Id 1 Question the ___Protocol Allows the Administrator to Assign A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Next Generation Web Scanning Presentation
Next generation web scanning New Zealand: A case study First presented at KIWICON III 2009 By Andrew Horton aka urbanadventurer NZ Web Recon Goal: To scan all of New Zealand's web-space to see what's there. Requirements: – Targets – Scanning – Analysis Sounds easy, right? urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets What does 'NZ web-space' mean? It could mean: •Geographically within NZ regardless of the TLD •The .nz TLD hosted anywhere •All of the above For this scan it means, IPs geographically within NZ urbanadventurer (Andrew Horton) www.morningstarsecurity.com Finding Targets We need creative methods to find targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com DNS Zone Transfer urbanadventurer (Andrew Horton) www.morningstarsecurity.com Find IP addresses on IRC and by resolving lots of NZ websites 58.*.*.* 60.*.*.* 65.*.*.* 91.*.*.* 110.*.*.* 111.*.*.* 113.*.*.* 114.*.*.* 115.*.*.* 116.*.*.* 117.*.*.* 118.*.*.* 119.*.*.* 120.*.*.* 121.*.*.* 122.*.*.* 123.*.*.* 124.*.*.* 125.*.*.* 130.*.*.* 131.*.*.* 132.*.*.* 138.*.*.* 139.*.*.* 143.*.*.* 144.*.*.* 146.*.*.* 150.*.*.* 153.*.*.* 156.*.*.* 161.*.*.* 162.*.*.* 163.*.*.* 165.*.*.* 166.*.*.* 167.*.*.* 192.*.*.* 198.*.*.* 202.*.*.* 203.*.*.* 210.*.*.* 218.*.*.* 219.*.*.* 222.*.*.* 729,580,500 IPs. More than we want to try. urbanadventurer (Andrew Horton) www.morningstarsecurity.com IP address blocks in the IANA IPv4 Address Space Registry Prefix Designation Date Whois Status [1] ----- -

Dspace 1.8 Documentation
DSpace 1.8 Documentation DSpace 1.8 Documentation Author: The DSpace Developer Team Date: 03 November 2011 URL: https://wiki.duraspace.org/display/DSDOC18 Page 1 of 621 DSpace 1.8 Documentation Table of Contents 1 Preface _____________________________________________________________________________ 13 1.1 Release Notes ____________________________________________________________________ 13 2 Introduction __________________________________________________________________________ 15 3 Functional Overview ___________________________________________________________________ 17 3.1 Data Model ______________________________________________________________________ 17 3.2 Plugin Manager ___________________________________________________________________ 19 3.3 Metadata ________________________________________________________________________ 19 3.4 Packager Plugins _________________________________________________________________ 20 3.5 Crosswalk Plugins _________________________________________________________________ 21 3.6 E-People and Groups ______________________________________________________________ 21 3.6.1 E-Person __________________________________________________________________ 21 3.6.2 Groups ____________________________________________________________________ 22 3.7 Authentication ____________________________________________________________________ 22 3.8 Authorization _____________________________________________________________________ 22 3.9 Ingest Process and Workflow ________________________________________________________ 24 -

Building Multiplayer Games with Web Sockets #GHC19 About Us
Leveling Up: Building Multiplayer Games with Web Sockets #GHC19 About Us: #GHC19 Agenda 0. Introduction 1. Simple Chat Application 2. Multiplayer Game 3. Further Applications #GHC19 www.kahoot.com #GHC19 #GHC19 #GHC19 #GHC19 Diagram source: BMC Blog #GHC19 Diagram source: BMC Blog TCP and UDP are the transport level protocols TCP UDP Reliable Unreliable Connection-oriented Connectionless Segment sequencing No sequencing Acknowledge No acknowledgement segments #GHC19 Source: Pluralsight #GHC19 Diagram source: BMC Blog #GHC19 Diagram source: BMC Blog HTTP is used to share information on the application layer #GHC19 Graphic Source: Webnots Alternatives to WebSockets ● Browser Plug-Ins ● Polling ● Long Polling ● Server-Sent Events (SSE) #GHC19 The WebSocket protocol is used for real-time communication RFC-6455 #GHC19 Source: IETF RFC-6455 Some benefits of WebSockets Event driven Reduces network overhead - no need to send full HTTP requests HTTP compatible Co-exists on same port as your web server TLS/SSL compatible Same security as HTTPS #GHC19 WebSocket connection overview #GHC19 Diagram source: PubNub Staff Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Data Transfer Base Framing Protocol -
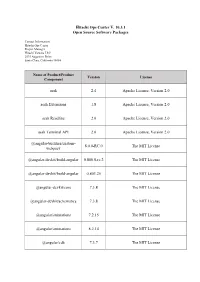
Open Source Software Packages
Hitachi Ops Center V. 10.3.1 Open Source Software Packages Contact Information: Hitachi Ops Center Project Manager Hitachi Vantara LLC 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component aesh 2.4 Apache License, Version 2.0 aesh Extensions 1.8 Apache License, Version 2.0 aesh Readline 2.0 Apache License, Version 2.0 aesh Terminal API 2.0 Apache License, Version 2.0 @angular-builders/custom- 8.0.0-RC.0 The MIT License webpack @angular-devkit/build-angular 0.800.0-rc.2 The MIT License @angular-devkit/build-angular 0.803.25 The MIT License @angular-devkit/core 7.3.8 The MIT License @angular-devkit/schematics 7.3.8 The MIT License @angular/animations 7.2.15 The MIT License @angular/animations 8.2.14 The MIT License @angular/cdk 7.3.7 The MIT License Name of Product/Product Version License Component @angular/cli 8.0.0 The MIT License @angular/cli 8.3.25 The MIT License @angular/common 7.2.15 The MIT License @angular/common 8.2.14 The MIT License @angular/compiler 7.2.15 The MIT License @angular/compiler 8.2.14 The MIT License @angular/compiler-cli 8.2.14 The MIT License @angular/core 7.2.15 The MIT License @angular/forms 7.2.13 The MIT License @angular/forms 7.2.15 The MIT License @angular/forms 8.2.14 The MIT License @angular/forms 8.2.7 The MIT License @angular/language-service 8.2.14 The MIT License @angular/platform-browser 7.2.15 The MIT License @angular/platform-browser 8.2.14 The MIT License Name of Product/Product Version License Component @angular/platform-browser- 7.2.15 The MIT License -

Deploying with Jruby Is the Definitive Text on Getting Jruby Applications up and Running
Early Praise for Deploying JRuby Deploying with JRuby is the definitive text on getting JRuby applications up and running. Joe has pulled together a great collection of deployment knowledge, and the JRuby story is much stronger as a result. ➤ Charles Oliver Nutter JRuby Core team member and coauthor, Using JRuby Deploying with JRuby answers all of the most frequently asked questions regarding real-world use of JRuby that I have seen, including many we were not able to answer in Using JRuby. Whether you’re coming to JRuby from Ruby or Java, Joe fills in all the gaps you’ll need to deploy JRuby with confidence. ➤ Nick Sieger JRuby Core team member and coauthor, Using JRuby This book is an excellent guide to navigating the various JRuby deployment op- tions. Joe is fair in his assessment of these technologies and describes a clear path for getting your Ruby application up and running on the JVM. ➤ Bob McWhirter TorqueBox team lead at Red Hat Essential reading to learn not only how to deploy web applications on JRuby but also why. ➤ David Calavera Creator of Trinidad Deploying with JRuby is a must-read for anyone interested in production JRuby deployments. The book walks through the major deployment strategies by providing easy-to-follow examples that help the reader take full advantage of the JRuby servers while avoiding the common pitfalls of migrating an application to JRuby. ➤ Ben Browning TorqueBox developer at Red Hat Deploying with JRuby is an invaluable resource for anyone planning on using JRuby for web-based development. For those who have never used JRuby, Joe clearly presents its many advantages and few disadvantages in comparison to MRI. -

J2EETM Deployment: the Jonas Case Study
J2EETM Deployment: The JOnAS Case Study François Exertier Bull, 1, rue de Provence BP 208 38432 Echirolles Cedex [email protected] RÉSUMÉ. La spécification J2EE (Java 2 platform Enterprise Edition) définit une architecture de serveur d'application Java. Jusqu'à J2EE 1.3, seuls les aspects de déploiement concernant le développeur d'applications étaient adressés. Avec J2EE 1.4, les interfaces et les étapes de déploiement ont été plus précisément spécifiées dans la spécification "J2EE Deployment". JOnAS (Java Open Application Server) est une plate-forme J2EE développée au sein du consortium ObjectWeb. Les aspects déploiement sont en cours de développement. Cet article décrit les concepts liés au déploiement dans J2EE, ainsi que les problématiques levées lors de leur mise en œuvre pour JOnAS. Il n'a pas pour but de présenter un travail abouti, mais illustre le déploiement par un cas concret et ébauche une liste de besoins non encore satisfaits dans le domaine. ABSTRACT. The J2EE (Java 2 platform Enterprise Edition) specification defines an architecture for Java Application Servers. Until J2EE 1.3, the deployment aspect was addressed from the developer point of view only. Since J2EE 1.4, deployment APIs and steps have been more precisely specified within the "J2EE Deployment Specification". JOnAS (Java Open Application Server) is a J2EE platform implementation by ObjectWeb. The deployment aspects are under development. This article describes the J2EE Deployment concepts, and the issues raised when implementing deployment features within JOnAS. It does not provide a complete solution, but illustrates deployment through a concrete example and initiates a list of non fulfilled requirements. -

CKAN) Developer Documentation Release 1.5.2A
Comprehensive Knowledge Archive Network (CKAN) Developer Documentation Release 1.5.2a Open Knowledge Foundation January 07, 2015 Contents 1 Option 1: Package Installation3 1.1 Prepare your System...........................................3 1.2 Run the Package Installer........................................ 24 2 Option 2: Install from Source 29 2.1 Install the Source............................................. 29 3 Post-Installation Setup 35 3.1 Create an Admin User.......................................... 35 3.2 Load Test Data.............................................. 35 3.3 Deployment............................................... 35 4 Customization 37 4.1 Site Name and Description........................................ 37 4.2 Adding CSS, Javascript and other HTML using Config Options.................... 37 4.3 More Advanced Customization..................................... 38 5 Load Datasets 41 5.1 Import Data with the CKAN API.................................... 41 5.2 Import Data with the Harvester Extension................................ 43 6 Common CKAN Tasks 45 6.1 Understanding Paster........................................... 45 6.2 Common Tasks Using Paster....................................... 46 7 Set and Manage Permissions 51 7.1 Overview................................................. 51 7.2 Default Permissions........................................... 53 7.3 Managing Permissions.......................................... 53 7.4 Openness Modes............................................. 54 8 Prepare to Use Extensions -

Comparison of Web Server Software from Wikipedia, the Free Encyclopedia
Create account Log in Article Talk Read Edit ViewM ohrisetory Search Comparison of web server software From Wikipedia, the free encyclopedia Main page This article is a comparison of web server software. Contents Featured content Contents [hide] Current events 1 Overview Random article 2 Features Donate to Wikipedia 3 Operating system support Wikimedia Shop 4 See also Interaction 5 References Help 6 External links About Wikipedia Community portal Recent changes Overview [edit] Contact page Tools Server Developed by Software license Last stable version Latest release date What links here AOLserver NaviSoft Mozilla 4.5.2 2012-09-19 Related changes Apache HTTP Server Apache Software Foundation Apache 2.4.10 2014-07-21 Upload file Special pages Apache Tomcat Apache Software Foundation Apache 7.0.53 2014-03-30 Permanent link Boa Paul Phillips GPL 0.94.13 2002-07-30 Page information Caudium The Caudium Group GPL 1.4.18 2012-02-24 Wikidata item Cite this page Cherokee HTTP Server Álvaro López Ortega GPL 1.2.103 2013-04-21 Hiawatha HTTP Server Hugo Leisink GPLv2 9.6 2014-06-01 Print/export Create a book HFS Rejetto GPL 2.2f 2009-02-17 Download as PDF IBM HTTP Server IBM Non-free proprietary 8.5.5 2013-06-14 Printable version Internet Information Services Microsoft Non-free proprietary 8.5 2013-09-09 Languages Jetty Eclipse Foundation Apache 9.1.4 2014-04-01 Čeština Jexus Bing Liu Non-free proprietary 5.5.2 2014-04-27 Galego Nederlands lighttpd Jan Kneschke (Incremental) BSD variant 1.4.35 2014-03-12 Português LiteSpeed Web Server LiteSpeed Technologies Non-free proprietary 4.2.3 2013-05-22 Русский Mongoose Cesanta Software GPLv2 / commercial 5.5 2014-10-28 中文 Edit links Monkey HTTP Server Monkey Software LGPLv2 1.5.1 2014-06-10 NaviServer Various Mozilla 1.1 4.99.6 2014-06-29 NCSA HTTPd Robert McCool Non-free proprietary 1.5.2a 1996 Nginx NGINX, Inc. -

154 Core Jetty
#154 CONTENTS INCLUDE: n Jetty Architecture n Configuring Jetty n Basic Usage Jetty n Advanced Usage n Using with Web Frameworks A Lightweight, Open-Source Web Server and Servlet Container n Running Standalone By Jos Dirksen n Integration with Maven and more... Visit refcardz.com SelectChannelConnector Uses NIO buffers with a non-blocking threading ABOUT JETTY model. Threads are only allocated to connec- tions with requests. Use when there are many connections that have idle periods. Jetty, an open-source web server hosted by the Eclipse foundation, is a full-fledged HTTP server and Servlet container that can be easily SslSocketConnector SSL version of the SocketConnector configured to serve static and dynamic content. You can very easily SslSelectChannelConnector SSL version of the SelectChannelConnector embed Jetty into your own applications using Java or XML-based AJPConnector Use for connections from Apache modules: configuration or run Jetty directly from Maven. Additionally, you can use mod_proxy_ajp and mod_jk. Jetty in many different high-demand areas such as Yahoo Hadoop Cluster, HTTPSPDYServerConnector Supports the SPDY protocol and performs SPDY Google AppEngine, and Yahoo! Zimbra. to HTTP conversion. If SPDY is not negotiated, This RefCard refers primarily to Jetty 8; however, most of the configuration falls back to HTTPS. Get More Refcardz! Refcardz! Get More discussed will work on Jetty 7. Handler JETTY ARCHITECTURE The handler is the component that deals with requests received by a connector. There are three types of handlers in Jetty. It’s important to understand the architecture behind Jetty. The main • Coordinating handlers route requests to other handlers. architecture of Jetty consists out of the following four components. -
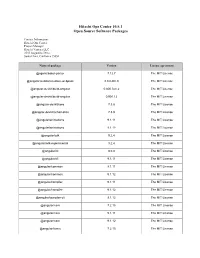
Open Source Software Packages
Hitachi Ops Center 10.5.1 Open Source Software Packages Contact Information: Hitachi Ops Center Project Manager Hitachi Vantara LLC 2535 Augustine Drive Santa Clara, California 95054 Name of package Version License agreement @agoric/babel-parser 7.12.7 The MIT License @angular-builders/custom-webpack 8.0.0-RC.0 The MIT License @angular-devkit/build-angular 0.800.0-rc.2 The MIT License @angular-devkit/build-angular 0.901.12 The MIT License @angular-devkit/core 7.3.8 The MIT License @angular-devkit/schematics 7.3.8 The MIT License @angular/animations 9.1.11 The MIT License @angular/animations 9.1.12 The MIT License @angular/cdk 9.2.4 The MIT License @angular/cdk-experimental 9.2.4 The MIT License @angular/cli 8.0.0 The MIT License @angular/cli 9.1.11 The MIT License @angular/common 9.1.11 The MIT License @angular/common 9.1.12 The MIT License @angular/compiler 9.1.11 The MIT License @angular/compiler 9.1.12 The MIT License @angular/compiler-cli 9.1.12 The MIT License @angular/core 7.2.15 The MIT License @angular/core 9.1.11 The MIT License @angular/core 9.1.12 The MIT License @angular/forms 7.2.15 The MIT License @angular/forms 9.1.0-next.3 The MIT License @angular/forms 9.1.11 The MIT License @angular/forms 9.1.12 The MIT License @angular/language-service 9.1.12 The MIT License @angular/platform-browser 7.2.15 The MIT License @angular/platform-browser 9.1.11 The MIT License @angular/platform-browser 9.1.12 The MIT License @angular/platform-browser-dynamic 7.2.15 The MIT License @angular/platform-browser-dynamic 9.1.11 The MIT License @angular/platform-browser-dynamic -

Teaching with Dynamic Documents Web Applications and Local Resources
Teaching with Dynamic Documents Web Applications and Local Resources Jerzy Karczmarczuk Dept. of Computer Science, University of Caen, Caen, France Keywords: HTML5, Javascript, SVG, Servers, Python, Tornado, AJAX, LaTeX, Mathematical Tools, Moodle, Nodejs, Websockets. Abstract: One of the bottlenecks in the application of computer methods in teaching is the limited effort in the develop- ment of tools for the creation of pedagogical material (documents, presentations, software). These tools exist, but they are often dispersed, and sometimes not well known. Some methodological work would be very useful. Our talk concentrates on the usage of Web-oriented infor- mation processing techniques, from the perspective of an individual: making presentations, scripting them, adding dynamical content from specialized servers, enhancing the interaction between different sources, etc. We give some simple examples belonging to the domain of teaching of sciences. The usage of servers help to modularize the teaching software support, avoiding big, monolithic applications. 1 PEDAGOGICAL CREATION used as the main interfaces. AND WEB TECHNOLOGIES The world-wide success of collaborative computer-assisted teaching platforms such as Moodle ((Dougiamas and Taylor, 2003; Moodle, 2015)), This talk is addressed mainly, not exclusively, to Chamilo, etc., is established. Course databases, teachers of mathematically oriented sciences, who cohort assembly, management of timed examinations want to prepare visually rich, dynamic, and inter- – all this frees the teachers’ -

US Cities Exposed a Shodan-Based Security Study on Exposed Assets in the US
US Cities Exposed A Shodan-Based Security Study on Exposed Assets in the US Numaan Huq, Stephen Hilt, and Natasha Hellberg Trend Micro Forward-Looking Threat Research (FTR) Team A TrendLabsSM Research Paper TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information Contents and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the 4 particular facts and circumstances presented and nothing herein should be construed otherwise. Trend Micro Exposed Cyber Assets reserves the right to modify the contents of this document at any time without prior notice. Translations of any material into other languages are intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions arise related to the accuracy of a translation, please refer to 6 the original language official version of the document. Any discrepancies or differences created in the translation are Exposed Cities not binding and have no legal effect for compliance or enforcement purposes. Although Trend Micro uses reasonable efforts to include accurate and up-to-date information herein, Trend Micro makes no warranties or representations of any kind as to its accuracy, currency, or completeness. You agree 36 that access to and use of and reliance on this document and the content thereof is at your own risk. Trend Micro Safeguarding Against disclaims all warranties of any kind, express or implied.