US Cities Exposed a Shodan-Based Security Study on Exposed Assets in the US
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
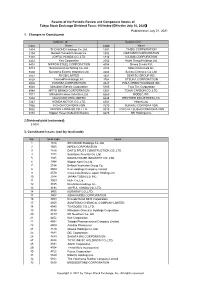
Published on July 21, 2021 1. Changes in Constituents 2
Results of the Periodic Review and Component Stocks of Tokyo Stock Exchange Dividend Focus 100 Index (Effective July 30, 2021) Published on July 21, 2021 1. Changes in Constituents Addition(18) Deletion(18) CodeName Code Name 1414SHO-BOND Holdings Co.,Ltd. 1801 TAISEI CORPORATION 2154BeNext-Yumeshin Group Co. 1802 OBAYASHI CORPORATION 3191JOYFUL HONDA CO.,LTD. 1812 KAJIMA CORPORATION 4452Kao Corporation 2502 Asahi Group Holdings,Ltd. 5401NIPPON STEEL CORPORATION 4004 Showa Denko K.K. 5713Sumitomo Metal Mining Co.,Ltd. 4183 Mitsui Chemicals,Inc. 5802Sumitomo Electric Industries,Ltd. 4204 Sekisui Chemical Co.,Ltd. 5851RYOBI LIMITED 4324 DENTSU GROUP INC. 6028TechnoPro Holdings,Inc. 4768 OTSUKA CORPORATION 6502TOSHIBA CORPORATION 4927 POLA ORBIS HOLDINGS INC. 6503Mitsubishi Electric Corporation 5105 Toyo Tire Corporation 6988NITTO DENKO CORPORATION 5301 TOKAI CARBON CO.,LTD. 7011Mitsubishi Heavy Industries,Ltd. 6269 MODEC,INC. 7202ISUZU MOTORS LIMITED 6448 BROTHER INDUSTRIES,LTD. 7267HONDA MOTOR CO.,LTD. 6501 Hitachi,Ltd. 7956PIGEON CORPORATION 7270 SUBARU CORPORATION 9062NIPPON EXPRESS CO.,LTD. 8015 TOYOTA TSUSHO CORPORATION 9101Nippon Yusen Kabushiki Kaisha 8473 SBI Holdings,Inc. 2.Dividend yield (estimated) 3.50% 3. Constituent Issues (sort by local code) No. local code name 1 1414 SHO-BOND Holdings Co.,Ltd. 2 1605 INPEX CORPORATION 3 1878 DAITO TRUST CONSTRUCTION CO.,LTD. 4 1911 Sumitomo Forestry Co.,Ltd. 5 1925 DAIWA HOUSE INDUSTRY CO.,LTD. 6 1954 Nippon Koei Co.,Ltd. 7 2154 BeNext-Yumeshin Group Co. 8 2503 Kirin Holdings Company,Limited 9 2579 Coca-Cola Bottlers Japan Holdings Inc. 10 2914 JAPAN TOBACCO INC. 11 3003 Hulic Co.,Ltd. 12 3105 Nisshinbo Holdings Inc. 13 3191 JOYFUL HONDA CO.,LTD. -

Synology Router Rt2600ac Hardware Installation Guide
Synology Router RT2600ac Hardware Installation Guide Table of Contents Chapter 1: Meet Your Synology Router Package Contents 3 Synology Router at a Glance 4 Safety Instructions 5 Chapter 2: Set up Your Synology Router Install Antennas 6 Position Your Synology Router 7 Connect to Your Synology Router 7 Set up Synology Router Manager (SRM) 9 Appendix A: Specifications Appendix B: LED Indicator Table Synology_HIG_RouterRT2600ac_20160930 2 Chapter Meet Your Synology Router 1 Thank you for purchasing this Synology product! Before setting up your new Synology Router, please check the package contents to verify that you have received all of the items below. Also, make sure to read the safety instructions carefully to avoid harming yourself or damaging your Synology Router. Note: All images below are for illustrative purposes only, and may differ from the actual product. Package Contents Main unit x 1 AC power adapter x 1 RJ-45 LAN cable x 1 Antenna x 4 3 Chapter 1: Meet Your Synology Router Synology Router at a Glance No. Article Name Location Description 1 Antenna Base Install the included antennas here. 2 Power Button Press to power on/off the Synology Router. 3 Power Port Connect the AC power adapter here. Press and hold for four seconds (Soft Reset) or for ten seconds (Hard 4 RESET Button Rear Panel Reset). Connect an external drive, USB printer, or other types of USB devices 5 USB 2.0 Port here. Connect a network cable from the ISP modem into this port to establish 6 WAN Port WAN connection. 7 LAN Port Connect network cables into these ports to establish LAN connection. -

Turn for More Solutions
Audio Solutions Installation & Design Services Servers Carts Kiosks Small Form Factor Computers Desktops Lighting Software PRODUCTS Disaster Recovery Products Notebooks & Tablets Telehealth Solutions Interactive Solutions Rugged Telemedicine Kits Temperature Sensing Kiosks Interactive Touchscreen LCDs Sanitizable Technology Wall-Mounted Arms & Cabinets A | COMPUTING SOLUTIONS D | VIRTUALIZATION 1. ACCESSORIES: Belkin, C2G, Case Logic, Kensington, Targus 1. BACKUP & DR: Arcserve, Barracuda, Nakivo, Veeam, Zerto 2. ANTIVIRUS: AVG, BitDefender, Malware Bytes, McAfee, Panda 2. CLOUD: Arcserve, Greencloud, Microsoft Security, Sophos, Symantec, Total Defense, Trend Micro 3. DESKTOP VIRTUALIZATION: Citrix, HVE, NComputing, VMWare 3. DESKTOPS: Howard, Dell, HP, Lenovo, Tangent 4. SERVER VIRTUALIZATION: Hyper-V, VMWare, XenServer 4. MANAGEMENT SOLUTIONS: Symantec 5. SERVERS: Howard, Dell, HPE, HVE, Lenovo, Microsoft, Nutanix 5. MOBILE PRESENTATION & CHARGING STATIONS: Aver, Bretford, 6. SOFTWARE-DEFINED STORAGE: Datacore Kwikboost, LocknCharge 7. STORAGE: Dell EMC, HPE, HVE, Lenovo, QNAP, Synology 6. NOTEBOOKS & TABLETS: Howard, Acer, Asus, Cybernet, Dell, Getac, HP, 8. VIRTUAL DESKTOP INFRASTRUCTURE: Citrix, Dell, HVE, Inuvika, LG, Lenovo, Microsoft, Panasonic, Samsung, Tangent, Toshiba, Xplore NComputing, VMWare 7. PRINTERS (2D & 3D): Brother, Canon, Dell, DYMO, Epson, HP, Lexmark, Panasonic, Samsung, Xerox 8. VIRTUAL REALITY: Epson, HP, Oculus Rift, Samsung E | PHYSICAL SECURITY 1. ACCESS CONTROL: 3xlogic, Avue Technologies, Axis, Bosch, B | AUDIOVISUAL SOLUTIONS GeoVision, Isonas, Openpath, MotorCast 2. CLOUD: Brivo, Openpath 1. AUDIO SOLUTIONS: Howard, AMX, Harman, Panasonic 3. DISPLAYS: LG, NEC, Panasonic, Planar, Samsung, Sharp, Sony, ViewSonic 2. BROADCASTING: Panasonic, Sony, Tri-Caster 4. ENCODERS: Axis, Bosch, Hikvision, Panasonic 3. CABLES: C2G, Comprehensive, Crestron, Peerless 5. MASS NOTIFICATION: Singlewire 4. FURNITURE: Middle Atlantic, Spectrum Industries, Worthington Direct 6. MOUNTING & ACCESSORIES: Advidia, Altronix, Avue Technologies, 5. -

Synology Rackstation RS1221RP+ Hardware Installation Guide
Synology NAS RS1221RP+ Hardware Installation Guide Table of Contents Chapter 1: Before You Start Package Contents 3 Synology RS1221RP+ at a Glance 4 System Modes and LED Indicators 6 Other LED Indicators 8 Hardware Specification 9 Spare Parts 10 Optional Accessories 10 Safety Instructions 11 Chapter 2: Hardware Setup Tools and Parts for Component Installation 12 Install Drives 12 Install Memory Modules 14 Install a PCle Add-in Card 17 Mount the Synology NAS to a 4-Post Rack 18 Start up Your Synology NAS 20 Chapter 3: System Maintenance Replace System Fan 21 Replace Power Supply Unit (PSU) 23 Chapter 4: Install DSM on Synology NAS Install DSM with Web Assistant 24 Learn More 24 Synology_HIG_RS1221RP+_20200928 2 Chapter Before You Start 1 Thank you for purchasing this Synology product! Before setting up your new Synology NAS, please check the package contents to verify that you have received the items below. Also, make sure to read the safety instructions carefully to avoid harming yourself or damaging your Synology NAS. Note: All images below are for illustrative purposes only, and may differ from the actual product. Package Contents Main unit x 1 AC power cord x 2 Screws for 3.5" drives x 36 Screws for 2.5" drives x 36 Drive tray key x 2 3 Synology RS1221RP+ at a Glance 1 23 4 5 6 7 7 8 9 10 11 12 13 8 14 15 No. Article Name Location Description Displays the power status of your Synology NAS. For more 1 POWER Indicator information, see "System Modes and LED Indicators". -
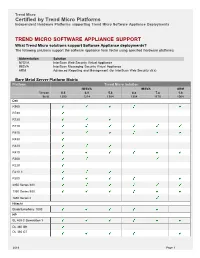
Certified by Trend Micro Platforms Independent Hardware Platforms Supporting Trend Micro Software Appliance Deployments
Trend Micro Certified by Trend Micro Platforms Independent Hardware Platforms supporting Trend Micro Software Appliance Deployments TREND MICRO SOFTWARE APPLIANCE SUPPORT What Trend Micro solutions support Software Appliance deployments? The following solutions support the software appliance form factor using specified hardware platforms Abbreviation Solution IWSVA InterScan Web Security Virtual Appliance IMSVA InterScan Messaging Security Virtual Appliance ARM Advanced Reporting and Management (for InterScan Web Security v5.x) Bare Metal Server Platform Matrix Platform Trend Micro Solution IWSVA IMSVA ARM Version 6.5 6.0 5.6 8.x 7.x 1.6 Build 1200 1214 1364 1304 1170 1068 Dell R900 R730 R720 R710 R610 R430 R420 R410 R300 R220 R210 II R200 2950 Series II/III 1950 Series II/III 1850 Series II Hitachi BladeSymphony 1000 HP BL 460 C Generation 1 DL 360 G9 DL 360 G7 2019 Page 1 Trend Micro Certified by Trend Micro Platforms Independent Hardware Platforms supporting Trend Micro Software Appliance Deployments Platform Trend Micro Solution IWSVA IMSVA ARM Version 6.5 6.0 5.6 8.x 7.x 1.6 Build 1200 1214 1364 1304 1170 1068 DL 360 G6 DL 380 G9 DL 380 G7 DL 380 G6 DL 380 G5 DL 385 G6 DL 385 G2 DL 350 G5 DL 388p G8 DL 380p G8 IBM Systems x3550 Systems x3550 M5 NEC Express5800 R120a-1 Express5800 R120RH-1 Resilience ATL 1012 Sun Sunfire X4450 SuperMicro Superserver 1026T Superserver 5016T Bare Metal Server Specifications Platform Hardware Specifications CPU Memory Hard Drive HD Controller NIC Dell PowerEdge R900 2 x Intel X7460 32GB Memory, 300 GB -

Next Generation Web Scanning Presentation
Next generation web scanning New Zealand: A case study First presented at KIWICON III 2009 By Andrew Horton aka urbanadventurer NZ Web Recon Goal: To scan all of New Zealand's web-space to see what's there. Requirements: – Targets – Scanning – Analysis Sounds easy, right? urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets What does 'NZ web-space' mean? It could mean: •Geographically within NZ regardless of the TLD •The .nz TLD hosted anywhere •All of the above For this scan it means, IPs geographically within NZ urbanadventurer (Andrew Horton) www.morningstarsecurity.com Finding Targets We need creative methods to find targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com DNS Zone Transfer urbanadventurer (Andrew Horton) www.morningstarsecurity.com Find IP addresses on IRC and by resolving lots of NZ websites 58.*.*.* 60.*.*.* 65.*.*.* 91.*.*.* 110.*.*.* 111.*.*.* 113.*.*.* 114.*.*.* 115.*.*.* 116.*.*.* 117.*.*.* 118.*.*.* 119.*.*.* 120.*.*.* 121.*.*.* 122.*.*.* 123.*.*.* 124.*.*.* 125.*.*.* 130.*.*.* 131.*.*.* 132.*.*.* 138.*.*.* 139.*.*.* 143.*.*.* 144.*.*.* 146.*.*.* 150.*.*.* 153.*.*.* 156.*.*.* 161.*.*.* 162.*.*.* 163.*.*.* 165.*.*.* 166.*.*.* 167.*.*.* 192.*.*.* 198.*.*.* 202.*.*.* 203.*.*.* 210.*.*.* 218.*.*.* 219.*.*.* 222.*.*.* 729,580,500 IPs. More than we want to try. urbanadventurer (Andrew Horton) www.morningstarsecurity.com IP address blocks in the IANA IPv4 Address Space Registry Prefix Designation Date Whois Status [1] ----- -

Dspace 1.8 Documentation
DSpace 1.8 Documentation DSpace 1.8 Documentation Author: The DSpace Developer Team Date: 03 November 2011 URL: https://wiki.duraspace.org/display/DSDOC18 Page 1 of 621 DSpace 1.8 Documentation Table of Contents 1 Preface _____________________________________________________________________________ 13 1.1 Release Notes ____________________________________________________________________ 13 2 Introduction __________________________________________________________________________ 15 3 Functional Overview ___________________________________________________________________ 17 3.1 Data Model ______________________________________________________________________ 17 3.2 Plugin Manager ___________________________________________________________________ 19 3.3 Metadata ________________________________________________________________________ 19 3.4 Packager Plugins _________________________________________________________________ 20 3.5 Crosswalk Plugins _________________________________________________________________ 21 3.6 E-People and Groups ______________________________________________________________ 21 3.6.1 E-Person __________________________________________________________________ 21 3.6.2 Groups ____________________________________________________________________ 22 3.7 Authentication ____________________________________________________________________ 22 3.8 Authorization _____________________________________________________________________ 22 3.9 Ingest Process and Workflow ________________________________________________________ 24 -

Building Multiplayer Games with Web Sockets #GHC19 About Us
Leveling Up: Building Multiplayer Games with Web Sockets #GHC19 About Us: #GHC19 Agenda 0. Introduction 1. Simple Chat Application 2. Multiplayer Game 3. Further Applications #GHC19 www.kahoot.com #GHC19 #GHC19 #GHC19 #GHC19 Diagram source: BMC Blog #GHC19 Diagram source: BMC Blog TCP and UDP are the transport level protocols TCP UDP Reliable Unreliable Connection-oriented Connectionless Segment sequencing No sequencing Acknowledge No acknowledgement segments #GHC19 Source: Pluralsight #GHC19 Diagram source: BMC Blog #GHC19 Diagram source: BMC Blog HTTP is used to share information on the application layer #GHC19 Graphic Source: Webnots Alternatives to WebSockets ● Browser Plug-Ins ● Polling ● Long Polling ● Server-Sent Events (SSE) #GHC19 The WebSocket protocol is used for real-time communication RFC-6455 #GHC19 Source: IETF RFC-6455 Some benefits of WebSockets Event driven Reduces network overhead - no need to send full HTTP requests HTTP compatible Co-exists on same port as your web server TLS/SSL compatible Same security as HTTPS #GHC19 WebSocket connection overview #GHC19 Diagram source: PubNub Staff Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Opening Handshake Client Handshake Server Handshake #GHC19 Source: IETF RFC-6455 Data Transfer Base Framing Protocol -

News Announcement Announcement
NEWS ANNOUNCEMENT DVBLogic , Synology and PCTV Systems Working Together to Bring Extended Freedom to TV at Home DVBLink Package Turns Synology NAS into Rich Featured Centre of Connected TV Experience Berlin, 12 September 2012 News Facts • DVBLink Package for up to four TV tuner s runs on most Synology NAS • Supports all popular DVB TV standards in parallel • Optimized for TV tuners from PCTV Systems • Live TV and recorded shows on DLNA enabled TVs and CE devices as well as computers (Windows, Mac and Linux) • Schedule and manage recordings via web interface and DVBLink Mobile Client Apps for iOS, Android and Win dows Phone • Electronic program guides (EPG) on all clients within the home network • DVBLink TV Server for Time-shift TV on all streaming clients Synology NAS turning the NAS • Stand-alone solution - works without a PC into a personal video recorder (PVR) and server for Live TV. Porting the DVBLink software into a Synology NAS package brings TV streaming, remote recording and EPG to NAS devices further freeing TV from being stuck on CE devices or in PC environments. Attached to any home network and equipped with a PCTV tuner, the NAS device becomes the central TV device at home. T he DVBLink App makes Live- TV and recorded content available on a number of clients throughout the house. Managing recordings and browsing the EPG is also available on mobile phones in the same Wi Fi thanks to the DVBLink Mobile Client Apps. All configuration and management of the Package is done via a web interface. A pure CE TV experience brings easy access to channels and programs on favourite TV device, needs no fiddling around with softwa re installations and only those devices up and running that are really necessary. -

GTC-ONE-Minute-Brief-92.Pdf
Equity | Currencies & Commodities | Corporate & Global Economic News & Economic Calendar 29 January 2019 Economic and political news Key indices Bosasa’s Ex-Chief Operating Officer, Angelo Agrizzi, in his testimony, As at 28 1 Day 1 D % WTD % MTD % Prev. month YTD % disclosed that the company agreed to pay ZAR300,000 a month to Jan 2019 Chg Chg Chg Chg % Chg Chg former President, Jacob Zuma’s charitable foundation to shield it from JSE All Share 53767.47 -282.76 -0.52 -0.52 1.95 4.09 1.95 prosecution. (ZAR) JSE Top 40 (ZAR) 47600.25 -292.16 -0.61 -0.61 1.87 4.63 1.87 South Africa’s Transport Minister, Blade Nzimande, stated that the government is keen to see South African Airways (SAA) debt restructured FTSE 100 (GBP) 6747.10 -62.12 -0.91 -0.91 0.28 -3.61 0.28 at the earliest. Meanwhile, SAA Chief Executive Officer, Vuyani Jarana, DAX 30 (EUR) 11210.31 -71.48 -0.63 -0.63 6.17 -6.20 6.17 stated that commercial banks have in principle approved ZAR3.5bn of CAC 40 (EUR) 4888.58 -37.24 -0.76 -0.76 3.34 -5.46 3.34 the funding SAA requires for operating expenses until April. S&P 500 (USD) 2643.85 -20.91 -0.78 -0.78 5.47 -9.18 5.47 Nasdaq Trade union, Solidarity, stated that former South African Broadcasting 7085.69 -79.18 -1.11 -1.11 6.79 -9.48 6.79 Corporation Chief Operating Officer, Hlaudi Motsoeneng, has made his Composite (USD) first payment of ZAR300,000 to the union. -

NAKIVO Backup & Replication V10.1
What’s New NAKIVO Backup & Replication v10.1 What’s New www.nakivo.com 1 What’s New What’s New in Backup for Microsoft Office 365 With NAKIVO Backup & Replication, businesses can ensure that their Microsoft Office 365 data is always accessible and recoverable when they face data loss events and ransomware attacks. With version 10.1, NAKIVO expands the functionality of Backup for Microsoft Office 365 to include protection for OneDrive for Business in addition to Exchange Online. Now you can use NAKIVO Backup & Replication to back up Exchange mailboxes and OneDrive for Business data and perform granular recovery of emails, attachments, files and folders. NAKIVO Backup & Replication is an all-in-one data protection solution for virtual, physical, cloud and SaaS environments. Customers can improve recovery times, reduce storage costs, shrink backup windows and automate data protection with a range of backup and recovery features. See for yourself how well NAKIVO Backup & Replication works in your environment with the 15-day Free Trial. OneDrive for Business Backup Backup for Microsoft Office 365 with NAKIVO Backup & Replication helps businesses to mitigate the risk of data loss by offering cost-effective backup and instant recovery for OneDrive for Business. Customers can: • Perform incremental backups of OneDrive • Locate OneDrive objects quickly by searching for Business data backups by file or folder name • Instantly recover OneDrive files and folders • Protect up to thousands of OneDrive for back to the original OneDrive account or Business user accounts with a single software different accounts deployment 2 What’s New Improvements • Ability to use locking functionality on a Backup • The Director service can now be restarted Repository so it can be used by only one directly from the web interface. -

Who Is Knocking on the Telnet Port: a Large-Scale Empirical Study of Network Scanning
Session 15: Network Security 2 ASIACCS’18, June 4–8, 2018, Incheon, Republic of Korea Who is Knocking on the Telnet Port: A Large-Scale Empirical Study of Network Scanning Hwanjo Heo Seungwon Shin KAIST KAIST ETRI [email protected] [email protected] ABSTRACT this information (i.e., who serves what) is absolutely imperative for Network scanning is the primary procedure preceding many net- attackers. Hence, attackers aggressively gather this information by work attacks. Until recently, network scanning has been widely directly searching target hosts or even employing already deployed studied to report a continued growth in volume and Internet-wide malware (e.g., botnet) for efficiency. trends including the underpinning of distributed scannings by lin- As such, since this network scanning is an indispensable process gering Internet worms. It is, nevertheless, imperative to keep us for cyber attacks, attention should still be paid to it, even though informed with the current state of network scanning, for factual it has been studied, investigated, and monitored for a long time. and comprehensive understanding of the security threats we are Indeed, researchers and practitioners have already deeply surveyed, facing, and new trends to serve as the presage of imminent threats. analyzed, and measured this behavior [3, 8, 26, 34, 35]. However, it In this paper, we analyze the up-to-date connection-level log should be kept in mind that the characteristics of network scanning data of a large-scale campus network to study the recent scanning (e.g., main target services and scan origins) are quite sensitive to the trends in breadth.