Ten Steps to Smartphone Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sophos Mobile Security
Sophos Mobile Security Protect your Android devices against malware and other threats The market dominance of Android devices and the inherent openness of Android led to the proliferation of malware and Potentially Unwanted Applications (PUA). SophosLabs detected over a million new pieces of malware in 2014 alone, and the growth rate is accelerating. Malware can lead to data loss, reputation loss, additional costs, and reduced performance. Highlights Protection and performance The Sophos Mobile Security antivirus app protects your Android devices without compromising Ì Privacy Advisor warns performance or battery life. The app uses up-to-the-minute intelligence from SophosLabs and the Sophos of potential privacy core antivirus engine. This means your apps are automatically scanned for malware as you install them. breaches Sophos Mobile Security’s consistent performance has earned recognition from independent testing agencies including AV-Test. Ì Security Advisor gives tips to improve device Malware protection security Our Sophos Mobile Security antivirus app protects your Android devices with proactive identification of malware. Your apps are automatically scanned for malware as you install them. Sophos includes protection Ì Loss and Theft for PUAs and low-reputation apps—new apps that have no known history and may pose a threat. PUAs Protection include adware, rootkits, diallers, and any association the app may have to previous malicious behaviour such as a certificate that has been compromised. Ì App Protection with additional passwords for Web protection sensitive apps Surf securely on the internet from your Android device. Sophos Mobile Security checks all websites against a Ì Spam Filter SophosLabs database for known malicious sites and prevents users from accessing them. -

SMS “Virtual Collection Center” Smartphone
Feed the Future Innovation Lab for Livestock Systems INNOVATION SUMMARY: SMS “VIRTUAL COLLECTION CENTER” SMARTPHONE APP The Virtual Collection Center (VCC) is an innovative short message service (SMS) mobile application (app) for improved goat marketing. Through the use of the VCC app, inventory updates flow from cooperative members to leaders, while cooperative leaders use the VCC app to share price information with members and fill orders from traders by inviting members to sales events. The VCC app improves the goat value chain by reducing transaction costs, which should strengthen cooperatives and benefit small livestock producers by increasing trade volumes. Lead Implementing Institution: University of Florida Category: Marketing & Distribution Applied in: Nepal The VCC app is implemented by Heifer International Nepal whose Innovation Type: Technology New/Adapted: New field personnel assist cooperative members in downloading the app while providing training and Created for: Mainly Women Nutrition Linkage: Dietary Quality monitoring in the initial stages. The app is designed to be intuitive, eliminating the need for intensive training. Within cooperatives, the In Nepal, goats are an essential source of income and nearly every rural Nepali household app is accessed by “VCC owns at least a few goats. To buy goats, traders often travel over large areas characterized managers”, who are members of cooperative self-help groups by rugged terrain and poor infrastructure, making multiple visits to individual households necessary to complete sales. The resulting high transaction costs can stifle the value chain. (subgroups within the Cooperatives can reduce transaction costs by allowing for bulk purchases of animals. But cooperatives), and cooperative cooperatives may struggle to coordinate sales by members spread out over large areas of leaders. -

The Classic Blackberry – Supercharged
COMING SOON! The classic BlackBerry – supercharged. BlackBerry® Curve™ 3G smartphone The new BlackBerry Curve 3G smartphone from AT&T is BlackBerry Curve 3G powerful yet affordable. This BlackBerry classic now gives smartphone you 3G speed and everything you expect from the popular The first 3G Curve BlackBerry Curve family, with a QWERTY keyboard, work and from AT&T. personal email, powerful personal management capabilities and much more. A superior connection. • Be at the forefront. With simultaneous voice and data when using the 3G or Wi-Fi network, you can check the facts on email or the web while talking on the phone with clients or colleagues. • Work with speed and confidence. The BlackBerry Curve 3G • Speed with flexibility. The BlackBerry Curve 3G smartphone has a powerful 624 MHz processor, 256 MB flash smartphone allows you to quickly download and upload memory/256 MB SDRAM and an included 2 GB microSD™ card content and surf the web faster on the nation’s fastest for storage, expandable up to 32 GB. broadband mobile network.* And with built-in Wi-Fi® • Focused applications. Keep up-to-date and informed of your (802.11 b/g/n), access the information and download the work and life – explore BlackBerry® App World™ and pre-loaded large files you need at Wi-Fi speeds. applications including LinkedIn™, My-Cast® Weather, Bloomberg® • Automatically unlimited. The new BlackBerry Curve 3G Mobile, AllSport GPS™, WHERE®, City ID®, Facebook®, MySpace™, smartphone automatically connects to AT&T Wi-Fi Hot Twitter™ and more. Spots in the U.S.** for unlimited usage on the AT&T Wi-Fi • Capture the moment. -

Total Defense Mobile Security
USER'S GUIDE Total Defense Mobile Security Total Defense Mobile Security User's Guide Publication date 2015.04.09 Copyright© 2015 Total Defense Mobile Security Legal Notice All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without written permission from an authorized representative of Total Defense. The inclusion of brief quotations in reviews may be possible only with the mention of the quoted source. The content can not be modified in any way. Warning and Disclaimer. This product and its documentation are protected by copyright. The information in this document is provided on an “as is” basis, without warranty. Although every precaution has been taken in the preparation of this document, the authors will not have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the information contained in this work. This book contains links to third-party Websites that are not under the control of Total Defense, therefore Total Defense is not responsible for the content of any linked site. If you access a third-party website listed in this document, you will do so at your own risk. Total Defense provides these links only as a convenience, and the inclusion of the link does not imply that Total Defense endorses or accepts any responsibility for the content of the third-party site. Trademarks. Trademark names may appear in this book. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Android 4.4 home screen Company / developer Google Open Handset Alliance Android Open Source Project (AOSP) Programmed in C (core), C++, Java (UI) OS family Unix-like Working state Current Source model Open source with proprietary components Initial release September 23, 2008 Latest stable release 4.4.2 KitKat / December 9, 2013 Marketing target Smartphones Tablet computers Available language(s) Multi-lingual (46 languages) Package manager Google Play, APK Supported platforms 32-bit ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) [1] [2] [3] Userland Bionic libc, shell from NetBSD, native core utilities with a few from NetBSD Default user interface Graphical (Multi-touch) License Apache License 2.0 Linux kernel patches under GNU GPL v2 [4] Official website www.android.com Android is an operating system based on the Linux kernel, and designed primarily for touchscreen mobile devices such as smartphones and tablet computers. Initially developed by Android, Inc., which Google backed financially Android (operating system) 2 and later bought in 2005, Android was unveiled in 2007 along with the founding of the Open Handset Alliance: a consortium of hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices. The first publicly available smartphone running Android, the HTC Dream, was released on October 22, 2008. The user interface of Android is based on direct manipulation, using touch inputs that loosely correspond to real-world actions, like swiping, tapping, pinching and reverse pinching to manipulate on-screen objects. Internal hardware such as accelerometers, gyroscopes and proximity sensors are used by some applications to respond to additional user actions, for example adjusting the screen from portrait to landscape depending on how the device is oriented. -
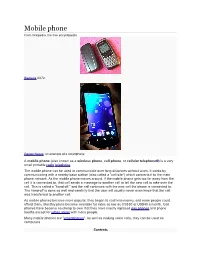
Mobile Phone from Wikipedia, the Free Encyclopedia
Mobile phone From Wikipedia, the free encyclopedia Siemens AX72. Galaxy Nexus, an example of a smartphone A mobile phone (also known as a wireless phone, cell phone, or cellular telephone[1]) is a very small portable radio telephone. The mobile phone can be used to communicate over long distances without wires. It works by communicating with a nearby base station (also called a "cell site") which connects it to the main phone network. As the mobile phone moves around, if the mobile phone gets too far away from the cell it is connected to, that cell sends a message to another cell to tell the new cell to take over the call. This is called a "hand off," and the call continues with the new cell the phone is connected to. The hand-off is done so well and carefully that the user will usually never even know that the call was transferred to another cell. As mobile phones became more popular, they began to cost less money, and more people could afford them. Monthly plans became available for rates as low as US$30 or US$40 a month. Cell phones have become so cheap to own that they have mostly replaced pay phones and phone booths except for urban areas with many people. Many mobile phones are "smartphones". As well as making voice calls, they can be used as computers. Contents [hide] 1 History 2 Technology 3 Shapes 4 How mobile phones work 5 Networks and payment 6 Smartphones 7 References History[change | change source] Mobile phones in the 1950s through 1970s were large and heavy, and most were built into cars. -

Mobile Security Companion to the CIS Critical Security Controls (Version 6)
Mobile Security Companion to the CIS Critical Security Controls (Version 6) 1 Mobile Security Companion to the CIS Critical Security Controls (Version 6) Introduction ................................................................................................................................................................................................................................................................. 3 Description ................................................................................................................................................................................................................................................................... 5 CIS Critical Security Controls (Version 6): Mobile Security .................................................................................................................................................................... 5 2 Introduction Mobile devices are starting to replace laptops for regular business use. Organizations are building or porting their applications to mobile platforms, so users are increasingly accessing the same data with mobile as with their laptops. Also, organizations have increasingly implemented Bring Your Own Device (BYOD) policies to manage this trend. However, many organizations have been struggling with the increase of personal mobile devices, and don’t fully understand the security risks they may bring. There are concerns that their compact size makes them easy to lose, that they run newer operating systems that don’t -

A Comparative Analysis of Mobile Operating Systems Rina
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-6, Issue-12, Dec 2018 E-ISSN: 2347-2693 A Comparative Analysis of mobile Operating Systems Rina Dept of IT, GGDSD College, Chandigarh ,India *Corresponding Author: [email protected] Available online at: www.ijcseonline.org Accepted: 09/Dec/2018, Published: 31/Dec/2018 Abstract: The paper is based on the review of several research studies carried out on different mobile operating systems. A mobile operating system (or mobile OS) is an operating system for phones, tablets, smart watches, or other mobile devices which acts as an interface between users and mobiles. The use of mobile devices in our life is ever increasing. Nowadays everyone is using mobile phones from a lay man to businessmen to fulfill their basic requirements of life. We cannot even imagine our life without mobile phones. Therefore, it becomes very difficult for the mobile industries to provide best features and easy to use interface to its customer. Due to rapid advancement of the technology, the mobile industry is also continuously growing. The paper attempts to give a comparative study of operating systems used in mobile phones on the basis of their features, user interface and many more factors. Keywords: Mobile Operating system, iOS, Android, Smartphone, Windows. I. INTRUDUCTION concludes research work with future use of mobile technology. Mobile operating system is the interface between user and mobile phones to communicate and it provides many more II. HISTORY features which is essential to run mobile devices. It manages all the resources to be used in an efficient way and provides The term smart phone was first described by the company a user friendly interface to the users. -

Maxphone—Multi-Access Extension for Smartphones Fact Sheet
Completed DHS Science and Technology Directorate MaXphone—Multi-Access Extension for Smartphones Providing devices that embrace Land Mobile P25, cellular/Public Switched Telephone Network voice, Radio (LMR) and broadband cellular networks and Voice-over-IP. It also allows for enhanced security by The First Responder Network Authority (FirstNet) is providing end-to-end P25 encryption across LMR and charged with creating a nationwide public safety broadband broadband networks. network that provides the public safety community with a Enabling customizable, affordable applications boost in network capacity and capability. Still, commercial MaXphone leverages rapid development in commercial cellular broadband networks (e.g., 4G LTE and 3G) will broadband networks and smartphone capability. Open likely remain the dominant option to support first responder application development environments (e.g., Android) broadband applications for the immediate future. enable novel, innovative, customizable and affordable first Broadband networks do not provide first responders with responder applications. An open source, fully functioning mission critical voice capabilities (i.e., radio-to-radio or P25 software package will be available on the Android one-to-many communications) that are available on LMR environment. MaxJacket will be based on COTS networks. However, application and service development in components and contain the necessary functions for the P25 the LMR domain stand in stark contrast to the explosive solution. growth in the commercial broadband sector. Therefore, a reasonable, cost effective approach to creating more capable first responder devices embraces existing LMR networks Legacy P25 handset and commercial broadband cellular networks by using open P25 platforms to encourage application development. IP25 P25 Network Gateway Access The Department of Homeland Security Science and Technology Directorate and U.S. -

Securing and Managing Wearables in the Enterprise
White Paper: Securing and Managing Wearables in the Enterprise Streamline deployment and protect smartwatch data with Samsung Knox Configure White Paper: Securing and Managing Wearables in the Enterprise 2 Introduction: Smartwatches in the Enterprise As the wearable device market heats up, wrist-worn devices Industries as varied as healthcare, such as smartwatches are leading the pack. According to CCS Insight, forecasts for global sales of smart wearable devices finance, energy, transportation, will grow strongly over the next five years, with the global public safety, retail and hospitality market reaching nearly $30 billion by 2023.1 are deploying smartwatches for While smartwatches for fitness and activity tracking are popular, consumer demand is only part of the equation. added business value. Enterprises are also seeing business value in wearable devices. In a report by Robert Half Technology, 81 percent of CIOs surveyed expect wearable devices like smartwatches to Samsung has been working to address these concerns and become common tools in the workplace.2 has developed the tools to make its Galaxy and Galaxy Active smartwatches customizable, easily manageable and highly secure for enterprise users. This white paper will look at how these tools address key wearable security and manageability challenges, as well as considerations for smartwatch 81% deployments. of CIOs surveyed expect wearable devices like smartwatches to become common tools in the workplace. Industries as varied as healthcare, finance, energy, transportation, public safety, retail and hospitality are deploying smartwatches for added business value, such as hands-free communication for maintenance workers, task management, as well as physical monitoring of field workers in dangerous or remote locations. -

Threat Modeling Framework for Mobile Communication Systems
Threat modeling framework for mobile communication systems Siddharth Prakash Rao Silke Holtmanns Tuomas Aura Aalto University Nokia-Bell Labs Aalto University Espoo, Finland Espoo, Finland Espoo, Finland siddharth:rao@aalto: silke:holtmanns@nokia-bell- tuomas:aura@aalto: labs:com ABSTRACT protocols, which evolved in a more open setup, security tools avail- Due to the complex nature of mobile communication systems, most able in the public domain for the laer are now used by hackers to of the security eorts in its domain are isolated and scaered across exploit the mobile networks [9]. underlying technologies. is has resulted in an obscure view of Despite the odds, mobile communication systems have under- the overall security. In this work, we aempt to x this problem gone a fair amount of scrutiny from the security research com- by proposing a domain-specic threat modeling framework. By munity. For example, internal components of a mobile device [71, gleaning from a diverse and large body of security literature, we 74, 101], radio communication between the phone and the cell systematically organize the aacks on mobile communications into towers[37, 162], and mobile core network protocols [55, 80, 122] various tactics and techniques. Our framework is designed to model have been tested for security-critical issues. All these isolated adversarial behavior in terms of its aack phases and to be used as research eorts are scaered across underlying protocols and tech- a common taxonomy matrix. We also provide concrete examples nologies, and, it has resulted in an obscure and complex view of mo- of using the framework for modeling the aacks individually and bile communication security. -

Brightcloud® Mobile Security SDK
DATASHEET BrightCloud® Mobile Security SDK Simple, flexible, powerful detection and protection for Android® devices Overview • Malicious apps and PUAs are a threat to personal and corporate data, and can compromise Mobile Security SDK benefits: financial transactions 1) Industry-leading mobile threat protection • In 2019, Trojans accounted for 56.9% of Android threats detected1 2) Does not slow devices or hinder user productivity • The BrightCloud Mobile Security SDK offers 3) Simple, flexible development options for partners enhanced mobile security, including antivirus, antimalware, application scanning and interrogation, device root detection, and device risk scoring Individuals using smartphones and tablets tend to Webroot detects a variety of malicious apps, including malware, engage in activities that increase the risk of attacks spyware, and trojans. PUAs include commercial rooting tools, on themselves and networks. For instance, using hacking tools, aggressive advertising, and data leakage apps. unsecured public WiFi or downloading apps from Security administrators may consider eliminating PUAs, as they untrustworthy third-party sites can infect a device have the potential to impact data loss or incur unwanted mobile with mobile malware. These could lead to unwanted usage fees. consequences, including data exfiltration, camera and microphone hijacking, financial extortion, or acting as a The BrightCloud Mobile Security SDK addresses mobile device Trojan horse into the WiFi network it connects to. threats by enabling technology partners to offer enhanced mobile security for their customers within their solutions. It features antivirus, antimalware, application scanning and interrogation, Spyware 1.6% Rootkits 0.3% device root detection, and device risk scoring, all while utilizing System Monitor 0.3% very little memory, bandwidth, or battery life.