Which Hardware Platform Best Protects Client Pcs? Software Alone Can’T Defend Against Modern Threats
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AMD Ryzen™ PRO & Athlon™ PRO Processors Quick Reference Guide
AMD Ryzen™ PRO & Athlon™ PRO Processors Quick Reference guide AMD Ryzen™ PRO Processors with Radeon™ Graphics for Business Laptops (Socket FP6/FP5) 1 Core/Thread Frequency Boost/Base L2+L3 Cache Graphics Node TDP Intel vPro Core/Thread Frequency Boost*/Base L2+L3 Cache Graphics Node TDP AMD PRO technologies COMPARED TO 4.9/1.1 Radeon™ 6/12 UHD AMD Ryzen™ 7 PRO 8/16 Up to 12MB Graphics 7nm 15W intel Intel Core i7 10810U GHz 13MB 4750U 4.1/1.7 GHz CORE i7 14nm 15W (7 Cores) 10th Gen Intel Core i7 10610U 4/8 4.9/1.8 9MB UHD GHz AMD Ryzen™ 7 PRO Up to Radeon™ intel 4/8 6MB 10 12nm 15W 4.8/1.9 3700U 4.0/2.3 GHz Vega CORE i7 Intel Core i7 8665U 4/8 9MB UHD 14nm 15W 8th Gen GHz Radeon™ AMD Ryzen™ 5 PRO 6/12 Up to 11MB Graphics 7nm 15W intel 4.4/1.7 4650U 4.0/2.1 GHz CORE i5 Intel Core i5 10310U 4/8 7MB UHD 14nm 15W GHz (6 Cores) 10th Gen AMD Ryzen™ 5 PRO 4/8 Up to 6MB Radeon™ 12nm 15W intel 4.1/1.6 3500U 3.7/2.1 GHz Vega8 CORE i5 Intel Core i5 8365U 4/8 7MB UHD 14nm 15W th GHz 8 Gen Radeon™ AMD Ryzen™ 3 PRO 4/8 Up to 6MB Graphics 7nm 15W intel 4.1/2.1 4450U 3.7/2.5 GHz CORE i3 Intel Core i3 10110U 2/4 5MB UHD 14nm 15W (5 Cores) 10th Gen GHz AMD Ryzen™ 3 PRO 4/4 Up to 6MB Radeon™ 12nm 15W intel 3.9/2.1 3300U 3.5/2.1 GHz Vega6 CORE i3 Intel Core i3 8145U 2/4 4.5MB UHD 14nm 15W 8th Gen GHz AMD Athlon™ PRO Processors with Radeon™ Vega Graphics for Business Laptops (Socket FP5) AMD Athlon™ PRO Up to Radeon™ intel Intel Pentium 4415U 2/4 2.3 GHz 2.5MB HD 610 14nm 15W 300U 2/4 3.3/2.4 GHz 5MB Vega3 12nm 15W 1. -

AMD's Early Processor Lines, up to the Hammer Family (Families K8
AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) Dezső Sima October 2018 (Ver. 1.1) Sima Dezső, 2018 AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) • 1. Introduction to AMD’s processor families • 2. AMD’s 32-bit x86 families • 3. Migration of 32-bit ISAs and microarchitectures to 64-bit • 4. Overview of AMD’s K8 – K10.5 (Hammer-based) families • 5. The K8 (Hammer) family • 6. The K10 Barcelona family • 7. The K10.5 Shanghai family • 8. The K10.5 Istambul family • 9. The K10.5-based Magny-Course/Lisbon family • 10. References 1. Introduction to AMD’s processor families 1. Introduction to AMD’s processor families (1) 1. Introduction to AMD’s processor families AMD’s early x86 processor history [1] AMD’s own processors Second sourced processors 1. Introduction to AMD’s processor families (2) Evolution of AMD’s early processors [2] 1. Introduction to AMD’s processor families (3) Historical remarks 1) Beyond x86 processors AMD also designed and marketed two embedded processor families; • the 2900 family of bipolar, 4-bit slice microprocessors (1975-?) used in a number of processors, such as particular DEC 11 family models, and • the 29000 family (29K family) of CMOS, 32-bit embedded microcontrollers (1987-95). In late 1995 AMD cancelled their 29K family development and transferred the related design team to the firm’s K5 effort, in order to focus on x86 processors [3]. 2) Initially, AMD designed the Am386/486 processors that were clones of Intel’s processors. -

AMD Raven Ridge
DELIVERING A NEW LEVEL OF VISUAL PERFORMANCE IN AN SOC AMD “RAVEN RIDGE” APU Dan Bouvier, Jim Gibney, Alex Branover, Sonu Arora Presented by: Dan Bouvier Corporate VP, Client Products Chief Architect AMD CONFIDENTIAL RAISING THE BAR FOR THE APU VISUAL EXPERIENCE Up to MOBILE APU GENERATIONAL 200% MORE CPU PERFORMANCE PERFORMANCE GAINS Up to 128% MORE GPU PERFORMANCE Up to 58% LESS POWER FIRST “Zen”-based APU CPU Performance GPU Performance Power HIGH-PERFORMANCE AMD Ryzen™ 7 2700U 7th Gen AMD A-Series APU On-die “Vega”-based graphics Scaled GPU Managed Improved Upgraded Increased LONG BATTERY LIFE and CPU up to power delivery memory display package Premium form factors reach target and thermal bandwidth experience performance frame rate dissipation efficiency density 2 | AMD Ryzen™ Processors with Radeon™ Vega Graphics - Hot Chips 30 | * See footnotes for details. “RAVEN RIDGE” APU AMD “ZEN” x86 CPU CORES CPU 0 “ZEN” CPU CPU 1 (4 CORE | 8 THREAD) USB 3.1 NVMe PCIe FULL PCIe GPP ----------- ----------- Discrete SYSTEM 4MB USB 2.0 SATA GFX CONNECTIVITY CPU 2 CPU 3 L3 Cache X64 DDR4 HIGH BANDWIDTH SOC FABRIC System Infinity Fabric & MEMORY Management SYSTEM Unit ACCELERATED Platform Multimedia Security MULTIMEDIA Processor Engines AMD GFX+ 1MB L2 EXPERIENCE X64 DDR4 (11 COMPUTE UNITS) Cache Video Audio Sensor INTEGRATED CU CU CU CU CU CU Display Codec ACP Fusion Controller Next SENSOR Next Hub FUSION HUB CU CU CU CU CU AMD “VEGA” GPU UPGRADED DISPLAY ENGINE 3 | AMD Ryzen™ Processors with Radeon™ Vega Graphics - Hot Chips 30 | SIGNIFICANT DENSITY INCREASE “Raven Ridge” die BGA Package: 25 x 35 x 1.38mm Technology: GLOBALFOUNDRIES 14nm – 11 layer metal Transistor count: 4.94B 59% 16% Die Size: 209.78mm2 more transistors smaller die than prior generation “Bristol Ridge” APU 4 | AMD Ryzen™ Processors with Radeon™ Vega Graphics - Hot Chips 30 | * See footnotes for details. -
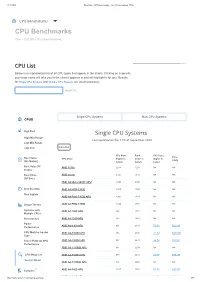
CPU Benchmarks - List of Benchmarked Cpus
11.09.2020 PassMark - CPU Benchmarks - List of Benchmarked CPUs CPU Benchmarks CPU Benchmarks Over 1,000,000 CPUs Benchmarked CPU List Below is an alphabetical list of all CPU types that appear in the charts. Clicking on a specific processor name will take you to the chart it appears in and will highlight it for you. Results for Single CPU Systems and Multiple CPU Systems are listed separately. Find CPU Single CPU Systems Multi CPU Systems CPUS High End Single CPU Systems High Mid Range Last updated on the 11th of September 2020 Low Mid Range Low End Column CPU Mark Rank CPU Value Price Best Value CPU Name (higher is (lower is (higher is (USD) (On Market) better) better) better) Best Value XY AMD 3015e 2,678 1285 NA NA Scatter Best Value AMD 3020e 2,721 1272 NA NA (All time) AMD A4 Micro-6400T APU 1,004 2126 NA NA New Desktop AMD A4 PRO-3340B 1,519 1790 NA NA New Laptop AMD A4 PRO-7300B APU 1,421 1839 NA NA Single Thread AMD A4 PRO-7350B 1,024 2108 NA NA Systems with AMD A4-1200 APU 445 2572 NA NA Multiple CPUs Overclocked AMD A4-1250 APU 432 2583 NA NA Power AMD A4-3300 APU 994 2131 76.50 $12.99 Performance CPU Mark by Socket AMD A4-3300M APU 665 2394 22.19 $29.99* Type Cross-Platform CPU AMD A4-3305M APU 807 2273 38.78 $20.81 Performance AMD A4-3310MX APU 844 2239 NA NA CPU Mega List AMD A4-3320M APU 877 2212 23.77 $36.90 Search Model AMD A4-3330MX APU 816 2265 NA NA 0 1,067 2078 Compare AMD A4-3400 APU 53.35 $20.00 https://www.cpubenchmark.net/cpu_list.php AMD A4 3420 APU 8 01 $12 9 * 1/87 11.09.2020 PassMark - CPU Benchmarks - List -

AMD Introduces World's Most Powerful 16- Core
November 7, 2019 AMD Introduces World’s Most Powerful 16- core Consumer Desktop Processor, the AMD Ryzen™ 9 3950X – AMD Ryzen™ 9 3950X rounds out 3rd Gen Ryzen desktop processor series, arriving November 25 – – New AMD Athlon™ 3000G processor to provide everyday users with unmatched performance per dollar, coming November 19 – SANTA CLARA, Calif., Nov. 07, 2019 (GLOBE NEWSWIRE) -- Today, AMD announced the release of the highly anticipated flagship 16-core AMD Ryzen 9 3950X processor, available worldwide November 25, 2019. AMD Ryzen 9 3950X processor brings the ultimate processor for gamers with effortless 1080P gaming in select titles1 and up to 2X more energy efficient processing power compared to the competition2 as the world’s fastest 16- core consumer desktop processor3. In addition, AMD also announced a significant performance uplift4 coming for mainstream desktop users with the new AMD Athlon 3000G, arriving November 19, 2019. “We are excited to bring the AMD Ryzen™ 9 3950X to market later this month, offering enthusiasts the most powerful 16-core desktop processor ever,” said Chris Kilburn, corporate vice president and general manager, client channel, AMD. “We are focused on offering the best solutions at every level of the market, including the AMD Athlon 3000G for everyday PC users that delivers great performance at an incredible price point.” AMD Ryzen 9 3950X: Fastest 16-core Consumer Desktop Processor Offering up to 22% performance increase over previous generations5, the AMD Ryzen 9 3950X offers faster 1080p gaming in select titles1 and content creation6 than the competition. Built on the industry-leading “Zen 2” architecture, the AMD Ryzen 9 3950X also excels in power efficiency3 with a TDP7 of 105W. -

Amd's Commitment To
This presentation contains forward-looking statements concerning Advanced Micro Devices, Inc. (AMD) such as AMD’s journey; the proposed transaction with Xilinx, Inc. including expectations, benefits and plans of the proposed transaction; total addressable markets; AMD’s technology roadmaps; the features, functionality, performance, availability, timing and expected benefits of future AMD products; AMD’s path forward in data center, PCs and gaming; and AMD’s 2021 financial outlook, long-term financial model and ability to drive shareholder returns, which are made pursuant to the Safe Harbor provisions of the Private Securities Litigation Reform Act of 1995. Forward looking statements are commonly identified by words such as "would," "may," "expects," "believes," "plans," "intends," "projects" and other terms with similar meaning. Investors are cautioned that the forward- looking statements in this presentation are based on current beliefs, assumptions and expectations, speak only as of the date of this presentation and involve risks and uncertainties that could cause actual results to differ materially from current expectations. Such statements are subject to certain known and unknown risks and uncertainties, many of which are difficult to predict and generally beyond AMD's control, that could cause actual results and other future events to differ materially from those expressed in, or implied or projected by, the forward-looking information and statements. Investors are urged to review in detail the risks and uncertainties in AMD’s Securities and Exchange Commission filings, including but not limited to AMD’s most recent reports on Forms 10-K and 10-Q. AMD does not assume, and hereby disclaims, any obligation to update forward-looking statements made in this presentation, except as may be required by law. -

Optimizing for AMD Ryzen
AMD RYZEN™ CPU OPTIMIZATION Presented by Ken Mitchell & Elliot Kim AMD RYZEN™ CPU OPTIMIZATION ABSTRACT Join AMD ISV Game Engineering team members for an introduction to the AMD Ryzen™ CPU followed by advanced optimization topics. Learn about the “Zen” microarchitecture, power management, and CodeXL profiler. Gain insight into code optimization opportunities using hardware performance-monitoring counters. Examples may include assembly and C/C++. ‒ Ken Mitchell is a Senior Member of Technical Staff in the Radeon Technologies Group/AMD ISV Game Engineering team where he focuses on helping game developers utilize AMD CPU cores efficiently. Previously, he was tasked with automating & analyzing PC applications for performance projections of future AMD products. He studied computer science at the University of Texas at Austin. ‒ Elliot Kim is a Senior Member of Technical Staff in the Radeon Technologies Group/AMD ISV Game Engineering team where he focuses on helping game developers utilize AMD CPU cores efficiently. Previously, he worked as a game developer at Interactive Magic and has since gained extensive experience in 3D technology and simulations programming. He holds a BS in Electrical Engineering from Northeastern University in Boston. 3 | GDC17 AMD RYZEN CPU OPTIMIZATION | 2017-03-02 | AMD AGENDA Introduction ‒Microarchitecture ‒Power Management ‒Profiler Optimization ‒Compiler ‒Concurrency ‒Shader Compiler ‒Prefetch ‒Data Cache 4 | GDC17 AMD RYZEN CPU OPTIMIZATION | 2017-03-02 | AMD Introduction Microarchitecture “Zen” MICROARCHITECTURE AN UNPRECEDENTED IPC IMPROVEMENT Updated Feb 28, 2017: Generatinal IPCuplift for the “Zen” architecture vs. “Piledriver” architecture is +52% with an estimated SPECint_base2006 score compiled with GCC 4.6 –O2 at a fixed 3.4GHz. Generational IPC uplift for the “Zen” architecture vs. -

Ideapad 3 15ADA05 Reference
PSREF Product Specifications IdeaPad 3 15ADA05 Reference OVERVIEW 1. Power button 5. HDMI 1.4b 2. Card reader 6. USB 2.0 3. Headphone / microphone combo jack (3.5mm) 7. 2x USB 3.2 Gen 1 4. Power connector IdeaPad 3 15ADA05 - August 17 2021 1 of 7 PSREF Product Specifications IdeaPad 3 15ADA05 Reference PERFORMANCE Processor Processor Family AMD 3000, AMD Athlon™, or AMD Ryzen™ 3 / 5 / 7 Processor Processor Base Max Memory Processor Name Cores Threads Cache Processor Graphics Frequency Frequency Support 1MB L2 / AMD 3020e 2 2 1.2GHz 2.6GHz DDR4-2400 AMD Radeon™ Graphics 4MB L3 AMD Athlon Silver 1MB L2 / 2 2 2.3GHz 3.2GHz DDR4-2400 AMD Radeon Graphics 3050U 4MB L3 AMD Athlon Gold 1MB L2 / 2 4 2.4GHz 3.3GHz DDR4-2400 AMD Radeon Graphics 3150U 4MB L3 AMD Ryzen 3 1MB L2 / 2 4 2.6GHz 3.5GHz DDR4-2400 AMD Radeon Graphics 3250U 4MB L3 AMD Ryzen 5 2MB L2 / AMD Radeon Vega 8 4 8 2.1GHz 3.7GHz DDR4-2400 3500U 4MB L3 Graphics AMD Ryzen 7 2MB L2 / AMD Radeon RX Vega 10 4 8 2.3GHz 4.0GHz DDR4-2400 3700U 4MB L3 Graphics Operating System Operating System • Windows® 10 Home 64 • Windows 10 Home in S mode • Windows 10 Pro 64 • FreeDOS • No operating system Graphics Graphics Graphics Type Memory Key Features AMD Radeon Graphics Integrated Shared DirectX® 12 AMD Radeon Vega 8 Graphics Integrated Shared DirectX 12 AMD Radeon RX Vega 10 Graphics Integrated Shared DirectX 12 Monitor Support Monitor Support Supports up to 2 independent displays via native display and 1 external monitor; supports external monitor via HDMI® (up to 3840x2160@30Hz) Chipset Chipset AMD SoC (System on Chip) platform Memory Max Memory[1] • Up to 8GB (8GB SO-DIMM) DDR4-2400 offering (AMD 3020e models) • Up to 12GB (4GB soldered + 8GB SO-DIMM) DDR4-2400 offering (Athlon or Ryzen models) Memory Slots • One DDR4 SO-DIMM slot (AMD 3020e models) • One memory soldered to systemboard, one DDR4 SO-DIMM slot, dual-channel capable (Athlon or Ryzen models) Memory Type IdeaPad 3 15ADA05 - August 17 2021 2 of 7 PSREF Product Specifications IdeaPad 3 15ADA05 Reference DDR4-2400 Notes: 1. -
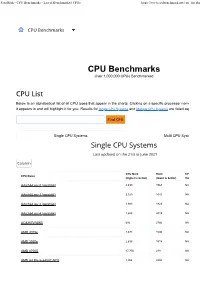
CPU Benchmarks - List of Benchmarked Cpus
PassMark - CPU Benchmarks - List of Benchmarked CPUs https://www.cpubenchmark.net/cpu_list.php CPU Benchmarks Over 1,000,000 CPUs Benchmarked Below is an alphabetical list of all CPU types that appear in the charts. Clicking on a specific processor name will take you to the ch it appears in and will highlight it for you. Results for Single CPU Systems and Multiple CPU Systems are listed separately. Single CPU Systems Multi CPU Systems CPU Mark Rank CPU Value CPU Name (higher is better) (lower is better) (higher is better) AArch64 rev 0 (aarch64) 2,499 1567 NA AArch64 rev 1 (aarch64) 2,320 1642 NA AArch64 rev 2 (aarch64) 1,983 1823 NA AArch64 rev 4 (aarch64) 1,653 2019 NA AC8257V/WAB 693 2766 NA AMD 3015e 2,678 1506 NA AMD 3020e 2,635 1518 NA AMD 4700S 17,756 238 NA AMD A4 Micro-6400T APU 1,004 2480 NA PassMark - CPU Benchmarks - List of Benchmarked CPUs https://www.cpubenchmark.net/cpu_list.php CPU Mark Rank CPU Value CPU Name (higher is better) (lower is better) (higher is better) AMD A4 PRO-7300B APU 1,481 2133 NA AMD A4 PRO-7350B 1,024 2465 NA AMD A4-1200 APU 445 3009 NA AMD A4-1250 APU 428 3028 NA AMD A4-3300 APU 961 2528 9.09 AMD A4-3300M APU 686 2778 22.86 AMD A4-3305M APU 815 2649 39.16 AMD A4-3310MX APU 785 2680 NA AMD A4-3320M APU 640 2821 16.42 AMD A4-3330MX APU 681 2781 NA AMD A4-3400 APU 1,031 2458 9.51 AMD A4-3420 APU 1,052 2443 7.74 AMD A4-4000 APU 1,158 2353 38.60 AMD A4-4020 APU 1,214 2310 13.34 AMD A4-4300M APU 997 2486 33.40 AMD A4-4355M APU 816 2648 NA AMD A4-5000 APU 1,282 2257 NA AMD A4-5050 APU 1,328 2219 NA AMD A4-5100 -
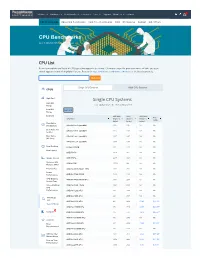
CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android Ios / Iphone
Software Hardware Benchmarks Services Store Support About Us Forums 0 CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone CPU Benchmarks Over 1,000,000 CPUs Benchmarked CPU List Below is an alphabetical list of all CPU types that appear in the charts. Clicking on a specific processor name will take you to the chart it appears in and will highlight it for you. Results for Single CPU Systems and Multiple CPU Systems are listed separately. Find CPU Single CPU Systems Multi CPU Systems CPUS High End Single CPU Systems High Mid Range Last updated on the 28th of May 2021 Low Mid Column Range Low End CPU Mark Rank CPU Value Price CPU Name (higher is (lower is (higher is (USD) better) better) better) Best Value (On Market) AArch64 rev 0 (aarch64) 2,335 1605 NA NA Best Value XY AArch64 rev 1 (aarch64) 2,325 1606 NA NA Scatter Best Value AArch64 rev 2 (aarch64) 1,937 1807 NA NA (All time) AArch64 rev 4 (aarch64) 1,676 1968 NA NA New Desktop AC8257V/WAB 693 2730 NA NA New Laptop AMD 3015e 2,678 1472 NA NA Single Thread AMD 3020e 2,637 1481 NA NA Systems with AMD 4700S 17,756 222 NA NA Multiple CPUs Overclocked AMD A4 Micro-6400T APU 1,004 2445 NA NA Power Performance AMD A4 PRO-3340B 1,706 1938 NA NA CPU Mark by AMD A4 PRO-7300B APU 1,481 2097 NA NA Socket Type Cross-Platform AMD A4 PRO-7350B 1,024 2428 NA NA CPU Performance AMD A4-1200 APU 445 2969 NA NA AMD A4-1250 APU 428 2987 NA NA CPU Mega List AMD A4-3300 APU 961 2494 53.40 $18.00* Search Model AMD A4-3300M APU 686 2740 22.86 $29.99* 0 Compare AMD -

AMD Announces World's Best Mobile Processors¹ in CES 2021 Keynote
January 12, 2021 AMD Announces World’s Best Mobile Processors¹ In CES 2021 Keynote AMD Ryzen Threadripper PRO Processors, designed for the most demanding professional workloads, coming to retail channel SANTA CLARA, Calif., Jan. 12, 2021 (GLOBE NEWSWIRE) -- CES 2021 -- Today, AMD (NASDAQ: AMD) announced the full portfolio of AMD Ryzen™ 5000 Series Mobile Processors, bringing the highly-efficient and extremely powerful “Zen 3” core architecture to the laptop market. New AMD Ryzen 5000 Series Mobile Processors provide unprecedented levels of performance and incredible battery life for gamers, creators, and professionals. New laptops powered by Ryzen 5000 Series Mobile processors will be available from major PC manufacturers including ASUS, HP and Lenovo, starting in Q1 2021. Expanding its leadership client computing product portfolio featuring the “Zen 3” core, AMD also announced the AMD Ryzen PRO 5000 Series Mobile Processors, delivering enterprise- grade security and seamless manageability to commercial users. Throughout the course of 2021, AMD expects a broad portfolio of more than 150 consumer and commercial notebooks based on the Ryzen 5000 Series Mobile Processors. “As the PC becomes an even more essential part of how we work, play and connect, users demand more performance, security and connectivity,” said Saeid Moshkelani, senior vice president and general manager, Client business unit, AMD. “The new AMD Ryzen 5000 Series Desktop and Mobile Processors bring the best innovation AMD has to offer to consumers and professionals as we continue our commitment to delivering best-in-class experiences with instant responsiveness, incredible battery life and fantastic designs. With our PC partners, we are delivering top-quality performance and no-compromise solutions alongside our record-breaking growth in the notebook and desktop space in the previous year.” AMD Ryzen 5000 Series Mobile Processors Building upon the previous generation of leadership mobile processors, the Ryzen 5000 Series includes high-performance H- and ultra-mobile U-Series processors. -

Cs433 Amd Zen 2
CS433 AMD ZEN 2 Hyoungwook Nam (hn5) Anjana Suresh Kumar (anjanas3) Vibhor Dodeja (vdodeja2) Namrata Mantri (nmantri2) Table of Contents 1. Overview 2. Pipeline Structure 3. Memory Hierarchy 4. Security and Power 5. Takeaways Overview History of AMD's x86 microarchitectures (1) K5 - K7 (95~02) K8 (03~08) K10 (09~11) x86 frontend, RISC backend Introduced x86-64 ISA Up to 6 cores Superscalar, OoO, speculation Dual-core (Athlon 64 X2) Shared L3 cache SIMD, L2 cache (K6) Integrated memory controller GPU integrated APUs (Fusion) https://www.tomshardware.com/picturestory/713-amd-cpu-history.html History of AMD's x86 microarchitectures (2) Bulldozer (11~16) Zen (17 ~ ) Multi-core module (MCM) Simultaneous Multi-thread (SMT) Two cores per module Two threads per core Shared FP and L2 in a module Higher single-thread performance AMD Financial Analyst Day, May 2015 Multi-core Module (MCM) Structure of Zen Single EPYC Package Single Die (Chiplet) Multiple dies in a package, 2 core complexes (ccx) per die, and up to 4 cores per ccx. (~4c8t per die) Fully connected NUMA between dies with infinity fabric (IF) which also interconnects ccx. https://www.slideshare.net/AMD/amd-epyc-microprocessor-architecture Zen 2 Changes Over Zen 1 and Zen+ Dedicated IO chiplet using hybrid process - TSMC 7nm CPU cores + GF 14nm IO chiplet 2x more cores per package - up to 16 for consumer and 64 for server More ILP - Better predictor, wider execution, deeper window, etc. 2x Larger L3 and faster IF2 Extra security features against spectre attacks https://www.pcgamesn.com/amd/amd-zen-2-release-date-specs-performance