Ethical Aspects of Managing a Social Network Site: a Disclosive Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Figure 1 Timeline of the Launch Dates of Many Major Snss and Dates When Community Sites Re-Launched with SNS Features
Figure 1 Timeline of the launch dates of many major SNSs and dates when community sites re-launched with SNS features 212 Journal of Computer-Mediated Communication 13 (2008) 210–230 ª 2008 International Communication Association Beyond profiles, Friends, comments, and private messaging, SNSs vary greatly in their features and user base. Some have photo-sharing or video-sharing capabilities; others have built-in blogging and instant messaging technology. There are mobile- specific SNSs (e.g., Dodgeball), but some web-based SNSs also support limited mobile interactions (e.g., Facebook, MySpace, and Cyworld). Many SNSs target people from specific geographical regions or linguistic groups, although this does not always determine the site’s constituency. Orkut, for example, was launched in the United States with an English-only interface, but Portuguese-speaking Brazilians quickly became the dominant user group (Kopytoff, 2004). Some sites are designed with specific ethnic, religious, sexual orientation, political, or other identity-driven categories in mind. There are even SNSs for dogs (Dogster) and cats (Catster), although their owners must manage their profiles. While SNSs are often designed to be widely accessible, many attract homoge- neous populations initially, so it is not uncommon to find groups using sites to segregate themselves by nationality, age, educational level, or other factors that typically segment society (Hargittai, this issue), even if that was not the intention of the designers. A History of Social Network Sites The Early Years According to the definition above, the first recognizable social network site launched in 1997. SixDegrees.com allowed users to create profiles, list their Friends and, beginning in 1998, surf the Friends lists. -
Page Ranking Advogato Free and Open So
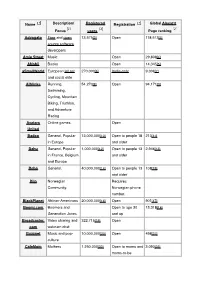
Name Description/ Registered Registration Global Alexa[1] Focus users Page ranking Advogato Free and open 13,575[2] Open 118,513[3] source software developers Amie Street Music Open 29,808[4] ANobii Books Open 14,345[5] aSmallWorld European jet set 270,000[6] Invite-only 9,306[7] and social elite Athlinks Running, 54,270[8] Open 94,171[9] Swimming, Cycling, Mountain Biking, Triathlon, and Adventure Racing Avatars Online games. Open United Badoo General, Popular 13,000,000[10] Open to people 18 213[11] in Europe and older Bahu General, Popular 1,000,000[12] Open to people 13 2,946[13] in France, Belgium and older and Europe Bebo General. 40,000,000[14] Open to people 13 108[15] and older Biip Norwegian Requires Community. Norwegian phone number. BlackPlanet African-Americans 20,000,000[16] Open 901[17] Boomj.com Boomers and Open to age 30 15,318[18] Generation Jones and up Broadcaster. Video sharing and 322,715[19] Open com webcam chat Buzznet Music and pop- 10,000,000[20] Open 498[21] culture CafeMom Mothers 1,250,000[22] Open to moms and 3,090[23] moms-to-be Cake Investing Open Financial Care2 Green living and 9,961,947[24] Open social activism Classmates.c School, college, 50,000,000[25] Open 923[26] om work and the military Cloob General. Popular Open in Iran. College College students. requires an e-mail Tonight address with an ".edu" ending CouchSurfin Worldwide network 871,049[27] Open g for making connections between travelers and the local communities they visit. -

A Study of Internet Based Community Interactions
Virtual Online Communities: A Study of Internet Based Community Interactions A dissertation presented to the faculty of the Scripps College of Communication of Ohio University In partial fulfillment of the requirements for the degree Doctor of Philosophy Adrian M. Budiman August 2008 This dissertation titled Virtual Communities Online: A Study of Internet Based Community Interactions by ADRIAN M. BUDIMAN has been approved for the School of Media Arts and Studies and the Scripps College of Communication by Drew McDaniel Professor of Telecommunications Gregory J. Shepherd Dean, Scripps College of Communication ii Abstract BUDIMAN, ADRIAN M., Ph.D., August 2008, Mass Communication Virtual Online Communities: A Study of Internet Based Community Interactions (167 pp.) Director of Dissertation: Drew McDaniel The aim of this research was to better understand virtual online communities (VOCs), that is, communities that are formed and maintained through the Internet. This research was guided by four research questions: What do participants in VOCs actually seek? How does a participant critically evaluate information produced in VOCs? What differences do VOC members perceive between their online community experiences compared to their experiences in real-life face-to-face communities? In what ways might a VOC shape its members’ views toward political and social change? The methodology employed was participant observation of 20 informants within their online and offline realms plus in-depth interviews with each informant. Interviews and observations were conducted from 2005 – 2007. This research identified two different types of VOCs: dependent and self- contained VOCs. Dependent VOCs act as extensions to already existent face-to-face communities while self-sustained VOCs are communities where relationships between members are formed, developed, and nurtured purely through virtual encounters on the Internet based on shared interests. -

Crime Prevention in the Virtual Community
CPTED in Bytes The Blurring Lines of Community Barry Davidson Executive Director, ICA Today’s Task Broaden our perspective of the effectiveness of technology in community engagement & crime prevention. Identify technology tools that are current (for the moment) Begin looking forward (Instead of playing catch up!) “Identify the future that has already happened” Peter Drucker Why We Need To Pay Attention Your Corner of The World You Know You Wanted to Know “Old” Tech Tools The Usual Suspects: Email Static Websites Forums/Blogs On-line News Sites The Past The Past We are reactive to social disorder issues Attitude of mistrust of technology by safety professionals More hindsight than foresight: 1994 – Email has no place in the office 1996 – Internet has no place in the office 1998 – eCommerce is too dangerous 2002 – IM is never going catch on 2005 – Social Networking sites are just a fad 2006 - Google maps will not be a usable tool or concern 2008 – YouTube is just a passing fancy for kids Join the Social Networking Revolution The NEW Technology Tools Social Networking Providers: Facebook Facebook Twitter MySpace More than 700 million Nexopia active users Plaxo People spend over Yahoo 700 billion minutes per month on YouTube Facebook RSS Feeds Communications by the thumb . Social Media Stats What is Community? A group of human beings that: have a common interest. common vision. work collaboratively towards a common goal or good. Has no physical or geographic borders Top 4 Social Networking Communities Facebook - Founded by Mark Zuckerberg, Facebook was designed as a social networking site for Harvard students. -

This Is the Published Version of a Paper
http://www.diva-portal.org This is the published version of a paper published in Seminar.net: Media, technology and lifelong learning. Citation for the original published paper (version of record): Enochsson, A-B. (2007) Tweens on the Internet: Communication in virtual guestbooks. Seminar.net: Media, technology and lifelong learning, 3(2) Access to the published version may require subscription. N.B. When citing this work, cite the original published paper. Permanent link to this version: http://urn.kb.se/resolve?urn=urn:nbn:se:kau:diva-25130 Tweens on the Internet - communication in virtual guest books AnnBritt Enochsson The Interactive Institute, Stockholm And Karlstad University Email: [email protected] Abstract Today digital communication is a natural part of young people’s social life. It has increased drastically during the last few years, and there are still a lot of questions about what this means, and how this new media affects communication. This study focuses on young people of 11-13, i.e.the age between children and teenagers, also called tweens. In a large study, the overall aim is to see what communication in the Internet community LunarStorm means to them in their social life. This particular paper reports on the content of the asynchronous communication in the participants’ digital guest books, which is one of the main channels for communication between the participants. A group of 15 tweens from a small village in Sweden were studied when communicating in Sweden’s largest Internet community, LunarStorm. The research method used was what is usually described as cyber ethnography. -

Loree O'sullivan
SELLING THROUGH SOCIAL MEDIA: CHARMING PROSPECTS WITH CONTEXT & CONFIDENCE LOREE O’SULLIVAN 2 LOREE O’SULLIVAN DIGITAL MARKETING STRATEGIST AT FABRICUT INC. Digital Marketer dig·i·tal /ˈdijidl/ mar·ket·er /ˈmärkədər/ A marketer who does all the things on all the devices for all of the platforms to accomplish all the goals for all of the teams - and still somehow manages to achieve greatness (with the help of coffee). SELLING THROUGH SOCIAL MEDIA CHARMING PROSPECTS WITH CONTEXT & CONFIDENCE Social media is everywhere. It’s everything! Whether consumers are researching reviews of a product, looking for customer support for an issue, sharing their satisfaction or disappointment from a purchase, or asking WHY ARE WE questions around best practices - social media has become LOOKING AT the place where consumers can engage in a way that is fast, SOCIAL MEDIA? reactive, and fits into their established dialogue. JUST HOW OBSESSED WITH SOCIAL MEDIA ARE WE? DOWN TO THE NUMBERS 54 74 78 22 60 BUSINESSES GENERATED USE FACEBOOK USAGE ACROSS WORLD POPULATION USE INSTAGRAM DAILY LEADS FROM SOCIAL DAILY AGE GROUPS 30-49 ON FACEBOOK 54% of B2B businesses 74% of Facebook users Use any form of social media: 22% of the world’s total 60% users indicate that they visit and marketers said say they visit the site daily 88% of 18 to 29 population uses these platforms on a daily basis. they’ve generated leads 78% of 30 to 49 Facebook. from social media 64% of 50 to 64 SOURCE http://www.pewinternet.org/2018/03/01/social-media-use-in-2018/ A LITTLE BIT OF HISTORY -

Social Network Sites: Definition, History, and Scholarship
Social Network Sites: Definition, History, and Scholarship danah m. boyd [email protected] School of Information University of California-Berkeley Nicole B. Ellison [email protected] Department of Telecommunication, Information Studies, and Media Michigan State University Abstract Introduction Social Network Sites: A Definition A History of Social Network Sites Previous Scholarship Overview of this Special Theme Section Future Research Acknowledgments Notes References About the Authors Abstract Social network sites (SNSs) are increasingly attracting the attention of academic and industry researchers intrigued by their affordances and reach. This special theme section of the Journal of Computer-Mediated Communication brings together scholarship on these emergent phenomena. In this introductory article, we describe features of SNSs and propose a comprehensive definition. We then present one perspective on the history of such sites, discussing key changes and developments. After briefly summarizing existing scholarship concerning SNSs, we discuss the articles in this special section and conclude with considerations for future research. Introduction Since their introduction, social network sites (SNSs) such as MySpace, Facebook, Cyworld, and Bebo have attracted millions of users, many of whom have integrated these sites into their daily practices. As of this writing, there are hundreds of SNSs, with various technological affordances, supporting a wide range of interests and practices. While their key technological features are fairly consistent, the cultures that emerge around SNSs are varied. Most sites support the maintenance of pre-existing social networks, but others help strangers connect based on shared interests, political views, or activities. Some sites cater to diverse audiences, while others attract people based on common language or shared racial, sexual, religious, or nationality-based identities. -

Broadcasters and the Broadcasters and the Internet
Broadcasters and the Broadcasters and the Internet Internet EBU Members’ Internet Presence Distribution Strategies Online Consumption Trends Social Networking and Video Sharing Communities November 2007 European Broadcasting Union Strategic Information Service (SIS) L’Ancienne-Route 17A CH-1218 Grand-Saconnex Switzerland Phone +41 (0) 22 717 21 11 Fax +41 (0)22 747 40 00 www.ebu.ch/sis European Broadcasting Union l Strategic Information Service Broadcasters and the Internet EBU Members' Internet Presence Distribution Strategies Online Consumption Trends Social Networking and Video Sharing Communities November 2007 The Report Staff This report was produced by the Strategic Information Service of the EBU. Editor: Alexander Shulzycki Production Editor: Anna-Sara Stalvik Principal Researcher: Anna-Sara Stalvik Special appreciation to: Danish Radio and Television (DR) Swedish Television (SVT) Swedish Radio (SR) Cover Design: Philippe Juttens European Broadcasting Union Telephone: +41 22 717 2111 Address: L'Ancienne-Route 17A, 1218 Geneva, Switzerland SIS web-site: www.ebu.ch/director_general/sis.php SIS contact e-mail: [email protected] BROADCASTERS AND THE INTERNET TABLE OF CONTENTS INTRODUCTION.............................................................................................................. 1 OVERVIEW .............................................................................................................................1 1. The general Internet landscape: usage, websites, advertising ............................................ -

Social Media Use and Socio-Political Participation of College Students
SOCIAL MEDIA USE AND SOCIO-POLITICAL PARTICIPATION OF COLLEGE STUDENTS MA SOCIOLOGY i | P a g e TABLE OF CONTENTS LIST OF FIGURES iii-iv ABSTRACT v CHAPTERS TITLE PAGE NUMBER I INTRODUCTION 1-11 II LITERATURE REVIEW 12-27 III METHODOLOGY 28-31 IV ANALYSIS AND INTERPRETATION 32-49 V FINDINGS, CONCLUSION AND 50-54 SUGGESTIONS BIBLIOGRAPHY 55-57 APPENDIX-I 58-63 QUESTIONNAIRE ii | P a g e LIST OF FIGURES FIGURE NAME PAGE NO: NUMBER 1. STREAM OF STUDY 32 2. EDUCATION LEVEL 33 3. MARITAL STATUS 33 4. PLACE OF LIVING 34 5. LANGUAGE KNOWN 34 6. HOURS A DAY 35 7. POSTINGS ON SOCIAL MEDIA 35 8. KIND OF ACTIVITIES PERFORMS 36 9. USAGE OF SOCIAL MEDIA 37 10. ISSUES MATTER MOST 38 11. TAKE PARTING IN CAMPAIGN 38 12. IMPACT OF SOCIAL MEDIA ON STUDENT 39 13. ONLINE SOCIAL ACTIVITY TO REAL WORLD ACTIVITY 39 14. CHANGE IN ATTITUDE 40 15. RESPONDS TO SOCIAL ISSUES 40 16. SOCIAL MEDIA ON ACADEMICS 41 17. MOTIVATED IN POLITICAL ACTIVITIES 42 18. MADE ACTIVE IN BOTH SOCIAL AND POLITICAL 42 ACTIVITIES iii | P a g e 19. SAFE IN PROVIDING PERSONAL INFORMATION 43 20. TRUSTWORTHINESS TOWARDS THE PEOPLE MEETS IN 43 SNS 21. ACCEPTANCE OF OPINIONS BY OTHERS 44 22. FACED HARASSMENT/ASSAULT ON SNS 44 23. BETTER INFORMED THROUGH SNS 45 24. CROSS CHECKS ONLINE INFORMATION 45 25. SOCIAL NETWORKING SITES TO OFFLINE MEDIA 46 26. SOCIAL NETWORKING SITES HAVING ACCOUNTS 47 27. PREFERRED SOCIAL MEDIA SITES 47 28. MEMBER OF STUDENT UNION 48 29. SOCIAL MEDIA IN FOLLOWING POLITICAL IDEOLOGY 48 30. -

Enhancing Current Feedback Processes Through Social Media
Enhancing Current Feedback Processes through Social Media Monitoring An exploratory study of Social Media and Social Media monitoring practices within an MNC looking to combine new practices with traditional customer-centric processes. Author(s): Fredrik Bergstrand, Tutor: Professor Hans Jansson Growth Through Innovation and International Marketing Subject: Business Administration Emily A. Finlaw, Level and semester: Master's level, Spring 2011 Growth Through Innovation and International Marketing Growth Through Innovation and International Marketing Master Thesis, 2011 ENHANCING CURRENT FEEDBACK PROCESSES THROUGH SOCIAL MEDIA MONITORING An exploratory study of Social Media and Social Media monitoring practices within an MNC looking to combine new practices with traditional customer- centric processes. Fredrik Bergstrand & Emily A. Finlaw “Today, everything is about Social Media” – Andreas Kaplan and Michael Haenlein “Just as the eyes are the windows to the soul, business intelligence is a window to the dynamics of a business” – Cindi Howson “[Social Media monitoring] is not a car - but it is a vehicle for acquiring and sharing knowledge” – definition from Lexalytics, sited from Mike Marshall “Your most unhappy customers are your greatest source of learning.” – Bill Gates “Knowledge is not good if you don´t apply it” – Johann Wolfgang von Goethe Acknowledgements It is our pleasure to thank all those who made contributions to this thesis over the past few months and throughout this learning journey. We would first like to thank Volvo Construction Equipment Region International for making this thesis possible. Thank you to Lars-Gunnar Larsson and Hanna Bragberg for creating a cutting-edge topic which has manifested into the inspiration for this thesis. -

The Case of Indigenous Tweets
Ní Bhroin, Social media-innovation Social Media-Innovation: The Case of Indigenous Tweets Niamh Ní Bhroin Department of Media and Communication, University of Oslo [email protected] ABSTRACT KEYWORDS: Twitter presents new opportunities for individual communication. Consequently, it may be a relevant arena Social Media-Innovation; Communication Capabilities; Media- in which to address the social need of minority language maintenance. The Indigenous Tweets website ted Interaction; Minority Languages; Indigenous Tweets presents a directory of minority language users on Twitter (www.indigenoustweets.com). It aims to create new opportunities to use these languages, thus to address a social need through media innovation. In this The Journal of Media Innovations 2.1 (2015), 89-106. article, I draw on a theoretical framework from Media Innovation and Social Innovation Studies, to deline- ate the concept of Social Media-Innovation. I propose three distinguishing attributes. Firstly, users of these http://www.journals.uio.no/index.php/TJMI innovations must consider them relevant to address identified social needs. Secondly, the communication © Niamh Ní Bhroin 2015. capabilities they present must support addressing these needs. Thirdly, they should facilitate mediated interaction that enhances society’s capacity to act. Having delineated the concept I explore how its at- tributes are manifest in practice with reference to the case of Indigenous Tweets. I find that the relevance of Indigenous Tweets is negotiated with regard to culturally specific needs in different social contexts. The development and use of its communication capabilities are supported by incremental experimentation and learning. Furthermore, while it facilitates mediated interactions that are designed to enhance society’s capacity to act, these occur in a hybrid media context and are influenced by the range of agents involved.