Skype for Business Is Available for All RSCCD Employees
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
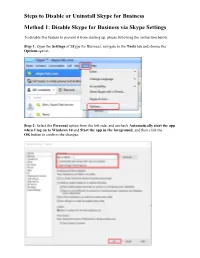
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Integrating Business Processes with Microsoft Lync & Skype for Business
Integrating Business Processes with Microsoft Lync & Skype for Business A Knowledge Guide by MindLink Software Contents Introduction 3 Barriers To Decision Making 3 Removing Barriers By Leveraging Real-Time Messaging 4 Making Information Accessible 5 • Pull • Push • Command Unleashing The Developer In Everyone 6 Worked Example – Integration With A 7 Marketing Automation Tool Mitigating Risk While Enabling Fluid Integration 10 What Is Mindlink™ 11 Mindlink Suite 11 Introduction Making decisions is hard. Making the right decisions without all the right information is harder. To make effective choices you need everything that matters in front of you, or at the very least you have to remember everything in context. Today’s businesses can’t settle for scattered sources from disparate systems that require manual searching, analysing and collating when it can all be delivered to their feet when they need it. Barriers To Decision Making Businesses evolve rapidly. New systems are designed, redesigned and implemented, replaced and updated regularly. Different departments have different requirements and this usually leads to various information systems spread throughout the organisation. When it comes to making decisions, multiple departments are normally involved, bringing with them information from their own systems. As a decision maker, how can you efficiently and effectively get exactly what you need to make the right choice? The standard procedure may be to ask each departmental stakeholder to send to you the information that they deem relevant. Getting everybody into a room or a conference is hard enough without having to worry about missing information. Ultimately it leads to a string of meetings with various different bits of information that make little progress as data is missing, forgotten, misplaced or misrepresented. -

VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center
VIRTUAL ENGAGEMENT BEST PRACTICES Student Leadership & Involvement | 211 University Center Table of Contents Click on any of the titles below to be navigated to that section SLI POLICIES ........................................................................................................................... 1 USING TIGERZONE TO YOUR ADVANTAGE .............................................................................. 1 ONLINE MEETING PLATFORMS ............................................................................................... 2 ONLINE BROADCASTING PLATFORMS ..................................................................................... 3 ONLINE CHAT PLATFORMS ..................................................................................................... 3 VIDEO CONFERENCE TIPS (for Zoom) ...................................................................................... 4 VIRTUAL ENGAGEMENT IDEAS ............................................................................................... 5 VIRTUAL ENTERTAINMENT ..................................................................................................... 6 SLI POLICIES During Phase 1 there are to be NO IN PERSON STUDENT EVENTS. This applies to events both ON and OFF campus. If your organization is found to be hosting in person events you will be given ONE warning from Student Leadership & Involvement. If your organization is found to be hosting student events a second time your organization will be suspended for the remainder of the 2020-2021 -

Microsoft Skype for Business Deployment Guide
Microsoft Skype for Business Deployment Guide Multimedia Connector for Skype for Business 8.5.0 3/8/2020 Table of Contents Multimedia Connector for Skype for Business Deployment Guide 4 Architecture 6 Paired Front End Pools 9 Federation Platform with Microsoft Office 365 Cloud 12 Managing T-Server and UCMA Connectors 14 Prerequisites 16 Provisioning for UCMA Connectors 22 Using Telephony Objects 24 Managing UCMA Connectors 28 Managing T-Server 33 Upgrading Multimedia Connector for Skype For Business 36 Configuring Skype for Business Application Endpoints 37 Configuring Skype for Business User Endpoints 38 High-Availability Deployment 39 Performance 45 Managing Workspace Plugin for Skype for Business 46 Using Workspace Plugin for Skype for Business 51 Handling IM Transcripts 60 Supported Features 61 Alternate Routing 62 Call Monitoring 63 Call Supervision 64 Calling using Back-to-Back User Agent 70 Conference Resource Pools 77 Disable Lobby Bypass 80 Emulated Agents 82 Emulated Ringing 85 Handling Direct Calls 86 Handling Pass-Through Calls 89 Hiding Sensitive Data 91 IM Treatments 93 IM Suppression 94 Music On Hold 97 No-Answer Supervision 98 Presence 99 Remote Recording 103 Remote Treatments 110 Transport Layer Security 112 UTF-8 Encoding 114 Supported Media Types 116 T-Library Functionality 120 Attribute Extensions 124 Hardware Sizing Guidelines and Capacity Planning 130 Error Messages 132 Known Limitations and Workarounds 134 Multimedia Connector for Skype for Business Deployment Guide Multimedia Connector for Skype for Business Deployment Guide Welcome to the Multimedia Connector for Skype for Business Deployment Guide. This Deployment Guide provides deployment procedures and detailed reference information about the Multimedia Connector for Skype for Business as a product, and its components: T-Server, UCMA Connector, and Workspace Plugin. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

CCIA Comments in ITU CWG-Internet OTT Open Consultation.Pdf
CCIA Response to the Open Consultation of the ITU Council Working Group on International Internet-related Public Policy Issues (CWG-Internet) on the “Public Policy considerations for OTTs” Summary. The Computer & Communications Industry Association welcomes this opportunity to present the views of the tech sector to the ITU’s Open Consultation of the CWG-Internet on the “Public Policy considerations for OTTs”.1 CCIA acknowledges the ITU’s expertise in the areas of international, technical standards development and spectrum coordination and its ambition to help improve access to ICTs to underserved communities worldwide. We remain supporters of the ITU’s important work within its current mandate and remit; however, we strongly oppose expanding the ITU’s work program to include Internet and content-related issues and Internet-enabled applications that are well beyond its mandate and core competencies. Furthermore, such an expansion would regrettably divert the ITU’s resources away from its globally-recognized core competencies. The Internet is an unparalleled engine of economic growth enabling commerce, social development and freedom of expression. Recent research notes the vast economic and societal benefits from Rich Interaction Applications (RIAs), a term that refers to applications that facilitate “rich interaction” such as photo/video sharing, money transferring, in-app gaming, location sharing, translation, and chat among individuals, groups and enterprises.2 Global GDP has increased US$5.6 trillion for every ten percent increase in the usage of RIAs across 164 countries over 16 years (2000 to 2015).3 However, these economic and societal benefits are at risk if RIAs are subjected to sweeping regulations. -

IM Security Documentation on Page Vi
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release notes, and/or the latest version of the applicable documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/trend-micro-im-security.aspx Trend Micro, the Trend Micro t-ball logo, Control Manager, MacroTrap, and TrendLabs are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2016. Trend Micro Incorporated. All rights reserved. Document Part No.: TIEM16347/140311 Release Date: September 2016 Protected by U.S. Patent No.: Pending This documentation introduces the main features of the product and/or provides installation instructions for a production environment. Read through the documentation before installing or using the product. Detailed information about how to use specific features within the product may be available at the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Privacy and Personal Data Collection Disclosure Certain features available in Trend Micro products collect and send feedback regarding product usage and detection information to Trend Micro. Some of this data is considered personal in certain jurisdictions and under certain regulations. -

Microsoft Office
Microsoft Office MICROSOFT OFFICE INTRODUCTION Microsoft Office is an office suite of desktop applications, servers and services for the Microsoft Windows and OS X operating systems. It was first announced by Bill Gates of Microsoft on August 1, 1988 at COMDEX in Las Vegas. Initially a marketing term for a bundled set of applications, the first version of Office contained Microsoft Word, Microsoft Excel and Microsoft PowerPoint. Over the years, Office applications have grown substantially closer with shared features such as a common spell checker, OLEdata integration and Visual Basic for Applications scripting language. Microsoft also positions Office as a development platform for line-of-business software under the Office Business Applications brand. On 10 July 2012, Softpedia reported that Office is used by over a billion people worldwide. The current versions are Office 2013 for Windows, released on October 11, 2012; and Office 2011 for OS X, released October 26, 2010 On 24 October 2012, the RTM final code of Office 2013 Professional Plus was released to TechNet and MSDN subscribers for download. On 15 November 2012, the 60-day trial version of Office 2013 Professional Plus was released for download. All devices running Windows Phone and Windows RT come pre-installed with Office Mobile and Office RT, respectively. Office Mobile is also available for Android phones and the iPhone. A version of Office for the iPad was launched in March 2014. A web-based version of Office called Office Online, is also available COMPONENTS Word Microsoft Word is a word processor and was previously considered the main program in Office. -

LAN Messenger
SVERIAN Scientific LAN Messenger Pooja Purohit, Sakhare Shital, Kothari Rasika and Jadhav Dipali Department of Computer Engineering, SVERI’s College of Engineering (Poly.), Pandharpur Student Article Abstract: This is LAN messenger application; it’s a social media project for Final year college students. It is a Client – server application program developed in Visual Studio 2005 (VB .NET). Here the individual can chat with other individual through LAN connection. Even they can exchange file through one computer to other. Administrator can view chat logs through server. Here no need of Internet access. This application can be used in all workplace which is helpful in submitting information and to connect with workplace staff. Introduction: A LAN messenger is an instant messaging program designed for use within a single local area network (LAN). Many LAN messengers offer basic functionality for sending private messages, file transfer , chat rooms and graphical smileys . The advantage of using a simple LAN messenger over a normal instant messenger is that no active Internet connection or central server is required - and only people inside the firewall will have access to the system. LAN messenger is an easy to use, server based LAN messaging application for effective communication. It is correctly identified and works under all operating systems with unlimited user accounts and is the only secure messenger. The simple interface makes special training needless . Literature Review: The LM uses two-tier client server architecture as shown in figure 1. The application handling is completed separately for database queries and updates and for business logic processing and user interface presentation. -

Acceptable Use of Instant Messaging Issued by the CTO
State of West Virginia Office of Technology Policy: Acceptable Use of Instant Messaging Issued by the CTO Policy No: WVOT-PO1010 Issued: 11/24/2009 Revised: 12/22/2020 Page 1 of 4 1.0 PURPOSE This policy details the use of State-approved instant messaging (IM) systems and is intended to: • Describe the limitations of the use of this technology; • Discuss protection of State information; • Describe privacy considerations when using the IM system; and • Outline the applicable rules applied when using the State-provided system. This document is not all-inclusive and the WVOT has the authority and discretion to appropriately address any unacceptable behavior and/or practice not specifically mentioned herein. 2.0 SCOPE This policy applies to all employees within the Executive Branch using the State-approved IM systems, unless classified as “exempt” in West Virginia Code Section 5A-6-8, “Exemptions.” The State’s users are expected to be familiar with and to comply with this policy, and are also required to use their common sense and exercise their good judgment while using Instant Messaging services. 3.0 POLICY 3.1 State-provided IM is appropriate for informal business use only. Examples of this include, but may not be limited to the following: 3.1.1 When “real time” questions, interactions, and clarification are needed; 3.1.2 For immediate response; 3.1.3 For brainstorming sessions among groups; 3.1.4 To reduce chances of misunderstanding; 3.1.5 To reduce the need for telephone and “email tag.” 3.2 Employees must only use State-approved instant messaging. -
Licensing Windows and Microsoft Office for Use on the Macintosh
Volume Licensing brief Licensing Windows and Microsoft Office for use on the Macintosh This brief applies to all Volume Licensing programs. Contents Summary .............................................................................................................................................................................. 1 What’s new in this brief .................................................................................................................................................... 1 Details .................................................................................................................................................................................... 1 Licensing of the Windows operating system for the Mac ................................................................................ 1 Scenarios ....................................................................................................................................................................... 2 Licensing of Microsoft Office for Windows and Microsoft Office for Mac .................................................. 6 Frequently asked questions ............................................................................................................................................ 7 Summary This licensing brief addresses the commonly asked questions about licensing the Windows operating system and Microsoft Office to run on the Macintosh. What’s new in this brief This replaces a previous version published in August 2015. It has