(In-)Security of 64-Bit Block Ciphers Karthikeyan Bhargavan, Gaëtan Leurent
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

File Systems and Disk Layout I/O: the Big Picture
File Systems and Disk Layout I/O: The Big Picture Processor interrupts Cache Memory Bus I/O Bridge Main I/O Bus Memory Disk Graphics Network Controller Controller Interface Disk Disk Graphics Network 1 Rotational Media Track Sector Arm Cylinder Platter Head Access time = seek time + rotational delay + transfer time seek time = 5-15 milliseconds to move the disk arm and settle on a cylinder rotational delay = 8 milliseconds for full rotation at 7200 RPM: average delay = 4 ms transfer time = 1 millisecond for an 8KB block at 8 MB/s Bandwidth utilization is less than 50% for any noncontiguous access at a block grain. Disks and Drivers Disk hardware and driver software provide basic facilities for nonvolatile secondary storage (block devices). 1. OS views the block devices as a collection of volumes. A logical volume may be a partition ofasinglediskora concatenation of multiple physical disks (e.g., RAID). 2. OS accesses each volume as an array of fixed-size sectors. Identify sector (or block) by unique (volumeID, sector ID). Read/write operations DMA data to/from physical memory. 3. Device interrupts OS on I/O completion. ISR wakes up process, updates internal records, etc. 2 Using Disk Storage Typical operating systems use disks in three different ways: 1. System calls allow user programs to access a “raw” disk. Unix: special device file identifies volume directly. Any process that can open thedevicefilecanreadorwriteany specific sector in the disk volume. 2. OS uses disk as backing storage for virtual memory. OS manages volume transparently as an “overflow area” for VM contents that do not “fit” in physical memory. -

Report on the AES Candidates
Rep ort on the AES Candidates 1 2 1 3 Olivier Baudron , Henri Gilb ert , Louis Granb oulan , Helena Handschuh , 4 1 5 1 Antoine Joux , Phong Nguyen ,Fabrice Noilhan ,David Pointcheval , 1 1 1 1 Thomas Pornin , Guillaume Poupard , Jacques Stern , and Serge Vaudenay 1 Ecole Normale Sup erieure { CNRS 2 France Telecom 3 Gemplus { ENST 4 SCSSI 5 Universit e d'Orsay { LRI Contact e-mail: [email protected] Abstract This do cument rep orts the activities of the AES working group organized at the Ecole Normale Sup erieure. Several candidates are evaluated. In particular we outline some weaknesses in the designs of some candidates. We mainly discuss selection criteria b etween the can- didates, and make case-by-case comments. We nally recommend the selection of Mars, RC6, Serp ent, ... and DFC. As the rep ort is b eing nalized, we also added some new preliminary cryptanalysis on RC6 and Crypton in the App endix which are not considered in the main b o dy of the rep ort. Designing the encryption standard of the rst twentyyears of the twenty rst century is a challenging task: we need to predict p ossible future technologies, and wehavetotake unknown future attacks in account. Following the AES pro cess initiated by NIST, we organized an op en working group at the Ecole Normale Sup erieure. This group met two hours a week to review the AES candidates. The present do cument rep orts its results. Another task of this group was to up date the DFC candidate submitted by CNRS [16, 17] and to answer questions which had b een omitted in previous 1 rep orts on DFC. -

Semiconductor Memories
Semiconductor Memories Prof. MacDonald Types of Memories! l" Volatile Memories –" require power supply to retain information –" dynamic memories l" use charge to store information and require refreshing –" static memories l" use feedback (latch) to store information – no refresh required l" Non-Volatile Memories –" ROM (Mask) –" EEPROM –" FLASH – NAND or NOR –" MRAM Memory Hierarchy! 100pS RF 100’s of bytes L1 1nS SRAM 10’s of Kbytes 10nS L2 100’s of Kbytes SRAM L3 100’s of 100nS DRAM Mbytes 1us Disks / Flash Gbytes Memory Hierarchy! l" Large memories are slow l" Fast memories are small l" Memory hierarchy gives us illusion of large memory space with speed of small memory. –" temporal locality –" spatial locality Register Files ! l" Fastest and most robust memory array l" Largest bit cell size l" Basically an array of large latches l" No sense amps – bits provide full rail data out l" Often multi-ported (i.e. 8 read ports, 2 write ports) l" Often used with ALUs in the CPU as source/destination l" Typically less than 10,000 bits –" 32 32-bit fixed point registers –" 32 60-bit floating point registers SRAM! l" Same process as logic so often combined on one die l" Smaller bit cell than register file – more dense but slower l" Uses sense amp to detect small bit cell output l" Fastest for reads and writes after register file l" Large per bit area costs –" six transistors (single port), eight transistors (dual port) l" L1 and L2 Cache on CPU is always SRAM l" On-chip Buffers – (Ethernet buffer, LCD buffer) l" Typical sizes 16k by 32 Static Memory -

EEPROM Emulation
...the world's most energy friendly microcontrollers EEPROM Emulation AN0019 - Application Note Introduction This application note demonstrates a way to use the flash memory of the EFM32 to emulate single variable rewritable EEPROM memory through software. The example API provided enables reading and writing of single variables to non-volatile flash memory. The erase-rewrite algorithm distributes page erases and thereby doing wear leveling. This application note includes: • This PDF document • Source files (zip) • Example C-code • Multiple IDE projects 2013-09-16 - an0019_Rev1.09 1 www.silabs.com ...the world's most energy friendly microcontrollers 1 General Theory 1.1 EEPROM and Flash Based Memory EEPROM stands for Electrically Erasable Programmable Read-Only Memory and is a type of non- volatile memory that is byte erasable and therefore often used to store small amounts of data that must be saved when power is removed. The EFM32 microcontrollers do not include an embedded EEPROM module for byte erasable non-volatile storage, but all EFM32s do provide flash memory for non-volatile data storage. The main difference between flash memory and EEPROM is the erasable unit size. Flash memory is block-erasable which means that bytes cannot be erased individually, instead a block consisting of several bytes need to be erased at the same time. Through software however, it is possible to emulate individually erasable rewritable byte memory using block-erasable flash memory. To provide EEPROM functionality for the EFM32s in an application, there are at least two options available. The first one is to include an external EEPROM module when designing the hardware layout of the application. -

A Hybrid Swapping Scheme Based on Per-Process Reclaim for Performance Improvement of Android Smartphones (August 2018)
Received August 19, 2018, accepted September 14, 2018, date of publication October 1, 2018, date of current version October 25, 2018. Digital Object Identifier 10.1109/ACCESS.2018.2872794 A Hybrid Swapping Scheme Based On Per-Process Reclaim for Performance Improvement of Android Smartphones (August 2018) JUNYEONG HAN 1, SUNGEUN KIM1, SUNGYOUNG LEE1, JAEHWAN LEE2, AND SUNG JO KIM2 1LG Electronics, Seoul 07336, South Korea 2School of Software, Chung-Ang University, Seoul 06974, South Korea Corresponding author: Sung Jo Kim ([email protected]) This work was supported in part by the Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education under Grant 2016R1D1A1B03931004 and in part by the Chung-Ang University Research Scholarship Grants in 2015. ABSTRACT As a way to increase the actual main memory capacity of Android smartphones, most of them make use of zRAM swapping, but it has limitation in increasing its capacity since it utilizes main memory. Unfortunately, they cannot use secondary storage as a swap space due to the long response time and wear-out problem. In this paper, we propose a hybrid swapping scheme based on per-process reclaim that supports both secondary-storage swapping and zRAM swapping. It attempts to swap out all the pages in the working set of a process to a zRAM swap space rather than killing the process selected by a low-memory killer, and to swap out the least recently used pages into a secondary storage swap space. The main reason being is that frequently swap- in/out pages use the zRAM swap space while less frequently swap-in/out pages use the secondary storage swap space, in order to reduce the page operation cost. -

AN-1471 Application Note
AN-1471 APPLICATION NOTE One Technology Way • P. O. Box 9106 • Norwood, MA 02062-9106, U.S.A. • Tel: 781.329.4700 • Fax: 781.461.3113 • www.analog.com ADuCM4050 Flash EEPROM Emulation by Pranit Jadhav and Rafael Lajara INTRODUCTION provides assurance that the flash initialization function works as Nonvolatile data storage is a necessity in many embedded expected. An ECC check is enabled for the entire user space in systems. Data, such as boot up configuration, calibration constants, the flash memory of the ADuCM4050. If ECC errors are reported and network related information, is normally stored on an during any read operation, the ECC engine automatically corrects electronically erasable programmable read only memory 1-bit errors and only reports on detection of 2-bit errors. When a (EEPROM) device. The advantage of using the EEPROM to store read occurs on the flash, appropriate flags are set in the status this data is that a single byte on an EEPROM device can be register of the ADuCM4050. If interrupts are generated, the source rewritten or updated without affecting the contents in the other address of the ECC error causing an interrupt is available in the locations. FLCC0_ECC_ADDR register for the interrupt service routine (ISR) to read. The ADuCM4050 is an ultra low power microcontroller unit (MCU) with integrated flash memory. The ADuCM4050 includes Emulation of the EEPROM on the integrated flash memory 512 kB of embedded flash memory with a 72-bit wide data bus reduces the bill of material (BOM) cost by omitting the EEPROM that provides two 32-bits words of data and one corresponding in the design. -

File System Layout
File Systems Main Points • File layout • Directory layout • Reliability/durability Named Data in a File System index !le name directory !le number structure storage o"set o"set block Last Time: File System Design Constraints • For small files: – Small blocks for storage efficiency – Files used together should be stored together • For large files: – ConCguous allocaon for sequenCal access – Efficient lookup for random access • May not know at file creaon – Whether file will become small or large File System Design Opons FAT FFS NTFS Index Linked list Tree Tree structure (fixed, asym) (dynamic) granularity block block extent free space FAT array Bitmap Bitmap allocaon (fixed (file) locaon) Locality defragmentaon Block groups Extents + reserve Best fit space defrag MicrosoS File Allocaon Table (FAT) • Linked list index structure – Simple, easy to implement – SCll widely used (e.g., thumb drives) • File table: – Linear map of all blocks on disk – Each file a linked list of blocks FAT MFT Data Blocks 0 1 2 3 !le 9 block 3 4 5 6 7 8 9 !le 9 block 0 10 !le 9 block 1 11 !le 9 block 2 12 !le 12 block 0 13 14 15 16 !le 12 block 1 17 18 !le 9 block 4 19 20 FAT • Pros: – Easy to find free block – Easy to append to a file – Easy to delete a file • Cons: – Small file access is slow – Random access is very slow – Fragmentaon • File blocks for a given file may be scaered • Files in the same directory may be scaered • Problem becomes worse as disk fills Berkeley UNIX FFS (Fast File System) • inode table – Analogous to FAT table • inode – Metadata • File owner, access permissions, -

Miss in the Middle Attacks on IDEA and Khufu
Miss in the Middle Attacks on IDEA and Khufu Eli Biham? Alex Biryukov?? Adi Shamir??? Abstract. In a recent paper we developed a new cryptanalytic techni- que based on impossible differentials, and used it to attack the Skipjack encryption algorithm reduced from 32 to 31 rounds. In this paper we describe the application of this technique to the block ciphers IDEA and Khufu. In both cases the new attacks cover more rounds than the best currently known attacks. This demonstrates the power of the new cryptanalytic technique, shows that it is applicable to a larger class of cryptosystems, and develops new technical tools for applying it in new situations. 1 Introduction In [5,17] a new cryptanalytic technique based on impossible differentials was proposed, and its application to Skipjack [28] and DEAL [17] was described. In this paper we apply this technique to the IDEA and Khufu cryptosystems. Our new attacks are much more efficient and cover more rounds than the best previously known attacks on these ciphers. The main idea behind these new attacks is a bit counter-intuitive. Unlike tra- ditional differential and linear cryptanalysis which predict and detect statistical events of highest possible probability, our new approach is to search for events that never happen. Such impossible events are then used to distinguish the ci- pher from a random permutation, or to perform key elimination (a candidate key is obviously wrong if it leads to an impossible event). The fact that impossible events can be useful in cryptanalysis is an old idea (for example, some of the attacks on Enigma were based on the observation that letters can not be encrypted to themselves). -

ZFS On-Disk Specification Draft
ZFS On-Disk Specification Draft Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A 1 ©2006 Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. Sun, Sun Microsystems, the Sun logo, Java, JavaServer Pages, Solaris, and StorEdge are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. U.S. Government Rights Commercial software. Government users are subject to the Sun Microsystems, Inc. standard license agreement and applicable provisions of the FAR and its supplements. DOCUMENTATION IS PROVIDED AS IS AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. Unless otherwise licensed, use of this software is authorized pursuant to the terms of the license found at: http://developers.sun.com/berkeley_license.html Ce produit ou document est protégé par un copyright et distribué avec des licences qui en restreignent l'utilisation, la copie, la distribution, et la décompilation. Aucune partie de ce produit ou document ne peut être reproduite sous aucune forme, par quelque moyen que ce soit, sans l'autorisation préalable et écrite de Sun et de ses bailleurs de licence, s'il y en a. -

Comparative Analysis of Advanced Encryption Standard, Blowfish and Rivest Cipher 4 Algorithms
www.ijird.com November, 2014 Vol 3 Issue 11 ISSN 2278 – 0211 (Online) Comparative Analysis of Advanced Encryption Standard, Blowfish and Rivest Cipher 4 Algorithms Adolf Fenyi Researcher, Kwame Nkrumah University of Science and Technology, Knust, Ghana Joseph G. Davis Lecturer, Kwame Nkrumah University of Science and Technology, Knust, Ghana Dr. Kwabena Riverson Head of Programme CSIR Institute of Industrial Research Accra, Ghana Abstract: Cryptography is one of the main categories of computer security that converts information from its normal form into an unreadable form. The two main characteristics that identify and differentiate one encryption algorithm from another are its ability to secure the protected data against attacks and its speed and efficiency in doing so.Cryptography is required to transmit confidential information over the network. It is also demanding in wide range of applications which includes mobile and networking applications. Cryptographic algorithms play a vital role in providing the data security against malicious attacks. But on the other hand, they consume significant amount of computing resources like CPU time, memory, encryption time etc. Normally, symmetric key algorithms are preferred over asymmetric key algorithms as they are very fast in nature. Symmetric algorithms are classified as block cipher and stream ciphers algorithms. In this research project, I comparedthe AES and Blowfish algorithms with different modes of operation (ECB, CBC, and CFB) and RC4 algorithm (stream cipher) in terms encryption time, decryption time, memory utilization and throughput at different settings likevariable key size and variable data packet size.A stimulation program is developed using PHP and JavaScript scripting languages. The program encrypts and decrypts different file sizes ranging from 1MB to 50MB. -
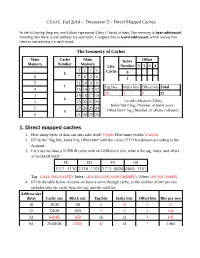
1. Direct Mapped Caches 1
CS 61C SpringFall 2014 2014 – Discussion 5 – Direct Mapped Caches In the following diagram, each block represents 8 bits (1 byte) of data. Our memory is byte-addressed, meaning that there is one address for each byte. Compare this to word-addressed, which means that there is one address for each word. The Geometry of Caches Main Cache Main Index Offset Memory Number Memory CPU Number 3 2 1 0 ... 3 2 1 0 Cache 0 0 6 7 6 5 4 1 5 11 10 9 8 1 Tag bits Index bits Offset bits Total 4 15 14 13 12 29 1 2 32 3 19 18 17 16 2 2 23 22 21 20 1word=4 bytes=32bits Index bits=log (Number of index rows) 1 27 26 25 24 2 3 Offset bits=log2(Number of offsets columns) 0 31 30 29 28 1. Direct mapped caches 1. How many bytes of data can our cache hold? 8 bytes How many words? 2 words 2. Fill in the “Tag bits, Index bits, Offset bits” with the correct T:I:O breakdown according to the diagram. 3. Let’s say we have a 8192KiB cache with an 128B block siZe, what is the tag, index, and offset of 0xFEEDF00D? FE ED F0 0D 1111 1110 1110 1101 1111 0000 0000 1101 Tag: 1 1111 1101 (0x1FD) Index: 1101 1011 1110 0000 (0xDBE0) Offset: 000 1101 (0x0D) 4. Fill in the table below. Assume we have a write-through cache, so the number of bits per row includes only the cache data, the tag, and the valid bit. -

AES, Blowfish and Twofish for Security of Wireless Networks
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 07 Issue: 06 | June 2020 www.irjet.net p-ISSN: 2395-0072 Comparison of Encryption Algorithms: AES, Blowfish and Twofish for Security of Wireless Networks Archisman Ghosh Department of Computer Science & Engineering, National Institute of Technology, Durgapur, West Bengal, India --------------------------------------------------------------------------***--------------------------------------------------------------------- Abstract - Encryption is the process of encoding data to A secure WiFi system uses algorithms such as DES, RSA, prevent unauthorized access. Cyber security is the need of AES, Blowfish and Twofish to secure the communication the hour which ensures transfer of data across the internet over seemingly unsecured Internet channels. In addition, with confidentiality and integrity, and provides protection the existing cryptographic algorithm is based on an against malicious attacks. In this research paper, encryption model designed by Horst Feistel of IBM [4]. comparison between the encryption algorithms, viz. AES (Advanced Encryption Standard), Blowfish, and Twofish is In this paper, a comparative study of the cryptographic done in terms of time of encryption and decryption, and algorithms: AES, Blowfish and Twofish has been done and their throughput, and the results are analysed indicating the the results have been analysed in order to find the superiority of Twofish over AES and Blowfish as a viable algorithm most suitable for encrypting data in wireless algorithm for data encryption in wireless networks. networks. Keywords: Cryptography, Network security, AES, 2. Overview of the algorithms Blowfish, Twofish, Secure communication. 2.1 AES 1. Introduction The Advanced Encryption Standard (AES) is a Owing to the advancement in internet accessibility and cryptographic algorithm for encryption of electronic data networking, most of the security sensitive stuff like established by the U.S.