Learn About Differences in Addressing Between Ipv4 and Ipv6
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

15-744: Computer Networking Multicast Routing Example Applications Overview
Multicast Routing • Unicast: one source to one destination • Multicast: one source to many destinations 15-744: Computer Networking • Two main functions: • Efficient data distribution • Logical naming of a group L-20 Multicast 2 Example Applications Overview • Broadcast audio/video • IP Multicast Service Basics • Push-based systems • Software distribution • Multicast Routing Basics • Web-cache updates • Teleconferencing (audio, video, shared • Overlay Multicast whiteboard, text editor) • Multi-player games • Reliability • Server/service location • Other distributed applications • Congestion Control 3 4 1 IP Multicast Architecture Multicast – Efficient Data Distribution Src Src Service model Hosts Host-to-router protocol (IGMP) Routers Multicast routing protocols (various) 5 6 Multicast Router Responsibilities IP Multicast Service Model (rfc1112) • Learn of the existence of multicast groups • Each group identified by a single IP address (through advertisement) • Groups may be of any size • Identify links with group members • Members of groups may be located anywhere in the Internet • Establish state to route packets • Members of groups can join and leave at will • Replicate packets on appropriate interfaces • Senders need not be members • Routing entry: • Group membership not known explicitly • Analogy: Src, incoming interface List of outgoing interfaces • Each multicast address is like a radio frequency, on which anyone can transmit, and to which anyone can tune-in. 7 8 2 IP Multicast Addresses Multicast Scope Control – Small TTLs • Class -

IP Datagram ICMP Message Format ICMP Message Types
ICMP Internet Control Message Protocol ICMP is a protocol used for exchanging control messages. CSCE 515: Two main categories Query message Computer Network Error message Programming Usage of an ICMP message is determined by type and code fields ------ IP, Ping, Traceroute ICMP uses IP to deliver messages. Wenyuan Xu ICMP messages are usually generated and processed by the IP software, not the user process. Department of Computer Science and Engineering University of South Carolina IP header ICMP Message 20 bytes CSCE515 – Computer Network Programming IP Datagram ICMP Message Format 1 byte 1 byte 1 byte 1 byte VERS HL Service Total Length Datagram ID FLAG Fragment Offset 0781516 31 TTL Protocol Header Checksum type code checksum Source Address Destination Address payload Options (if any) Data CSCE515 – Computer Network Programming CSCE515 – Computer Network Programming ICMP Message Types ICMP Address Mask Request and Reply intended for a diskless system to obtain its subnet mask. Echo Request Id and seq can be any values, and these values are Echo Response returned in the reply. Destination Unreachable Match replies with request Redirect 0781516 31 Time Exceeded type(17 or 18) code(0) checksum there are more ... identifier sequence number subnet mask CSCE515 – Computer Network Programming CSCE515 – Computer Network Programming ping Program ICMP Echo Request and Reply Available at /usr/sbin/ping Test whether another host is reachable Send ICMP echo_request to a network host -n option to set number of echo request to send -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

IEEE 1588 Frequency and Time & Phase Profiles at ITU-T
IEEE 1588 Frequency and Time & phase profiles at ITU-T Silvana Rodrigues, System Engineering, IDT , [email protected] WSTS - 2013, San Jose ©2009 Integrated Device Technology, Inc. Agenda ● IEEE-1588TM Profile ● ITU-T G.8265.1 – Frequency Profile ● ITU-T G.8275.1 – Time and Phase Profile ● ITU-T G.8275.2 – Time and Phase Profile with partial support from the network IEEE 1588TM is a trademark of its respective owner www.IDT.com PAGE 2 CONFIDENTIAL IEEE-1588 Profiles ● IEEE-1588 defines profile as “The set of allowed Precision Time Protocol (PTP) features applicable to a device” ● “The purpose of a PTP profile is to allow organizations to specify specific selections of attribute values and optional features of PTP that, when using the same transport protocol, inter-work and achieve a performance that meets the requirements of a particular application.” ● A PTP profile should define ● Best master clock algorithm options ● Configuration management options ● Path delay mechanisms (peer delay or delay request-response) ● The range and default values of all PTP configurable attributes and data set members ● The transport mechanisms required, permitted, or prohibited ● The node types required, permitted, or prohibited ● The options required, permitted, or prohibited * IEEE Std 1588-2008 IEEE Standard for a Precision Clock Synchronization Protocol, copyright 2008 IEEE. All right reserved. www.IDT.com PAGE 3 CONFIDENTIAL ITU-T FREQUENCY PROFILE www.IDT.com PAGE 4 CONFIDENTIAL ITU-T G.8265.1 Frequency Profile IEEE-1588 without support from -

Transport Layer Chapter 6
Transport Layer Chapter 6 • Transport Service • Elements of Transport Protocols • Congestion Control • Internet Protocols – UDP • Internet Protocols – TCP • Performance Issues • Delay-Tolerant Networking Revised: August 2011 CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 The Transport Layer Responsible for delivering data across networks with the desired Application reliability or quality Transport Network Link Physical CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Transport Service • Services Provided to the Upper Layer » • Transport Service Primitives » • Berkeley Sockets » • Socket Example: Internet File Server » CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Services Provided to the Upper Layers (1) Transport layer adds reliability to the network layer • Offers connectionless (e.g., UDP) and connection- oriented (e.g, TCP) service to applications CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Services Provided to the Upper Layers (2) Transport layer sends segments in packets (in frames) Segment Segment CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Transport Service Primitives (1) Primitives that applications might call to transport data for a simple connection-oriented service: • Client calls CONNECT, SEND, RECEIVE, DISCONNECT • Server calls LISTEN, RECEIVE, SEND, DISCONNECT Segment CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice -
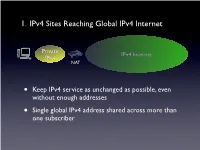
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3. -

Aerohive Configuration Guide: RADIUS Authentication | 2
Aerohive Configuration Guide RADIUS Authentication Aerohive Configuration Guide: RADIUS Authentication | 2 Copyright © 2012 Aerohive Networks, Inc. All rights reserved Aerohive Networks, Inc. 330 Gibraltar Drive Sunnyvale, CA 94089 P/N 330068-03, Rev. A To learn more about Aerohive products visit www.aerohive.com/techdocs Aerohive Networks, Inc. Aerohive Configuration Guide: RADIUS Authentication | 3 Contents Contents ...................................................................................................................................................................................................................... 3 IEEE 802.1X Primer................................................................................................................................................................................................... 4 Example 1: Single Site Authentication .................................................................................................................................................................... 6 Step 1: Configuring the Network Policy ..............................................................................................................................................................7 Step 2: Configuring the Interface and User Access .........................................................................................................................................7 Step 3: Uploading the Configuration and Certificates .................................................................................................................................... -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

1722 Over IP
1722 over IP Kevin Gross 26 October 2010 [email protected] 1722 fields • 802.3 header • 802.1Q tag • Ethertype • Control/data • Subtype • Version • Type specific data • Stream ID • Media clock restart • Sequence number • 802.1AS timestamp • Timestamp uncertain • Gateway info • Length • Payload IP fields • IP header – Version – Header length – DSCP – Total length – ID – Flags – Fragment offset – TTL – Protocol – Header checksum – Source IP – Destination IP • UDP header – Source port number – Destination port number – Checksum – Length RTP fields • Version • Marker • Payload type • Sequence number • Timestamp • Synchronization source • Synchronization routes 1733 RTCP fields • Name • Grandmaster ID • Time base indicator • Stream ID • 802.1AS timestamp 1722 over IP • Ethernet header • 802.1Q tag • IP header – DSCP • UDP header – Length • Control/data • Subtype • Version • Type specific data • Stream ID • Media clock restart • Sequence number • 802.1AS timestamp • Timestamp uncertain • Gateway info • Length • Payload Overhead • 1722 – Ethernet – 38 (includes preamble, header, FCS and IFG) – 802.1Q tag – 4 – 1722 header – 24 – Total = 66 octets • 1733 – Ethernet – 38 – 802.1Q tag – 4 – IP header – 20 or 40 – UDP header – 8 – RTP header – 12 – Total = 82 or 102 octets • 1722 over IP – Ethernet – 38 – 802.1Q tag – 4 – IP header – 20 or 40 – UDP header – 8 – 1722 header – 24 – Total = 94 or 114 octets IP multicast • Internet Group Management Protocol (IGMP) – IPv4 group membership • Multicast Listener Discovery (MLD) – IPv6 group membership • Multicast Address Dynamic Client Allocation Protocol (MADCAP) – RFC 2730. Implemented in Microsoft DHCP servers. Not widely deployed. • Unicast-Prefix-based IPv6 Multicast Addresses – RFC 3306, 3307. Requires ZMAAP. • ZMAAP – Not in use. IETF draft ( draft-ietf-zeroconf-zmaap- 02.txt ) expired in 2003. -

Domain Name System System Work?
What is the DNS? - how it works Isaac Maposa | Dev Anand Teelucksingh | Beran Gillen Community Onboarding Program | 11 March 2017 Agenda 1 2 3 What is the Domain Structure of the How does the Name System? Domain Name Domain Name System System Work? 4 5 6 Who makes the Stakeholders in the Engage with ICANN Domain Name Domain Name ??? System Work? System. | 2 What is the Domain Name System (DNS)? The Internet, what is it..? ● The Internet is a network of networks that interconnects devices to exchange information. ● In order to “talk” to each other, all of these devices must have a unique numerical address called an Internet Protocol address or IP Address. An example of an IP address is 94.127.53.132 ● When you visit a website from your browser, you are requesting the website from your device’s IP address to the web server’s IP address. ● However, you don’t type in the ip address of the web server, rather the domain name of for example www.google.com ● In so doing, you have queried the DNS. ● So what is this DNS???? | 4 What is the Domain Name System? ● The Domain Name System or DNS overcomes this problem of remembering IP addresses by mapping domain names to IP addresses. ● While this sounds like a phone book, it is not a centralised database. ● The DNS is a distributed database across a hierarchy of networks of servers and provide ways for devices and software (like browsers and email) to query the DNS to get an IP address. ● Domain names must be unique. -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet. -

Ipv6 Security: Myths & Legends
IPv6 security: myths & legends Paul Ebersman – [email protected] 21 Apr 2015 NANOG on the Road – Boston So many new security issues with IPv6! Or are there… IPv6 Security issues • Same problem, different name • A few myths & misconceptions • Actual new issues • FUD (Fear Uncertainty & Doubt) Round up the usual suspects! Remember these? • ARP cache poisoning • P2p ping pong attacks • Rogue DHCP ARP cache poisoning • Bad guy broadcasts fake ARP • Hosts on subnet put bad entry in ARP Cache • Result: MiM or DOS Ping pong attack • P2P link with subnet > /31 • Bad buy sends packet for addr in subnet but not one of two routers • Result: Link clogs with routers sending packet back and forth Rogue DHCP • Client broadcasts DHCP request • Bad guy sends DHCP offer w/his “bad” router as default GW • Client now sends all traffic to bad GW • Result: MiM or DOS Look similar? • Neighbor cache corruption • P2p ping pong attacks • Rogue DHCP + rogue RA Solutions? • Lock down local wire • /127s for p2p links (RFC 6164) • RA Guard (RFC 6105) And now for something completely different! So what is new? • Extension header chains • Packet/Header fragmentation • Predictable fragment headers • Atomic fragments The IPv4 Packet 14 The IPv6 Packet 15 Fragmentation • Minimum 1280 bytes • Only source host can fragment • Destination must get all fragments • What happens if someone plays with fragments? IPv6 Extension Header Chains • No limit on length • Deep packet inspection bogs down • Confuses stateless firewalls • Fragments a problem • draft-ietf-6man-oversized-header-chain-09