Monitoring of Servers and Server Rooms by Iot System That Can Configure and Control Its Terminal Sensors Behind a NAT Using a Wiki Page on the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Synthesiology”, a New Academic Journal
MESSAGES FROM THE EDITORIAL BOARD There has been a wide gap between science and society. The last three hundred years of the history of modern science indicates to us that many research results disappeared or took a long time to become useful to society. Due to the difficulties of bridging this gap, it has been recently called the valley of death or the nightmare stage (Note 1). Rather than passively waiting, therefore, researchers and engineers who understand the potential of the research should be active. To bridge the gap, technology integration (i.e. Type 2 Basic Research − Note 2) of scientific findings for utilizing them in society, in addition to analytical research, has been one of the wheels of progress (i.e. Full Research − Note 3). Traditional journals, have been collecting much analytical type knowledge that is factual knowledge and establishing many scientific disciplines (i.e. Type 1 Basic Research − Note 4). Technology integration research activities, on the other hand, have been kept as personal know-how. They have not been formalized as universal knowledge of what ought to be done. As there must be common theories, principles, and practices in the methodologies of technology integration, we regard it as basic research. This is the reason why we have decided to publish “Synthesiology”, a new academic journal. Synthesiology is a coined word combining “synthesis” and “ology”. Synthesis which has its origin in Greek means integration. Ology is a suffix attached to scientific disciplines. Each paper in this journal will present scenarios selected for their societal value, identify elemental knowledge and/or technologies to be integrated, and describe the procedures and processes to achieve this goal. -

Emacs-W3m User's Manual
This file documents emacs-w3m, an Emacs interface tow3m. This edition is for emacs-w3m version 1.4.567. Emacs-w3m User's Manual An Emacs interface to w3m for emacs-w3m version 1.4.567 The emacs-w3m development team Copyright c 2000-2014 TSUCHIYA Masatoshi Permission is granted to copy, distribute and/or modify this document under the terms of the GNU General Public License, Version 2 or any later version published by the Free Software Foundation. This document is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABIL- ITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. You should have received a copy of the GNU General Public License along with this document; see the file COPYING. If not, write to the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA. i Table of Contents Emacs-w3m User's Manual :::::::::::::::::::::::: 1 1 Preliminary remarks:::::::::::::::::::::::::::: 2 2 It's so easy to begin to use emacs-w3m ::::::: 3 2.1 What version of Emacs can be used? ::::::::::::::::::::::::::: 3 2.2 Using w3m: the reason why emacs-w3m is fast:::::::::::::::::: 3 2.3 Things required to run emacs-w3m ::::::::::::::::::::::::::::: 3 2.4 Installing emacs-w3m :::::::::::::::::::::::::::::::::::::::::: 5 2.5 Installing on non-UNIX-like systems :::::::::::::::::::::::::::: 6 2.6 Minimal settings to run emacs-w3m :::::::::::::::::::::::::::: 7 3 Basic usage :::::::::::::::::::::::::::::::::::::: 8 -

Index Images Download 2006 News Crack Serial Warez Full 12 Contact
index images download 2006 news crack serial warez full 12 contact about search spacer privacy 11 logo blog new 10 cgi-bin faq rss home img default 2005 products sitemap archives 1 09 links 01 08 06 2 07 login articles support 05 keygen article 04 03 help events archive 02 register en forum software downloads 3 security 13 category 4 content 14 main 15 press media templates services icons resources info profile 16 2004 18 docs contactus files features html 20 21 5 22 page 6 misc 19 partners 24 terms 2007 23 17 i 27 top 26 9 legal 30 banners xml 29 28 7 tools projects 25 0 user feed themes linux forums jobs business 8 video email books banner reviews view graphics research feedback pdf print ads modules 2003 company blank pub games copyright common site comments people aboutus product sports logos buttons english story image uploads 31 subscribe blogs atom gallery newsletter stats careers music pages publications technology calendar stories photos papers community data history arrow submit www s web library wiki header education go internet b in advertise spam a nav mail users Images members topics disclaimer store clear feeds c awards 2002 Default general pics dir signup solutions map News public doc de weblog index2 shop contacts fr homepage travel button pixel list viewtopic documents overview tips adclick contact_us movies wp-content catalog us p staff hardware wireless global screenshots apps online version directory mobile other advertising tech welcome admin t policy faqs link 2001 training releases space member static join health -

Dtwiki: a Disconnection and Intermittency Tolerant Wiki
DTWiki: A Disconnection and Intermittency Tolerant Wiki Bowei Du Eric A. Brewer Computer Science Division Computer Science Division 445 Soda Hall 623 Soda Hall University of California, Berkeley University of California, Berkeley Berkeley, CA 94720-1776 Berkeley, CA 94720-1776 [email protected] [email protected] ABSTRACT which the users can participate in writing Wikipedia articles. The Wikis have proven to be a valuable tool for collaboration and con- popularity of “wikis” [4] as website content management software tent generation on the web. Simple semantics and ease-of-use make also speaks to the usefulness of the medium. Generally speaking, wiki systems well suited for meeting many emerging region needs wikis have proven to be an excellent tool for collaboration and con- in the areas of education, collaboration and local content genera- tent generation. tion. Despite their usefulness, current wiki software does not work Several aspects of wikis are interesting for the emerging regions well in the network environments found in emerging regions. For context. First, there is a great need in emerging regions for content example, it is common to have long-lasting network partitions due that is locally relevant. Local content can take a variety of forms, to cost, power and poor connectivity. Network partitions make a from a local translation of existing online material to the commu- traditional centralized wiki architecture unusable due to the un- nity knowledge bases. Most of the content on the web today is availability of the central server. Existing solutions towards ad- written in English and targeted towards in the industrialized world. -

Stardas Pakalnis) • the Contextit Project
Streamspin: Mobile Services for The Masses Christian S. Jensen www.cs.aau.dk/~csj Overview • Web 2.0 • The mobile Internet • The Streamspin system • Tracking of moving objects AAU, September 10, 2007 2 Web 2.0 • Web 2.0 captures the sense that there is something qualitatively different about today's web. • Leveraging the collective intelligence of communities • New ways of interacting • Sharing of user-generated content • Text Wiki’s, e.g., Wikipedia Blogs • Photos E.g., Flickr, Plazes, 23 • Video E.g., YouTube AAU, September 10, 2007 3 Web 2.0 • Community concepts abound… • Feedback and rating schemes E.g., ratings of sellers and buyers at auctions, ratings of content • Social tagging, tag clouds, folksonomies • Wiki’s Collaborative authoring • RSS feeds • Active web sites, Ajax • Fueled by Google-like business models Google 2006 revenue: USD 10.6 billion; net income: USD 3.1 billion; 12k employees Microsoft now has 8k people in Online Services AAU, September 10, 2007 4 Flickr • From the Flickr entry on Wikipedia • “In addition to being a popular Web site for users to share personal photographs, the service is widely used by bloggers as a photo repository. Its popularity has been fueled by its innovative online community tools that allow photos to be tagged and browsed by folksonomic means.” • Launched in February 2004. Acquired by Yahoo! in March 2005. Updated from beta to gamma in May 2006. • “On December 29th, 2006 the upload limits on free accounts were increased to 100Mb a month (from 20Mb)” AAU, September 10, 2007 5 YouTube • From the YouTube entry on Wikipedia • “The domain name "YouTube.com" was activated on February 15, 2005…” • “According to a July 16, 2006 survey, 100 million clips are viewed daily on YouTube, with an additional 65,000 new videos uploaded per 24 hours.” • “Currently staffed by 67 employees, the company was named TIME magazine's "Invention of the Year" for 2006. -

Software Knowledge Management Using Wikis: a Needs and Features Analysis
FACULDADE DE ENGENHARIA DA UNIVERSIDADE DO PORTO Software Knowledge Management using Wikis: a needs and features analysis Rafael Araújo Pires FINAL VERSION Report of Dissertation Master in Informatics and Computing Engineering Supervisor: Ademar Manuel Teixeira de Aguiar (PhD) Co-Supervisor: João Carlos Pascoal de Faria (PhD) March 2010 Software Knowledge Management using Wikis: a needs and features analysis Rafael Araújo Pires Report of Dissertation Master in Informatics and Computing Engineering Approved in oral examination by the committee: Chair: Maria Cristina Ribeiro (PhD) ____________________________________________________ External Examiner: Isabel Ramos (PhD) Internal Examiner: Ademar Manuel Teixeira de Aguiar (PhD) March 25, 2010 Abstract Knowledge Management is a sub-section of management that pursuits improvement in business performance. It increases the organization's ability to learn, to innovate, to solve problems and aims to enhance organizational knowledge processing. It is looking for the available and required knowledge assets that are divided as tangible and intangible. Tangible assets, which are related to explicit knowledge, include manuals, customer information, news, employees, patent licenses, proposals, project artifacts, etc. Intangible assets, which are related to tacit knowledge, include skills, experiences and knowledge of employees within the organization. It is a method that simplifies the process of sharing, distributing, creating, capturing, and understanding a company’s knowledge. The challenges involved -

A Simple Application Program Interface for Saving Java Program Data on a Wiki
Hindawi Publishing Corporation Advances in Software Engineering Volume 2012, Article ID 981783, 9 pages doi:10.1155/2012/981783 Research Article A Simple Application Program Interface for Saving Java Program Data on a Wiki Takashi Yamanoue, Kentaro Oda, and Koichi Shimozono Computing and Communications Center, Kagoshima University, Korimoto, Kagoshima 890-0065, Japan Correspondence should be addressed to Takashi Yamanoue, [email protected] Received 14 November 2011; Revised 18 January 2012; Accepted 23 January 2012 Academic Editor: Andreas Menychtas Copyright © 2012 Takashi Yamanoue et al. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. A simple application program interface (API) for Java programs running on a wiki is implemented experimentally. A Java program with the API can be running on a wiki, and the Java program can save its data on the wiki. The Java program consists of PukiWiki, which is a popular wiki in Japan, and a plug-in, which starts up Java programs and classes of Java. A Java applet with default access privilege cannot save its data at a local host. We have constructed an API of applets for easy and unified data input and output at a remote host. We also combined the proposed API and the wiki system by introducing a wiki tag for starting Java applets. It is easy to introduce new types of applications using the proposed API. We have embedded programs such as a simple text editor, a simple music editor, a simple drawing program, and programming environments in a PukiWiki system using this API. -

A Sensor Network for the Internet of Things Integrated with a Bidirectional Backend
Degree Project Electrical Engineering July 2014 A sensor network for the Internet of Things Integrated with a bidirectional backend Linus Hobring Philip Söderberg Department of Communication Systems (DIKO) Blekinge Institute of Technology 371 79 Karlskrona Sweden This thesis is submitted to the Department of Communication Systems at Blekinge Institute of Technology in partial fulfillment of the requirements for the degree of Master of Science in Electrical Engineering with emphasis on Telecommunication Systems. The thesis is equivalent to 20 weeks of full time studies. Contact Information: Authors: Linus Hobring and Philip Söderberg E-mail: linus{dot}hobring{at}gmail.com and philip{dot}soderberg{at}gmail.com External advisor: Ruwan Lakmal Silva University advisor: Markus Fiedler Department of communication Systems Department of Communication Systems Internet : www.bth.se Blekinge Institute of Technology Phone : +46 455 38 50 00 371 79 Karlskrona Fax : +46 455 38 50 57 Sweden ii ABSTRACT Internet of Things is rapidly evolving. This thesis includes a study of single-board computers suitable for machine-to-machine communication together with the developing process of a sensor network integrated with a bidirectional communication platform. Raspberry Pi was selected as the single-board computer used in the proposed system. The Message Queuing Telemetry Transport protocol was selected as main communication protocol to handle all exchange of information between the network and the bidirectional communication platform. It was selected because of its reliability, low bandwidth and publish/subscribe architecture. Decision-making procedures were implemented to work with both local sensor data and data from different Message Queuing Telemetry Transport streams, such as GPS data, used to calculate the distance between the user’s smart phone and the office to prepare the workstation, temperature sensors and ambient light sensors controlling Philips HUE light bulbs. -
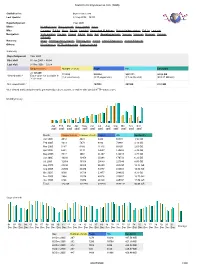
Statistics for Brynosaurus.Com (2005)
Statistics for brynosaurus.com (2005) Statistics for: brynosaurus.com Last Update: 27 Sep 2006 − 06:00 Reported period: Year 2005 When: Monthly history Days of month Days of week Hours Who: Countries Full list Hosts Full list Last visit Unresolved IP Address Robots/Spiders visitors Full list Last visit Navigation: Visits duration File type Viewed Full list Entry Exit Operating Systems Versions Unknown Browsers Versions Unknown Referers: Origin Refering search engines Refering sites Search Search Keyphrases Search Keywords Others: Miscellaneous HTTP Status codes Pages not found Summary Reported period Year 2005 First visit 01 Jan 2005 − 00:04 Last visit 31 Dec 2005 − 23:54 Unique visitors Number of visits Pages Hits Bandwidth <= 125249 151229 328224 2621111 94.06 GB Viewed traffic * Exact value not available in (1.2 visits/visitor) (2.17 pages/visit) (17.33 hits/visit) (652.17 KB/visit) 'Year' view Not viewed traffic * 167672 261929 7.32 GB * Not viewed traffic includes traffic generated by robots, worms, or replies with special HTTP status codes. Monthly history Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec 2005 2005 2005 2005 2005 2005 2005 2005 2005 2005 2005 2005 Month Unique visitors Number of visits Pages Hits Bandwidth Jan 2005 4012 4621 8432 62678 1.93 GB Feb 2005 4919 5671 8892 79888 2.10 GB Mar 2005 5487 6460 11410 93405 2.66 GB Apr 2005 6941 8147 23657 130853 3.49 GB May 2005 7517 9004 21307 139015 3.71 GB Jun 2005 10393 12458 25968 170723 6.32 GB Jul 2005 12958 15156 28649 225540 8.05 GB Aug 2005 22292 25919 46389 355390 -

Qwikweb: Integrating Mailing List and Wikiwikiweb for Group Communication
qwikWeb: integrating mailing list and WikiWikiWeb for group communication ¤ Kouichirou Eto, Satoru Takabayashi and Toshiyuki Masui National Institute of Advanced Industrial Science and Technology Akihabara Daibiru 10F,1-18-13 Sotokanda, Chiyoda-ku, Tokyo 101-0021, JAPAN. fk-eto, s.takabayashi, [email protected] ABSTRACT have been used for a long time. A mailing list is a single e-mail ac- We have developed a new powerful group communication system count which represents a set of e-mail addresses. When an e-mail qwikWeb, which is an integration of a WikiWikiWeb (wiki) and a message is sent to the address of a mailing list, the message is for- mailing list system. Mailing lists are useful for exchanging dy- warded to all the addresses which are registered as members of the namic information among people, but not useful for sharing static mailing list. If you make a mailing list for a group, you don’t have information. Wikis are useful for storing and editing static infor- to send messages to all the members, but you only have to send a mation on the Web, but sometimes people want to restrict the users single message to the mailing list address. or want to know who is responsible for the edited wiki page. Also, Although mailing lists are widely used these days, using them is casual users cannot create a wiki site or a mailing list easily. not always the best way for sharing information, because of the fol- We solved these problems by combining wiki and mailing list. lowing reasons. -

Wikiで実現する軽妙ウェブサイト
Wikiで実現する軽妙ウェブサイト 塚本 牧生 <[email protected]> アジェンダ 1. はじめに 2. Wikiの利用事例から 3. Wikiのシステム構築 1 1. はじめに 1. はじめに 2. Wikiの利用事例から 3. Wikiのシステム構築 1. はじめに 1.1 Wikiを使ってますか? 1.2 Wikiとは何か。 1.3 Wikiの歴史。 2 1.1 Wikiを使ってますか? 1.1 Wikiを使ってますか? 1.2 Wikiとは何か。 1.3 Wikiの歴史。 1.1 Wikiを使ってますか? Web and Internet Application Day(※) JUSによるInternet Week 2004でのカンファレンス blog、Wiki、SNSの3セッション(各1時間40分) Wikiセッションは… Wikiに興味がある人、Wiki利用者向け 他セッション同様、定員200名の会場がほぼ満席の盛況 ※ http://www.nic.ad.jp/iw2004/program/C10.html 3 1.1 Wikiを使ってますか? 第4回Wikiばな「Wiki博覧会」開催 2005年にshino、塚本他で企画、開催 スタンダードなWiki4種と先鋭的なWiki十数種を紹介 一つを除き、開発者自身が紹介 Wiki実装者、設置者など技術者向け 発表者13名、スタッフ11名、一般参加者50名 1.1 Wikiを使ってますか? livedoor Wikiサービス開始 2005年7月にベータ版としてサービス開始 2005年8月に正式版としてサービス開始 正式サービス開始時点4,500サイト、4万ページ 1,000ページ超の巨大サイト 10名以上で更新しているWikiらしいサイト 4 1.1 Wikiを使ってますか? Wikiを使うことは、特別なことではなくなっている Wikiを使うことは、特別なことではなくなっている。 あなたはWikiを使っていますか? 1.2 Wikiとは何か。 1.1 Wikiを使ってますか? 1.2 Wikiとは何か。 1.3 Wikiの歴史。 5 1.2 Wikiとは何か。 掲示板とは何か? 定義はない。 説明はできない。 イメージは共有できている。 blogとは何か? 定義はない。 説明はできない。 イメージは共有できている。 1.2 Wikiとは何か。 Wikiとは何か? 定義はない。 説明はできない。 イメージも共有されてない? ↓ まずは「Wikiとはどんなものか」イメージ 6 1.2 Wikiとは何か。 編集可能なWebサイト。 今見ているページをブラウザ上ですぐに編集できる。 今見ているページをブラウザ上ですぐに削除できる。 新しいページをブラウザ上で追加作成できる。 1.2 Wikiとは何か。 HTML不要のWeb作成ツール。 一覧も表も「それっぽく書くだけ」のWiki記法。 ページ名やURLがリンクになるオートリンク。 * WikiWikiとは? WikiWikiは、Web上で共同オーサリングをできるサイトを構築するためのツールです。 もっと簡単に言いましょう。 - 誰でもページを作成したり修正できるシステムがWikiWikiです。 - 書き方は普通のテキストとほとんど同じ、誰でもすぐに慣れます。 -- 参照 : WikiWikiRules ** Wikiクローン WikiWikiとそのクローンは、CGIなどの形で配布されています。 7 1.2 Wikiとは何か。 原始的だけど自由なデータベース。 -

Interactive Semantic Wikis Deliverable D1.1
Integrated Project Priority 2.4.7 Semantic based knowledge systems Interactive Semantic Wikis Deliverable D1.1 Version 1.0 08.01.2007 Dissemination level: PU Nature Prototype Due date 31.12.2006 Lead contractor Cognium Systems SA Start date of project 01.01.2006 Duration 36 months NEPOMUK 08.01.2007 Authors COG: Mikhail Kotelnikov, Alexander Polonsky DFKI: Malte Kiesel FZI: Max Völkel, Heiko Haller IBM: Mikhail Sogrin KTH: Pär Lannerö NUIG: Brian Davis Mentors DFKI: Ansgar Bernardi DFKI: Thomas Roth-Berghofer Project Co-ordinator Dr. Ansgar Bernardi German Research Center for Artificial Intelligence (DFKI) GmbH Erwin-Schroedinger-Strasse (Building 57) D 67663 Kaiserslautern Germany Email: [email protected], phone: +49 631 205 3582, fax: +49 631 205 4910 Partners DEUTSCHES FORSCHUNGSZENTRUM FUER KUENSTLICHE INTELLIGENZ GMBH (DFKI) IBM IRELAND PRODUCT DISTRIBUTION LIMITED (IBM) SAP AG (SAP) HEWLETT PACKARD GALWAY LTD (HPGL) THALES S.A. (TRT) PRC GROUP - THE MANAGEMENT HOUSE S.A. (PRC) EDGE-IT S.A.R.L (EDG) COGNIUM SYSTEMS S.A. (COG) NATIONAL UNIVERSITY OF IRELAND, GALWAY (NTUA) ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL) FORSCHUNGSZENTRUM INFORMATIK AN DER UNIVERSITAET KARLSRUHE (FZI) UNIVERSITAET HANNOVER (L3S) INSTITUTE OF COMMUNICATION AND COMPUTER SYSTEMS (ICCS) KUNGLIGA TEKNISKA HOEGSKOLAN (KTH) UNIVERSITA DELLA SVIZZERA ITALIANA (USI) IRION MANAGEMENT CONSULTING GMBH (IMC) Copyright: NEPOMUK Consortium 2006 Copyright on template: Irion Management Consulting GmbH 2006 Deliverable D1.1 Version 1.0 2 NEPOMUK 08.01.2007 Versions