Product Updates New L7 Signatures
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
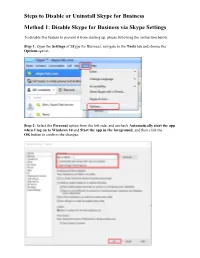
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center
VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center Table of Contents Click on any of the titles below to be navigated to that section SLI POLICIES ........................................................................................................................... 1 USING TIGERZONE TO YOUR ADVANTAGE .............................................................................. 1 ONLINE MEETING PLATFORMS ............................................................................................... 2 ONLINE BROADCASTING PLATFORMS ..................................................................................... 3 ONLINE CHAT PLATFORMS ..................................................................................................... 3 VIDEO CONFERENCE TIPS (for Zoom) ...................................................................................... 4 VIRTUAL ENGAGEMENT IDEAS ............................................................................................... 5 VIRTUAL ENTERTAINMENT ..................................................................................................... 6 SLI POLICIES During Phase 1 there are to be NO IN PERSON STUDENT EVENTS. This applies to events both ON and OFF campus. If your organization is found to be hosting in person events you will be given ONE warning from Student Leadership & Involvement. If your organization is found to be hosting student events a second time your organization will be suspended for the remainder of the 2020-2021 -

Is Our Privacy Being Compromised As We Speak? Eavesdropper's Heaven
IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.10, October 2017 119 Is our privacy being compromised as we speak? Eavesdropper’s heaven or a nightmare? A study of Mobile Voice over Internet Protocol (mVoIP) and Instant Messaging (IM) Applications. Farhan Ahmed Muhammad Ahsan Muhammad Saeed Nasir Touheed Siddiqui Najam Department of Computer Department of Computer Department of Computer Department of Computer Science, University of Science, IBA Karachi Science, University of Science, University of Karachi Pakistan Karachi Karachi Karachi, Pakistan Karachi, Pakistan Karachi, Pakistan Abstract around these applications, these two key areas are not at all In the recent times, mobile voice over internet protocol (mVoIP) explored and there are only a handful of studies if at all applications have been greatly adopted by the masses and have which examine aspect of these so called “perfect really captured much of the attention in the application market applications”. Majority of the people who use these place. These applications not only provide voice communication applications aren’t even aware of the fact that anyone can with little to no cost but also offer instant messaging service. basically intercept their communication and if the People across the world use applications like this and some even communicate daily with others just by using these applications communication is not encrypted, can easily read and misuse rather than the conventional way of text messages and GSM calls. their information. Other than this, is the communication With applications consolidating millions and millions of users, encrypted at the servers or is the privacy of the user in the security and privacy is a topic which many prefer not to discuss. -

Timeline 1994 July Company Incorporated 1995 July Amazon
Timeline 1994 July Company Incorporated 1995 July Amazon.com Sells First Book, “Fluid Concepts & Creative Analogies: Computer Models of the Fundamental Mechanisms of Thought” 1996 July Launches Amazon.com Associates Program 1997 May Announces IPO, Begins Trading on NASDAQ Under “AMZN” September Introduces 1-ClickTM Shopping November Opens Fulfillment Center in New Castle, Delaware 1998 February Launches Amazon.com Advantage Program April Acquires Internet Movie Database June Opens Music Store October Launches First International Sites, Amazon.co.uk (UK) and Amazon.de (Germany) November Opens DVD/Video Store 1999 January Opens Fulfillment Center in Fernley, Nevada March Launches Amazon.com Auctions April Opens Fulfillment Center in Coffeyville, Kansas May Opens Fulfillment Centers in Campbellsville and Lexington, Kentucky June Acquires Alexa Internet July Opens Consumer Electronics, and Toys & Games Stores September Launches zShops October Opens Customer Service Center in Tacoma, Washington Acquires Tool Crib of the North’s Online and Catalog Sales Division November Opens Home Improvement, Software, Video Games and Gift Ideas Stores December Jeff Bezos Named TIME Magazine “Person Of The Year” 2000 January Opens Customer Service Center in Huntington, West Virginia May Opens Kitchen Store August Announces Toys “R” Us Alliance Launches Amazon.fr (France) October Opens Camera & Photo Store November Launches Amazon.co.jp (Japan) Launches Marketplace Introduces First Free Super Saver Shipping Offer (Orders Over $100) 2001 April Announces Borders Group Alliance August Introduces In-Store Pick Up September Announces Target Stores Alliance October Introduces Look Inside The BookTM 2002 June Launches Amazon.ca (Canada) July Launches Amazon Web Services August Lowers Free Super Saver Shipping Threshold to $25 September Opens Office Products Store November Opens Apparel & Accessories Store 2003 April Announces National Basketball Association Alliance June Launches Amazon Services, Inc. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

CCIA Comments in ITU CWG-Internet OTT Open Consultation.Pdf
CCIA Response to the Open Consultation of the ITU Council Working Group on International Internet-related Public Policy Issues (CWG-Internet) on the “Public Policy considerations for OTTs” Summary. The Computer & Communications Industry Association welcomes this opportunity to present the views of the tech sector to the ITU’s Open Consultation of the CWG-Internet on the “Public Policy considerations for OTTs”.1 CCIA acknowledges the ITU’s expertise in the areas of international, technical standards development and spectrum coordination and its ambition to help improve access to ICTs to underserved communities worldwide. We remain supporters of the ITU’s important work within its current mandate and remit; however, we strongly oppose expanding the ITU’s work program to include Internet and content-related issues and Internet-enabled applications that are well beyond its mandate and core competencies. Furthermore, such an expansion would regrettably divert the ITU’s resources away from its globally-recognized core competencies. The Internet is an unparalleled engine of economic growth enabling commerce, social development and freedom of expression. Recent research notes the vast economic and societal benefits from Rich Interaction Applications (RIAs), a term that refers to applications that facilitate “rich interaction” such as photo/video sharing, money transferring, in-app gaming, location sharing, translation, and chat among individuals, groups and enterprises.2 Global GDP has increased US$5.6 trillion for every ten percent increase in the usage of RIAs across 164 countries over 16 years (2000 to 2015).3 However, these economic and societal benefits are at risk if RIAs are subjected to sweeping regulations. -

IM Security Documentation on Page Vi
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release notes, and/or the latest version of the applicable documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/trend-micro-im-security.aspx Trend Micro, the Trend Micro t-ball logo, Control Manager, MacroTrap, and TrendLabs are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2016. Trend Micro Incorporated. All rights reserved. Document Part No.: TIEM16347/140311 Release Date: September 2016 Protected by U.S. Patent No.: Pending This documentation introduces the main features of the product and/or provides installation instructions for a production environment. Read through the documentation before installing or using the product. Detailed information about how to use specific features within the product may be available at the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Privacy and Personal Data Collection Disclosure Certain features available in Trend Micro products collect and send feedback regarding product usage and detection information to Trend Micro. Some of this data is considered personal in certain jurisdictions and under certain regulations. -

Technology Requirements for Using Video Conferencing with Victims
Technology Requirements for Using Video Conferencing with Victims Videoconferencing can offer survivors an alternative way to meet with a provider or counselor. For survivors who lack transportation or live too far from a program or counselor, videoconferencing may be the only way they can obtain medical, legal, or trauma-informed therapy. There are several free or low cost (if upgraded) web-based conference services, each with different advantages and technical requirements. (For more information on safety and privacy considerations when using video conferencing, read “Tips for Using Video Conferencing for Victim Services.”) Types of Web-Based Services and Technical Requirements There are many factors to consider when choosing a web-based video conferencing system, including cost, operating systems, whether calls can be recorded, and how many people can be on a call at the same time. All web-conferencing systems require a connection to the Internet and can be used with either Windows or Mac. The systems reviewed here include Skype, Google Hangouts, Oovoo, Gruveo, and Zoom. Note that the systems reviewed here are available for free or for minimal costs. Some paid-for services may offer more features, security, and privacy. An important consideration in choosing a web-based conferencing system is the degree to which data is encrypted. This means whether data is encrypted indicating no one but the users can access the data or whether the data can be viewed and accessed by the service provider. This may be critical should the service provider receive a subpoena for your data. All of the systems below offer instant messaging, in-call chat, an unlimited number of meetings, and a telephone call-in option while video conferencing. -

Contextual Typeahead Sticker Suggestions on Hike Messenger
Contextual Typeahead Sticker Suggestions on Hike Messenger Mohamed Hanoosh1 , Abhishek Laddha1 and Debdoot Mukherjee1 1Hike Messenger, New Delhi, India fmoh.hanoosh, abhishekl, [email protected], Abstract In this demonstration, we present Hike’s sticker recommendation system, which helps users choose the right sticker to substitute the next message that they intend to send in a chat. We describe how the system addresses the issue of numerous ortho- graphic variations for chat messages and operates under 20 milliseconds with low CPU and memory footprint on device. 1 Introduction In messaging apps such as Facebook Messenger, WhatsApp, Line and Hike, new modalities such as emojis, gifs and stick- Figure 1: Sticker Recommendation UI and a high level flow diagram ers are extensively used to visually express thoughts and emo- tions [Lim, 2015; Donato and Paggio, 2017; Barbieri et al., the most relevant stickers for a given chat context defined by 2017]. While emojis are mostly used in conjunction with text, the previous message(s) and the text typed in the chat input stickers can provide a graphic alternative for text messages box. However, due to frequent additions to the sticker inven- altogether. Hike1 stickers are composed of an artwork (e.g., tory and a massive skew in historical usage toward a hand- cartoonized characters and objects) and a stylized text for a ful of popular stickers, it becomes difficult to collect reliable, commonly used chat phrase (See stickers in Fig. 1). Hike unbiased data to train such an end-to-end model. Moreover, has tens of thousands of such stickers in different languages an end-to-end model will need to be retrained frequently to so that its users can engage in rich conversations by chatting support new stickers and the updated model will have to be with stickers back to back. -

Table of Contents
2016-2017 PARENT-STUDENT HANDBOOK De Smet Jesuit High School 233 North New Ballas Road Creve Coeur, MO 63141 (314) 567-3500 www.desmet.org DE SMET JESUIT HIGH SCHOOL Parent and Student Handbook Dear Parents: Your knowledge of the information in the Student and Parent Handbook is essential for the efficient operation of the school. Please review this handbook and discuss the guidelines with your son. Each student and his parents must sign a copy of the signature form (that your son will receive the first day of school) and return it to his homeroom teacher. Signing this form indicates that both the student and his parents have read the handbook, including policies regarding acceptable use of computers, and agree to abide by these policies. Additionally, signing this signature page acknowledges your legal and financial responsibility to De Smet Jesuit High School. Also, in an effort to communicate more efficiently, De Smet Jesuit requires at least one current parent/guardian e-mail address. Your son is to return this signed form to his homeroom teacher during the first full week of school. Friday, August 26, 2016 is the deadline. Students will be removed from the De Smet Jesuit network if they have not returned this form by August 26, 2016. There may be a 24-48 hour delay in receiving network privileges if a signed agreement is returned after that date. Additionally, an electronic version of this handbook is available at www.desmet.org. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - HANDBOOK AND COMPUTER POLICY SIGNATURE FORM __________________________________ ________________________________ NAME OF STUDENT (PLEASE PRINT) SR / JR / SO / FR ___________________________________ ______________ ______________ STUDENT SIGNATURE HOMEROOM STUDENT NO. -

Lovefilm API
LOVEFiLM API WWW::Lovefilm::API What does LOVEFiLM do? DVDs & games in the post Video on demand via PC, Sony & Samsung TVs Other devices coming soon... Use their website to view film reviews, create a rental list, play trailers, play films etc etc API Exposes lots of the functionality Can write apps to manage your rental list Search for films, actors, directors... Can serve up images for films, links to play trailers, synopsis of each film links for each actor etc etc WWW::Lovefilm::API I created it to help me learn the API I wanted to write apps but before I could do that I needed some lower level code Based on another module in CPAN... thanks to David Westbrook for his blessing OAuth Open standard Used by Twitter, Myspace, Yahoo, Google etc Open protocol to allow secure API authorisation Provides 2 levels of access A website can be given permission to access a users account on the LOVEFiLM site with out being given the users password 2 Legged Oauth 2 legged is the simplest and most common Also called ºtokenlessº No access to users data Quite a lot of the calls do not require anything more than signed requests Signing Send your application key Generate a signiture using the shared secret No need for HTTPS GET /catalog/title?expand=actors%2Csynopsis&term=batman HTTP/1.1 Server: openapi.lovefilm.com Authorization: Oauth oauth_consumer_key="2blu7svnhwkzw29zg7cwkydn", oauth_nonce="b2254b2bd8bf62423c73f1", oauth_signature="h7aMKlgTuE3FvnUIoNWNNuM42Gw%3D", oauth_signature_method="HMAC-SHA1", oauth_timestamp="1256822344", oauth_version="1.0" 3 Legged More of a ºdanceº A user moves from your website/app to the LOVEFiLM web site and you are asked if you wish to give permision to your app.