PTP) Is an Ethernet Or IP-Based Protocol for Synchronizing Time Clocks on a Collection of Network Devices Using a Master/Slave Distribution Mechanism
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Time-Synchronized Data Collection in Smart Grids Through Ipv6 Over
Time-synchronized Data Collection in Smart Grids through IPv6 over BLE Stanley Nwabuona Markus Schuss Simon Mayer Pro2Future GmbH Graz University of Technology Pro2Future GmbH and Graz Graz, Austria Graz, Austria University of Technology [email protected] [email protected] Graz, Austria [email protected] Konrad Diwold Lukas Krammer Alfred Einfalt Siemens Corporate Siemens Corporate Siemens Corporate Technology Technology Technology Vienna, Austria Vienna, Austria Vienna, Austria [email protected] [email protected] [email protected] ABSTRACT INTRODUCTION For the operation of electrical distribution system an increased Due to the progressing integration of distributed energy re- shift towards smart grid operation can be observed. This shift sources (such as domestic photovoltaics) into the distribution provides operators with a high level of reliability and efficiency grid [5], conventional – mostly passive – monitoring and con- when dealing with highly dynamic distribution grids. Techni- trol schemes of power systems are no longer applicable. This cally, this implies that the support for a bidirectional flow of is because these are not designed to handle and manage the data is critical to realizing smart grid operation, culminating in volatile and dynamic behavior stemming from these new active the demand for equipping grid entities (such as sensors) with grid entities. Therefore, advanced controlling and monitoring communication and processing capabilities. Unfortunately, schemes are required for distribution grid operation (i.e., in- the retrofitting of brown-field electric substations in distribu- cluding in Low-Voltage (LV) grids) to avoid system overload tion grids with these capabilities is not straightforward – this which could incur permanent damages. -

Ieee 802.1 for Homenet
IEEE802.org/1 IEEE 802.1 FOR HOMENET March 14, 2013 IEEE 802.1 for Homenet 2 Authors IEEE 802.1 for Homenet 3 IEEE 802.1 Task Groups • Interworking (IWK, Stephen Haddock) • Internetworking among 802 LANs, MANs and other wide area networks • Time Sensitive Networks (TSN, Michael David Johas Teener) • Formerly called Audio Video Bridging (AVB) Task Group • Time-synchronized low latency streaming services through IEEE 802 networks • Data Center Bridging (DCB, Pat Thaler) • Enhancements to existing 802.1 bridge specifications to satisfy the requirements of protocols and applications in the data center, e.g. • Security (Mick Seaman) • Maintenance (Glenn Parsons) IEEE 802.1 for Homenet 4 Basic Principles • MAC addresses are “identifier” addresses, not “location” addresses • This is a major Layer 2 value, not a defect! • Bridge forwarding is based on • Destination MAC • VLAN ID (VID) • Frame filtering for only forwarding to proper outbound ports(s) • Frame is forwarded to every port (except for reception port) within the frame's VLAN if it is not known where to send it • Filter (unnecessary) ports if it is known where to send the frame (e.g. frame is only forwarded towards the destination) • Quality of Service (QoS) is implemented after the forwarding decision based on • Priority • Drop Eligibility • Time IEEE 802.1 for Homenet 5 Data Plane Today • 802.1Q today is 802.Q-2011 (Revision 2013 is ongoing) • Note that if the year is not given in the name of the standard, then it refers to the latest revision, e.g. today 802.1Q = 802.1Q-2011 and 802.1D -

Implementing an IEEE 1588 V2 on I.MX RT Using Ptpd, Freertos, and Lwip TCP/IP Stack
NXP Semiconductors Document Number: AN12149 Application Note Rev. 1 , 09/2018 Implementing an IEEE 1588 V2 on i.MX RT Using PTPd, FreeRTOS, and lwIP TCP/IP stack 1. Introduction Contents This application note describes the implementation of 1. Introduction .........................................................................1 the IEEE 1588 V2 Precision Time Protocol (PTP) on 2. IEEE 1588 basic overview ..................................................2 2.1. Synchronization principle ........................................ 3 the i.MX RT MCUs running FreeRTOS OS. The IEEE 2.2. Timestamping ........................................................... 5 1588 standard provides accurate clock synchronization 3. IEEE 1588 functions on i.MX RT .......................................6 for distributed control nodes in industrial automation 3.1. Adjustable timer module .......................................... 6 3.2. Transmit timestamping ............................................. 8 applications. 3.3. Receive timestamping .............................................. 8 3.4. Time synchronization ............................................... 8 The implementation runs on the i.MX RT10xx 3.5. Input capture and output compare block .................. 8 Evaluation Kit (EVK) board with i.MX RT10xx MCUs. 4. IEEE 1588 implementation for i.MX RT ............................9 The demo software is based on the NXP MCUXpresso 4.1. Hardware components .............................................. 9 4.2. Software components ............................................ -

Which Time Server Option Is Best for Synchronizing Your Clocks
WHICH TIME SERVER OPTION IS BEST FOR SYNCHRONIZING YOUR CLOCKS? Any electronic device that automatically displays REGARDING MASTER the current local time – your clocks, phone, tablet, TIME CONTROLLERS computer and even most TVs – has to pull that time from a time server. AND The time server acts as a messenger of sorts; IP NETWORK CLOCKS it reads the time from a reference clock and distributes that information via a computer network (ETHERNET OR WI-FI) to your device when the device requests it. The time server could be a local network time server or an internet time server. SNTP, or Simple Network Time Protocol, is an internet standard protocol that allows a clock or device to contact a server and get the current time. It’s a simplification of the more robustNTP (Network Time Protocol) and is used in most embedded devices and computers. Once the device receives the current Coordinated Universal Time (UTC), the device applies offsets such as time zone or daylight saving time considerations, as well as the time spent on the network retrieving the time, before displaying the accurate local time. January 2018 AMERICAN TIME WHITE PAPER BY: MAX BLOM When it comes to syncing time for your organization’s clocks, you have 3 options: Let’s take a look at how each of these options work, their pros and cons, and our recommendation. Port 123 is reserved specifically for External Server IP Address NTP/SNTP communication 1 The NIST – the U.S. Department of Commerce’s National Institute of Standards and Technology – is the primary source for synchronizing time systems in the U.S. -

Endrun TECHNOLOGIES Præcis Cntp Network Time Server
Smarter Timing Solutions EndRun TECHNOLOGIES Præcis Cntp Network Time Server User’s Manual Præcis Cntp Network Time Server User’s Manual EndRun Technologies 1360 North Dutton Avenue #200 Santa Rosa, California USA 95401 Phone 707-573-8633 • Fax 707-573-8619 Preface Thank you for purchasing the Præcis Cntp Network Time Server. Our goal in developing this product is to bring precise, Universal Coordinated Time (UTC) into your network quickly, easily and reliably. Your new Præcis Cntp is fabricated using the highest quality materials and manufacturing processes available today, and will give you years of troublefree service. About EndRun Technologies Founded in 1998 and headquartered in Santa Rosa, California, we are the leaders in the exciting new time and frequency distribution technology based on the Code Division Multiple Access (CDMA) mobile telecommunications infrastructure. Our innovative designs and painstaking attention to the details of efficient manufacturability have made us the first to bring this technology to the broad synchronization market at prices small businesses can afford. EndRun Technologies markets this technology in three major product lines: Network Time Sources/Servers – These units are configured for optimum performance in operation with network servers/networks running the Internet protocol known as the Network Time Protocol (NTP). Instrumentation Time and Frequency References – These products provide UTC traceable time and frequency signals for use in precision test and measurement instrumentation. OEM Time and Frequency Engines – These products provide the core time and frequency capabilities to our customers who require lower cost and tighter integration with their own products. About this manual This manual will guide you through simple installation and set up procedures. -

NBAR2 Standard Protocol Pack 1.0
NBAR2 Standard Protocol Pack 1.0 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 © 2013 Cisco Systems, Inc. All rights reserved. CONTENTS CHAPTER 1 Release Notes for NBAR2 Standard Protocol Pack 1.0 1 CHAPTER 2 BGP 3 BITTORRENT 6 CITRIX 7 DHCP 8 DIRECTCONNECT 9 DNS 10 EDONKEY 11 EGP 12 EIGRP 13 EXCHANGE 14 FASTTRACK 15 FINGER 16 FTP 17 GNUTELLA 18 GOPHER 19 GRE 20 H323 21 HTTP 22 ICMP 23 IMAP 24 IPINIP 25 IPV6-ICMP 26 IRC 27 KAZAA2 28 KERBEROS 29 L2TP 30 NBAR2 Standard Protocol Pack 1.0 iii Contents LDAP 31 MGCP 32 NETBIOS 33 NETSHOW 34 NFS 35 NNTP 36 NOTES 37 NTP 38 OSPF 39 POP3 40 PPTP 41 PRINTER 42 RIP 43 RTCP 44 RTP 45 RTSP 46 SAP 47 SECURE-FTP 48 SECURE-HTTP 49 SECURE-IMAP 50 SECURE-IRC 51 SECURE-LDAP 52 SECURE-NNTP 53 SECURE-POP3 54 SECURE-TELNET 55 SIP 56 SKINNY 57 SKYPE 58 SMTP 59 SNMP 60 SOCKS 61 SQLNET 62 SQLSERVER 63 SSH 64 STREAMWORK 65 NBAR2 Standard Protocol Pack 1.0 iv Contents SUNRPC 66 SYSLOG 67 TELNET 68 TFTP 69 VDOLIVE 70 WINMX 71 NBAR2 Standard Protocol Pack 1.0 v Contents NBAR2 Standard Protocol Pack 1.0 vi CHAPTER 1 Release Notes for NBAR2 Standard Protocol Pack 1.0 NBAR2 Standard Protocol Pack Overview The Network Based Application Recognition (NBAR2) Standard Protocol Pack 1.0 is provided as the base protocol pack with an unlicensed Cisco image on a device. -

IBM Z Server Time Protocol Guide
Front cover Draft Document for Review August 3, 2020 1:37 pm SG24-8480-00 IBM Z Server Time Protocol Guide Octavian Lascu Franco Pinto Gatto Gobehi Hans-Peter Eckam Jeremy Koch Martin Söllig Sebastian Zimmermann Steve Guendert Redbooks Draft Document for Review August 3, 2020 7:26 pm 8480edno.fm IBM Redbooks IBM Z Server Time Protocol Guide August 2020 SG24-8480-00 8480edno.fm Draft Document for Review August 3, 2020 7:26 pm Note: Before using this information and the product it supports, read the information in “Notices” on page vii. First Edition (August 2020) This edition applies to IBM Server Time Protocol for IBM Z and covers IBM z15, IBM z14, and IBM z13 server generations. This document was created or updated on August 3, 2020. © Copyright International Business Machines Corporation 2020. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Draft Document for Review August 3, 2020 8:32 pm 8480TOC.fm Contents Notices . vii Trademarks . viii Preface . ix Authors. ix Comments welcome. .x Stay connected to IBM Redbooks . xi Chapter 1. Introduction to Server Time Protocol . 1 1.1 Introduction to time synchronization . 2 1.1.1 Insertion of leap seconds . 2 1.1.2 Time-of-Day (TOD) Clock . 3 1.1.3 Industry requirements . 4 1.1.4 Time synchronization in a Parallel Sysplex. 6 1.2 Overview of Server Time Protocol (STP) . 7 1.3 STP concepts and terminology . 9 1.3.1 STP facility . 9 1.3.2 TOD clock synchronization . -
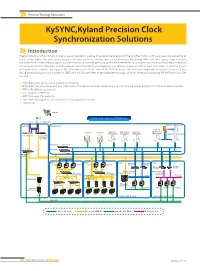
Kysync,Kyland Precision Clock Synchronization Solutions
Precise Timing Solutions KySYNC,Kyland Precision Clock Synchronization Solutions Introduction Precision clock synchronization solutions are using external precise time reference to establish the synchronization with local clocks by delivering all kinds of time signal. The time source provides the time reference, and the time server distributes the timing. While the time source is not available, the time server’s time keeping ability will be critical to assure the precision of the time reference. So in a precision clock synchronization network, the precision of time reference, time distribution and time keeping are hook-ups and all plays important role in each time node. In order to ensure all legacy devices which only support IRIG-B format could still be synced, the PTP (Precision Time Protocol) signal will need to be converted into IRIG-B format through clock conversion. IEEE 1588 will also be need to be distributed through all kinds of network including PRP/HSR and also SDH network. Kyland provides turnkey timing solution including: High-precision time server and IEEE 1588 industrial Ethernet switches supporting IEEE 1588 in both power profile (C37.238) and telecom profile PTP to IRIG-B time conversion IEEE 1588 over PRP/HSR IEEE 1588 over SDH network TMS (Time Management System) & Service Management System Time tester Satellite KySYNC, Intelligent Gateway, PRP/HSR Solution E1/T1 GPS Antenna Remote Control Center KySYNC Station Level Protection Engineering Server A Sever B Operation Maintenance Operation Workstation Workstation Workstation -

Encryption Is Futile: Delay Attacks on High-Precision Clock Synchronization 1
R. ANNESSI, J. FABINI, F.IGLESIAS, AND T. ZSEBY: ENCRYPTION IS FUTILE: DELAY ATTACKS ON HIGH-PRECISION CLOCK SYNCHRONIZATION 1 Encryption is Futile: Delay Attacks on High-Precision Clock Synchronization Robert Annessi, Joachim Fabini, Felix Iglesias, and Tanja Zseby Institute of Telecommunications TU Wien, Austria Email: fi[email protected] Abstract—Clock synchronization has become essential to mod- endanger control decisions, and adversely affect the overall ern societies since many critical infrastructures depend on a functionality of a wide range of (critical) services that depend precise notion of time. This paper analyzes security aspects on accurate time. of high-precision clock synchronization protocols, particularly their alleged protection against delay attacks when clock syn- In recent years, security of clock synchronization received chronization traffic is encrypted using standard network security increased attention as various attacks on clock synchronization protocols such as IPsec, MACsec, or TLS. We use the Precision protocols (and countermeasures) were proposed. For this Time Protocol (PTP), the most widely used protocol for high- reason, clock synchronization protocols need to be secured precision clock synchronization, to demonstrate that statistical whenever used outside of fully trusted network environments. traffic analysis can identify properties that support selective message delay attacks even for encrypted traffic. We furthermore Clock synchronization protocols are specifically susceptible to identify a fundamental conflict in secure clock synchronization delay attacks since the times when messages are sent and between the need of deterministic traffic to improve precision and received have an actual effect on the receiver’s notion of the need to obfuscate traffic in order to mitigate delay attacks. -

Ipv6-Security Monitoring
Security Monitoring ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 22 July 2014 1 Managing and Monitoring IPv6 Networks p SNMP Monitoring p IPv6-Capable SNMP Management Tools p NetFlow Analysis p Syslog p Keeping accurate time p Intrusion Detection p Managing the Security Configuration 2 Using SNMP for Managing IPv6 Networks 3 What is SNMP? p SNMP – Simple Network Management Protocol p Industry standard, hundreds of tools exist to exploit it p Present on any decent network equipment p Query/response based: GET / SET p Monitoring generally uses GET p Object Identifiers (OIDs) p Keys to identify each piece of data p Concept of MIB (Management Information Base) p Defines a collection of OIDs What is SNMP? p Typical queries n Bytes In/Out on an interface, errors n CPU load n Uptime n Temperature or other vendor specific OIDs p For hosts (servers or workstations) n Disk space n Installed software n Running processes n ... p Windows and UNIX have SNMP agents What is SNMP? p UDP protocol, port 161 p Different versions n v1 (1988) – RFC1155, RFC1156, RFC1157 p Original specification n v2 – RFC1901 ... RFC1908 + RFC2578 p Extends v1, new data types, better retrieval methods (GETBULK) p Used is version v2c (simple security model) n v3 – RFC3411 ... RFC3418 (w/security) p Typically we use SNMPv2 (v2c) SNMP roles p Terminology: n Manager (the monitoring station) n Agent (running on the equipment/server) How does it work? p Basic commands n GET (manager → agent) p Query for a value n GET-NEXT (manager → agent) p Get next value (e.g. -

Emerging Solutions in Time Synchronization Security
Emerging Solutions in Time Synchronization Security Karen O’Donoghue, [email protected] IEEE/NIST Challenges in the Smart Grid Workshop, 7 September 2014 www.internetsociety.org Agenda • Why Security Now? • Requirements • What currently exists? • IEEE 1588 • IETF NTP NTS • Next steps and parting thoughts… IEEE/NIST Time Challenges in Smart Grid Workshop – 26 Oct 2016 Why Security Now? • Increasing interconnection and decentralization • Increasing evidence of the impact of inadequate security • Interdependency between security and time • Legal and Compliance requirements 3 IEEE/NIST Time Challenges in Smart Grid Workshop – 26 Oct 2016 Requirements for Time Synchronization Security § RFC 7384: Security Requirements of Time Protocols in Packet Switched Networks, Oct 2014 – Threat model § Internal versus external attacker § Man-in-the-middle versus injection § Threats § Requirements analysis § IEEE 1588 requirements analysis – https://ieee-sa.centraldesktop.com/1588/file/27229936/ – (contact me for access to this document if necessary) 4 IEEE/NIST Time Challenges in Smart Grid Workshop – 26 Oct 2016 RFC 7384: Threats • Manipulation of time synchronization packets, • Masquerading as a legitimate participant in the time synchronization protocol, • Replay of legitimate packets, • Tricking nodes into believing time from the wrong master, • Intercepting and removing valid synchronization packets, • Delaying legitimate time synchronization packets on the network, • Denial of service attacks on the network at layer 2 and layer 3, • Denial of service by overloading the cryptographic processing components, • Denial of service by overloading the time synchronization protocol, • Corruption of the time source used by the grand master, • Protocol design and implementation vulnerabilities, and • Using the time synchronization protocol for broader network surveillance and fingerprinting types of activities. -

Timing Needs in Cable Networks
Timing Needs in Cable Networks Yair Neugeboren Director System Architecture, Network and Cloud, ARRIS ITSF 2017 Outline • What is a Cable Network? • Timing Aspects in Cable • Distributed Architecture and Timing Requirements • Mobile Backhaul Support through Cable Networks Copyright 2017 – ARRIS Enterprises, LLC. All rights reserved 09 October 2017 2 Outline • What is a Cable Network? • Timing Aspects in Cable • Distributed Architecture and Timing Requirements • Mobile Backhaul Support through Cable Networks Copyright 2017 – ARRIS Enterprises, LLC. All rights reserved 09 October 2017 3 Cable Services Delivery - Today Commercial Residential Web Surf + OTT Video Voice Data Video Video Digital Analog Telephone Services Services Conferencing On Demand Television Television Gaming HFC Channelized Network Downstream [MHz] Copyright 2017 – ARRIS Enterprises, LLC. All rights reserved 09 October 2017 5 What is DOCSIS? The cable TV industry came together in the late 90’s and set up a group called CableLabs They created a set of specifications called Data Over Cable Service Interface Specifications, or DOCSIS for short DOCSIS defines the electrical and logical interfaces specification for network and RF elements in a cable network DOCSIS is a Point to Multipoint Protocol Downstream is continuous “One to Many” Upstream is dynamically scheduled BW allocation DOCSIS versions are 1.0, 1.1, 2.0, 3.0 and 3.1 Copyright 2017 – ARRIS Enterprises, LLC. All rights reserved 09 October 2017 6 Customer Assurance Lawful Cable Network TopologyRecord / Billing Systems Enforcement Back Office Northbound API The HFC network provides the communications link between the CMTS/CCAP and the stations, STBs, CMs and eMTAs. SDN Controller Abstrac on & Applica on HFC plant consists of up to ~160 km of optical fiber, fewLogi chundred meters of coaxial cable, RF distributions and Amplifiers.