Stop the Abuse of Gmail!
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Understanding Post Office Protocol (POP3)
Understanding Post Office Protocol (POP3) Author: Conrad Chung, 2BrightSparks Introduction Most Internet users with email accounts would have used some form of “client” software (Outlook, Thunderbird etc.) to access and manage their email at one point or another. To retrieve emails, these email clients may require the configuration of Post Office Protocol (or POP3) before messages can be downloaded from the server. This article will help readers understand what POP3 is and how it works. What is Post Office Protocol? The Post Office Protocol (POP3) is an Internet standard protocol used by local email software clients to retrieve emails from a remote mail server over a TCP/IP connection. Since the first version was created in 1984, the Post Office Protocol (currently at Version 3) has since became one of the most popular protocols and is used by virtually every email client to date. Its popularity lies in the protocol’s simplicity to configure, operate and maintain. Email servers hosted by Internet service providers also use POP3 to receive and hold emails intended for their subscribers. Periodically, these subscribers will use email client software to check their mailbox on the remote server and download any emails addressed to them. Once the email client has downloaded the emails, they are usually deleted from the server, although some email clients allow users to specify that mails be copied or saved on the server for a period of time. Email clients generally use the well-known TCP port 110 to connect to a POP3 server. If encrypted communication is supported on the POP3 server, users can optionally choose to connect either by using the STLS command after the protocol initiation stage or by using POP3S, which can use the Transport Layer Security (TLS) or Secure Sockets Layer (SSL) on TCP port 995 to connect to the server. -

Imail V12 Web Client Help
Ipswitch, Inc. Web: www.imailserver.com 753 Broad Street Phone: 706-312-3535 Suite 200 Fax: 706-868-8655 Augusta, GA 30901-5518 Copyrights ©2011 Ipswitch, Inc. All rights reserved. IMail Server – Web Client Help This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. Except as permitted by such license, no part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the expressed prior written consent of Ipswitch, Inc. The content of this manual is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Ipswitch, Inc. While every effort has been made to assure the accuracy of the information contained herein, Ipswitch, Inc. assumes no responsibility for errors or omissions. Ipswitch, Inc. also assumes no liability for damages resulting from the use of the information contained in this document. Ipswitch Collaboration Suite (ICS), the Ipswitch Collaboration Suite (ICS) logo, IMail, the IMail logo, WhatsUp, the WhatsUp logo, WS_FTP, the WS_FTP logos, Ipswitch Instant Messaging (IM), the Ipswitch Instant Messaging (IM) logo, Ipswitch, and the Ipswitch logo are trademarks of Ipswitch, Inc. Other products and their brands or company names are or may be trademarks or registered trademarks, and are the property of their respective companies. Update History December 2011 v12 April 2011 v11.5 October 2010 v11.03 May 2010 v11.02 Contents CHAPTER 1 Introduction to IMail Web Client About Ipswitch Web Messaging Help .................................................................................................................. -

'Order Denying the Motion to Dismiss As to the Merits Of
Case 5:15-cv-04062-LHK Document 49 Filed 08/12/16 Page 1 of 38 1 2 3 4 5 6 7 8 UNITED STATES DISTRICT COURT 9 NORTHERN DISTRICT OF CALIFORNIA 10 SAN JOSE DIVISION 11 12 DANIEL MATERA, Case No. 15-CV-04062-LHK 13 Plaintiff, ORDER DENYING MOTION TO DISMISS AS TO THE MERITS OF 14 v. PLAINTIFF’S CLAIMS 15 GOOGLE INC., Re: Dkt. No. 20 16 Defendant. 17 United States District Court District United States Northern District of California District Northern 18 Plaintiff Daniel Matera (“Plaintiff”), individually and on behalf of those similarly situated, 19 alleges that Defendant Google Inc. (“Google”) violated federal and state wiretapping laws in its 20 operation of Gmail, an email service. ECF No. 1 (“Compl.”).1 Before the Court is Google’s 21 motion to dismiss for failure to state a claim. ECF No. 20. Having considered the parties’ 22 submissions, the relevant law, and the record in this case, the Court DENIES Google’s motion to 23 dismiss as to the merits of Plaintiff’s claims. The Court will issue a separate order on standing 24 issues. 25 26 1 27 Unless otherwise noted, all ECF references are to the docket of 15-CV-04062 in the Northern District of California. 28 1 Case No. 15-CV-04062-LHK ORDER DENYING MOTION TO DISMISS AS TO THE MERITS OF PLAINTIFF’S CLAIMS Case 5:15-cv-04062-LHK Document 49 Filed 08/12/16 Page 2 of 38 I. BACKGROUND 1 A. Factual Background 2 1. In re Google Inc. -

Tools to Trace Path Between Server and Web Applications Over Internet
Proceedings of the UGC Sponsored National Conference on Advanced Networking and Applications, 27th March 2015 Tools to Trace Path between Server and Web Applications over Internet P Veeralakshmi Department of Computer Science, Sourashtra College, Madurai-5 [email protected] A Dhavapandiammal Department of Computer Application, Sourashtra College, Madurai-5 [email protected] --------------------------------------------------------ABSTRACT------------------------------------------------------- The rise of the Internet and the worldwideweb had a wide revolution not only in network communications but also in application design and development. It is common to captured pieces of business functionality into distinct objects or components, and then made them available as self-contained Web services that can be accessed using Internet-based protocols and tools. Some tools Smartsniff, Httpnetworksniffer, Winwebcrawler, Wireshark, Network Manager and WebLogAnalyzer are discussed to trace the path between client request and server response, history report of path travelled. Keywords: network manager, protocols, report, webcrawler, wireshark ---------------------------------------------------------------------------------------------------------------- 1.Introduction the web server and displays them in a simple table. for The Internet is itself an enormous network, so whenever we every http request, the following information is displayed: access the Internet, we are using a network. The Web is host name, http method -
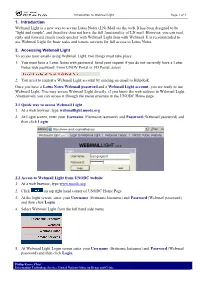
1. Introduction Webmail Light Is a New Way to Access Lotus Notes (LN) Mail Via the Web
Introduction to Webmail Light Page 1 of 2 1. Introduction Webmail Light is a new way to access Lotus Notes (LN) Mail via the web. It has been designed to be "light and simple", and therefore does not have the full functionality of LN mail. However, you can read, reply and forward emails much quicker with Webmail Light than with Webmail. It is recommended to use Webmail Light for basic tasks and remote services for full access to Lotus Notes. 2. Accessing Webmail Light To access your emails using Webmail Light, two things must take place: 1. You must have a Lotus Notes web password. Send your request if you do not currently have a Lotus Notes web password. From UNOV Portal or FO Portal, select 2. You need to request a Webmail Light account by sending an email to Helpdesk. Once you have a Lotus Notes Webmail password and a Webmail Light account, you are ready to use Webmail Light. You may access Webmail Light directly, if you know the web address to Webmail Light. Alternatively you can access it through the menu structure in the UNODC Home page. 2.1 Quick way to access Webmail Light 1. At a web browser, type webmaillight.unodc.org 2. At Login screen, enter your Username (firstname.lastname) and Password (Webmail password) and then click Login. 2.2 Access to Webmail Light from UNODC website 1. At a web browser, type www.unodc.org 2. Click on top right hand corner of UNODC Home Page. 3. At the login screen, enter your Username (firstname.lastname) and Password (Webmail password) and then click Login. -
![Full Report [PDF]](https://docslib.b-cdn.net/cover/3654/full-report-pdf-1153654.webp)
Full Report [PDF]
SPECIAL ANALYSIS OurWhere Shifting the Jobs Are: EconomicOur Region’s and PopulationOccupational ProfilesStructure JOINT VENTURE’S 2004 index of silicon valley MEASURING PROGRESS TOWARD THE GOALS OF SILICON VALLEY 2010 Joint Venture: Silicon Valley Network Joint Venture: Silicon Valley Network is a regional, nonpartisan voice and a civic catalyst for solutions to problems that impact all sectors of the community. Joint Venture brings together established and emerging leaders from business, labor, government, education, nonprofits and the broader community to build a sustainable region that competes globally. We work to promote economic prosperity and improve the quality of life in the region, making Silicon Valley a better place to live and work. Joint Venture welcomes your participation in its various activities, which are described in detail at www.jointventure.org. PREPARED BY: INDEX ADVISERS COLLABORATIVE KRIS CASTO STEPHEN LEVY NANCY RAGEY ECONOMICS Santa Clara County Cities Association Center for Continuing Study of the Community Foundation Silicon Valley DOUG HENTON MIKE CURRAN California Economy ANNALEE SAXENIAN JOHN MELVILLE NOVA Workforce Board WILL LIGHTBOURNE University of California, Berkeley Santa Clara County Social Services LIZ BROWN JANE DECKER ANN SKEET Santa Clara County Agency American Leadership Forum: ERICA BJORNSSON MIKE EVANHOE JOHN MALTBIE Silicon Valley HEIDI YOUNG Santa Clara Valley Transportation San Mateo County STERLING SPEIRN Authority CONNIE MARTINEZ Peninsula Community Foundation MARGUERITE GONG HANCOCK Children’s -

You Can Configure Microsoft Outlook to Access Your Office 365 Account by Setting up an Exchange Connection
You can configure Microsoft Outlook to access your Office 365 account by setting up an Exchange connection. An Exchange connection provides access your email, calendar, contacts, and tasks in Outlook. You can also set up Outlook to access your email by using IMAP. However, if you use IMAP you can only access your email from Outlook, not your calendar, contacts, and tasks. Notes: ▪ Office 365 is designed to work with any version of Microsoft Office in mainstream support. Get Outlook for Windows Outlook is included with Microsoft Office 365. Faculty and staff with a Thiel ID and undergraduate students with an Office 365 account can download Microsoft Office for Windows via webmail for free. Please visit the Solution Center webpage for more information. Configure Outlook for Windows 1. Open Outlook. 2. At the Welcome screen, click Next. 3. When asked if you want to set up Outlook to connect to an email account, select Yes and then click Next. 4. The Auto Account Setup wizard opens. Enter your name, your email address using your ID#@thiel.edu, and your Thiel ID network password. Then, click Next 5. Outlook will complete the setup for your account, which might take several minutes. When you are notified that your account was successfully configured, click Finish. 6. You may need to restart Outlook for the changes to take effect. Change offline access setting You can use Outlook on your laptop or desktop computer when you’re not connected to the Internet. Email, calendar, and other items are kept in an Outlook data file on your computer so you can work offline. -

Phenomenological, Postphenomenological, and Posthumanistic Explorations
Email and Its Involvements in the Lives of K-12 Teachers: Phenomenological, Postphenomenological, and Posthumanistic Explorations by Joni McBeth Turville A thesis submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy Department of Secondary Education University of Alberta © Joni McBeth Turville, 2018 i ABSTRACT Web-connected devices are everywhere and can be used to send electronic messages, no matter the time or place. They are not merely tools or a means to an end; they also shape our everyday lives. In kindergarten to Grade 12 (K-12) schools, teachers are increasingly contacted by parents, students, colleagues, and others. They have reported that digital communication can be overwhelming when added to what teachers typically do outside regular work hours, such as planning, grading, and writing student reports. Using email as a critical example of a digital communications tool, this study examines the experiences of K-12 teachers in receiving email outside their regular work hours. Inspired by Max van Manen’s phenomenological approach entitled “Phenomenology of Practice”, this research explores experiences situated in this professional context. Interviews were conducted with 24 teachers in Alberta, Canada from Grades K to 12 to collect lived experience descriptions or examples of receiving email outside regular work hours as they were lived through. This research also uses postphenomenology in order to gain insight into the past, present, and future of email and proposes a model to describe the evolution of digital communications tools. The final chapter explores a posthumanistic approach related to both phenomenology and postphenomenology called “interviewing objects” to uncover what email may be producing. -
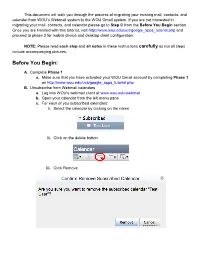
Before You Begin
This document will walk you through the process of migrating your existing mail, contacts, and calendar from WOU’s Webmail system to the WOU Gmail system. If you are not interested in migrating your mail, contacts, and calendar please go to Step C from the Before You Begin section. Once you are finished with this tutorial, visit http://www.wou.edu/ucs/google_apps_tutorial.php and proceed to phase 3 for mobile device and desktop client configuration. NOTE: Please read each step and all notes in these instructions carefully as not all steps include accompanying pictures. Before You Begin: A. Complete Phase 1 a. Make sure that you have activated your WOU Gmail account by completing Phase 1 on http://www.wou.edu/ucs/google_apps_tutorial.php B. Unsubscribe from Webmail calendars a. Log into WOU’s webmail client at www.wou.edu/webmail b. Open your calendar from the left menu pane c. For each of you subscribed calendars: i. Select the calendar by clicking on the name ii. Click on the delete button iii. Click Remove C. Setting up your Gmail account a. Log into your Gmail account at http://gmail.mail.wou.edu b. Click on Settings in the upper right-hand corner of the screen c. Click on the Accounts tab d. Click on Add another email address you own e. Enter your name and WOU email address and click Next Step f. Click Send Notification g. Return to your inbox h. You should have an email with the subject “Western Oregon University Confirmation - Send Mail as [email protected].” If you do not see this email, wait 2 minutes and refresh your inbox. -

A Survey of Current Research on Captcha
International Journal of Computer Science & Engineering Survey (IJCSES) Vol.7, No.3, June 2016 A SURVEY OF CURRENT RESEARCH ON CAPTCHA Walid Khalifa Abdullah Hasan Aljabel AlGharbi University,Faculty of Eng-Jadu ,EE dept, Gharyan, Libya ABSTRACT The internet has been playing an increasingly important role in our daily life, with the availability of many web services such as email and search engines. However, these are often threatened by attacks from computer programs such as bots. To address this problem, CAPTCHA (Completely Automated Public Turing Test to Tell Computers and Humans Apart) was developed to distinguish between computer programs and human users. Although this mechanism offers good security and limits automatic registration to web services, some CAPTCHAs have several weaknesses which allow hackers to infiltrate the mechanism of the CAPTCHA. This paper examines recent research on various CAPTCHA methods and their categories. Moreover it discusses the weakness and strength of these types. KEYWORDS CAPTCHA (Completely Automated Public Turing test to tell Computers and Human Apart), Bot programs, Hackers, spammer, Scrapers ,search engines. 1.INTRODUCTION The internet contributes profoundly to many aspects of human life such as communications, education, and online commercial activities etc. Some web services have online registration where the users provide information in order to connect and use services such as email in Yahoo, Gmail and Hotmail. However, many programs have been developed by hackers which automatically complete website registration pages with incorrect information which can cause traffic congestion, minimizing the performance of the system and in some cases, even causing it to fail, particularly where a website has a huge number of accounts. -

Email Transfer from Webmail to Gmail
Email Transfer from Webmail to Gmail Product: Google Mail Symptom: Transfer Webmail to Gmail Solution: Transfer Webmail to Gmail Footprints Public Solution #70834 In Your Oakland University Email Account 1. Click the gear in the top right corner then click Settings from the dropdown menu 2. Select Forwarding and POP/IMAP tab and then Enable POP for all mail (even mail that has already been downloaded) 3. Click Save Changes at the bottom of the screen Setting up 2-Step Verification and App Specific Password 1. Click on the circle with a letter in the top right corner and click My Account 2. Click Sign-in & security 3. Scroll down and click 2-Step Verification 4. Click Get Started 5. Type in your phone number and choose if you would like to receive a text or a phone call 6. You will need to input the code you received and click Next 7. You will the need to click Turn On to enable 2-Step Verification 8. Click the back arrow to go back to the Sign-in & security settings 9. Scroll down and click App passwords 10. Click Select Device and then choose Other (Custom name) 11. Name the device gmail then click Generate 12. A password will be generated. Copy the password, you will use it later In Your New Gmail Account 1. Click the gear in the top right corner then click Settings 2. Select the Accounts and Import tab then click Add a mail account 3. Type in your Oakland University email address in the popup window then click Next 4. -

Personal & Contextual Portability and Plasticity with Opensocial
Widgets and Spaces: Personal & Contextual Portability and Plasticity with OpenSocial THÈSE NO 5804 (2013) PRÉSENTÉE LE 30 AOUT 2013 À LA FACULTÉ DES SCIENCES ET TECHNIQUES DE L'INGÉNIEUR INSTITUT DE GÉNIE ÉLECTRIQUE ET ÉLECTRONIQUE PROGRAMME DOCTORAL EN INFORMATIQUE, COMMUNICATIONS ET INFORMATION ÉCOLE POLYTECHNIQUE FÉDÉRALE DE LAUSANNE POUR L'OBTENTION DU GRADE DE DOCTEUR ÈS SCIENCES PAR Evgeny BOGDANOV acceptée sur proposition du jury: Dr A. Karimi, président du jury Dr D. Gillet, Dr C. Salzmann, directeurs de thèse Dr E. L.-C. Law, rapporteur Dr L. Moccozet, rapporteur Dr C. Ullrich, rapporteur Suisse 2013 A person who never made a mistake never tried anything new — Albert Einstein To my parents. Acknowledgments This thesis is only partially my work. It would not be possible without my friends, relatives, colleagues who were helping me (knowingly or unknowingly) during this PhD journey. I am hugely grateful to all of you! Denis Gillet and Christophe Salzmann. Thank you for accepting me into your research family, for giving me the freedom in choosing and shaping the research directions according to my interests, for being my mentors. After our discussions I was always leaving your office inspired and highly motivated. This is indeed something! I would like to thank my thesis committee members for reading my thesis and being my examinators: Alireza Karimi, Effie Lai-Chong Law, Carsten Ullrich, Laurent Moccozet. My research work was partially funded through the following projects: ROLE, PALETTE, SWITCH, GO-LAB. I am thankful to these projects and I did appreciate working in them. Stéphane Sire, I owe you a huge chunk of my thesis and my personal development.