Bonjour Printing Specification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Thoughts on Flash
Apple has a long relationship with Adobe. In fact, we met Adobe’s founders when they were in their proverbial garage. Apple was their first big customer, adopting their Postscript language for our new Laserwriter printer. Apple invested in Adobe and owned around 20% of the company for many years. The two companies worked closely together to pioneer desktop publishing and there were many good times. Since that golden era, the companies have grown apart. Apple went through its near death experience, and Adobe was drawn to the corporate market with their Acrobat products. Today the two companies still work together to serve their joint creative customers – Mac users buy around half of Adobe’s Creative Suite products – but beyond that there are few joint interests. I wanted to jot down some of our thoughts on Adobe’s Flash products so that customers and critics may better understand why we do not allow Flash on iPhones, iPods and iPads. Adobe has characterized our decision as being primarily business driven – they say we want to protect our App Store – but in reality it is based on technology issues. Adobe claims that we are a closed system, and that Flash is open, but in fact the opposite is true. Let me explain. First, there’s “Open”. Adobe’s Flash products are 100% proprietary. They are only available from Adobe, and Adobe has sole authority as to their future enhancement, pricing, etc. While Adobe’s Flash products are widely available, this does not mean they are open, since they are controlled entirely by Adobe and available only from Adobe. -

Ipsec, SSL, Firewall, Wireless Security
IPSec 1 Outline • Internet Protocol – IPv6 • IPSec – Security Association (SA) – IPSec Base Protocol (AH, ESP) – Encapsulation Mode (transport, tunnel) 2 IPv6 Header • Initial motivation: – 32-bit address space soon to be completely allocated. – Expands addresses to 128 bits • 430,000,000,000,000,000,000 for every square inch of earth’s surface! • Solves IPv4 problem of insufficient address space • Additional motivation: – header format helps speedy processing/forwarding – header changes to facilitate QoS IPv6 datagram format: – fixed-length 40 byte header – no fragmentation allowed 3 IPv6 Header (Cont) Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data 4 Other Changes from IPv4 • Checksum: removed entirely to reduce processing time at each hop • Options: allowed, but outside of header, indicated by “Next Header” field • ICMPv6: new version of ICMP – additional message types, e.g. “Packet Too Big” – multicast group management functions 5 IPv6 Security – IPsec mandated • IPsec is mandated in IPv6 – This means that all implementations (i.e. hosts, routers, etc) must have IPsec capability to be considered as IPv6-conformant • When (If?) IPv6 is in widespread use, this means that IPsec will be installed everywhere – At the moment, IPsec is more common in network devices (routers, etc) than user hosts, but this would change with IPsec • All hosts having IPsec => real end-to-end security possible 6 IPv6 Security • Enough IP addrs for every imaginable device + Real end-to-end security = Ability to securely communicate from anything to anything 7 IPv6 Security – harder to scan networks • With IPv4, it is easy to scan a network – With tools like nmap, can scan a typical subnet in a few minutes see: http://www.insecure.org/nmap/ – Returning list of active hosts and open ports – Many worms also operate by scanning • e.g. -

Stylewriter II 1992.Pdf
~ ., ('D ~ (/)~ .........~ 0... t ('D • •.• , .: ... .. .. --;, .. :. ....;. -~·~ ;-·-·: ~'"1\l; 1 r,• .;"':· :· ,,.!\.._.,.,1.. .:~"· 1.. ·1. ~ · : '. •,\ . : (t~~ .... ~... ~}'°.... '_.;•)·l~ -~'"st-if.~ ~,. ·! ..ti.. -.. r. ,::-.~ },.... :r1'··'} .~~\;.tot"' '" ·'~ ' -·:/' "·~ ~ ......\':!...·, .. -;,.lo :"< ,,.~:.--. ·~·;.~·."it~·,, . ;,-~>l'!"y.. ... .·;:~~;~t;l - ..-r:.~!.'-~ (tl jf:· -~";t''!f.{: . ·;.,. .. - 14~:.... / " .v;; .. <) ?~ ~-..~ ~,,... ~ { "~·-~ r-J~1 ~-.;:r~i: ~~~ ; .. .J,-:.;~~~·;1.)~ ;~·~::t:!{.1i..~: -~. ti Apple Computer, Inc. Apple, the Apple logo, AppleTalk, LaserWriter, Macintosh, MuhiFinder, and StyleWriter are trademarks of Apple Computer, Inc., registered in che U.S. and other countries. This manual and the software described in it are copyrighted, with all rights reserved. Balloon Help, Finder, and Syscem 7 arc trademarks of Apple Computer, Inc. Under the copyright laws, this manual or the software may not be copied, in whole or pan, without written consent of Apple, except in the normal use of the software or to Adobe, Adobe Illustrator, and PostScript are trademarks of Adobe Systems Incorporated, make a backup copy of the software. The same proprietary and copyright notices must registered in the United States. Adobe Photoshop is a trademark of Adobe Systems be affixed to any permitted copies as were affixed to che original. This excepcion does Incorporated. not allow copies to be made for ochers, whether or noc sold, but all of the macerial Exposure is a registered trademark of Preferred Publishers, Inc. purchased (with all backup copies) may be sold, given, or loaned to another person. Under the law, copying includes translacing into another language or format. ITC Zapf Dingbats is a registered trademark of Internacional lypcface Corporal ion. You may use the software on any compmer owned by you, but extra copies cannot be MacPaint is a registered trademark of Claris Corporation. -

SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst
ISSN (Print) : 2320 – 3765 ISSN (Online): 2278 – 8875 International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering Vol. 2, Issue 5, May 2013 SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst. Prof, Dept. of ECE, Siliguri Institute of Technology, Sukna, Siliguri, West Bengal, India 1 Network Engineer, Network Dept, Ericsson Global India Ltd, India2 Abstract:-. The Secure Internet Live Conferencing (SILC) protocol, a new generation chat protocol provides full featured conferencing services, compared to any other chat protocol. Its main interesting point is security which has been described all through the paper. We have studied how encryption and authentication of the messages in the network achieves security. The security has been the primary goal of the SILC protocol and the protocol has been designed from the day one security in mind. In this paper we have studied about different keys which have been used to achieve security in the SILC protocol. The main function of SILC is to achieve SECURITY which is most important in any chat protocol. We also have studied different command for communication in chat protocols. Keywords: SILC protocol, IM, MIME, security I.INTRODUCTION SILC stands for “SECURE INTERNET LIVE CONFERENCING”. SILC is a secure communication platform, looks similar to IRC, first protocol & quickly gained the status of being the most popular chat on the net. The security is important feature in applications & protocols in contemporary network environment. It is not anymore enough to just provide services; they need to be secure services. The SILC protocol is a new generation chat protocol which provides full featured conferencing services; additionally it provides security by encrypting & authenticating the messages in the network. -

Organizing Screens with Mission Control | 61
Organizing Screens with 7 Mission Control If you’re like a lot of Mac users, you like to do a lot of things at once. No matter how big your screen may be, it can still feel crowded as you open and arrange multiple windows on the desktop. The solution to the problem? Mission Control. The idea behind Mission Control is to show what you’re running all at once. It allows you to quickly swap programs. In addition, Mission Control lets you create multiple virtual desktops (called Spaces) that you can display one at a time. By storing one or more program windows in a single space, you can keep open windows organized without cluttering up a single screen. When you want to view another window, just switch to a different virtual desktop. Project goal: Learn to use Mission Control to create and manage virtual desktops (Spaces). My New Mac, Lion Edition © 2011 by Wallace Wang lion_book-4c.indb 59 9/9/2011 12:04:57 PM What You’ll Be Using To learn how to switch through multiple virtual desktops (Spaces) on your Macintosh using Mission Control, you’ll use the following: > Mission Control > The Safari web browser > The Finder program Starting Mission Control Initially, your Macintosh displays a single desktop, which is what you see when you start up your Macintosh. When you want to create additional virtual desktops, or Spaces, you’ll need to start Mission Control. There are three ways to start Mission Control: > Start Mission Control from the Applications folder or Dock. > Press F9. -
Ideal Spaces OS-Platform-Browser Support
z 4.9 OS-Platform-Browser Support v1.4 2020spaces.com 4.9 Table of Contents Overview....................................................................................................... 3 System Requirements ................................................................................... 4 Windows .................................................................................................................................................... 4 Mac ............................................................................................................................................................ 4 Support Criteria ............................................................................................ 5 OS Platform ................................................................................................................................................ 5 OS Version .................................................................................................................................................. 5 Web Browser and Operating System Combinations ..................................... 6 Current Platform / Web Browser Support ................................................................................................. 6 Out of Scope Browsers and Operating Systems ............................................ 7 Opera ..................................................................................................................................................... 7 Linux ...................................................................................................................................................... -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -
Apple Bonjour for Windows 7 32 Bit Downloadl
Apple Bonjour For Windows 7 32 Bit Downloadl Apple Bonjour For Windows 7 32 Bit Downloadl 1 / 2 Download bonjour for windows 7 64 bit for free. Development Tools downloads - Bonjour SDK by Apple Inc. and many more programs are available for instant .... Download locations for Bonjour 1.0.6, Downloads: 9828, Size: 2.05 MB. Easily network your PC to an existing network. ... File section. File Type: Win32 EXE MIME Type: ... Company Name: Apple Inc. File Description: Bonjour .... You can download Bonjour for Windows from Apple's Bonjour support pages. Bonjour for Windows is bundled with Bonjour Print Services for .... Download Bonjour for Windows XP (32/64 bit) Free. ... Languages: English (en); Publisher Software: Apple Computer Inc; Gadgets: Desktop PC, Ultrabook, .... Bonjour, free and safe download. Bonjour latest version: A Free Networking Tool From Apple Computers. The Bonjour program was created by Apple as a .... Bonjour Print Services. Free Apple Windows XP/Vista/7/8/10 Version 2.0.2 Full Specs.. Apple's Bonjour is a software program that automatically manages ... With Microsoft Windows, it's optional, as long as your PC has no programs that require it. ... Rolls Out Bonjour Print Services for Windows as Free Download .... If you need help downloading or updating iTunes from the Microsoft Store, contact Microsoft for help. ... Windows 7 and 8 · Windows 10 ... Support; Bonjour; Apple Application Support 32-bit; Apple Application Support 64-bit.. Download Bonjour for Windows. ... Sistema operativo Windows 7 32 bit / Vista 32-bit / XP 32-bit / Windows 8; Licencia: Freeware (Gratis); Creador: Apple ... Bonjour para Windows es una aplicación útil y libre de Apple, con el que se crea ... -
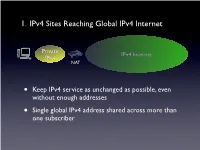
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3. -

XEP-0347: Internet of Things - Discovery
XEP-0347: Internet of Things - Discovery Peter Waher mailto:peterwaher@hotmail:com xmpp:peter:waher@jabber:org http://www:linkedin:com/in/peterwaher Ronny Klauck mailto:rklauck@informatik:tu-cottbus:de xmpp:TBD http://www-rnks:informatik:tu-cottbus:de/~rklauck 2018-11-03 Version 0.5.1 Status Type Short Name Deferred Standards Track iot-discovery This specification describes an architecture based on the XMPP protocol whereby Things can be in- stalled and safely discovered by their owners and connected into networks of Things. Legal Copyright This XMPP Extension Protocol is copyright © 1999 – 2020 by the XMPP Standards Foundation (XSF). Permissions Permission is hereby granted, free of charge, to any person obtaining a copy of this specification (the ”Specification”), to make use of the Specification without restriction, including without limitation the rights to implement the Specification in a software program, deploy the Specification in a network service, and copy, modify, merge, publish, translate, distribute, sublicense, or sell copies of the Specifi- cation, and to permit persons to whom the Specification is furnished to do so, subject to the condition that the foregoing copyright notice and this permission notice shall be included in all copies or sub- stantial portions of the Specification. Unless separate permission is granted, modified works that are redistributed shall not contain misleading information regarding the authors, title, number, or pub- lisher of the Specification, and shall not claim endorsement of the modified works by the authors, any organization or project to which the authors belong, or the XMPP Standards Foundation. Warranty ## NOTE WELL: This Specification is provided on an ”AS IS” BASIS, WITHOUT WARRANTIES OR CONDI- TIONS OF ANY KIND, express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. -

Enterprise Best Practices for Ios Devices On
White Paper Enterprise Best Practices for iOS devices and Mac computers on Cisco Wireless LAN Updated: January 2018 © 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 51 Contents SCOPE .............................................................................................................................................. 4 BACKGROUND .................................................................................................................................. 4 WIRELESS LAN CONSIDERATIONS .................................................................................................... 5 RF Design Guidelines for iOS devices and Mac computers on Cisco WLAN ........................................................ 5 RF Design Recommendations for iOS devices and Mac computers on Cisco WLAN ........................................... 6 Wi-Fi Channel Coverage .................................................................................................................................. 7 ClientLink Beamforming ................................................................................................................................ 10 Wi-Fi Channel Bandwidth ............................................................................................................................. 10 Data Rates .................................................................................................................................................... 12 802.1X/EAP Authentication .......................................................................................................................... -

Download Bonjour Service Pc Question: Q: I Need to Reinstall Bonjour on Windows 10
download bonjour service pc Question: Q: I need to reinstall Bonjour on Windows 10. Can't fond where to download. Had to recover my Windows 10 iTunes server. Running iHomeserver. It needs Bonjour. I need to reinstall Bonjour for Windows but can't find the download for it. Apple Software Update doesn't think any software is missing. Would really appreciate help! Dell XPS All-in-One Touch PC-OTHER, Windows 8, Windows 8.1. Posted on Feb 24, 2017 11:57 AM. Start with Install missing components, or review the rest of that user tip and do a full rebuild of iTunes. Posted on Feb 24, 2017 2:30 PM. All replies. Loading page content. Page content loaded. Start with Install missing components, or review the rest of that user tip and do a full rebuild of iTunes. Feb 24, 2017 2:30 PM. Thank you for the reply. I just reinstalled iTunes and Bonjour came with it. No worries now! Feb 24, 2017 2:32 PM. Feb 24, 2017 3:49 PM. I have the same question, can anyone help? Apr 7, 2017 3:09 PM. Try the same answer as given previously: Start with Install missing components, or review the rest of that user tip and do a full rebuild of iTunes. Apr 7, 2017 3:20 PM. I tried that multiple times with no help. I need to reinstall Bonjour and there is no way to download it (or I couldn't find any way on the apple website). May 16, 2017 6:30 PM. There is no standalone source for the Bonjour installer.