Smartphone and Smartwatch for Human Activity Recognition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Texting on a Smartwatch Versus a Smartphone: a Comparison of Their Effects on Driving Performance
TEXTING ON A SMARTWATCH VERSUS A SMARTPHONE: A COMPARISON OF THEIR EFFECTS ON DRIVING PERFORMANCE A Dissertation by Joel Persinger Master of Arts, Wichita State University, 2014 Bachelor of Science, Eastern Kentucky University, 2005 Submitted to the Department of Psychology and the faculty of the Graduate School of Wichita State University in partial fulfillment of the requirements for the degree of Doctor of Philosophy December 2017 ©Copyright 2017 by Joel A. Persinger All Rights Reserved TEXTING ON A SMARTWATCH VERSUS A SMARTPHONE: A COMPARISON OF THEIR EFFECTS ON DRIVING PERFORMANCE The following faculty members have examined the final copy of this dissertation for form and content, and recommend that it be accepted in partial fulfillment of the requirement for the degree of Doctor of Philosophy, with a major in Psychology. _____________________________________________ Rui Ni, Committee Chair _____________________________________________ Alex Chaparro, Committee Member _____________________________________________ Barbara Chaparro, Committee Member _____________________________________________ Jibo He, Committee Member _____________________________________________ Jeremy Patterson, Committee Member Accepted for the College of Liberal Arts and Sciences _______________________________________________ Ron Matson, Dean Accepted for the Graduate School _______________________________________________ Dennis Livesay, Dean iii DEDICATION To my beautiful wife, who has pushed me to go further than I ever thought I could. She has truly carried me though graduate school with love and encouragement. iv ABSTRACT The National Safety Council reports that 6 percent or more car crashes involved text messaging from a smartphone. In addition, many studies have found that cell phone while driving increases crash risk by 2.8–5 times (Klauer et al. 2006; Redelmeier and Tibshirani 1997; Violanti 1998; Violanti and Marshall 1996). -

Ten Steps to Smartphone Security
Ten Steps to Smartphone Security Smartphones continue to grow in popularity and are now as powerful and functional as many computers. It is important to protect your smartphone just like you protect your computer as mobile cybersecurity threats are growing. These mobile security tips can help you reduce the risk of exposure to mobile security threats: 1. Set PINs and passwords. To prevent unauthorized access to your phone, set a password or Personal Identification Number (PIN) on your phone’s home screen as a first line of defense in case your phone is lost or stolen. When possible, use a different password for each of your important log-ins (email, banking, personal sites, etc.). You should configure your phone to automatically lock after five minutes or less when your phone is idle, as well as use the SIM password capability available on most smartphones. 2. Do not modify your smartphone’s security settings. Do not alter security settings for convenience. Tampering with your phone’s factory settings, jailbreaking, or rooting your phone undermines the built-in security features offered by your wireless service and smartphone, while making it more susceptible to an attack. 3. Backup and secure your data. You should backup all of the data stored on your phone – such as your contacts, documents, and photos. These files can be stored on your computer, on a removal storage card, or in the cloud. This will allow you to conveniently restore the information to your phone should it be lost, stolen, or otherwise erased. 4. Only install apps from trusted sources. -

SMS “Virtual Collection Center” Smartphone
Feed the Future Innovation Lab for Livestock Systems INNOVATION SUMMARY: SMS “VIRTUAL COLLECTION CENTER” SMARTPHONE APP The Virtual Collection Center (VCC) is an innovative short message service (SMS) mobile application (app) for improved goat marketing. Through the use of the VCC app, inventory updates flow from cooperative members to leaders, while cooperative leaders use the VCC app to share price information with members and fill orders from traders by inviting members to sales events. The VCC app improves the goat value chain by reducing transaction costs, which should strengthen cooperatives and benefit small livestock producers by increasing trade volumes. Lead Implementing Institution: University of Florida Category: Marketing & Distribution Applied in: Nepal The VCC app is implemented by Heifer International Nepal whose Innovation Type: Technology New/Adapted: New field personnel assist cooperative members in downloading the app while providing training and Created for: Mainly Women Nutrition Linkage: Dietary Quality monitoring in the initial stages. The app is designed to be intuitive, eliminating the need for intensive training. Within cooperatives, the In Nepal, goats are an essential source of income and nearly every rural Nepali household app is accessed by “VCC owns at least a few goats. To buy goats, traders often travel over large areas characterized managers”, who are members of cooperative self-help groups by rugged terrain and poor infrastructure, making multiple visits to individual households necessary to complete sales. The resulting high transaction costs can stifle the value chain. (subgroups within the Cooperatives can reduce transaction costs by allowing for bulk purchases of animals. But cooperatives), and cooperative cooperatives may struggle to coordinate sales by members spread out over large areas of leaders. -

The Classic Blackberry – Supercharged
COMING SOON! The classic BlackBerry – supercharged. BlackBerry® Curve™ 3G smartphone The new BlackBerry Curve 3G smartphone from AT&T is BlackBerry Curve 3G powerful yet affordable. This BlackBerry classic now gives smartphone you 3G speed and everything you expect from the popular The first 3G Curve BlackBerry Curve family, with a QWERTY keyboard, work and from AT&T. personal email, powerful personal management capabilities and much more. A superior connection. • Be at the forefront. With simultaneous voice and data when using the 3G or Wi-Fi network, you can check the facts on email or the web while talking on the phone with clients or colleagues. • Work with speed and confidence. The BlackBerry Curve 3G • Speed with flexibility. The BlackBerry Curve 3G smartphone has a powerful 624 MHz processor, 256 MB flash smartphone allows you to quickly download and upload memory/256 MB SDRAM and an included 2 GB microSD™ card content and surf the web faster on the nation’s fastest for storage, expandable up to 32 GB. broadband mobile network.* And with built-in Wi-Fi® • Focused applications. Keep up-to-date and informed of your (802.11 b/g/n), access the information and download the work and life – explore BlackBerry® App World™ and pre-loaded large files you need at Wi-Fi speeds. applications including LinkedIn™, My-Cast® Weather, Bloomberg® • Automatically unlimited. The new BlackBerry Curve 3G Mobile, AllSport GPS™, WHERE®, City ID®, Facebook®, MySpace™, smartphone automatically connects to AT&T Wi-Fi Hot Twitter™ and more. Spots in the U.S.** for unlimited usage on the AT&T Wi-Fi • Capture the moment. -
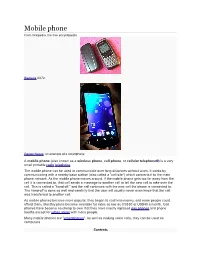
Mobile Phone from Wikipedia, the Free Encyclopedia
Mobile phone From Wikipedia, the free encyclopedia Siemens AX72. Galaxy Nexus, an example of a smartphone A mobile phone (also known as a wireless phone, cell phone, or cellular telephone[1]) is a very small portable radio telephone. The mobile phone can be used to communicate over long distances without wires. It works by communicating with a nearby base station (also called a "cell site") which connects it to the main phone network. As the mobile phone moves around, if the mobile phone gets too far away from the cell it is connected to, that cell sends a message to another cell to tell the new cell to take over the call. This is called a "hand off," and the call continues with the new cell the phone is connected to. The hand-off is done so well and carefully that the user will usually never even know that the call was transferred to another cell. As mobile phones became more popular, they began to cost less money, and more people could afford them. Monthly plans became available for rates as low as US$30 or US$40 a month. Cell phones have become so cheap to own that they have mostly replaced pay phones and phone booths except for urban areas with many people. Many mobile phones are "smartphones". As well as making voice calls, they can be used as computers. Contents [hide] 1 History 2 Technology 3 Shapes 4 How mobile phones work 5 Networks and payment 6 Smartphones 7 References History[change | change source] Mobile phones in the 1950s through 1970s were large and heavy, and most were built into cars. -

A Comparative Analysis of Mobile Operating Systems Rina
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-6, Issue-12, Dec 2018 E-ISSN: 2347-2693 A Comparative Analysis of mobile Operating Systems Rina Dept of IT, GGDSD College, Chandigarh ,India *Corresponding Author: [email protected] Available online at: www.ijcseonline.org Accepted: 09/Dec/2018, Published: 31/Dec/2018 Abstract: The paper is based on the review of several research studies carried out on different mobile operating systems. A mobile operating system (or mobile OS) is an operating system for phones, tablets, smart watches, or other mobile devices which acts as an interface between users and mobiles. The use of mobile devices in our life is ever increasing. Nowadays everyone is using mobile phones from a lay man to businessmen to fulfill their basic requirements of life. We cannot even imagine our life without mobile phones. Therefore, it becomes very difficult for the mobile industries to provide best features and easy to use interface to its customer. Due to rapid advancement of the technology, the mobile industry is also continuously growing. The paper attempts to give a comparative study of operating systems used in mobile phones on the basis of their features, user interface and many more factors. Keywords: Mobile Operating system, iOS, Android, Smartphone, Windows. I. INTRUDUCTION concludes research work with future use of mobile technology. Mobile operating system is the interface between user and mobile phones to communicate and it provides many more II. HISTORY features which is essential to run mobile devices. It manages all the resources to be used in an efficient way and provides The term smart phone was first described by the company a user friendly interface to the users. -

Maxphone—Multi-Access Extension for Smartphones Fact Sheet
Completed DHS Science and Technology Directorate MaXphone—Multi-Access Extension for Smartphones Providing devices that embrace Land Mobile P25, cellular/Public Switched Telephone Network voice, Radio (LMR) and broadband cellular networks and Voice-over-IP. It also allows for enhanced security by The First Responder Network Authority (FirstNet) is providing end-to-end P25 encryption across LMR and charged with creating a nationwide public safety broadband broadband networks. network that provides the public safety community with a Enabling customizable, affordable applications boost in network capacity and capability. Still, commercial MaXphone leverages rapid development in commercial cellular broadband networks (e.g., 4G LTE and 3G) will broadband networks and smartphone capability. Open likely remain the dominant option to support first responder application development environments (e.g., Android) broadband applications for the immediate future. enable novel, innovative, customizable and affordable first Broadband networks do not provide first responders with responder applications. An open source, fully functioning mission critical voice capabilities (i.e., radio-to-radio or P25 software package will be available on the Android one-to-many communications) that are available on LMR environment. MaxJacket will be based on COTS networks. However, application and service development in components and contain the necessary functions for the P25 the LMR domain stand in stark contrast to the explosive solution. growth in the commercial broadband sector. Therefore, a reasonable, cost effective approach to creating more capable first responder devices embraces existing LMR networks Legacy P25 handset and commercial broadband cellular networks by using open P25 platforms to encourage application development. IP25 P25 Network Gateway Access The Department of Homeland Security Science and Technology Directorate and U.S. -

Securing and Managing Wearables in the Enterprise
White Paper: Securing and Managing Wearables in the Enterprise Streamline deployment and protect smartwatch data with Samsung Knox Configure White Paper: Securing and Managing Wearables in the Enterprise 2 Introduction: Smartwatches in the Enterprise As the wearable device market heats up, wrist-worn devices Industries as varied as healthcare, such as smartwatches are leading the pack. According to CCS Insight, forecasts for global sales of smart wearable devices finance, energy, transportation, will grow strongly over the next five years, with the global public safety, retail and hospitality market reaching nearly $30 billion by 2023.1 are deploying smartwatches for While smartwatches for fitness and activity tracking are popular, consumer demand is only part of the equation. added business value. Enterprises are also seeing business value in wearable devices. In a report by Robert Half Technology, 81 percent of CIOs surveyed expect wearable devices like smartwatches to Samsung has been working to address these concerns and become common tools in the workplace.2 has developed the tools to make its Galaxy and Galaxy Active smartwatches customizable, easily manageable and highly secure for enterprise users. This white paper will look at how these tools address key wearable security and manageability challenges, as well as considerations for smartwatch 81% deployments. of CIOs surveyed expect wearable devices like smartwatches to become common tools in the workplace. Industries as varied as healthcare, finance, energy, transportation, public safety, retail and hospitality are deploying smartwatches for added business value, such as hands-free communication for maintenance workers, task management, as well as physical monitoring of field workers in dangerous or remote locations. -

Apple and Nokia: the Transformation from Products to Services
9 Apple and Nokia: The Transformation from Products to Services In the mid- to late 2000s, Nokia flourished as the world’s dominant mobile phone – and mobile phone operating software – producer. Founded in 1871 originally as a rubber boots manufacturer, by 2007 Nokia produced more than half of all mobile phones sold on the planet, and its Symbian mobile operating system commanded a 65.6 percent global market share. 1 But within half a decade, Nokia would falter and be surpassed in the smartphone market not only by Apple’s revolu- tionary iPhone but also by competitors including Google and Samsung. And in September 2013, Nokia would sell its mobile phone business to Microsoft for $7 billion. 2 Apple literally came out of nowhere – it sold exactly zero mobile phones before the year 2007 (the year Nokia held more than half of the global market share) – but by the first quarter of 2013, Apple had captured almost 40 percent of the US smartphone market and over 50 percent of the operating profit in the global handset industry.3 In fiscal year 2013, Apple would sell five times more smart- phones than Nokia: 150 million iPhones compared to Nokia’s sales of 30 million Lumia Windows phones. 4 In contrast to Nokia, Apple real- ized it wasn’t just about the mobile device itself, it was about leveraging software to create a platform for developing compelling mobile experi- ences – including not just telephony but also music, movies, applica- tions, and computing – and then building a business model that allows partners to make money alongside the company (e.g., Apple’s iTunes and AppStore) and, in so doing, perpetuate a virtuous cycle of making the iPhone attractive to customers over multiple life cycles through ever-ex- panding feature sets. -

UI Design for Wearable Devices
FACULTY OF ENGINEERING UNIVERSITY OF PORTO UI Design for Wearable Devices Vitor Mota Master in Informatics and Computing Engineering Supervised by: Miguel Pimenta Monteiro (Assistant professor) Pedro Rocha (GlinttHS) January 2015 2 Abstract Smartwatches have been around for some time now (Ranger 2015), but 2015 is the year this wearable technology will finally get its boom in terms of popularity and growth. Technology giants like Apple, Google and Samsung are betting on their own-line of products such as the Apple Watch, Android Wear and Gear respectively (Apple Inc 2015a; Google Inc 2015b; SAMSUNG 2015). All of these devices are computation capable electronics with very small touch capacitive screens, limited number of hardware buttons with varying screen sizes and even shapes. Our research focused mainly on these constraints and how to successfully develop user friendly GUI’s for such small screens. The goal was to develop a model with guidelines to help developers provide easy to use and user friendly applications at a visual and interaction level to end users. To successfully achieve this, we first took a deep look at the available technology within these devices, including the framework each of the major platforms provide and the underlying hardware capabilities such as sensors like GPS, gyroscope, the use of the touch screen or microphone for user input and whether the shape of the device (round or squared) can have different effects on the design and usability. We also analyzed the impact of placement and arrangement of interface components having in mind that this technology, since it is a wearable watch, can be worn on both wrists and therefore will be used with only one hand that may obscure a different portion of the interface depending on which wrist the user uses it (Chandra and Raghunath 2000). -

Characterizing Smartwatch Usage in the Wild
Characterizing Smartwatch Usage In The Wild Xing Liu1 Tianyu Chen1 Feng Qian1 Zhixiu Guo23 Felix Xiaozhu Lin4 Xiaofeng Wang1 Kai Chen25 1Indiana University Bloomington 2SKLOIS, Institute of Information Engineering, Chinese Academy of Sciences 3Beijing Jiaotong University 4Purdue ECE 5School of Cyber Security, University of Chinese Academy of Sciences ABSTRACT participants, we conduct an in-depth characterization of three key Smartwatch has become one of the most popular wearable aspects of smartwatch usage “in the wild”: usage patterns, energy computers on the market. We conduct an IRB-approved consumption, and network traffic characteristics. This is to our measurement study involving 27 Android smartwatch users. Using knowledge the most comprehensive and in-depth crowd-sourced a 106-day dataset collected from our participants, we perform in- study of smartwatches. Our key measurement results consist of depth characterization of three key aspects of smartwatch usage “in the following. the wild”: usage patterns, energy consumption, and network traffic. • We characterize the smartwatch usage patterns. An Android Based on our findings, we identify key aspects of the smartwatch watch can stay in one of the four states with diverse power ecosystem that can be further improved, propose recommendations, characteristics: fully awake, dozing (with dimmed watch face and point out future research directions. display and restricted system activity), sleeping (screen further turned off), and charging. We find that smartwatch’s wake-up CCS Concepts period accounts for only 2% of the overall usage period among • → the four states. The wake-up sessions are not only short, but Human-centered computing Ubiquitous and mobile also frequent (72 times per day on average). -

Nexus S 4G: First Pure Google 4G Device with Android 2.3 in the US 22 March 2011
Nexus S 4G: First Pure Google 4G Device with Android 2.3 in the US 22 March 2011 outdoors, so videos, pictures and games look their best and the sun won't wash them out. Sprint Nexus S 4G customers will be among the first to receive Android software upgrades and new Google mobile apps. In many cases, the device will get the updates and new apps as soon as they are available. Nexus S 4G features a 5 megapixel rear-facing camera and camcorder and front-facing VGA camera. In addition, Nexus S 4G features a gyroscope sensor to provide a smooth, fluid gaming experience when the user tilts the device up or down or pans the phone to the left or right. Sprint extends its 4G device innovation with the upcoming availability of the 20th 4G device and Additional key features include: fourth 4G phone, Nexus S 4G from Google. Coming to Sprint this spring, it will also be able to • 3G/4G Mobile Hotspot capability, take advantage of the controls and services supporting up to six Wi-Fi enabled devices enabled by Google Voice integration built into the simultaneously Sprint Network. • Android Market for access to more than 150,000 applications, widgets and games available Manufactured by Samsung, Nexus S 4G comes for download to customize the experience packed with a pure Google experience using • Google mobile services such as Google Android 2.3, Gingerbread, the fastest version of Search, Gmail, Google Maps with Navigation, Android available for smartphones. It is powered syncing with Google Calendar, Voice Actions and by a 1GHz Samsung application processor that YouTube produces rich 3D-like graphics, faster upload and • Corporate email (Microsoft Exchange download times and supports HD-like multimedia ActiveSync), personal (POP & IMAP) email and content along with a dedicated Graphics instant messaging Processing Unit (GPU) to make playing mobile • Near Field Communication (NFC) games, browsing the Web and watching videos a technology, which allows the device to read fast, fluid and smooth experience.