trails Planning eligibility is granted for six years and will expire February 24, 2026. Please note that to retain grant eligibility in future years, RCO must be notified of any major amendments as they occur. An incorrect or incomplete plan may impact your project’s evaluation. Please let me know if you have any further planning questions, [email protected]. Your point of contact for grant applications is [email protected]. Sincerely, Katie Knight Pruit Planning Specialist Table of Contents CHAPTER 1 INTRODUCTION 1 Planning Context 2 Planning Process 8 CHAPTER 2 EXISTING INVENTORY 12 Park Classification & Service Area 15 Park & Recreation Programming 23 Natural Resources 25 CHAPTER 3 VISION, GOALS & POLICY SUPPORT 26 Guiding Fundamentals 27 Vision & Goals 30 Objectives -

Rootless Containers with Podman and Fuse-Overlayfs
CernVM Workshop 2019 (4th June 2019) Rootless containers with Podman and fuse-overlayfs Giuseppe Scrivano @gscrivano Introduction 2 Rootless Containers • “Rootless containers refers to the ability for an unprivileged user (i.e. non-root user) to create, run and otherwise manage containers.” (https://rootlesscontaine.rs/ ) • Not just about running the container payload as an unprivileged user • Container runtime runs also as an unprivileged user 3 Don’t confuse with... • sudo podman run --user foo – Executes the process in the container as non-root – Podman and the OCI runtime still running as root • USER instruction in Dockerfile – same as above – Notably you can’t RUN dnf install ... 4 Don’t confuse with... • podman run --uidmap – Execute containers as a non-root user, using user namespaces – Most similar to rootless containers, but still requires podman and runc to run as root 5 Motivation of Rootless Containers • To mitigate potential vulnerability of container runtimes • To allow users of shared machines (e.g. HPC) to run containers without the risk of breaking other users environments • To isolate nested containers 6 Caveat: Not a panacea • Although rootless containers could mitigate these vulnerabilities, it is not a panacea , especially it is powerless against kernel (and hardware) vulnerabilities – CVE 2013-1858, CVE-2015-1328, CVE-2018-18955 • Castle approach : it should be used in conjunction with other security layers such as seccomp and SELinux 7 Podman 8 Rootless Podman Podman is a daemon-less alternative to Docker • $ alias -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Systematization of Vulnerability Discovery Knowledge: Review
Systematization of Vulnerability Discovery Knowledge Review Protocol Nuthan Munaiah and Andrew Meneely Department of Software Engineering Rochester Institute of Technology Rochester, NY 14623 {nm6061,axmvse}@rit.edu February 12, 2019 1 Introduction As more aspects of our daily lives depend on technology, the software that supports this technology must be secure. We, as users, almost subconsciously assume the software we use to always be available to serve our requests while preserving the confidentiality and integrity of our information. Unfortunately, incidents involving catastrophic software vulnerabilities such as Heartbleed (in OpenSSL), Stagefright (in Android), and EternalBlue (in Windows) have made abundantly clear that software, like other engineered creations, is prone to mistakes. Over the years, Software Engineering, as a discipline, has recognized the potential for engineers to make mistakes and has incorporated processes to prevent such mistakes from becoming exploitable vulnerabilities. Developers leverage a plethora of processes, techniques, and tools such as threat modeling, static and dynamic analyses, unit/integration/fuzz/penetration testing, and code reviews to engineer secure software. These practices, while effective at identifying vulnerabilities in software, are limited in their ability to describe the engineering failures that may have led to the introduction of vulnerabilities. Fortunately, as researchers propose empirically-validated metrics to characterize historical vulnerabilities, the factors that may have led to the introduction of vulnerabilities emerge. Developers must be made aware of these factors to help them proactively consider security implications of the code that they contribute. In other words, we want developers to think like an attacker (i.e. inculcate an attacker mindset) to proactively discover vulnerabilities. -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE of CONTENTS 2016 Internet Security Threat Report 2
Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE OF CONTENTS 2016 Internet Security Threat Report 2 CONTENTS 4 Introduction 21 Tech Support Scams Go Nuclear, 39 Infographic: A New Zero-Day Vulnerability Spreading Ransomware Discovered Every Week in 2015 5 Executive Summary 22 Malvertising 39 Infographic: A New Zero-Day Vulnerability Discovered Every Week in 2015 8 BIG NUMBERS 23 Cybersecurity Challenges For Website Owners 40 Spear Phishing 10 MOBILE DEVICES & THE 23 Put Your Money Where Your Mouse Is 43 Active Attack Groups in 2015 INTERNET OF THINGS 23 Websites Are Still Vulnerable to Attacks 44 Infographic: Attackers Target Both Large and Small Businesses 10 Smartphones Leading to Malware and Data Breaches and Mobile Devices 23 Moving to Stronger Authentication 45 Profiting from High-Level Corporate Attacks and the Butterfly Effect 10 One Phone Per Person 24 Accelerating to Always-On Encryption 45 Cybersecurity, Cybersabotage, and Coping 11 Cross-Over Threats 24 Reinforced Reassurance with Black Swan Events 11 Android Attacks Become More Stealthy 25 Websites Need to Become Harder to 46 Cybersabotage and 12 How Malicious Video Messages Could Attack the Threat of “Hybrid Warfare” Lead to Stagefright and Stagefright 2.0 25 SSL/TLS and The 46 Small Business and the Dirty Linen Attack Industry’s Response 13 Android Users under Fire with Phishing 47 Industrial Control Systems and Ransomware 25 The Evolution of Encryption Vulnerable to Attacks 13 Apple iOS Users Now More at Risk than 25 Strength in Numbers 47 Obscurity is No Defense -

Compromised Connections
COMPROMISED CONNECTIONS OVERCOMING PRIVACY CHALLENGES OF THE MOBILE INTERNET The Universal Declaration of Human Rights, the International Covenant on Civil and Political Rights, and many other international and regional treaties recognize privacy as a fundamental human right. Privacy A WORLD OF INFORMATION underpins key values such as freedom of expression, freedom of association, and freedom of speech, IN YOUR MOBILE PHONE and it is one of the most important, nuanced and complex fundamental rights of contemporary age. For those of us who care deeply about privacy, safety and security, not only for ourselves but also for our development partners and their missions, we need to think of mobile phones as primary computers As mobile phones have transformed from clunky handheld calling devices to nifty touch-screen rather than just calling devices. We need to keep in mind that, as the storage, functionality, and smartphones loaded with apps and supported by cloud access, the networks these phones rely on capability of mobiles increase, so do the risks to users. have become ubiquitous, ferrying vast amounts of data across invisible spectrums and reaching the Can we address these hidden costs to our digital connections? Fortunately, yes! We recommend: most remote corners of the world. • Adopting device, data, network and application safety measures From a technical point-of-view, today’s phones are actually more like compact mobile computers. They are packed with digital intelligence and capable of processing many of the tasks previously confined -

History and Evolution of the Android OS
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Springer - Publisher Connector CHAPTER 1 History and Evolution of the Android OS I’m going to destroy Android, because it’s a stolen product. I’m willing to go thermonuclear war on this. —Steve Jobs, Apple Inc. Android, Inc. started with a clear mission by its creators. According to Andy Rubin, one of Android’s founders, Android Inc. was to develop “smarter mobile devices that are more aware of its owner’s location and preferences.” Rubin further stated, “If people are smart, that information starts getting aggregated into consumer products.” The year was 2003 and the location was Palo Alto, California. This was the year Android was born. While Android, Inc. started operations secretly, today the entire world knows about Android. It is no secret that Android is an operating system (OS) for modern day smartphones, tablets, and soon-to-be laptops, but what exactly does that mean? What did Android used to look like? How has it gotten where it is today? All of these questions and more will be answered in this brief chapter. Origins Android first appeared on the technology radar in 2005 when Google, the multibillion- dollar technology company, purchased Android, Inc. At the time, not much was known about Android and what Google intended on doing with it. Information was sparse until 2007, when Google announced the world’s first truly open platform for mobile devices. The First Distribution of Android On November 5, 2007, a press release from the Open Handset Alliance set the stage for the future of the Android platform. -

Tutorial: Setup for Android Development
Tutorial: Setup for Android Development Adam C. Champion, Ph.D. CSE 5236: Mobile Application Development Autumn 2019 Based on material from C. Horstmann [1], J. Bloch [2], C. Collins et al. [4], M.L. Sichitiu (NCSU), V. Janjic (Imperial College London), CSE 2221 (OSU), and other sources 1 Outline • Getting Started • Android Programming 2 Getting Started (1) • Need to install Java Development Kit (JDK) (not Java Runtime Environment (JRE)) to write Android programs • Download JDK for your OS: https://adoptopenjdk.net/ * • Alternatively, for OS X, Linux: – OS X: Install Homebrew (http://brew.sh) via Terminal, – Linux: • Debian/Ubuntu: sudo apt install openjdk-8-jdk • Fedora/CentOS: yum install java-1.8.0-openjdk-devel * Why OpenJDK 8? Oracle changed Java licensing (commercial use costs $$$); Android SDK tools require version 8. 3 Getting Started (2) • After installing JDK, download Android SDK from http://developer.android.com • Simplest: download and install Android Studio bundle (including Android SDK) for your OS • Alternative: brew cask install android- studio (Mac/Homebrew) • We’ll use Android Studio with SDK included (easiest) 4 Install! 5 Getting Started (3) • Install Android Studio directly (Windows, Mac); unzip to directory android-studio, then run ./android-studio/bin/studio64.sh (Linux) 6 Getting Started (4) • Strongly recommend testing Android Studio menu → Preferences… or with real Android device File → Settings… – Android emulator: slow – Faster emulator: Genymotion [14], [15] – Install USB drivers for your Android device! • Bring up Android SDK Manager – Install Android 5.x–8.x APIs, Google support repository, Google Play services – Don’t worry about non-x86 Now you’re ready for Android development! system images 7 Outline • Getting Started • Android Programming 8 Introduction to Android • Popular mobile device Mobile OS Market Share OS: 73% of worldwide Worldwide (Jul. -
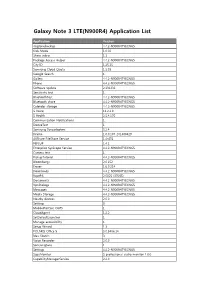
Galaxy Note 3 LTE(N900R4) Application List
Galaxy Note 3 LTE(N900R4) Application List Application Version ringtonebackup 4.4.2-N900R4TYECNG5 Kids Mode 1.0.02 Share video 1.1 Package Access Helper 4.4.2-N900R4TYECNG5 City ID 1.25.15 Samsung Cloud Quota 1.5.03 Google Search 1 Gallery 4.4.2-N900R4TYECNG5 Phone 4.4.2-N900R4TYECNG5 Software update 2.131231 Sensitivity test 1 BluetoothTest 4.4.2-N900R4TYECNG5 Bluetooth share 4.4.2-N900R4TYECNG5 Calendar storage 4.4.2-N900R4TYECNG5 S Voice 11.2.2.0 S Health 2.5.4.170 Communication Notifications 1 DeviceTest 1 Samsung Syncadapters 5.2.4 Drama 1.0.0.107_201400429 AllShare FileShare Service 1.4r476 PEN.UP 1.4.1 Enterprise SysScope Service 4.4.2-N900R4TYECNG5 Camera test 1 PickupTutorial 4.4.2-N900R4TYECNG5 Bloomberg+ 2.0.152 Eraser 1.6.0.214 Downloads 4.4.2-N900R4TYECNG5 RootPA 2.0025 (37085) Documents 4.4.2-N900R4TYECNG5 VpnDialogs 4.4.2-N900R4TYECNG5 Messages 4.4.2-N900R4TYECNG5 Media Storage 4.4.2-N900R4TYECNG5 Nearby devices 2.0.0 Settings 3 MobilePrintSvc_CUPS 1 CloudAgent 1.2.2 SetDefaultLauncher 1 Manage accessibility 1 Setup Wizard 1.3 POLARIS Office 5 5.0.3406.14 Idea Sketch 3 Voice Recorder 2.0.0 SamsungSans 1 Settings 4.4.2-N900R4TYECNG5 SapaMonitor S professional audio monitor 1.0.0 CapabilityManagerService 2.4.0 S Note 3.1.0 Samsung Link 1.8.1904 Samsung WatchON Video 14062601.1.21.78 Street View 1.8.1.2 Alarm 1 PageBuddyNotiSvc 1 Favorite Contacts 4.4.2-N900R4TYECNG5 Google Search 3.4.16.1149292.arm KNOX 2.0.0 Exchange services 4.2 GestureService 1 Weather 140211.01 Samsung Print Service Plugin 1.4.140410 Tasks provider 4.4.2-N900R4TYECNG5