Cryptocurrencies Without Proof of Work
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

American Bar Association Business Law Section Committee on Derivatives and Futures Law
American Bar Association Business Law Section Committee on Derivatives and Futures Law Winter Meeting 2018 Naples, Florida Friday, January 19, 2018 10:15 a.m. to 11:30 a.m. NEW PRODUCTS / FINANCIAL TECHNOLOGY Moderator for the Program: Conrad G. Bahlke, Willkie Farr &Gallagher LLP Speakers: Geoffrey F. Aronow, Sidley Austin LLP Debra W. Cook, Depository Trust & Clearing Corporation Katherine Cooper, Law Office of Katherine Cooper Isabelle Corbett, R3 David Lucking, Allen & Overy LLP Brian D. Quintenz, Commissioner, U.S. Commodity Futures Trading Commission ABA BUSINESS LAW SECTION DERIVATIVES & FUTURES LAW COMMITTEE 2018 WINTER MEETING NEW PRODUCTS / FIN TECH PANEL 2017 Developments in US Regulation of Virtual Currencies and Related Products: Yin and Yang January 5, 2018 By Katherine Cooper1 2017 was a year during which virtual currencies began to move into the mainstream financial markets. This generated significant legal and regulatory developments as U.S. regulators faced numerous novel products attempting to blend the old with the new. Although facing so many novel issues, the regulators’ responses tell a familiar story of the struggle to balance the yin of customer protection with the yang of encouraging financial innovation and competition. Below is a summary of 2017 developments from the SEC, CFTC, OCC, FinCEN and the States. I. Securities and Exchange Commission a. Bitcoin Exchange-Traded Products A number of sponsors of proposed Bitcoin exchange traded products had applications for approval pending before the Securities and Exchange Commission at the beginning of 2017. In March 2017, the SEC rejected a proposal backed by Tyler and Cameron Winklevoss.2 The Bats Exchange proposed a rule amendment which would list the shares of the Winklevoss Bitcoin Trust for trading. -

Rev. Rul. 2019-24 ISSUES (1) Does a Taxpayer Have Gross Income Under
26 CFR 1.61-1: Gross income. (Also §§ 61, 451, 1011.) Rev. Rul. 2019-24 ISSUES (1) Does a taxpayer have gross income under § 61 of the Internal Revenue Code (Code) as a result of a hard fork of a cryptocurrency the taxpayer owns if the taxpayer does not receive units of a new cryptocurrency? (2) Does a taxpayer have gross income under § 61 as a result of an airdrop of a new cryptocurrency following a hard fork if the taxpayer receives units of new cryptocurrency? BACKGROUND Virtual currency is a digital representation of value that functions as a medium of exchange, a unit of account, and a store of value other than a representation of the United States dollar or a foreign currency. Foreign currency is the coin and paper money of a country other than the United States that is designated as legal tender, circulates, and is customarily used and accepted as a medium of exchange in the country of issuance. See 31 C.F.R. § 1010.100(m). - 2 - Cryptocurrency is a type of virtual currency that utilizes cryptography to secure transactions that are digitally recorded on a distributed ledger, such as a blockchain. Units of cryptocurrency are generally referred to as coins or tokens. Distributed ledger technology uses independent digital systems to record, share, and synchronize transactions, the details of which are recorded in multiple places at the same time with no central data store or administration functionality. A hard fork is unique to distributed ledger technology and occurs when a cryptocurrency on a distributed ledger undergoes a protocol change resulting in a permanent diversion from the legacy or existing distributed ledger. -

Crypto-Asset Markets: Potential Channels for Future Financial Stability
Crypto-asset markets Potential channels for future financial stability implications 10 October 2018 The Financial Stability Board (FSB) is established to coordinate at the international level the work of national financial authorities and international standard-setting bodies in order to develop and promote the implementation of effective regulatory, supervisory and other financial sector policies. Its mandate is set out in the FSB Charter, which governs the policymaking and related activities of the FSB. These activities, including any decisions reached in their context, shall not be binding or give rise to any legal rights or obligations under the FSB’s Articles of Association. Contacting the Financial Stability Board Sign up for e-mail alerts: www.fsb.org/emailalert Follow the FSB on Twitter: @FinStbBoard E-mail the FSB at: [email protected] Copyright © 2018 Financial Stability Board. Please refer to: www.fsb.org/terms_conditions/ Contents Executive Summary ................................................................................................................... 1 1. Introduction ......................................................................................................................... 3 2. Primary risks in crypto-asset markets ................................................................................. 5 2.1 Market liquidity risks ............................................................................................... 5 2.2 Volatility risks ......................................................................................................... -

Asymmetric Proof-Of-Work Based on the Generalized Birthday Problem
Equihash: Asymmetric Proof-of-Work Based on the Generalized Birthday Problem Alex Biryukov Dmitry Khovratovich University of Luxembourg University of Luxembourg [email protected] [email protected] Abstract—The proof-of-work is a central concept in modern Long before the rise of Bitcoin it was realized [20] that cryptocurrencies and denial-of-service protection tools, but the the dedicated hardware can produce a proof-of-work much requirement for fast verification so far made it an easy prey for faster and cheaper than a regular desktop or laptop. Thus the GPU-, ASIC-, and botnet-equipped users. The attempts to rely on users equipped with such hardware have an advantage over memory-intensive computations in order to remedy the disparity others, which eventually led the Bitcoin mining to concentrate between architectures have resulted in slow or broken schemes. in a few hardware farms of enormous size and high electricity In this paper we solve this open problem and show how to consumption. An advantage of the same order of magnitude construct an asymmetric proof-of-work (PoW) based on a compu- is given to “owners” of large botnets, which nowadays often tationally hard problem, which requires a lot of memory to gen- accommodate hundreds of thousands of machines. For prac- erate a proof (called ”memory-hardness” feature) but is instant tical DoS protection, this means that the early TLS puzzle to verify. Our primary proposal Equihash is a PoW based on the schemes [8], [17] are no longer effective against the most generalized birthday problem and enhanced Wagner’s algorithm powerful adversaries. -

Initial Coin Offerings: Financing Growth with Cryptocurrency Token
Initial Coin Offerings: Financing Growth with Cryptocurrency Token Sales Sabrina T. Howell, Marina Niessner, and David Yermack⇤ June 21, 2018 Abstract Initial coin offerings (ICOs) are sales of blockchain-based digital tokens associated with specific platforms or assets. Since 2014 ICOs have emerged as a new financing instrument, with some parallels to IPOs, venture capital, and pre-sale crowdfunding. We examine the relationship between issuer characteristics and measures of success, with a focus on liquidity, using 453 ICOs that collectively raise $5.7 billion. We also employ propriety transaction data in a case study of Filecoin, one of the most successful ICOs. We find that liquidity and trading volume are higher when issuers offer voluntary disclosure, credibly commit to the project, and signal quality. s s ss s ss ss ss s ⇤NYU Stern and NBER; Yale SOM; NYU Stern, ECGI and NBER. Email: [email protected]. For helpful comments, we are grateful to Bruno Biais, Darrell Duffie, seminar participants at the OECD Paris Workshop on Digital Financial Assets, Erasmus University, and the Swedish House of Finance. We thank Protocol Labs and particularly Evan Miyazono and Juan Benet for providing data. Sabrina Howell thanks the Kauffman Foundation for financial support. We are also grateful to all of our research assistants, especially Jae Hyung (Fred) Kim. Part of this paper was written while David Yermack was a visiting professor at Erasmus University Rotterdam. 1Introduction Initial coin offerings (ICOs) may be a significant innovation in entrepreneurial finance. In an ICO, a blockchain-based venture raises capital by selling cryptographically secured digital assets, usually called “tokens.” These ventures often resemble the startups that conventionally finance themselves with angel or venture capital (VC) investment, though there are many scams, jokes, and tokens that have nothing to do with a new product or business. -
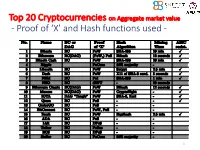
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Piecework: Generalized Outsourcing Control for Proofs of Work
(Short Paper): PieceWork: Generalized Outsourcing Control for Proofs of Work Philip Daian1, Ittay Eyal1, Ari Juels2, and Emin G¨unSirer1 1 Department of Computer Science, Cornell University, [email protected],[email protected],[email protected] 2 Jacobs Technion-Cornell Institute, Cornell Tech [email protected] Abstract. Most prominent cryptocurrencies utilize proof of work (PoW) to secure their operation, yet PoW suffers from two key undesirable prop- erties. First, the work done is generally wasted, not useful for anything but the gleaned security of the cryptocurrency. Second, PoW is natu- rally outsourceable, leading to inegalitarian concentration of power in the hands of few so-called pools that command large portions of the system's computation power. We introduce a general approach to constructing PoW called PieceWork that tackles both issues. In essence, PieceWork allows for a configurable fraction of PoW computation to be outsourced to workers. Its controlled outsourcing allows for reusing the work towards additional goals such as spam prevention and DoS mitigation, thereby reducing PoW waste. Meanwhile, PieceWork can be tuned to prevent excessive outsourcing. Doing so causes pool operation to be significantly more costly than today. This disincentivizes aggregation of work in mining pools. 1 Introduction Distributed cryptocurrencies such as Bitcoin [18] rely on the equivalence \com- putation = money." To generate a batch of coins, clients in a distributed cryp- tocurrency system perform an operation called mining. Mining requires solving a computationally intensive problem involving repeated cryptographic hashing. Such problem and its solution is called a Proof of Work (PoW) [11]. As currently designed, nearly all PoWs suffer from one of two drawbacks (or both, as in Bitcoin). -

Blockchain Law: the Fork Not Taken
Blockchain Law The fork not taken Robert A. Schwinger, New York Law Journal — November 24, 2020 I shall be telling this with a sigh Somewhere ages and ages hence: Two roads diverged in a wood, and I— I took the one less traveled by, And that has made all the difference. — Robert Frost Is the token holder — often the holder of some form of digital currency — always free to choose which branch of the fork to take? A blockchain is often envisioned as a record of a single continuous Background: ‘Two roads diverged in a sequential series of transactions, like the links of the metaphorical chain from which the term “blockchain” derives. But sometimes yellow wood’ the chain turns out to be not so single or continuous. Sometimes situations can arise where a portion of the chain can branch off A blockchain fork occurs when someone seeks to divide a into a new direction from the original chain, while the original chain blockchain into two branches by changing its source code, which also continues to move forward separately. This presents a choice is possible to do because the code is open. For those users who for the current holders of the digital tokens on that blockchain choose to upgrade their software, the software then “rejects about which direction they wish to follow going forward. In the all transactions from older software, effectively creating a new world of blockchain, this scenario is termed a “fork.” branch of the blockchain. However, those users who retain the old software continue to process transactions, meaning that But is the tokenholder—often the holder of some form of digital there is a parallel set of transactions taking place across two currency—always free to choose which branch of the fork to different chains.” See generally N. -

Consent Order: HDR Global Trading Limited, Et Al
Case 1:20-cv-08132-MKV Document 62 Filed 08/10/21 Page 1 of 22 UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF NEW YORK USDC SDNY DOCUMENT ELECTRONICALLY FILED COMMODITY FUTURES TRADING DOC #: COMMISSION, DATE FILED: 8/10/2021 Plaintiff v. Case No. 1:20-cv-08132 HDR GLOBAL TRADING LIMITED, 100x Hon. Mary Kay Vyskocil HOLDINGS LIMITED, ABS GLOBAL TRADING LIMITED, SHINE EFFORT INC LIMITED, HDR GLOBAL SERVICES (BERMUDA) LIMITED, ARTHUR HAYES, BENJAMIN DELO, and SAMUEL REED, Defendants CONSENT ORDER FOR PERMANENT INJUNCTION, CIVIL MONETARY PENALTY, AND OTHER EQUITABLE RELIEF AGAINST DEFENDANTS HDR GLOBAL TRADING LIMITED, 100x HOLDINGS LIMITED, SHINE EFFORT INC LIMITED, and HDR GLOBAL SERVICES (BERMUDA) LIMITED I. INTRODUCTION On October 1, 2020, Plaintiff Commodity Futures Trading Commission (“Commission” or “CFTC”) filed a Complaint against Defendants HDR Global Trading Limited (“HDR”), 100x Holdings Limited (100x”), ABS Global Trading Limited (“ABS”), Shine Effort Inc Limited (“Shine”), and HDR Global Services (Bermuda) Limited (“HDR Services”), all doing business as “BitMEX” (collectively “BitMEX”) as well as BitMEX’s co-founders Arthur Hayes (“Hayes”), Benjamin Delo (“Delo”), and Samuel Reed (“Reed”), (collectively “Defendants”), seeking injunctive and other equitable relief, as well as the imposition of civil penalties, for violations of the Commodity Exchange Act (“Act”), 7 U.S.C. §§ 1–26 (2018), and the Case 1:20-cv-08132-MKV Document 62 Filed 08/10/21 Page 2 of 22 Commission’s Regulations (“Regulations”) promulgated thereunder, 17 C.F.R. pts. 1–190 (2020). (“Complaint,” ECF No. 1.)1 II. CONSENTS AND AGREEMENTS To effect settlement of all charges alleged in the Complaint against Defendants HDR, 100x, ABS, Shine, and HDR Services (“Settling Defendants”) without a trial on the merits or any further judicial proceedings, Settling Defendants: 1. -

Cryptocurrency: the Economics of Money and Selected Policy Issues
Cryptocurrency: The Economics of Money and Selected Policy Issues Updated April 9, 2020 Congressional Research Service https://crsreports.congress.gov R45427 SUMMARY R45427 Cryptocurrency: The Economics of Money and April 9, 2020 Selected Policy Issues David W. Perkins Cryptocurrencies are digital money in electronic payment systems that generally do not require Specialist in government backing or the involvement of an intermediary, such as a bank. Instead, users of the Macroeconomic Policy system validate payments using certain protocols. Since the 2008 invention of the first cryptocurrency, Bitcoin, cryptocurrencies have proliferated. In recent years, they experienced a rapid increase and subsequent decrease in value. One estimate found that, as of March 2020, there were more than 5,100 different cryptocurrencies worth about $231 billion. Given this rapid growth and volatility, cryptocurrencies have drawn the attention of the public and policymakers. A particularly notable feature of cryptocurrencies is their potential to act as an alternative form of money. Historically, money has either had intrinsic value or derived value from government decree. Using money electronically generally has involved using the private ledgers and systems of at least one trusted intermediary. Cryptocurrencies, by contrast, generally employ user agreement, a network of users, and cryptographic protocols to achieve valid transfers of value. Cryptocurrency users typically use a pseudonymous address to identify each other and a passcode or private key to make changes to a public ledger in order to transfer value between accounts. Other computers in the network validate these transfers. Through this use of blockchain technology, cryptocurrency systems protect their public ledgers of accounts against manipulation, so that users can only send cryptocurrency to which they have access, thus allowing users to make valid transfers without a centralized, trusted intermediary. -

Short Selling Attack: a Self-Destructive but Profitable 51% Attack on Pos Blockchains
Short Selling Attack: A Self-Destructive But Profitable 51% Attack On PoS Blockchains Suhyeon Lee and Seungjoo Kim CIST (Center for Information Security Technologies), Korea University, Korea Abstract—There have been several 51% attacks on Proof-of- With a PoS, the attacker needs to obtain 51% of the Work (PoW) blockchains recently, including Verge and Game- cryptocurrency to carry out a 51% attack. But unlike PoW, Credits, but the most noteworthy has been the attack that saw attacker in a PoS system is highly discouraged from launching hackers make off with up to $18 million after a successful double spend was executed on the Bitcoin Gold network. For this reason, 51% attack because he would have to risk of depreciation the Proof-of-Stake (PoS) algorithm, which already has advantages of his entire stake amount to do so. In comparison, bad of energy efficiency and throughput, is attracting attention as an actor in a PoW system will not lose their expensive alternative to the PoW algorithm. With a PoS, the attacker needs mining equipment if he launch a 51% attack. Moreover, to obtain 51% of the cryptocurrency to carry out a 51% attack. even if a 51% attack succeeds, the value of PoS-based But unlike PoW, attacker in a PoS system is highly discouraged from launching 51% attack because he would have to risk losing cryptocurrency will fall, and the attacker with the most stake his entire stake amount to do so. Moreover, even if a 51% attack will eventually lose the most. For these reasons, those who succeeds, the value of PoS-based cryptocurrency will fall, and attempt to attack 51% of the PoS blockchain will not be the attacker with the most stake will eventually lose the most. -

Blockchain & Cryptocurrency Regulation
Blockchain & Cryptocurrency Regulation Third Edition Contributing Editor: Josias N. Dewey Global Legal Insights Blockchain & Cryptocurrency Regulation 2021, Third Edition Contributing Editor: Josias N. Dewey Published by Global Legal Group GLOBAL LEGAL INSIGHTS – BLOCKCHAIN & CRYPTOCURRENCY REGULATION 2021, THIRD EDITION Contributing Editor Josias N. Dewey, Holland & Knight LLP Head of Production Suzie Levy Senior Editor Sam Friend Sub Editor Megan Hylton Consulting Group Publisher Rory Smith Chief Media Officer Fraser Allan We are extremely grateful for all contributions to this edition. Special thanks are reserved for Josias N. Dewey of Holland & Knight LLP for all of his assistance. Published by Global Legal Group Ltd. 59 Tanner Street, London SE1 3PL, United Kingdom Tel: +44 207 367 0720 / URL: www.glgroup.co.uk Copyright © 2020 Global Legal Group Ltd. All rights reserved No photocopying ISBN 978-1-83918-077-4 ISSN 2631-2999 This publication is for general information purposes only. It does not purport to provide comprehensive full legal or other advice. Global Legal Group Ltd. and the contributors accept no responsibility for losses that may arise from reliance upon information contained in this publication. This publication is intended to give an indication of legal issues upon which you may need advice. Full legal advice should be taken from a qualified professional when dealing with specific situations. The information contained herein is accurate as of the date of publication. Printed and bound by TJ International, Trecerus Industrial Estate, Padstow, Cornwall, PL28 8RW October 2020 PREFACE nother year has passed and virtual currency and other blockchain-based digital assets continue to attract the attention of policymakers across the globe.