View the Thesis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2017-18 Annual Report
Helping Canadians for 10+ YEARS 2017-18 ANNUAL REPORT “I was very impressed with your services” – L.T., wireless customer in BC “I was very satisfied with the process.” – H.R., internet customer in ON “Awesome service. We are very content with the service and resolution.” – G.C., phone customer in NS “My agent was nice and super understanding” – D.W., TV customer in NB “I was very impressed with your services” – L.T., wireless customer in BC “I was very satisfied with the process.”– H.R., internet customer in ON “Awesome service. We are very content with the service and resolution.” – G.C., phone customer in NS “My agent was nice and super understanding” – D.W., TV customer in NB “I was very impressed with your services” – L.T., wireless customer in BC “I was very satisfied with the process.”– H.R., internet customer in ON “Awesome service. We are very content with the service and resolution.” – G.C., phone customer in NS “My agent was nice and super understanding” – D.W., TV customer in NB “I was very impressed with your services” –L.T., wireless customer in BC “I was very satisfied with the process.” – H.R., internet customer in ON “Awesome service. We are very content with the service and resolution.” – G.C., phone customer in NS “My agent was nice and super understanding” – D.W., TV customer in NB “I was very impressed with your services” – L.T., wireless customer in BC P.O. Box 56067 – Minto Place RO, Ottawa, ON K1R 7Z1 www.ccts-cprst.ca [email protected] 1-888-221-1687 TTY: 1-877-782-2384 Fax: 1-877-782-2924 CONTENTS 2017-18 -

Cologix Vancouver: Metro Connect Services Convenient, Simple Solution to Increase Access Across Data Centres Within a Metro Market
Cologix Vancouver: Metro Connect Services Convenient, simple solution to increase access across data centres within a metro market Cologix’s Metro Connect is a low-cost product offering that extends Cologix’s dense network availability to customers regardless of data centre location within a market. Metro Connect is a fibre-based service that offers bandwidth of 100Mb (FastE), 1000Mb (GigE), or 10G and higher (Passive Wave). FastE and GigE services are delivered through a Cologix switch to the customer via a copper cross-connect. The Passive Wave offering provides a dedicated lambda over Cologix fibre that customers must light with their own network equipment. Customers are able to request one of two diverse routes for all three services. Cologix Vancouver Metro Connect enables: Connections between Extended carrier and network A low-cost alternative to local Cologix’s 2 Vancouver data choice loops centres Our Vancouver Metro Connect product provides connections between 1050 West Pender and 555 West Hastings over shared dark fiber and Cologix-operated network equipment. The product comes in several different confgurations to solve various customer requirements. All Metro Connect services include a cross-connect within each facility to provide a complete end-to-end service. Cologix Vancouver Metro Connect Map Quick Facts: • Network neutral access to 10+ unique carriers on-site plus 20+ networks at the Redundant bre routes ymor St. Harbour Centre via Se have 1 meter clearance diverse fibre ring 1 Meter between duct systems • Home to the primary -
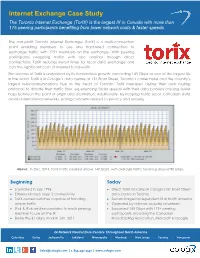
Cologix Torix Case Study
Internet Exchange Case Study The Toronto Internet Exchange (TorIX) is the largest IX in Canada with more than 175 peering participants benefiting from lower network costs & faster speeds The non-profit Toronto Internet Exchange (TorIX) is a multi-connection point enabling members to use one hardwired connection to exchange traffic with 175+ members on the exchange. With peering participants swapping traffic with one another through direct connections, TorIX reduces transit times for local data exchange and cuts the significant costs of Internet bandwidth. The success of TorIX is underlined by its tremendous growth, exceeding 145 Gbps as one of the largest IXs in the world. TorIX is in Cologix’s data centre at 151 Front Street, Toronto’s carrier hotel and the country’s largest telecommunications hub in the heart of Toronto. TorIX members define their own routing protocols to dictate their traffic flow, experiencing faster speeds with their data packets crossing fewer hops between the point of origin and destination. Additionally, by keeping traffic local, Canadian data avoids international networks, easing concerns related to privacy and security. Above: In Dec. 2014, TorIX traffic peaked above 140 Gbps, with average traffic hovering around 90 Gbps. Beginning Today Launched in July 1996 Direct TorIX on-ramp in Cologix’s151 Front Street Ethernet-based, layer 2 connectivity data centre in Toronto TorIX-owned switches capable of handling Second largest independent IX in North America ample traffic Operated by telecom industry volunteers IPv4 & IPv6 address provided to each peering Surpassed 145 Gbps with 175+ peering member to use on the IX participants, including the Canadian Broke the 61 Gbps mark in Jan. -

Cologix Montreal: Metro Connect Services Convenient, Simple Solution to Increase Access Across Data Centres Within a Metro Market
Cologix Montreal: Metro Connect Services Convenient, simple solution to increase access across data centres within a metro market Cologix’s Metro Connect is a low-cost product offering that extends Cologix’s dense network availability to customers regardless of data centre location within a market. Metro Connect is a fibre-based service that offers bandwidth of 100Mb (FastE), 1000Mb (GigE), or 10G and higher (Passive Wave). FastE and GigE services are delivered through a Cologix switch to the customer via a copper cross-connect. The Passive Wave offering provides a dedicated lambda over Cologix fibre that customers must light with their own network equipment. Customers are able to request one of two diverse routes for all three services. Cologix Montreal Metro Connect enables: Connections between Extended carrier and network A low-cost alternative to local Cologix’s 7 Montreal data choice loops centres Cologix’s Montreal Metro Connect product provides connections between the MTL1, Quick Facts: MTL2, MTL3, MTL4, MTL5, MTL6 and MTL7 data centres over shared dark fibre and Cologix-operated network equipment. The product comes in several different • Cologix operates confgurations to solve various customer requirements. All Metro Connect services include approx. 100,000 SQF across 7 a cross-connect within each facility to provide a complete end-to-end service. Montreal data centres • 2 pairs of 40-channel Cologix Montreal Metro Connect Map DWDM Mux-Demuxes (working and protect) enable 40x100 Gbps between each facility = 4Tbps Metro Optical -

State of Alberta Digital Infrastructure Report 2021
cybera.ca | [email protected] State of Alberta Digital Infrastructure Report 2021 Cybera Inc. Calgary Oce: Suite 200, 3512 - 33 St NW, Calgary, AB T2L 2A6 T: 403-210-5333 Edmonton Oce: Suite 1101, 10065 Jasper Avenue NW, Edmonton, AB T5J 3B1 cybera.ca | [email protected] | @cybera Table Of Contents Revision History Executive Summary Networking – At a Glance Recommendations for Improving Networking in Alberta Introduction Networking in Alberta Background Current Landscape: Broadband Availability in Alberta Alberta SuperNet: Vision and History CyberaNet Large Internet Service Providers (ISPs) Municipal / Community Networks Mobile Broadband Service 5G Rural First Nations Emergency Communication System Internet Exchange Points Low Earth Orbit Satellites (LEOs) Changes in the policy and regulatory landscape Other infrastructure owners IPv6 Future Needs and Opportunities Conclusion Appendices About Cybera Acknowledgements 2 Revision History DATE REVISED BY VERSION REVISIONS Oct 10, 2014 Cybera 0.9 Development of the first draft. Oct 20, 2014 Cybera 1.0 Revisions to all sections. Additions of the Executive Summary, Introduction and Data section. Oct 31, 2014 Cybera 1.1 Revisions to all sections. Sept 13, 2016 Cybera 2.0 Updated network section & acknowledgements. Updated hyperlinks and citations. July 15, 2021 Cybera 3.0 Updated all sections and added new content. 3 Executive Summary Digital infrastructure has become the foundation for innovation, economic growth and market diversification in Canada. Our network infrastructure, in particular, drives productivity, growth and competitiveness, and serves as an integral component of how individuals connect and interact with each other. As governments around the world plan for the future, digital infrastructure investments are being recognized as the bedrock upon which innovation in science and technology can be harnessed for the public good. -

Le Développement Des Startups En Contexte D'incertitude Et L'analyse
1. Louvain School of Management (LSM) Le développement des startups en contexte d’incertitude et l’analyse de la prise de décision dans une équipe multiculturelle Mémoire à titre « Confidentiel » Mémoire-projet réalisé par Sara BARATA CARRILHO Promoteur Julie HERMANS Lecteur Malo BEGUIN Année académique 2017-2018 En vue de l’obtention du diplôme Master 120 en Sciences de gestion Chaussée de Binche, 151 - 7000 Mons, Belgique www.uclouvain.be/lsm Mémoire à titre confidentiel 2. RESUME Ayant vu le jour aux Etats, Unis, le terme « startup » n’existe pas depuis longtemps. Il ne s’est généralisé à l’international que depuis une grosse vingtaine d’année. Mais son statut de petite entreprise ne l’empêche pas de devoir faire face à son environnement interne et externe tout comme les multinationales. La recherche exploratoire suivante aura lieu d’analyser les particularités organisationnelles liées à la communication interne d’une jeune startup canadienne, intitulée Planhub, ainsi que de proposer quelques recommandations managériales pour aborder au mieux le contexte d’incertitude dans lequel elle se développe. Mots clés : contexte d’incertitude, dissidence stratégique, prise de parole, silence organisationnel, recommandations managériales. Mémoire à titre confidentiel 3. REMERCIEMENTS Je voudrais sincèrement remercier ma promotrice, Julie Hermans, qui a accepté de m’encadrer dans cette recherche exploratoire même à distance. Ses conseils et sa disponibilité m’ont été très précieux dans la réalisation de mon mémoire. Je tiens également à remercier l’équipe managériale de l’entreprise, qui a accepté de soumettre leur startup comme sujet d’étude, ainsi que le reste de l’équipe qui a pris le temps de répondre aux questionnaires individuels. -
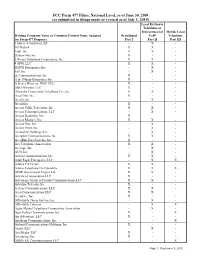
FCC Form 477 Filers, National Level, As of June 30, 2009 (As Submitted in Filings Made Or Revised As of July 1, 2010)
FCC Form 477 Filers, National Level, as of June 30, 2009 (as submitted in filings made or revised as of July 1, 2010) Local Exchange Telephone or Interconnected Mobile Local Holding Company Name or Common-Control Name Assigned Broadband VoIP Telephone for Form 477 Purposes Part I Part II Part III 1 Starview Solutions, LP - X - 101Netlink X X - 1stel, Inc. X X - 2Geton Net, Inc. X - - 3 Rivers Telephone Cooperative, Inc. X X - 4 SIWI LLC X X - 5LINX Enterprises, Inc. - X - 8x8, Inc. - X - @ Communications, Inc. X - - A & J Hardy Enterprises Inc. X - - A Better Wireless, NISP, LLC X - - ABG Wireless, LLC X - - Absaraka Cooperative Telephone Co., Inc. X X - Accel Net, Inc. X - - Accela, Inc. - X - Accelplus X - - Access Cable Television, Inc. X X - Access Communications, LLC - X - Access Kentucky, Inc. X - - Access Media 3, Inc. X X - Access One, Inc. - X - Access Point, Inc. - X - Accessline Holdings, Inc. - X - Accipiter Communications, Inc. X X - AccuBak Data Systems, Inc. X - - Ace Telephone Association X X - Acecape, Inc. - X - ACN, Inc. - X - Action Communications, Inc. X X - Adak Eagle Enterprises, LLC - X X Adams CATV Inc. X X - Adams Telephone Co-Operative X X X ADIR International Export Ltd. X X - Advanced Automation LLC X - - Advantage Group of Florida Communications LLC X X - Advanza Telecom, Inc. X - - Aeneas Communications, LLC X X - Aero Communications LLC X X - Aerowire, Inc. X - - Affordable Phone Service, Inc. - X - Affordable Telecom - X X Agate Mutual Telephone Cooperative Association - X - Agri-Valley Communications, Inc. X - X Air Advantage, LLC X - - Airadigm Communications, Inc. -
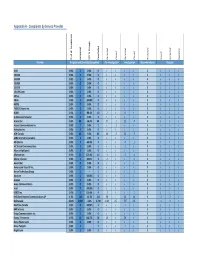
Appendix A: Complaints by Service Provider
Appendix A ‐ Complaints by Service Provider Complaints Change all % of Concluded Resolved Closed Resolved Closed Accepted Issued Accepted Rejected Accepted Y/Y % Provider Accepted and Concluded Complaints Pre‐Investigation Investigation Recommendation Decision #100 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010100 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010580 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010620 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010738 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1011295.com 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 295.ca 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 3Web 0.0% 0 ‐100.0% 0 0 0 0 0 0 0 0 0 450Tel 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 768812 Ontario Inc. 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 8COM 0.1% 8 ‐88.4% 10 2 0 8 0 0 0 0 0 A dimension humaine 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 Acanac Inc. 0.6% 64 ‐16.9% 64 37 1224 0 0 0 0 Access Communications Inc. 0.0% 1 0.0% 1 0 1 0 0 0 0 0 0 Achatplus Inc. 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 ACN Canada 0.8% 82 9.3% 81 54 2 22 3 0 0 0 0 AEBC Internet Corporation 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 AEI Internet 0.0% 3 ‐40.0% 5 0 0 41 0 0 0 0 AIC Global Communications 0.0% 1 0.0% 1 0 0 1 0 0 0 0 0 Alberta High Speed 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 Allstream Inc. -
ONN 6 Eng Codelist Only Webversion.Indd
6-DEVICE UNIVERSAL REMOTE Model: 100020904 CODELIST Need help? We’re here for you every day 7 a.m. – 9 p.m. CST. Give us a call at 1-888-516-2630 Please visit the website “www.onn-support.com” to get more information. 1 TABLE OF CONTENTS CODELIST TV 3 STREAM 5 STB 5 AUDIO SOUNDBAR 21 BLURAY DVD 22 2 CODELIST TV TV EQD 2014, 2087, 2277 EQD Auria 2014, 2087, 2277 Acer 4143 ESA 1595, 1963 Admiral 3879 eTec 2397 Affinity 3717, 3870, 3577, Exorvision 3953 3716 Favi 3382 Aiwa 1362 Fisher 1362 Akai 1675 Fluid 2964 Akura 1687 Fujimaro 1687 AOC 3720, 2691, 1365, Funai 1595, 1864, 1394, 2014, 2087 1963 Apex Digital 2397, 4347, 4350 Furrion 3332, 4093 Ario 2397 Gateway 1755, 1756 Asus 3340 GE 1447 Asustek 3340 General Electric 1447 Atvio 3638, 3636, 3879 GFM 1886, 1963, 1864 Atyme 2746 GPX 3980, 3977 Audiosonic 1675 Haier 2309, 1749, 1748, Audiovox 1564, 1276, 1769, 3382, 1753, 3429, 2121 2293, 4398, 2214 Auria 4748, 2087, 2014, Hannspree 1348, 2786 2277 Hisense 3519, 4740, 4618, Avera 2397, 2049 2183, 5185, 1660, Avol 2735, 4367, 3382, 3382, 4398 3118, 1709 Hitachi 1643, 4398, 5102, Axen 1709 4455, 3382, 0679 Axess 3593 Hiteker 3118 BenQ 1756 HKPro 3879, 2434 Blu:sens 2735 Hyundai 4618 Bolva 2397 iLo 1463, 1394 Broksonic 1892 Insignia 2049, 1780, 4487, Calypso 4748 3227, 1564, 1641, Champion 1362 2184, 1892, 1423, Changhong 4629 1660, 1963, 1463 Coby 3627 iSymphony 3382, 3429, 3118, Commercial Solutions 1447 3094 Conia 1687 JVC 1774, 1601, 3393, Contex 4053, 4280 2321, 2271, 4107, Craig 3423 4398, 5182, 4105, Crosley 3115 4053, 1670, 1892, Curtis -

Telecom Public Notice CRTC 2006-14-2
Telecom Public Notice CRTC 2006-14-2 Ottawa, 15 February 2007 Review of regulatory framework for wholesale services and definition of essential service Reference: 8663-C12-200614439 1. In this Public Notice, the Commission further amends the list of companies that are made parties to the proceeding established in Review of regulatory framework for wholesale services and definition of essential service, Telecom Public Notice CRTC 2006-14, 9 November 2006, as amended by Telecom Public Notice CRTC 2006-14-1, 15 December 2006, (Public Notice 2006-14). The Commission also amends certain procedures and the associated schedule dates. 2. In Public Notice 2006-14 at paragraph 28, the Commission set out the list of those entities that were made parties to the proceeding as follows: Bell Aliant Regional Communications, Limited Partnership (Bell Aliant), Bell Canada, Bragg Communications Inc. operating as EastLink, Cogeco Cable Inc. (Cogeco), MTS Allstream Inc. (MTS Allstream), Rogers Communications Inc. (RCI), Saskatchewan Telecommunications (SaskTel), Shaw Cablesystems G. P. (Shaw), Société en commandite Télébec (Télébec), TELUS Communications Company (TCC) and Vidéotron Ltd. (Vidéotron). 3. By letter dated 22 December 2006, Bell Canada requested that the Commission amend the list of entities that were made parties to add, as parties, all municipal electrical utility companies (MEUs) that offered and/or provided wholesale telecommunications services.1 4. By letter dated 4 January 2007, TCC supported Bell Canada's request2 and further submitted that all Canadian carriers should be made parties by the Commission. 5. On 12 January 2007, MTS Allstream filed comments to the Commission that opposed Bell Canada's and TCC's requests. -

Acquisition of Columbus International Inc Placing of New Shares
NOT FOR RELEASE, PUBLICATION OR DISTRIBUTION IN OR INTO THE UNITED STATES OF AMERICA, CANADA, AUSTRALIA, JAPAN OR SOUTH AFRICA OR ANY JURISDICTION WHERE TO DO SO WOULD VIOLATE THE LAWS OF THAT JURISDICTION 6 NOVEMBER 2014 CABLE & WIRELESS COMMUNICATIONS PLC PROPOSED ACQUISITION OF COLUMBUS INTERNATIONAL INC PLACING OF NEW SHARES The Board of Cable & Wireless Communications Plc (“CWC”) today announces that it has agreed terms to purchase 100 per cent. of the equity of Columbus International Inc, a leading privately-owned fibre- based telecommunications and technology services provider operating in the Caribbean, Central America and the Andean region, for USD1.85bn The move will significantly enhance CWC’s growth profile and accelerate the progress towards each of its strategic goals unveiled in May CWC also announces the placing of new shares constituting approximately 9.99 per cent. of CWC's outstanding share capital which will be used to finance in part the proposed acquisition The Enlarged Group is expected to generate significant operating cost and capital expenditure synergies, with additional revenue benefits also available The transaction will be earnings neutral in the first full year post-completion and materially earnings enhancing in subsequent years CWC's current dividend policy of 4c per share to be maintained post-completion The Board of Cable & Wireless Communications Plc ("CWC" or the "Company") today announces that it has agreed terms to acquire Columbus International Inc ("Columbus") for consideration of approximately USD1.85bn (for 100 per cent. of the equity). In addition, CWC will assume Columbus’ existing net debt as part of the Acquisition, which was USD1.17bn1 as at 30 June 2014. -

Broadband Study
Appendix A TORONTO BROADBAND STUDY Prepared for the City of Toronto by: FONTUR International Inc. MDB Insight Inc. October 2017 [FINAL v4] Table of Contents GLOSSARY .............................................................................................................................................................. 4 EXECUTIVE SUMMARY ........................................................................................................................................... 6 1 WHAT IS BROADBAND, AND WHY IS IT IMPORTANT? ................................................................................... 8 DEFINING BROADBAND ................................................................................................................................................... 8 INVESTMENT IN BROADBAND ACCESSIBILITY & AFFORDABILITY AS A KEY ELEMENT TO SMART CITY DEVELOPMENT & JOB CREATION .... 9 RESPONDING TO THE PRESSURES OF THE DIGITAL ECONOMY ................................................................................................ 12 2 BROADBAND TRENDS .................................................................................................................................. 14 BROADBAND OVER LTE (WIRELESS)................................................................................................................................. 14 5TH GENERATION CARRIER WIRELESS (5G) ........................................................................................................................ 15 INTERNET OF THINGS (IOT) ...........................................................................................................................................