List of Security Products
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security Analytics 8.1.X Reference Guide
Security Analytics 8.1.x Reference Guide Updated: Friday, November 15, 2019 Security Analytics Reference Guide Security Analytics 8.1 Copyrights, Trademarks, and Intellectual Property Copyright © 2019 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks or registered trademarks of Symantec Corp. or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. SYMANTEC CORPORATION PRODUCTS, TECHNICAL SERVICES, AND ANY OTHER TECHNICAL DATA REFERENCED IN THIS DOCUMENT ARE SUBJECT TO U.S. EXPORT CONTROL AND SANCTIONS LAWS, REGULATIONS AND REQUIREMENTS, AND MAY BE SUBJECT TO EXPORT OR IMPORT REGULATIONS IN OTHER COUNTRIES. YOU AGREE TO COMPLY STRICTLY WITH THESE LAWS, REGULATIONS AND REQUIREMENTS, AND ACKNOWLEDGE THAT YOU HAVE THE RESPONSIBILITY TO OBTAIN ANY LICENSES, PERMITS OR OTHER APPROVALS THAT MAY BE REQUIRED IN ORDER TO EXPORT, RE-EXPORT, TRANSFER IN COUNTRY OR IMPORT AFTER DELIVERY TO YOU. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton Antivirus™ 2009 Feature Comparison Chart
Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton AntiVirus™ 2009 Feature Comparison Chart Feature Norton 360 Norton Internet Norton Explanation Version 3.0 Security 2009 AntiVirus 2009 Core Protection Antivirus ✔ ✔ ✔ Detects and removes viruses, Internet worms, and Trojan horses Antispyware ✔ ✔ ✔ Prevents spyware from infecting the PC Email and instant messaging protection ✔ ✔ ✔ Monitors email and instant messaging so users can exchange files without exchanging threats Antispam ✔ ✔ Automatically filters out annoying and fraudulent or phishing email from the user’s email inbox Advanced Protection Botnet detection ✔ ✔ ✔ Detects and prevents others from taking control of the PC, accessing private information, or using the computer to host an attack Rootkit detection ✔ ✔ ✔ Finds and removes threats that are hidden deep in the operating system Norton™ Insight ✔ ✔ ✔ Includes innovative, intelligence-driven technology for faster, fewer, shorter scans Norton™ Pulse Updates ✔ ✔ ✔ Delivers rapid pulse updates every 5 to 15 minutes for protection against new threats Smart, two-way firewall ✔ ✔ Makes intelligent incoming and outgoing security decisions without interrupting users to ask them each time Enhanced browser protection ✔ ✔ ✔ Secures against Web-based attacks that use browser vulnerabilities to infect PCs with malware Real-time behavioral protection ✔ ✔ ✔ Provides enhanced, real-time protection (SONAR™) Wireless network security protection ✔ ✔ Checks the status of wireless network security and provides expert advice on managing -

Amit a Windows 7
DVD DVD Többé nem fog akadozni az internet 11 Friss 9 GB 2009 A LEGÚJABB DRIVEREK, HASZNOS PROGRAMOK, Megmutatjuk, hogyan kell beállítani a rejtélyes Qos-t – lépésről lépésre R 90 A HÓNAP JÁTÉKAI, EXKLUZÍV CSOMAgok… 9 tipp: tökéletes TFT-képminőség Nem kell drága pénzen új monitor! Profin beállítjuk a mostanit R 98 GO DIGITAL! 2009/11_ CHIPONLINE.HU Ennyire (nem) biztonságos a vírusirtója – felfedjük! A DVD-N: Tesztünkből kiderül, hogy miért csődöl be sok víruskereső éles helyzetben R 40 es VÍRUSVADÁSZ teLJ CSOMAG Amit a Windows 7 jobban tud… 46 Gyors sikerek! Több gépre... Csak a CHIP-en! R TELJES VERZIÓ TELJES VERZIÓ TELJES VERZIÓ Egyedi, vicces, ...Szinkroni- Sytem Backup: …és, amin még javítani kell. Az összes új funkció szórakoztató zálás, mentés, vadonatúj, családi album megosztás 2010-es verzió és rejtett képesség tesztje + a Win 7 mint második rendszer Szimatolók a PC-jén? Segítünk! A legjobb eszközök az adatlopás ellen: 100% anonim szörf és levelezés R 26 Zseniális új funkciók eszközeihez T ESZ pt 20 tipp, melyekkel lenyűgöző tulajdonságokat LA TOVÁBBI DVD-TARTALOM 58 P R csalogathat elő átlagos hardvereiből 84 Radeon HD5870 Radeon teszt >> HD5870 10 tény a CPU-król >> Új technológiák: OpenID >> Mozizzunk óriástévén >> Gyorsteszt: P55-ös alaplapok >> Rés a víruspajzson >> Ennyire jó a 7 Windows >> CHIP mini PC >> 20 dolog, amit nem tudott… >> Soha többé net akadozó 1995 Ft, előfizetéssel 1395 Ft R XXI. évfolyam, 11. szám, 2009. november P55-ÖSz ALA asztali PC-k 36 Kiadja a Motor-Presse Budapest Lapkiadó Kft. A forradalma R CD CD Többé nem fog akadozni az internet 11 melléklettel 2009 EXKLUZÍV CSOMAGOK, FRISS Megmutatjuk, hogyan kell beállítani a rejtélyes Qos-t – lépésről lépésre R 90 PROGRAMOK, VÍRUSVÉDELEM.. -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -

TFG Borrador 1 último
Trabajo Final de Grado Facultad de Ingeniería en Telecomunicaciones Tema: IMPLEMENTACIÓN DE UN SISTEMA AUTÓNOMO Y REDISEÑO DE LA RED DE DATOS Matias E. Lauretta Saad Tutor: Enrique G. Banchio Ignacio Segura 1 Año 2018 Dedicatoria A la paciencia y confianza en mí de mujer y mi familia. Matias E. Lauretta Saad 2 Agradecimientos A mi mujer por su confianza y apoyo. A mi familia que siempre me alentó a terminar mis estudios. A mis amigos y compañeros de la facultad que me acompañaron todos estos años. Matias E. Lauretta Saad 3 Resumen El auge de las tecnologías de internet conlleva a un incremento del uso de recursos de red lo que llevó al Instituto a tramitar la asignación de un número de sistema autónomo con el pool de direcciones IP asociadas. Siendo responsable de la propagación de estas direcciones y sus reglas de ruteo. Por consiguiente, resulta necesario un replanteo de la red del instituto que satisfaga las necesidades de los usuarios actuales y se provea de herramientas de administración de red que facilite la gestión de tráfico para los servicios relevados y la seguridad de la red. Con el presente trabajo se hace un relevamiento de las herramientas disponibles, servicios que brinda la red, necesidades futuras y se realiza un re-diseño lógico de la red y una propuesta de configuración para la herramienta de gestión y seguridad 4 Glosario ISP: Proveedor de Servicios de Internet o ISP (del inglés Internet Service Provider) AS: Sistema Autónomo o AS (del inglés Autonomous System) ASN: Número de Sistema Autónomo o ASN (del inglés Autonomous System Number) LACNIC: Registro de Direcciones de Internet para América Latina y Caribe (del inglés Latin American and Caribbean Internet Addresses Registry) MAN: Metropolitan Área Network, Red de Área Metropolitana WAN: Wide Area Network, Red de Área Amplia LAN: Local Area Network. -
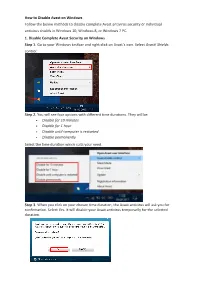
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Antivirus – Internet Security Software
AntiVirus – Internet Security Software Recommended AntiVirus Software to use with OfficeEMR™: Norton AntiVirus Symantec Endpoint Protection Business Class – Enterprise – AntiVirus Solution AntiVirus ONLY software products WITHOUT additional Firewalls What Happens with Internet Security Software Products and OfficeEMR™: Provide an additional Firewall and/or Shields Can prevent you from accessing secure Web Sites such as https://www.officemd.net Scan every Web Page that you go to when it loads Can make screens in OfficeEMR™ take a long time to load Can prevent our AutoConfigure from running Can prevent scanning documents into OfficeEMR™ from completing What You Can Do: Setup our Web Site www.officemd.net as an exception in its Firewall. --- or --- Turn off (Disable) the additional Firewall included and / or applicable Shields Contact Technical Support via the software company’s Web Site o many offer e-mail, phone, and/or chat for technical support o get help with and options available to be able to access secure (https://...) Web --- or --- Sites o get help with and options available for making www.officemd.net an exception o get help with and options available for turning off their Firewall and / or applicable Shields. --- or --- Uninstall and Install the AntiVirus ONLY version of that software product. --- or --- Uninstall and Install a different AntiVirus ONLY software product. Revised 05/2009 AntiVirus – Internet Security Software More Detailed Information: Internet Security Software Products provide an added Firewall and / or Shields to help block malicious content or Web Sites while surfing on the Web. Without changing settings, by default, Internet Security Software Products will scan every Web Page that you go to when it loads. -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

Ques 1) How to Book a Domain ? Follow These Steps for Booking
Ques 1) How to Book a Domain ? Follow these steps for booking your Domain Name: Step 1 In the Domain search box on the home page enter the domain name you want, select an extension for your Domain name (e.g. .com, .net, org, .tv etc.) and start your search by clicking on the Search button. Step 2 The results page will next show you whether the Domain is available or not. If not available then you will have to resume your search again. If your Domain name is available, you may proceed to register by selecting the checkbox against the domain name you want and clicking on Continue. Step 3 Proceed to complete the Domain registration form. Note: INSTALINKS.NET does not need any pre-registration, and you will directly proceeded to a Domain registration form. Registration is absolutely free of cost. You only have to register once on the site. After completing and submitting the Domain registration form, you will get an order code and will receive an email from Instalinks containing your all information pertaining to the domain that you have booked. Your domain will be activated within 48 hrs of receiving your payment. Note: This email does NOT mean that your domain has been registered, it merely confirms your order. You have to send the Cheque/Draft for the amount pertaining to the domain you have booked to INSTALINKS for the registration of the domain. From the day you have applied for Domain booking, Instalinks will keep it for a maximum period of 21 days, during which you will receive reminders. -

A Glance Into the Eye Pyramid Technical Article V2
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks against high ranking Italian government members and Italian institutions. The attacks were conducted by two Italian brothers to get financial information that would help them gain an advantage when trading on financial markets. Overview The campaign was carried out over several years starting in 2008 and continuing into 2010, 2011, 2012 and 2014. The mechanism the brothers used to distribute their malware was simple; targeted spear-phishing emails aimed at victims who had already been selected. The emails con- tained a malware attachment, which once opened harvested information from the victims’ computers. This information consisted of pictures, documents, archives, presenta- tions, email contacts, email bodies, usernames, passwords, keystrokes, web pages content and databases. Technical details The malware was written in VisualBasic.net and was obfuscated twice using common obfuscators: Dotfuscator and Skater .NET which can be easily reversed. The malware stored its sensitive data – license keys, URLs and paths – by encrypting with the Triple DES algorithm using the MD5 of a provided password as key and SHA256 of the pass- word as initialization vector. A glance into the Eye Pyramid 01 02 Figure 1 Security applications To remain unnoticed, it tried to disable any security application installed on the victim’s computer. Targeted