Webmail User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dark Internet Mail Environment (DIME) Terminology, Architecture, Security, Data Formats, and Protocol Specifications
COVER DEDICATION I would like to dedicate this project to the National Security Agency. For better or worse, good or evil, what follows would not have been created without you. Because sometimes upholding constitutional ideas just isn’t enough; sometimes you have to uphold the actual Constitution. May god bless these United States of America. May she once again become the land of the free and home of the brave. Ladar Levison CONTENTS Cover ......................................................................................................................................................................................................... 1 Dedication ................................................................................................................................................................................................. 2 Contents .................................................................................................................................................................................................... 3 Figures ...................................................................................................................................................................................................... 11 Overview ................................................................................................................................................................................................ 12 Part 1: Abstract .................................................................................................................................................................................... -

Understanding Post Office Protocol (POP3)
Understanding Post Office Protocol (POP3) Author: Conrad Chung, 2BrightSparks Introduction Most Internet users with email accounts would have used some form of “client” software (Outlook, Thunderbird etc.) to access and manage their email at one point or another. To retrieve emails, these email clients may require the configuration of Post Office Protocol (or POP3) before messages can be downloaded from the server. This article will help readers understand what POP3 is and how it works. What is Post Office Protocol? The Post Office Protocol (POP3) is an Internet standard protocol used by local email software clients to retrieve emails from a remote mail server over a TCP/IP connection. Since the first version was created in 1984, the Post Office Protocol (currently at Version 3) has since became one of the most popular protocols and is used by virtually every email client to date. Its popularity lies in the protocol’s simplicity to configure, operate and maintain. Email servers hosted by Internet service providers also use POP3 to receive and hold emails intended for their subscribers. Periodically, these subscribers will use email client software to check their mailbox on the remote server and download any emails addressed to them. Once the email client has downloaded the emails, they are usually deleted from the server, although some email clients allow users to specify that mails be copied or saved on the server for a period of time. Email clients generally use the well-known TCP port 110 to connect to a POP3 server. If encrypted communication is supported on the POP3 server, users can optionally choose to connect either by using the STLS command after the protocol initiation stage or by using POP3S, which can use the Transport Layer Security (TLS) or Secure Sockets Layer (SSL) on TCP port 995 to connect to the server. -

Imail V12 Web Client Help
Ipswitch, Inc. Web: www.imailserver.com 753 Broad Street Phone: 706-312-3535 Suite 200 Fax: 706-868-8655 Augusta, GA 30901-5518 Copyrights ©2011 Ipswitch, Inc. All rights reserved. IMail Server – Web Client Help This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. Except as permitted by such license, no part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the expressed prior written consent of Ipswitch, Inc. The content of this manual is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Ipswitch, Inc. While every effort has been made to assure the accuracy of the information contained herein, Ipswitch, Inc. assumes no responsibility for errors or omissions. Ipswitch, Inc. also assumes no liability for damages resulting from the use of the information contained in this document. Ipswitch Collaboration Suite (ICS), the Ipswitch Collaboration Suite (ICS) logo, IMail, the IMail logo, WhatsUp, the WhatsUp logo, WS_FTP, the WS_FTP logos, Ipswitch Instant Messaging (IM), the Ipswitch Instant Messaging (IM) logo, Ipswitch, and the Ipswitch logo are trademarks of Ipswitch, Inc. Other products and their brands or company names are or may be trademarks or registered trademarks, and are the property of their respective companies. Update History December 2011 v12 April 2011 v11.5 October 2010 v11.03 May 2010 v11.02 Contents CHAPTER 1 Introduction to IMail Web Client About Ipswitch Web Messaging Help .................................................................................................................. -
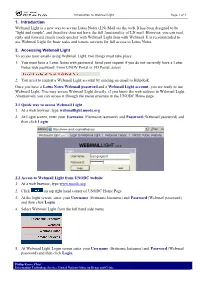
1. Introduction Webmail Light Is a New Way to Access Lotus Notes (LN) Mail Via the Web
Introduction to Webmail Light Page 1 of 2 1. Introduction Webmail Light is a new way to access Lotus Notes (LN) Mail via the web. It has been designed to be "light and simple", and therefore does not have the full functionality of LN mail. However, you can read, reply and forward emails much quicker with Webmail Light than with Webmail. It is recommended to use Webmail Light for basic tasks and remote services for full access to Lotus Notes. 2. Accessing Webmail Light To access your emails using Webmail Light, two things must take place: 1. You must have a Lotus Notes web password. Send your request if you do not currently have a Lotus Notes web password. From UNOV Portal or FO Portal, select 2. You need to request a Webmail Light account by sending an email to Helpdesk. Once you have a Lotus Notes Webmail password and a Webmail Light account, you are ready to use Webmail Light. You may access Webmail Light directly, if you know the web address to Webmail Light. Alternatively you can access it through the menu structure in the UNODC Home page. 2.1 Quick way to access Webmail Light 1. At a web browser, type webmaillight.unodc.org 2. At Login screen, enter your Username (firstname.lastname) and Password (Webmail password) and then click Login. 2.2 Access to Webmail Light from UNODC website 1. At a web browser, type www.unodc.org 2. Click on top right hand corner of UNODC Home Page. 3. At the login screen, enter your Username (firstname.lastname) and Password (Webmail password) and then click Login. -

Stored Communications Act: Reform of the Electronic Communications Privacy Act (ECPA)
Stored Communications Act: Reform of the Electronic Communications Privacy Act (ECPA) Richard M. Thompson II Legislative Attorney Jared P. Cole Legislative Attorney May 19, 2015 Congressional Research Service 7-5700 www.crs.gov R44036 Stored Communications Act: Reform of the Electronic Communications Privacy Act (ECPA Summary In 1986, Congress enacted the Electronic Communications Privacy Act (ECPA) to both protect the privacy of an individual’s electronic communications and provide the government with a means for accessing these communications and related records. Although passed at the infancy of the Internet, the Stored Communications Act (SCA), which is part of ECPA, has been interpreted over the years to cover the content of emails, private Facebook messages, YouTube videos, and so-called metadata, or non-content information, connected to our Internet transactions (e.g., websites visited, to/from and time/date stamps on emails). The scope of the SCA is determined largely by the entities to which it applies, “electronic communication service” (ECS) providers and “remote computing service” (RCS) providers, as defined in the statute. It does not apply to government access to records held by a party to the communication. The SCA has two core components. First, it creates a broad bar against service providers voluntarily disclosing a customer’s communications to the government or others, subject to various exceptions, and second, it establishes procedures under which the government can require a provider to disclose customers’ communications or records. As to government access, ECPA utilizes a tiered system with different levels of evidence required depending on whether the provider is an ECS or RCS; whether the data sought is content or non-content; whether the email has been opened; and whether advance notice has been given to the customer. -

You Can Configure Microsoft Outlook to Access Your Office 365 Account by Setting up an Exchange Connection
You can configure Microsoft Outlook to access your Office 365 account by setting up an Exchange connection. An Exchange connection provides access your email, calendar, contacts, and tasks in Outlook. You can also set up Outlook to access your email by using IMAP. However, if you use IMAP you can only access your email from Outlook, not your calendar, contacts, and tasks. Notes: ▪ Office 365 is designed to work with any version of Microsoft Office in mainstream support. Get Outlook for Windows Outlook is included with Microsoft Office 365. Faculty and staff with a Thiel ID and undergraduate students with an Office 365 account can download Microsoft Office for Windows via webmail for free. Please visit the Solution Center webpage for more information. Configure Outlook for Windows 1. Open Outlook. 2. At the Welcome screen, click Next. 3. When asked if you want to set up Outlook to connect to an email account, select Yes and then click Next. 4. The Auto Account Setup wizard opens. Enter your name, your email address using your ID#@thiel.edu, and your Thiel ID network password. Then, click Next 5. Outlook will complete the setup for your account, which might take several minutes. When you are notified that your account was successfully configured, click Finish. 6. You may need to restart Outlook for the changes to take effect. Change offline access setting You can use Outlook on your laptop or desktop computer when you’re not connected to the Internet. Email, calendar, and other items are kept in an Outlook data file on your computer so you can work offline. -
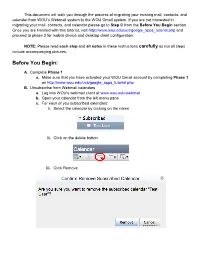
Before You Begin
This document will walk you through the process of migrating your existing mail, contacts, and calendar from WOU’s Webmail system to the WOU Gmail system. If you are not interested in migrating your mail, contacts, and calendar please go to Step C from the Before You Begin section. Once you are finished with this tutorial, visit http://www.wou.edu/ucs/google_apps_tutorial.php and proceed to phase 3 for mobile device and desktop client configuration. NOTE: Please read each step and all notes in these instructions carefully as not all steps include accompanying pictures. Before You Begin: A. Complete Phase 1 a. Make sure that you have activated your WOU Gmail account by completing Phase 1 on http://www.wou.edu/ucs/google_apps_tutorial.php B. Unsubscribe from Webmail calendars a. Log into WOU’s webmail client at www.wou.edu/webmail b. Open your calendar from the left menu pane c. For each of you subscribed calendars: i. Select the calendar by clicking on the name ii. Click on the delete button iii. Click Remove C. Setting up your Gmail account a. Log into your Gmail account at http://gmail.mail.wou.edu b. Click on Settings in the upper right-hand corner of the screen c. Click on the Accounts tab d. Click on Add another email address you own e. Enter your name and WOU email address and click Next Step f. Click Send Notification g. Return to your inbox h. You should have an email with the subject “Western Oregon University Confirmation - Send Mail as [email protected].” If you do not see this email, wait 2 minutes and refresh your inbox. -

A Security Analysis of Email Communications
A security analysis of email communications Ignacio Sanchez Apostolos Malatras Iwen Coisel Reviewed by: Jean Pierre Nordvik 2 0 1 5 EUR 28509 EN European Commission Joint Research Centre Institute for the Protection and Security of the Citizen Contact information Ignacio Sanchez Address: Joint Research Centre, Via Enrico Fermi 2749, I - 21027 Ispra (VA), Italia E-mail: [email protected] JRC Science Hub https://ec.europa.eu/jrc Legal Notice This publication is a Technical Report by the Joint Research Centre, the European Commission’s in-house science service. It aims to provide evidence-based scientific support to the European policy-making process. The scientific output expressed does not imply a policy position of the European Commission. Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use which might be made of this publication. All images © European Union 2015, except: Frontpage : © bluebay2014, fotolia.com JRC 99372 EUR 28509 EN ISSN 1831-9424 ISBN 978-92-79-66503-5 doi:10.2760/319735 Luxembourg: Publications Office of the European Union, 2015 © European Union, 2015 Reproduction is authorised provided the source is acknowledged. Printed in Italy Abstract The objective of this report is to analyse the security and privacy risks of email communications and identify technical countermeasures capable of mitigating them effectively. In order to do so, the report analyses from a technical point of view the core set of communication protocols and standards that support email communications in order to identify and understand the existing security and privacy vulnerabilities. On the basis of this analysis, the report identifies and analyses technical countermeasures, in the form of newer standards, protocols and tools, aimed at ensuring a better protection of the security and privacy of email communications. -

Email Transfer from Webmail to Gmail
Email Transfer from Webmail to Gmail Product: Google Mail Symptom: Transfer Webmail to Gmail Solution: Transfer Webmail to Gmail Footprints Public Solution #70834 In Your Oakland University Email Account 1. Click the gear in the top right corner then click Settings from the dropdown menu 2. Select Forwarding and POP/IMAP tab and then Enable POP for all mail (even mail that has already been downloaded) 3. Click Save Changes at the bottom of the screen Setting up 2-Step Verification and App Specific Password 1. Click on the circle with a letter in the top right corner and click My Account 2. Click Sign-in & security 3. Scroll down and click 2-Step Verification 4. Click Get Started 5. Type in your phone number and choose if you would like to receive a text or a phone call 6. You will need to input the code you received and click Next 7. You will the need to click Turn On to enable 2-Step Verification 8. Click the back arrow to go back to the Sign-in & security settings 9. Scroll down and click App passwords 10. Click Select Device and then choose Other (Custom name) 11. Name the device gmail then click Generate 12. A password will be generated. Copy the password, you will use it later In Your New Gmail Account 1. Click the gear in the top right corner then click Settings 2. Select the Accounts and Import tab then click Add a mail account 3. Type in your Oakland University email address in the popup window then click Next 4. -

On the Security of Practical Mail User Agents Against Cache Side-Channel Attacks †
applied sciences Article On the Security of Practical Mail User Agents against Cache Side-Channel Attacks † Hodong Kim 1 , Hyundo Yoon 1, Youngjoo Shin 2 and Junbeom Hur 1,* 1 Department of Computer Science and Engineering, Korea University, Seoul 02841, Korea; [email protected] (H.K.); [email protected] (H.Y.) 2 School of Computer and Information Engineering, Kwangwoon University, Seoul 01897, Korea; [email protected] * Correspondence: [email protected] † This paper is an extended version of our paper published in the 2020 International Conference on Information Networking (ICOIN), Barcelona, Spain, 7–10 January 2020. Received: 30 April 2020; Accepted: 26 May 2020; Published: 29 May 2020 Abstract: Mail user agent (MUA) programs provide an integrated interface for email services. Many MUAs support email encryption functionality to ensure the confidentiality of emails. In practice, they encrypt the content of an email using email encryption standards such as OpenPGP or S/MIME, mostly implemented using GnuPG. Despite their widespread deployment, there has been insufficient research on their software structure and the security dependencies among the software components of MUA programs. In order to understand the security implications of the structures and analyze any possible vulnerabilities of MUA programs, we investigated a number of MUAs that support email encryption. As a result, we found severe vulnerabilities in a number of MUAs that allow cache side-channel attacks in virtualized desktop environments. Our analysis reveals that the root cause originates from the lack of verification and control over the third-party cryptographic libraries that they adopt. In order to demonstrate this, we implemented a cache side-channel attack on RSA in GnuPG and then conducted an evaluation of the vulnerability of 13 MUAs that support email encryption in Ubuntu 14.04, 16.04 and 18.04. -

Efail: Breaking S/MIME and Openpgp Email Encryption Using Exfiltration Channels
Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels Damian Poddebniak and Christian Dresen, Münster University of Applied Sciences; Jens Müller, Ruhr University Bochum; Fabian Ising and Sebastian Schinzel, Münster University of Applied Sciences; Simon Friedberger, NXP Semiconductors, Belgium; Juraj Somorovsky and Jörg Schwenk, Ruhr University Bochum https://www.usenix.org/conference/usenixsecurity18/presentation/poddebniak This paper is included in the Proceedings of the 27th USENIX Security Symposium. August 15–17, 2018 • Baltimore, MD, USA ISBN 978-1-939133-04-5 Open access to the Proceedings of the 27th USENIX Security Symposium is sponsored by USENIX. Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels Damian Poddebniak1, Christian Dresen1, Jens Muller¨ 2, Fabian Ising1, Sebastian Schinzel1, Simon Friedberger3, Juraj Somorovsky2, and Jorg¨ Schwenk2 1Munster¨ University of Applied Sciences 2Ruhr University Bochum 3NXP Semiconductors, Belgium Abstract is designed to protect user data in such scenarios. With end-to-end encryption, the email infrastructure becomes OpenPGP and S/MIME are the two prime standards merely a transportation service for opaque email data and for providing end-to-end security for emails. We de- no compromise – aside from the endpoints of sender or scribe novel attacks built upon a technique we call mal- receiver – should affect the security of an end-to-end en- leability gadgets to reveal the plaintext of encrypted crypted email. emails. We use CBC/CFB gadgets to inject malicious plaintext snippets into encrypted emails. These snippets S/MIME and OpenPGP. The two most prominent stan- abuse existing and standard conforming backchannels to dards offering end-to-end encryption for email, S/MIME exfiltrate the full plaintext after decryption. -

Cryptic Journalism: News Reporting of Encryption
Cryptic journalism: news reporting of encryption Einar Thorsen School of Journalism, English and Communication Bournemouth University United Kingdom [email protected] ORCID http://orcid.org/0000-0002-7126-7293 This is an Accepted Manuscript of an article published by Taylor & Francis in Digital Journalism on 19/10/2016, available online: http://www.tandfonline.com/10.1080/21670811.2016.1243452 Abstract In light of Edward Snowden’s global surveillance disclosures, this article examines news discourses about online communication security and surveillance circumvention practices. It analyses 1,249 news reports mentioning encryption in The Guardian and The New York Times, covering a 3-year period from June 2012 to June 2015 (one year before and two years after the Snowden revelations). Whilst there was a marked increase in volume of news articles mentioning encryption post-Snowden, the context in which encryption is discussed has since shifted from an initial emphasis on "surveillance" towards "security" issues. However, the research found that greater news coverage of encryption did not necessarily mean an increase in depth of coverage, with most mentions of encryption vague and non-descript. In terms of source usage, the research finds an emphasis on private corporations in both publications analysed. This is problematic when many of the organisations allowed to speak on encryption were those accused of colluding with the US and UK Governments to aid covert mass surveillance - the likes of Google, Facebook, Apple, Microsoft and so forth - thus providing them with a platform to exonerate themselves from the accusations. This contradictory depiction of communication security serves the status quo and prevents advancement of the “encrypted by default” communication practice called for by Snowden.