End of Year Report for Parallel Vision Algorithm Design and Implementation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Physicality of the Analogue by Duncan Robinson BFA(Hons)
Physicality of the Analogue by Duncan Robinson BFA(Hons) Submitted in the fulfilment of the requirements for the degree of Master of Fine Arts. 2 Signed statement of originality This Thesis contains no material which has been accepted for a degree or diploma by the University or any other institution. To the best of my knowledge and belief, it incorporates no material previously published or written by another person except where due acknowledgment is made in the text. Duncan Robinson 3 Signed statement of authority of access to copying This Thesis may be made available for loan and limited copying in accordance with the Copyright Act 1968. Duncan Robinson 4 Abstract: Inside the video player, spools spin, sensors read and heads rotate, generating an analogue signal from the videotape running through the system to the monitor. Within this electro mechanical space there is opportunity for intervention. Its accessibility allows direct manipulation to take place, creating imagery on the tape as pre-recorded signal of black burst1 without sound rolls through its mechanisms. The actual physical contact, manipulation of the tape, the moving mechanisms and the resulting images are the essence of the variable electrical space within which the analogue video signal is generated. In a way similar to the methods of the Musique Concrete pioneers, or EISENSTEIN's refinement of montage, I have explored the physical possibilities of machine intervention. I am working with what could be considered the last traces of analogue - audiotape was superseded by the compact disc and the videotape shall eventually be replaced by 2 digital video • For me, analogue is the space inside the video player. -

Easter Eggs: Hidden Tracks and Messages in Musical Mediums
Proceedings ICMC|SMC|2014 14-20 September 2014, Athens, Greece Easter Eggs: Hidden Tracks and Messages in Musical Mediums Jonathan Weinel, Darryl Griffiths and Stuart Cunningham Creative & Applied Research for the Digital Society (CARDS) Glyndŵr University Plas Coch Campus, Mold Road, Wrexham, LL11 2AW, Wales +44 1978 293070 {j.weinel | Griffiths.d | s.cunningham}@glyndwr.ac.uk ABSTRACT the programmers’ office, in the style of the video game Doom [2]. The hidden game features credits and digital ‘Easter eggs’ are hidden components that can be found in images of the programmers. It is accessed by carrying computer software and various other media including out a particular series of actions on the 95th row of a music. In this paper the concept is explained, and various blank spreadsheet upon opening Excel. examples are discussed from a variety of mediums in- cluding analogue and digital audio formats. Through this discussion, the purpose of including easter eggs in musi- cal mediums is considered. We propose that easter eggs can serve to provide comic amusement within a work, but can also serve to support the artistic message of the art- work. Concealing easter eggs in music is partly depend- ent on the properties of the chosen medium; vinyl records Figure 1. Screenshots from the ‘hall of tortured souls’, in Mi- may use techniques such as double grooves, while digital crosoft Excel 95. formats such as CD may feature hidden tracks that follow long periods of empty space. Approaches such as these This paper will consider the purpose and realisation of and others are discussed. -

Artificial Intelligence, Ovvero Suonare Il Corpo Della Macchina O Farsi Suonare? La Costruzione Dell’Identità Audiovisiva Della Warp Records
Philomusica on-line 13/2 (2014) Artificial Intelligence, ovvero suonare il corpo della macchina o farsi suonare? La costruzione dell’identità audiovisiva della Warp Records Alessandro Bratus Dipartimento di Musicologia e Beni Culturali Università di Pavia [email protected] § A partire dai tardi anni Ottanta la § Starting from the late 1980s Warp Records di Sheffield (e in seguito Sheffield (then London) based Warp Londra) ha avuto un ruolo propulsivo Records pushed forward the extent nel mutamento della musica elettronica and scope of electronic dance music popular come genere di musica che well beyond its exclusive focus on fun non si limita all’accompagna-mento del and physical enjoinment. One of the ballo e delle occasioni sociali a esso key factors in the success of the label correlate. Uno dei fattori chiave nel was the creative use of the artistic successo dell’etichetta è stato l’uso possibilities provided by technology, creativo delle possibilità artistiche which fostered the birth of a di- offerte dalla tecnologia, favorendo la stinctive audiovisual identity. In this formazione di un’identità ben ca- respect a crucial role was played by ratterizzata, in primo luogo dal punto the increasing blurred boundaries di vista audiovisivo. Sotto questo profilo between video and audio data, su- un ruolo fondamentale ha giocato la bjected to shared processes of digital possibilità di transcodifica tra dati transformation, transcoding, elabora- audio e video nell’era digitale, poten- tion and manipulation. zialmente soggetti agli stessi processi di Although Warp Records repeatedly trasformazione, elaborazione e mani- resisted the attempts to frame its polazione. artistic project within predictable Nonostante la Warp Records abbia lines, its production –especially mu- ripetutamente resistito a ogni tentativo sic videos and compilations– suggests di inquadrare il proprio progetto arti- the retrospective construction of a stico entro coordinate prevedibili, i suoi consistent imagery. -
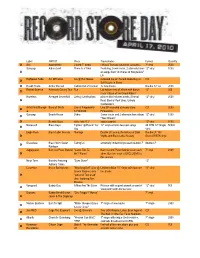
Label ARTIST Piece Tracks/Notes Format Quantity
Label ARTIST Piece Tracks/notes Format Quantity Sire Against Me! 2 song 7" single I Was A Teenage Anarchist (acoustic) 7" vinyl 2500 Sub-pop Album Leaf There Is a Wind Featuring 2 new tracks, 2 alternate takes 12" vinyl 1000 on songs from "A Chorus of Storytellers" LP Righteous Babe Ani DiFranco live @ Bull Moose recorded live on Record Store Day at CD Bull Moose in Maine Rough Trade Arthur Russell Calling Out of Context 12 new tracks Double 12" set 2000 Rocket Science Asteroids Galaxy Tour Fun Ltd edition vinyl of album with bonus 12" 250 track "Attack of the Ghost Riders" Hopeless Avenged Sevenfold Unholy Confessions picture disc includes tracks (Eternal 12" vinyl 2000 Rest, Eternal Rest (live), Unholy Confessions Artist First/Shangri- Band of Skulls Live at Fingerprints Live EP recorded at record store CD 2000 la 12/15/2009 Fingerprints Sub-pop Beach House Zebra 2 new tracks and 2 alternate from album 12" vinyl 1500 "Teen Dream" Beastie Boys white label 12" super surprise 12" vinyl 1000 Nonesuch Black Keys Tighten Up/Howlin' For 12" vinyl contains two new songs 45 RPM 12" Single 50000 You Vinyl Eagle Rock Black Label Society Skullage Double LP look at the history of Zakk Double LP 180 Wylde and Black Label Society Gram GREEN vinyl Graveface Black Moth Super Eating Us extremely limited foil pressed double LP double LP Rainbow Jagjaguwar Bon Iver/Peter Gabriel "Come Talk To Bon Iver and Peter Gabriel cover each 7" vinyl 2000 Me"/"Flume" other. Bon Iver track is EXCLUSIVE to this release Ninja Tune Bonobo featuring "Eyes -

A Study of Microtones in Pop Music
University of Huddersfield Repository Chadwin, Daniel James Applying microtonality to pop songwriting: A study of microtones in pop music Original Citation Chadwin, Daniel James (2019) Applying microtonality to pop songwriting: A study of microtones in pop music. Masters thesis, University of Huddersfield. This version is available at http://eprints.hud.ac.uk/id/eprint/34977/ The University Repository is a digital collection of the research output of the University, available on Open Access. Copyright and Moral Rights for the items on this site are retained by the individual author and/or other copyright owners. Users may access full items free of charge; copies of full text items generally can be reproduced, displayed or performed and given to third parties in any format or medium for personal research or study, educational or not-for-profit purposes without prior permission or charge, provided: • The authors, title and full bibliographic details is credited in any copy; • A hyperlink and/or URL is included for the original metadata page; and • The content is not changed in any way. For more information, including our policy and submission procedure, please contact the Repository Team at: [email protected]. http://eprints.hud.ac.uk/ Applying microtonality to pop songwriting A study of microtones in pop music Daniel James Chadwin Student number: 1568815 A thesis submitted to the University of Huddersfield in partial fulfilment of the requirements for the degree of Master of Arts University of Huddersfield May 2019 1 Abstract While temperament and expanded tunings have not been widely adopted by pop and rock musicians historically speaking, there has recently been an increased interest in microtones from modern artists and in online discussion. -

Xix Share Anticipated Debut Video for Viral Track “Kismet” on Masked Records / Warner Records
XIX SHARE ANTICIPATED DEBUT VIDEO FOR VIRAL TRACK “KISMET” ON MASKED RECORDS / WARNER RECORDS FEATURING TIKTOK STARS XOWIEJONES & BENKRO_TV WATCH HERE October 22, 2020 (Los Angeles, CA) – XIX are the next wave of musicians in the genre bending hyper-pop scene to make their own lane with their viral earworm “Kismet.” The song has been exploding on TikTok and has already amassed 7.8 million streams. Today, the duo comprised of Yung Skayda and Karm the Tool share the eagerly-awaited video on Masked Records / Warner Records with cameo appearances from alt-TikTok superstars Xowiejones and Benkro_TV. The video is a major statement for XIX, who are blazing a trail behind them in the Ramez Silyan- directed (Lil Peep) video as they wreak havoc on high school property in the night hours. The manic energy is unavoidably reminiscent of iconic teenage rebellion movies and soundtracks this aesthetic to a tee. The track's hook “Molly rocks in my green tea,” is becoming its own brand with more than 3 million TikTok videos created and over a dozen sounds supported by the likes of social media maven Charli D'Amelio, super producer Marshmello and renowned comedian Sacha Baron Cohen as Borat while promoting the new Borat 2 movie. The aforementioned lyric was intentionally isolated as the repeating phrase on the song by XIX with the premonition that it could spark a movement. As fate would have it, they were right. Now with millions of streams under their belt and an incredible video for “Kismet,” the future is bright for Yung Skayda and Karm, who are deeply inspired by punk rock, rap and metal and cite XXXTentacion as their biggest influence. -

Defense Intelligence Reference Document Warp Drive, Dark
UNCLASSIFIED/ / FOR OFFICIAL USE ONLY Defense Intelligence Reference Document Acquisition Threat Support 2 2010 1 December 2009 DiA-08-1004-001 '------ Warp Drive, Dark Energy1 a11d the Manipulation of Dimensions UNCLASSIFIED//FOR OFFICIAL USE ONLY UNCLASSIFIED//FOR OFFICIAL USE ONLY Drive, Dark Energy, and the Manipulation of 1 Dimensions Prepared Acquisition Support Division (DW0-3) · Defense Warning Office Directorate for Analysis Defense Intelligence Agency Authors: Richard Obousy, Ph.D. President, Richard Obousy Consulting, LLC Eric W . Davis, Ph.D. Senior Research Physicist EarthTech International, Inc. Administrative Note COPYRIGHT WARNING: Further dissemination of the photogra.phs in tl1is is not authbrized. This product is one in series of advanced technology reports produced in FY 2009 under the Defense Intelligence Agency, Defense Warning Office's Advanced Aerospace Weapon System Applications (AAWSA) Program. Comments questions pertaining to th.is document should addressed to James Lacatski, D.Eng., AAWSA Program Manager, Defense Agency, CLAR/DW0-3, Bldg 6000, Washington, 20340-5100. ii UNCLASSIFIED/ /FOR OFFICIAL USE ONLY - --··--""·---·-·-""" .. UNCLASSIFIED/ /FOR OFFICIAL USE ONLY Contents Introduction .••..... " ...•........•••........•.•...•......•.......•......••., ....•.....•.•....•.••....• , ....•.•• •••..... v \ . 2. General Relativistic Warp Drives ....•. ;•·•············••··"'··" .• " .....•....: ..•.. ".".. " ·• ...• ). •..... 1 2.1 Warp Drive Requirements ..•.... ".""" •. """" •.•.• " .. " ..• "" •• " .•• ""."." -

Nightmares on Wax Album Download Nightmares on Wax Album Download
nightmares on wax album download Nightmares on wax album download. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67a293cf8e521669 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Nightmares on wax album download. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67a293d028e915e8 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. -

Social Spatialisation EXPLORING LINKS WITHIN CONTEMPORARY SONIC ART by Ben Ramsay
Social spatialisation EXPLORING LINKS WITHIN CONTEMPORARY SONIC ART by Ben Ramsay This article aims to briefly explore some the compositional links that exist between Intelligent Dance Music (IDM) and acousmatic music. Whilst the central theme of this article will focus on compositional links it will suggest some ways in which we might use these links to enhance pedagogic practice and widen access to acousmatic music. In particular, the article is concerned with documenting artists within Intelligent Dance Music (IDM), and how their practices relate to acousmatic music composition. The article will include a hand full of examples of music which highlight this musical exchange and will offer some ways to use current academic thinking to explain how IDM and acousmatics are related, at least from a theoretical point of view. There is a growing body of compositional work and theoretical research that draws from both acousmatics and various forms of electronic dance music. Much of this work blurs the boundaries of electronic music composition, often with vastly different aesthetic and cultural outcomes. Elements of acousmatic composition can be found scattered throughout Intelligent Dance Music (IDM) and on the other side of the divide there are a number of composers who are entering the world of acousmatics from a dance music background. This dynamic exchange of ideas and compositional processes is resulting in an interesting blend of music which is able to sit quite comfortably inside an academic framework as well as inside a more commercial one. Whilst there are a number of genres of dance music that could be described in terms of the theories that would normally relate to acousmatic music composition practices, the focus of this article lies particularly with Intelligent Dance Music. -

Byetone Raster-Noton Alemania
SÁBADO 2 DE MAYO Aphex Twin Rephlex / Warp Records UK Aphex Twin, AFX, The Tuss, Polygon Window, Caustic Window, The Dice Man…. múltiples nombres para un sólo hombre: Richard D. James, una de las figuras más influyentes e innovadoras de los últimos 25 años. Creció en Cornwall (Inglaterra) donde ya desde muy pequeño comenzó a demostrar sus capacidades con experimentos electrónicos llegando a ganar un premio escolar por tocar una melodía con un Spectrum y un televisor alterado. En 1991 fundó Rephlex Records y lanzó su primer trabajo, se mudó a Londres y comenzó una imparable carrera ascendente publicando material bajo sus innumerables alias tanto en Warp Records como Rephlex. Desde Selected Ambient Works hasta Druqks pasando por clásicos como Ventolin, Come to Daddy o la serie Analord. Un artista excéntrico y controvertido, un personaje influyente que ha trascendido en innumerables ocasiones los límites del underground electrónico a base de trabajo y genialidades. Sus colaboraciones con el también genial Chris Cuningham nos han brindado algunos de los mejores trabajos audiovisuales hasta la fecha: Windowlicker, Come To Daddy o Rubber Johnny son algunas de las obras donde se ponen al descubierto sus locuras y cualidades. Acid, IDM, techno, ambient…. son algunos de los géneros que Aphex Twin domina a la perfección y en los que ha jugado y juega un papel fundamental como evolucionador y visionario. Rodeado por multitud de leyendas, con una perfección milimétrica en el dominio de viejos sintetizadores y la creación de nuevos sonidos y dotado de una de las mentes más inquietas y creativas que existen en la escena musical, Aphex Twin sigue creando, a día de hoy, registros en las fronteras de las normas aceptadas de la música. -

Corriente NOTA BIBLIOGRAFICA
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Repositorio Institucional de la Universidad de Córdoba On a proposal for a “Syro-Aramaic” reading of the Qur’ān Federico CORRIENTE Universidad de Zaragoza A very practical and commonly followed procedure to know the overall contents of a book is to begin at the end and read the résumé, should there be one, or the conclusions drawn by the author, only then undertaking the lengthy and close examination of the previous chapters containing the arguments in support of his contentions. In the case of the book entitled Die Syro-aramäische Lesart des Kor’an. Ein Beitrag zur Entschlüsselung der Koransprache 1, signed by Christoph Luxenberg, the reader of those final pages (299-306) can hardly remain imperturbed by the bold and far-reaching consequences of the proposals advanced by this scholar, namely 1) That the original language of the Qur’ ān would not have been Arabic, but an admixture of this and Aramaic ( eine aramäisch-arabische Mischsprache ), the very name of Mecca supposedly being Aramaic and the city itself an Aramaean settlement, 2) That the original wording and contents of the Qur’anic text that has reached us would have been substantially altered, not only in order to adjust it to the rules of Classical Arabic 2, but also because, in the alleged absence of a consistent and reliable oral transmission, the people in charge of producing its written records, were often no longer able to understand the Aramaic ingredients of that Mischsprache , and tried to give them sense in Arabic, with the expectable result of countless passages which would be 1 Berlin: Weinert, 2000. -

Seefeel Succour Mp3, Flac, Wma
Seefeel Succour mp3, flac, wma DOWNLOAD LINKS (Clickable) Genre: Electronic Album: Succour Country: UK Released: 1995 Style: IDM, Experimental, Ambient MP3 version RAR size: 1935 mb FLAC version RAR size: 1344 mb WMA version RAR size: 1574 mb Rating: 4.9 Votes: 480 Other Formats: XM FLAC AIFF APE VOC MPC WAV Tracklist 1 Meol 5:51 2 Extract 7:28 3 When Face Was Face 6:03 4 Fracture 5:52 5 Gatha 6:00 6 Ruby-Ha 6:08 7 Rupt 6:29 8 Vex 4:25 9 Cut 5:40 10 Utreat/Tempean 7:52 Credits Arranged By, Mixed By [Uncredited] – Mark Clifford Edited By [Digital Edit] [Uncredited] – Francis Arkwright* Mastered By [Uncredited] – Geoff Pesche Other [Tubes] [Uncredited] – Zoë Harris Producer [Uncredited] – Seefeel Written-by [Uncredited] – Seymour* (tracks: 4, 10), Fletcher* (tracks: 3, 4), Clifford*, Sarah Peacock Notes CD EP jewelcase with black & white photo copy inlay detailing the date of release, catalogue number, format and tracklisting. Other versions Category Artist Title (Format) Label Category Country Year Warp CD28, Succour (CD, Warp Records, Warp CD28, Seefeel UK 1995 WARPCD28 Album) Warp Records WARPCD28 Warp MC28, Succour (Cass, Warp Records, Warp MC28, Seefeel UK 1995 WARP MC28 Album, Promo) Warp Records WARP MC28 Succour (10xFile, WARPCDD 28 Seefeel Warp Records WARPCDD 28 UK 2006 FLAC, Album, RE) Warp MC28, Succour (Cass, Warp Records, Warp MC28, Seefeel UK 1995 WARP MC28 Album) Warp Records WARP MC28 Succour (2xLP, WARP LP 28 Seefeel Warp Records WARP LP 28 UK 1995 Album) Related Music albums to Succour by Seefeel Seefeel - Starethrough EP Seefeel - Faults Big Swifty & Associates - Wouldn't You Rather Be Involved In A Series Of Colorful Time-Wasting Trends? Seefeel - Seefeel Cajmere Feat.