G. & Sivaselvan, S. B, and Gopalan N. P, a Beginner S Guide to Unix. PHI
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mysql Workbench Mysql Workbench
MySQL Workbench MySQL Workbench Abstract This manual documents the MySQL Workbench SE version 5.2 and the MySQL Workbench OSS version 5.2. If you have not yet installed MySQL Workbench OSS please download your free copy from the download site. MySQL Workbench OSS is available for Windows, Mac OS X, and Linux. Document generated on: 2012-05-01 (revision: 30311) For legal information, see the Legal Notice. Table of Contents Preface and Legal Notice ................................................................................................................. vii 1. MySQL Workbench Introduction ..................................................................................................... 1 2. MySQL Workbench Editions ........................................................................................................... 3 3. Installing and Launching MySQL Workbench ................................................................................... 5 Hardware Requirements ............................................................................................................. 5 Software Requirements .............................................................................................................. 5 Starting MySQL Workbench ....................................................................................................... 6 Installing MySQL Workbench on Windows .......................................................................... 7 Launching MySQL Workbench on Windows ....................................................................... -

OS/2 Warp Catalogue
The OS/2 Software Source: www.xeu.com/blueware/ The OS/2 Warp Catalogue The Hottest Java The Strongest Platform The OS/2 Warp Catalogue In This Catalogue Anti-virus .......................................... 4 Backup .............................................. 4 It’s Java Time CD-ROMs ........................................ 4 Communications ........................ 6 Just when you thought that OS/2 was on its way back, it is receiving a strong Database Management .......... 9 infusion from Java and the internet. Development Tools ................ 10 As Dr. Michael Cowpland, president and CEO of Corel Disk Compression .................. 14 Corporation put it: “This platform is indeed one of the Games & Entertainment ..... 19 OS/2 Warp: best operating system solutions in which to run The Hottest Corel Office for Java (http://officeforjava.corel.com/), Graphics & Multimedia ........ 20 a suite of applications that is setting the standard for The Operating System ......... 21 Java Around! Java-based office suites, and marks another milestone OS/2 Warp is developing in the evolution of Java as a whole.” Productivity ................................. 21 into a strong and speedy Programmer’s Editors .......... 23 foundation for Java. The OS/2 Warp 4.0 Java implementation was recently This perfect fit is nicely updated with a better Virtual Machine (VM) and a REXX Programming ................ 23 symbolized by “Carmen” speedy Just In Time (JIT) compiler. Also, even older OS/2 the two-sided coffee cup versions, including Warp 3.0, Warp Connect Utilities & Tools ........................ 24 by dutch ceramist Erik-Jan |and Warp Server are now fully able to suppport Java. Books ............................................. 28 Kwakkel on the cover page. But the great work does not end with that: you can Registration Service ............. -

Instruction Manual Model 34988NI-SL
Instruction Manual (Original Instructions) Model 34988NI-SL Recover, Recycle, Recharge Machine for R-134a A/C Systems ROBINAIR.COM 800.533.6127 (en-US) Description: Recover, recycle, and recharge machine for use with R-134a equipped air conditioning systems. PRODUCT INFORMATION Record the serial number and year of manufacture of this unit for future reference. Refer to the product identification label on the unit for information. Serial Number: _______________________________Year of Manufacture: ____________ DISCLAIMER: Information, illustrations, and specifications contained in this manual are based on the latest information available at the time of publication. The right is reserved to make changes at any time without obligation to notify any person or organization of such revisions or changes. Further, ROBINAIR shall not be liable for errors contained herein or for incidental or consequential damages (including lost profits) in connection with the furnishing, performance, or use of this material. If necessary, obtain additional health and safety information from the appropriate government agencies, and the vehicle, refrigerant, and lubricant manufacturers. Table of Contents Safety Precautions . 2 Maintenance . 26 Explanation of Safety Signal Words . 2 Maintenance Schedule. 26 Explanation of Safety Decals. 2 Load Language. 27 Protective Devices. 4 Adjust Background Fill Target. 28 Refrigerant Tank Test. 4 Tank Fill. 28 Filter Maintenance. 29 Introduction . 5 Check Remaining Filter Capacity. 29 Technical Specifications . 5 Replace the Filter. 30 Features . 6 Calibration Check . 31 Control Panel Functions . 8 Change Vacuum Pump Oil . 32 Icon Legend. 9 Leak Check. 33 Setup Menu Functions. 10 Edit Print Header. 34 Initial Setup . 11 Replace Printer Paper. 34 Unpack the Machine. -

Fortran Resources 1
Fortran Resources 1 Ian D Chivers Jane Sleightholme October 17, 2020 1The original basis for this document was Mike Metcalf’s Fortran Information File. The next input came from people on comp-fortran-90. Details of how to subscribe or browse this list can be found in this document. If you have any corrections, additions, suggestions etc to make please contact us and we will endeavor to include your comments in later versions. Thanks to all the people who have contributed. 2 Revision history The most recent version can be found at https://www.fortranplus.co.uk/fortran-information/ and the files section of the comp-fortran-90 list. https://www.jiscmail.ac.uk/cgi-bin/webadmin?A0=comp-fortran-90 • October 2020. Added an entry for Nvidia to the compiler section. Nvidia has integrated the PGI compiler suite into their NVIDIA HPC SDK product. Nvidia are also contributing to the LLVM Flang project. • September 2020. Added a computer arithmetic and IEEE formats section. • June 2020. Updated the compiler entry with details of standard conformance. • April 2020. Updated the Fortran Forum entry. Damian Rouson has taken over as editor. • April 2020. Added an entry for Hewlett Packard Enterprise in the compilers section • April 2020. Updated the compiler section to change the status of the Oracle compiler. • April 2020. Added an entry in the links section to the ACM publication Fortran Forum. • March 2020. Updated the Lorenzo entry in the history section. • December 2019. Updated the compiler section to add details of the latest re- lease (7.0) of the Nag compiler, which now supports coarrays and submodules. -
Geany Tutorial
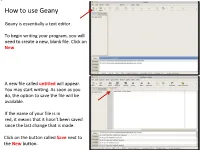
How to use Geany Geany is essentially a text editor. To begin writing your program, you will need to create a new, blank file. Click on New. A new file called untitled will appear. You may start writing. As soon as you do, the option to save the file will be available. If the name of your file is in red, it means that it hasn’t been saved since the last change that is made. Click on the button called Save next to the New button. Save the file in a directory you had previously created before you launched Geany and name it main.cpp. All of the files you will write and submit to will be named specifically main.cpp. Once the .cpp has been specified, Geany will turn on its color coding feature for the C++ template. Next, we will set up our environment and then write a simple program that will print something to the screen Feel free to supply your own name in this small program Before we do anything with it, we will need to configure some options to make your life easier in this class The vertical line to the right marks the ! boundary of your code. You will need to respect this limit in that any line of code you write must not cross this line and therefore be properly, manually broken down to the next line. Your code will be printed out for The line is not where it should be, however, and grading, and if your code crosses the we will now correct it line, it will cause line-wrapping and some points will be deducted. -

Emacspeak — the Complete Audio Desktop User Manual
Emacspeak | The Complete Audio Desktop User Manual T. V. Raman Last Updated: 19 November 2016 Copyright c 1994{2016 T. V. Raman. All Rights Reserved. Permission is granted to make and distribute verbatim copies of this manual without charge provided the copyright notice and this permission notice are preserved on all copies. Short Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::::::: 2 2 Announcing Emacspeak Manual 2nd Edition As An Open Source Project ::::::::::::::::::::::::::::::::::::::::::::: 3 3 Background :::::::::::::::::::::::::::::::::::::::::: 4 4 Introduction ::::::::::::::::::::::::::::::::::::::::: 6 5 Installation Instructions :::::::::::::::::::::::::::::::: 7 6 Basic Usage. ::::::::::::::::::::::::::::::::::::::::: 9 7 The Emacspeak Audio Desktop. :::::::::::::::::::::::: 19 8 Voice Lock :::::::::::::::::::::::::::::::::::::::::: 22 9 Using Online Help With Emacspeak. :::::::::::::::::::: 24 10 Emacs Packages. ::::::::::::::::::::::::::::::::::::: 26 11 Running Terminal Based Applications. ::::::::::::::::::: 45 12 Emacspeak Commands And Options::::::::::::::::::::: 49 13 Emacspeak Keyboard Commands. :::::::::::::::::::::: 361 14 TTS Servers ::::::::::::::::::::::::::::::::::::::: 362 15 Acknowledgments.::::::::::::::::::::::::::::::::::: 366 16 Concept Index :::::::::::::::::::::::::::::::::::::: 367 17 Key Index ::::::::::::::::::::::::::::::::::::::::: 368 Table of Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::: -

Mobile Phones and Cloud Computing
Mobile phones and cloud computing A quantitative research paper on mobile phone application offloading by cloud computing utilization Oskar Hamrén Department of informatics Human Computer Interaction Master’s programme Master thesis 2-year level, 30 credits SPM 2012.07 Abstract The development of the mobile phone has been rapid. From being a device mainly used for phone calls and writing text messages the mobile phone of today, or commonly referred to as the smartphone, has become a multi-purpose device. Because of its size and thermal constraints there are certain limitations in areas of battery life and computational capabilities. Some say that cloud computing is just another buzzword, a way to sell already existing technology. Others claim that it has the potential to transform the whole IT-industry. This thesis is covering the intersection of these two fields by investigating if it is possible to increase the speed of mobile phones by offloading computational heavy mobile phone application functions by using cloud computing. A mobile phone application was developed that conducts three computational heavy tests. The tests were run twice, by not using cloud computing offloading and by using it. The time taken to carry out the tests were saved and later compared to see if it is faster to use cloud computing in comparison to not use it. The results showed that it is not beneficial to use cloud computing to carry out these types of tasks; it is faster to use the mobile phone. 1 Table of Contents Abstract ..................................................................................................................................... 1 Table of Contents ..................................................................................................................... 2 1. Introduction .......................................................................................................................... 5 1.1 Previous research ........................................................................................................................ -

Vim for Humans Release 1.0
Vim for humans Release 1.0 Vincent Jousse August 12, 2015 CONTENTS 1 Preamble 1 1.1 Disclaimer .................... ..................... 1 1.2 Paid book but free price .................... ..................... 1 1.3 Free license .................... ..................... 1 1.4 Thanks .................... ..................... 1 2 Introduction 3 2.1 For who? .................... ..................... 4 2.2 What you will be learning .................... .................... 4 2.3 What you will not be learning .................... .................. 4 2.4 The hardest part is to get started .................... ................. 5 3 Having a usable Vim 7 3.1 Essential preamble: the insert mode .................... ............... 8 3.2 Modes: the powerful Vim secrets .................... 10 3.3 The lifesaver default configuration .................... 12 3.4 And now, the color! .................... ..................... 13 3.5 Ourfirst plugin: thefile explorer .................... 17 3.6 Here we go .................... ..................... 19 4 The text editor you’ve always dreamed of 23 4.1 Learning how to move: the copy/paste use case ..................... 23 4.2 Forgetting the directional keys .................... 26 4.3 Doing without the Esc key .................... .................... 29 4.4 Combining keys and moves .................... ................... 29 4.5 Search / Move quickly .................... ..................... 30 4.6 Visual mode .................... ..................... 31 4.7 It’s your turn! .................... .................... -

This PDF Is Provided Solely As a Reader Service. It Is Not Intended for Reproduction Or Public Distribution
Copyright (c) 2007, CMP Media LLC. Important note: This PDF is provided solely as a reader service. It is not intended for reproduction or public distribution. For more information on obtaining a Reprint, please contact a Reprint Services Rep at 516.562.7026 or visit www.cmpreprints.com/faxback.jhtml CODEF SCANNERS A LL S E { Sense of Security? } AS MORE CUSTOM-BUILT SOFTWARE MAKES ITS WAY INTO YOUR APP INFRASTRUCTURE, THE THREAT LANDSCAPE IS SHIFTING. CAN AN AUTOMATED CODE SCANNER SECURE YOUR BUSINESS, OR WILL IT SIMPLY LULL THE IT STAFF WHILE CRIMINALS by Justin Schuh Illustration by Ryan Etter PROWL? REMEMBER WHEN ATTACKERS WERE JUST OUT FOR FAME AND requirements. Purpose-built apps provide the frame- glory, and application security was someone else’s prob- work for a huge range of business processes, from lem? Big targets like Microsoft and Oracle drew the fire. dynamic Web sites, SOA (service-oriented architecture) All enterprise IT had to do was apply patches regularly and e-commerce to business process automation and and keep a properly configured firewall. administration. They also provide a target-rich environ- Those days are gone. Cracking corporate networks is ment for would be attackers. no longer a kid’s game, it’s a lucrative criminal growth In response to this escalating threat, major compliance industry. The attackers who stole 45.6 million credit- standards like HIPAA and PCI DSS (Payment Card Industry and debit-card numbers Data Security Standard) are incorporating—or at least STRATEGIC from TJX Companies were implying the necessity of—application security processes. -

Linux Fundamentals (GL120) U8583S This Is a Challenging Course That Focuses on the Fundamental Tools and Concepts of Linux and Unix
Course data sheet Linux Fundamentals (GL120) U8583S This is a challenging course that focuses on the fundamental tools and concepts of Linux and Unix. Students gain HPE course number U8583S proficiency using the command line. Beginners develop a Course length 5 days solid foundation in Unix, while advanced users discover Delivery mode ILT, vILT patterns and fill in gaps in their knowledge. The course View schedule, local material is designed to provide extensive hands-on View now pricing, and register experience. Topics include basic file manipulation; basic and View related courses View now advanced filesystem features; I/O redirection and pipes; text manipulation and regular expressions; managing jobs and processes; vi, the standard Unix editor; automating tasks with Why HPE Education Services? shell scripts; managing software; secure remote • IDC MarketScape leader 5 years running for IT education and training* administration; and more. • Recognized by IDC for leading with global coverage, unmatched technical Prerequisites Supported distributions expertise, and targeted education consulting services* Students should be comfortable with • Red Hat Enterprise Linux 7 • Key partnerships with industry leaders computers. No familiarity with Linux or other OpenStack®, VMware®, Linux®, Microsoft®, • SUSE Linux Enterprise 12 ITIL, PMI, CSA, and SUSE Unix operating systems is required. • Complete continuum of training delivery • Ubuntu 16.04 LTS options—self-paced eLearning, custom education consulting, traditional classroom, video on-demand -

Emacs Speaks Statistics (ESS): a Multi-Platform, Multi-Package Intelligent Environment for Statistical Analysis
Emacs Speaks Statistics (ESS): A multi-platform, multi-package intelligent environment for statistical analysis A.J. Rossini Richard M. Heiberger Rodney A. Sparapani Martin Machler¨ Kurt Hornik ∗ Date: 2003/10/22 17:34:04 Revision: 1.255 Abstract Computer programming is an important component of statistics research and data analysis. This skill is necessary for using sophisticated statistical packages as well as for writing custom software for data analysis. Emacs Speaks Statistics (ESS) provides an intelligent and consistent interface between the user and software. ESS interfaces with SAS, S-PLUS, R, and other statistics packages under the Unix, Microsoft Windows, and Apple Mac operating systems. ESS extends the Emacs text editor and uses its many features to streamline the creation and use of statistical software. ESS understands the syntax for each data analysis language it works with and provides consistent display and editing features across packages. ESS assists in the interactive or batch execution by the statistics packages of statements written in their languages. Some statistics packages can be run as a subprocess of Emacs, allowing the user to work directly from the editor and thereby retain a consistent and constant look- and-feel. We discuss how ESS works and how it increases statistical programming efficiency. Keywords: Data Analysis, Programming, S, SAS, S-PLUS, R, XLISPSTAT,STATA, BUGS, Open Source Software, Cross-platform User Interface. ∗A.J. Rossini is Research Assistant Professor in the Department of Biostatistics, University of Washington and Joint Assis- tant Member at the Fred Hutchinson Cancer Research Center, Seattle, WA, USA mailto:[email protected]; Richard M. -

UNIX Essentials (Hands-On)
UNIX essentials (hands-on) • the directory tree • running programs • the shell (using the T-shell) → command line processing → special characters → command types → shell variables → environment variables → wildcards → shell scripts → shell commands → pipes and redirection • OS commands • special files 1 • The Directory Tree → directories contain files and/or directories → / : means either the root directory, or a directory separator • consider /home/afniuser/AFNI_data3 afniuser/suma_demo → an "absolute" pathname begins with '/', a "relative" pathname does not • a relative pathname depends on where you start from • in the directories above, note which is a relative pathname → every directory has a parent directory • the relative pathname for the parent directory is '..' • the relative pathname for the current directory is '.' • consider './run_this_script' and '/bin/ls ../../suma_demo' → many commands can be used to return to the home directory (of "afniuser") • cd, cd ~, cd ~afniuser, cd $HOME, cd /home/afniuser • note the 2 special characters, '~' and '$' → while you work, keep your location within the directory tree in mind 2 → class work: • open a terminal window • commands: cd, pwd, ls, ls -al • use the "cd" command to go to the given directories e.g. for directory /usr/bin, use the command: cd /usr/bin once there, use the commands "pwd", "ls", and "ls -al" note that you can always return to the home directory via: cd / home/afniuser AFNI_data3 .. AFNI_data3/afni /usr/bin ~/abin ../../afniuser/../afniuser • first example (starting with the '/'directory), use the commands: cd / pwd ls ls -al 3 • Running Programs → a program is something that gets "executed", or "run" → the first element of a command line is generally a program (followed by a space) → most shells are case sensitive when processing a command → command examples: /bin/ls $HOME ~/AFNI_data3 count -digits 2 1 10 → script: an interpreted program (interpreted by another program) • e.g.