Best Simple Torrent Downloader Reddit
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
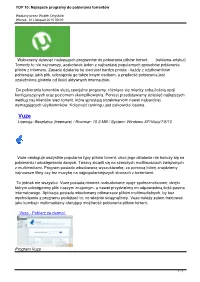
Najlepsze Programy Do Pobierania Torrentów
TOP 10: Najlepsze programy do pobierania torrentów Wpisany przez Wojtek Onyśków Wtorek, 10 Listopad 2015 09:00 Wybieramy dziesięć najlepszych programów do pobierania plików torrent. {reklama-artykul} Torrenty to nie najnowszy, aczkolwiek jeden z najbardziej popularnych sposobów pobierania plików z internetu. Zasada działania tej sieci jest bardzo prosta - każdy z użytkowników pobierając jakiś plik, udostępnia go także innym osobom, a prędkość pobierania jest uzależniona głównie od ilości aktywnych internautów. Do pobierania torrentów służą specjalne programy, różniące się między sobą ilością opcji konfiguracyjnych oraz poziomem skomplikowania. Poniżej przedstawiamy dziesięć najlepszych według nas klientów sieci torrent, które sprostają oczekiwaniom nawet najbardziej wymagających użytkowników. Kolejność rankingu jest całkowicie losowa. Vuze Licencja: Bezpłatna (freeware) / Rozmiar: 10.3 MB / System: Windows XP/Vista/7/8/10 Vuze obsługuje wszystkie popularne typy plików torrent, choć jego działanie nie kończy się na pobieraniu i udostępnianiu danych. Twórcy skupili się na szerszych możliwościach związanych z multimediami. Program posiada wbudowaną wyszukiwarkę, za pomocą której znajdziemy najnowsze filmy czy też muzykę na najpopularniejszych stronach z torrentami. To jednak nie wszystko. Vuze posiada również rozbudowane opcje społecznościowe, dzięki którym udostępnimy pliki naszym znajomym, a nawet przydzielimy im odpowiednią ilość pasma internetowego. Aplikacja posiada wbudowany odtwarzacz plików multimedialnych, by bez wychodzenia z programu podejrzeć to, co właśnie ściągnęliśmy. Vuze należy zatem traktować jako kombajn multimedialny oferujący możliwość pobierania plików torrent. Vuze - Pobierz za darmo! Program Vuze 1 / 7 TOP 10: Najlepsze programy do pobierania torrentów Wpisany przez Wojtek Onyśków Wtorek, 10 Listopad 2015 09:00 uTorrent Licencja: Bezpłatna (freeware) / Rozmiar: 1.73 MB / System: Windows XP/Vista/7/8/10 uTorrent to jeden z najpopularniejszych programów do pobierania plików torrent. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

New York University Annual Survey of American Law New York of American Law University Annual Survey
nys69-2_cv_nys69-2_cv 9/22/2014 8:41 AM Page 2 (trap 04 plate) Vol. 69 No. 2 Vol. New York University Annual Survey of American Law New York University Annual Survey of American Law New York ARTICLES TOWARD ADEQUACY Sarah L. Brinton SHOULD EVIDENCE OF SETTLEMENT NEGOTIATIONS AFFECT ATTORNEYS’ FEES AWARDS? Seth Katsuya Endo A LOOK INSIDE THE BUTLER’S CUPBOARD: HOW THE EXTERNAL WORLD REVEALS INTERNAL STATE OF MIND IN LEGAL NARRATIVES Cathren Koehlert-Page NOTES EXPERTISE AND IMMIGRATION ADMINISTRATION: WHEN DOES CHEVRON APPLY TO BIA INTERPRETATIONS OF THE INA? Paul Chaffin WHAT MOTIVATES ILLEGAL FILE SHARING? EMPIRICAL AND THEORETICAL APPROACHES Joseph M. Eno 2013 Volume 69 Issue 2 2013 35568-nys_69-2 Sheet No. 1 Side A 10/28/2014 12:36:12 \\jciprod01\productn\n\nys\69-2\FRONT692.txt unknown Seq: 1 23-OCT-14 9:10 NEW YORK UNIVERSITY ANNUAL SURVEY OF AMERICAN LAW VOLUME 69 ISSUE 2 35568-nys_69-2 Sheet No. 1 Side A 10/28/2014 12:36:12 NEW YORK UNIVERSITY SCHOOL OF LAW ARTHUR T. VANDERBILT HALL Washington Square New York City 35568-nys_69-2 Sheet No. 1 Side B 10/28/2014 12:36:12 \\jciprod01\productn\n\nys\69-2\FRONT692.txt unknown Seq: 2 23-OCT-14 9:10 New York University Annual Survey of American Law is in its seventy-first year of publication. L.C. Cat. Card No.: 46-30523 ISSN 0066-4413 All Rights Reserved New York University Annual Survey of American Law is published quarterly at 110 West 3rd Street, New York, New York 10012. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Comodo System Cleaner Version 3.0
Comodo System Cleaner Version 3.0 User Guide Version 3.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Comodo System Cleaner - User Guide Table of Contents 1.Comodo System-Cleaner - Introduction ............................................................................................................ 3 1.1.System Requirements...........................................................................................................................................5 1.2.Installing Comodo System-Cleaner........................................................................................................................5 1.3.Starting Comodo System-Cleaner..........................................................................................................................9 1.4.The Main Interface...............................................................................................................................................9 1.5.The Summary Area.............................................................................................................................................11 1.6.Understanding Profiles.......................................................................................................................................12 2.Registry Cleaner............................................................................................................................................. 15 2.1.Clean.................................................................................................................................................................16 -

Vysoké Učení Technické V Brně Detekcia Seedboxov V Sieti Bittorrent
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ FACULTY OF INFORMATION TECHNOLOGY ÚSTAV INFORMAČNÍCH SYSTÉMŮ DEPARTMENT OF INFORMATION SYSTEMS DETEKCIA SEEDBOXOV V SIETI BITTORRENT DETECTION OF SEEDBOXES INBITTORRENT NETWORK BAKALÁŘSKÁ PRÁCE BACHELOR’S THESIS AUTOR PRÁCE MARTIN GRNÁČ AUTHOR VEDOUCÍ PRÁCE Ing. LIBOR POLČÁK, Ph.D. SUPERVISOR BRNO 2018 Abstrakt Bakalárska práca sa venuje problematike sledovania a detekcie seedboxov v sieti BitTorrent za pomoci technológie netflow. V teoretickej časti je predstavená a popísaná architektúra P2P, základy a kľúčové pojmy architektúry BitTorrent a teoretická definícia seedboxu. Taktiež sú tu rozobrané metódy pomocou ktorých sa dá detekovať sieťová komunikácia a ďalej je uvedená analýza seedboxov v sieti a hľadanie ich charakteristík. Na základe týchto znalostí a sledovaní je navrhnutá sada nástrojov, ktoré napomáhajú ich detekcií. V praktickej časti je predstavená implementácia týchto nástrojov a výsledky ich testovania. Abstract Bachelor’s thesis is focused on issues with monitoring and detection of seedboxes in Bit- Torrent network with help of netflow technology. In the theoretical part of this thesis is introduced and described P2P architecture, basics and key terms of BitTorrent architec- ture and theoretical definition of seedbox. There are also described specific methods which can be used for detection of network communication and next there is described process of seedbox analysis in network and process of finding its characteristics. On base of this kno- wledge and observations is designed a set of tools,which help with detection of seedboxes. In the practical part of this work is presented implementation of these tools and results of testing these tools. Kľúčové slová BitTorrent, seedbox, detekcia, netflow, analýza, sieťová prevádzka, P2P, netflow Keywords BitTorrent, seedbox, detection, netflow, analysis, network traffic, P2P, netflow Citácia GRNÁČ, Martin. -

Digital Fountain Erasure-Recovery in Bittorrent
UNIVERSITÀ DEGLI STUDI DI BERGAMO Facoltà di Ingegneria Corso di Laurea Specialistica in Ingegneria Informatica Classe n. 35/S – Sistemi Informatici Digital Fountain Erasure Recovery in BitTorrent: integration and security issues Relatore: Chiar.mo Prof. Stefano Paraboschi Correlatore: Chiar.mo Prof. Andrea Lorenzo Vitali Tesi di Laurea Specialistica Michele BOLOGNA Matricola n. 56108 ANNO ACCADEMICO 2007 / 2008 This thesis has been written, typeset and prepared using LATEX 2". Printed on December 5, 2008. Alla mia famiglia “Would you tell me, please, which way I ought to go from here?” “That depends a good deal on where you want to get to,” said the Cat. “I don’t much care where —” said Alice. “Then it doesn’t matter which way you go,” said the Cat. “— so long as I get somewhere,” Alice added as an explanation. “Oh, you’re sure to do that,” said the Cat, “if you only walk enough.” Lewis Carroll Alice in Wonderland Acknowledgments (in Italian) Ci sono molte persone che mi hanno aiutato durante lo svolgimento di questo lavoro. Il primo ringraziamento va ai proff. Stefano Paraboschi e Andrea Vitali per la disponibilità, la competenza, i consigli, la pazienza e l’aiuto tecnico che mi hanno saputo dare. Grazie di avermi dato la maggior parte delle idee che sono poi confluite nella mia tesi. Un sentito ringraziamento anche a Andrea Rota e Ruben Villa per l’aiuto e i chiarimenti che mi hanno gentilmente fornito. Vorrei ringraziare STMicroelectronics, ed in particolare il gruppo Advanced System Technology, per avermi offerto le infrastrutture, gli spa- zi e tutto il necessario per svolgere al meglio il mio periodo di tirocinio. -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -

Downloading Copyrighted Materials
What you need to know before... Downloading Copyrighted Materials Including movies, TV shows, music, digital books, software and interactive games The Facts and Consequences Who monitors peer-to-peer file sharing? What are the consequences at UAF The Motion Picture Association of America for violators of this policy? (MPAA), Home Box Office, and other copyright Student Services at UAF takes the following holders monitor file-sharing on the Internet minimum actions when the policy is violated: for the illegal distribution of their copyrighted 1st Offense: contents. Once identified they issue DMCA Loss of Internet access until issue is resolved. (Digital Millennium Copyright Act) take-down 2nd Offense: notices to the ISP (Internet Service Provider), in Loss of Internet access pending which the University of Alaska is considered as resolution and a $100 fee assessment. one, requesting the infringement be stopped. If 3rd Offense: not stopped, lawsuit against the user is possible. Loss of Internet access pending resolution and a $250 fee assessment. What is UAF’s responsibility? 4th, 5th, 6th Offense: Under the Digital Millennium Copyright Act and Loss of Internet access pending resolution and Higher Education Opportunity Act, university a $500 fee assessment. administrators are obligated to track these infractions and preserve relevent logs in your What are the Federal consequences student record. This means that if your case goes for violators? to court, your record may be subpoenaed as The MPAA, HBO and similar organizations are evidence. Since illegal file sharing also drains becoming more and more aggressive in finding bandwidth, costing schools money and slowing and prosecuting alleged offenders in criminal Internet connections, for students trying to use court. -
No Ad Torrent Downloader No Ad Torrent Downloader
no ad torrent downloader No ad torrent downloader. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67a27aef1d21c3d9 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. BitCloudTorrent Downloader (No Ad) for PC. Download BitCloudTorrent Downloader (No Ad) PC for free at BrowserCam. Foossi Inc. published BitCloudTorrent Downloader (No Ad) for Android operating system mobile devices, but it is possible to download and install BitCloudTorrent Downloader (No Ad) for PC or Computer with operating systems such as Windows 7, 8, 8.1, 10 and Mac. Let's find out the prerequisites to install BitCloudTorrent Downloader (No Ad) on Windows PC or MAC computer without much delay. Select an Android emulator: There are many free and paid Android emulators available for PC and MAC, few of the popular ones are Bluestacks, Andy OS, Nox, MeMu and there are more you can find from Google. Compatibility: Before downloading them take a look at the minimum system requirements to install the emulator on your PC. -

Multi-Core Architecture for Anonymous Internet Streaming
Multi-core architecture for anonymous Internet streaming Quinten Stokkink Multi-core architecture for anonymous Internet streaming Master’s Thesis in Computer Science Parallel and Distributed Systems group Faculty of Electrical Engineering, Mathematics, and Computer Science Delft University of Technology Quinten Stokkink 3rd March 2017 Author Quinten Stokkink Title Multi-core architecture for anonymous Internet streaming MSc presentation 15th March 2017 Graduation Committee Graduation professor: Prof. dr. ir. D. H. J. Epema Delft University of Technology Supervisor: Dr. ir. J. A. Pouwelse Delft University of Technology Committee member: Dr. Z. Erkin Delft University of Technology Abstract There are two key components for high throughput distributed anonymizing ap- plications. The first key component is overhead due to message complexity of the utilized algorithms. The second key component is an nonscalable architecture to deal with this high throughput. These issues are compounded by the need for an- onymization. Using a state of the art serialization technology has been shown to increase performance, in terms of CPU utilization, by 65%. This is due to the com- pression (byte stuffing) used by this technology. It also decreased lines of code in the Tribler project by roughly 2000 lines. Single-core architectures are shown to be optimizable by performing a minimum s,t-cut on the data flows within the original architecture: between the entry point and the most costly CPU-utilizing compon- ent as derived from profiling the application. This method is used on the Tribler technology to create a multi-core architecture. The resulting architecture is shown to be significantly more efficient in terms of consumed CPU for the delivered file download speed. -

Master's Thesis
MASTER'S THESIS Analysis of UDP-based Reliable Transport using Network Emulation Andreas Vernersson 2015 Master of Science in Engineering Technology Computer Science and Engineering Luleå University of Technology Department of Computer Science, Electrical and Space Engineering Abstract The TCP protocol is the foundation of the Internet of yesterday and today. In most cases it simply works and is both robust and versatile. However, in recent years there has been a renewed interest in building new reliable transport protocols based on UDP to handle certain problems and situations better, such as head-of-line blocking and IP address changes. The first part of the thesis starts with a study of a few existing reliable UDP-based transport protocols, SCTP which can also be used natively on IP, QUIC and uTP, to see what they can offer and how they work, in terms of features and underlying mechanisms. The second part consists of performance and congestion tests of QUIC and uTP imple- mentations. The emulation framework Mininet was used to perform these tests using controllable network properties. While easy to get started with, a number of issues were found in Mininet that had to be resolved to improve the accuracy of emulation. The tests of QUIC have shown performance improvements since a similar test in 2013 by Connectify, while new tests have identified specific areas that might require further analysis such as QUIC’s fairness to TCP and performance impact of delay jitter. The tests of two different uTP implementations have shown that they are very similar, but also a few differences such as slow-start growth and back-off handling.