Combined Complexity of Probabilistic Query Evaluation Mikaël Monet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Number of Dissimilar Supergraphs of a Linear Graph
Pacific Journal of Mathematics THE NUMBER OF DISSIMILAR SUPERGRAPHS OF A LINEAR GRAPH FRANK HARARY Vol. 7, No. 1 January 1957 THE NUMBER OF DISSIMILAR SUPERGRAPHS OF A LINEAR GRAPH FRANK HARARY 1. Introduction* A (p, q) graph is one with p vertices and q lines. A formula is obtained for the number of dissimilar occurrences of a given (α, β) graph H as a subgraph of all (p, q) graphs G, oc<ip, β <: q, that is, for the number of dissimilar (p, q) supergraphs of H. The enumeration methods are those of Pόlya [7]. This result is then appli- ed to obtain formulas for the number of dissimilar complete subgraphs (cliques) and cycles among all (p, q) graphs. The formula for the num- ber of rooted graphs in [2] is a special case of the number of dissimilar cliques. This note complements [3] in which the number of dissimilar {p, k) subgraphs of a given (p, q) graph is found. We conclude with a discussion of two unsolved problems. A {linear) graph G (see [5] as a general reference) consists of a finite set V of vertices together with a prescribed subset W of the col- lection of all unordered pairs of distinct vertices. The members of W are called lines and two vertices vu v% are adjacent if {vlt v2} e W, that is, if there is a line joining them. By the complement Gr of a graph G, we mean the graph whose vertex-set coincides with that of G, in which two vertices are adjacent if and only if they are not adjacent in G. -

Remembering Frank Harary
Discrete Mathematics Letters Discrete Math. Lett. 6 (2021) 1–7 www.dmlett.com DOI: 10.47443/dml.2021.s101 Editorial Remembering Frank Harary On March 11, 2005, at a special session of the 36th Southeastern International Conference on Combinatorics, Graph The- ory, and Computing held at Florida Atlantic University in Boca Raton, the famous mathematician Ralph Stanton, known for his work in combinatorics and founder of the Institute of Combinatorics and Its Applications, stated that the three mathematicians who had the greatest impact on modern graph theory have now all passed away. Stanton was referring to Frenchman Claude Berge of France, Canadian William Tutte, originally from England, and a third mathematician, an American, who had died only 66 days earlier and to whom this special session was being dedicated. Indeed, that day, March 11, 2005, would have been his 84th birthday. This third mathematician was Frank Harary. Let’s see what led Harary to be so recognized by Stanton. Frank Harary was born in New York City on March 11, 1921. He was the oldest child of Jewish immigrants from Syria and Russia. He earned a B.A. degree from Brooklyn College in 1941, spent a graduate year at Princeton University from 1943 to 1944 in theoretical physics, earned an M.A. degree from Brooklyn College in 1945, spent a year at New York University from 1945 to 1946 in applied mathematics, and then moved to the University of California at Berkeley, where he wrote his Ph.D. Thesis on The Structure of Boolean-like Rings, in 1949, under Alfred Foster. -

Leverages and Constraints for Turkish Foreign Policy in Syrian War: a Structural Balance Approach
Instructions for authors, permissions and subscription information: E-mail: [email protected] Web: www.uidergisi.com.tr Leverages and Constraints for Turkish Foreign Policy in Syrian War: A Structural Balance Approach Serdar Ş. GÜNER* and Dilan E. KOÇ** * Assoc. Prof. Dr., Department of International Relations, Bilkent University ** Student, Department of International Relations, Bilkent University To cite this article: Güner, Serdar Ş. and Koç, Dilan E., “Leverages and Constraints for Turkish Foreign Policy in Syrian War: A Structural Balance Approach”, Uluslararası İlişkiler, Volume 15, No. 59, 2018, pp. 89-103. Copyright @ International Relations Council of Turkey (UİK-IRCT). All rights reserved. No part of this publication may be reproduced, stored, transmitted, or disseminated, in any form, or by any means, without prior written permission from UİK, to whom all requests to reproduce copyright material should be directed, in writing. References for academic and media coverages are beyond this rule. Statements and opinions expressed in Uluslararası İlişkiler are the responsibility of the authors alone unless otherwise stated and do not imply the endorsement by the other authors, the Editors and the Editorial Board as well as the International Relations Council of Turkey. Uluslararası İlişkiler Konseyi Derneği | Uluslararası İlişkiler Dergisi Web: www.uidergisi.com.tr | E- Mail: [email protected] Leverages and Constraints for Turkish Foreign Policy in Syrian War: A Structural Balance Approach Serdar Ş. GÜNER Assoc. Prof. Dr., Department of International Relations, Bilkent University, Ankara, Turkey. E-mail: [email protected] Dilan E. KOÇ Student, Department of International Relations, Bilkent University, Ankara, Turkey. E-mail: [email protected] The authors thank participants of the Seventh Eurasian Peace Science Network Meeting of 2018 and anonymous referees for their comments and suggestions. -

Introduction to Graph Theory: a Discovery Course for Undergraduates
Introduction to Graph Theory: A Discovery Course for Undergraduates James M. Benedict Augusta State University Contents 1 Introductory Concepts 1 1.1 BasicIdeas ...................................... 1 1.2 Graph Theoretic Equality . 2 1.3 DegreesofVertices .................................. 4 1.4 Subgraphs....................................... 6 1.5 The Complement of a Graph . 7 2 Special Subgraphs 9 2.1 Walks ......................................... 9 2.2 Components...................................... 10 2.3 BlocksofaGraph................................... 11 3 Three Famous Results and One Famous Graph 14 3.1 The Four-Color Theorem . 14 3.2 PlanarGraphs..................................... 16 3.3 ThePetersenGraph ................................. 18 3.4 TraceableGraphs ................................... 18 K(3;3;3) = H1 H2 Removing the edge w1v2 destroys the only C4 v 3 u1 H1: H2: w3 v v2 3 u w1 u 2 u u 2 v 1 3 w 1 w 2 2 w3 u3 w1 v2 v1 Place any edge of H1 into H2 or (vice versa) and a C4 is created. i Remarks By reading through this text one can acquire a familiarity with the elementary topics of Graph Theory and the associated (hopefully standard) notation. The notation used here follows that used by Gary Chartrand at Western Michigan University in the last third of the 20th century. His usage of notation was in‡uenced by that of Frank Harary at the University of Michigan beginning in the early 1950’s. The text’s author was Chartrand’s student at WMU from 1973 to 1976. In order to actually learn any graph theory from this text, one must work through and solve the problems found within it. Some of the problems are very easy. -

Combinatorics: a First Encounter
Combinatorics: a first encounter Darij Grinberg Thursday 10th January, 2019at 9:29pm (unfinished draft!) Contents 1. Preface1 1.1. Acknowledgments . .4 2. What is combinatorics?4 2.1. Notations and conventions . .4 1. Preface These notes (which are work in progress and will remain so for the foreseeable fu- ture) are meant as an introduction to combinatorics – the mathematical discipline that studies finite sets (roughly speaking). When finished, they will cover topics such as binomial coefficients, the principles of enumeration, permutations, parti- tions and graphs. The emphasis falls on enumerative combinatorics, meaning the art of computing sizes of finite sets (“counting”), and graph theory. I have tried to keep the presentation as self-contained and elementary as possible. The reader is assumed to be familiar with some basics such as induction proofs, equivalence relations and summation signs, as well as have some experience with mathematical proofs. One of the best places to catch up on these basics and to gain said experience is the MIT lecture notes [LeLeMe16] (particularly their first five chapters). Two other resources to familiarize oneself with proofs are [Hammac15] and [Day16]. Generally, most good books about “reading and writing mathemat- ics” or “introductions to abstract mathematics” should convey these skills, although the extent to which they actually do so may differ. These notes are accompanying two classes on combinatorics (Math 4707 and 4990) I am giving at the University of Minneapolis in Fall 2017. Here is a (subjective and somewhat random) list of recommended texts on the kinds of combinatorics that will be considered in these notes: • Enumerative combinatorics (aka counting): 1 Notes on graph theory (Thursday 10th January, 2019, 9:29pm) page 2 – The very basics of the subject can be found in [LeLeMe16, Chapters 14– 15]. -

Structural Balance: a Generalization of Heider's Theory'
VOL. 63, No. 5 SEPTEMBER, 1956 THE PSYCHOLOGICAL REVIEW STRUCTURAL BALANCE: A GENERALIZATION OF HEIDER'S THEORY' DORWIN CARTWRIGHT AND FRANK HARARY Research Center for Group Dynamics, University of Michigan A persistent problem of psychology will arise to change it toward a state has been how to deal conceptually of balance. These pressures may with patterns of interdependent prop- work to change the relation of affec- erties. This problem has been cen- tion between P and 0, the relation of tral, of course, in the theoretical responsibility between 0 and X, or the treatment by Gestalt psychologists of relation of evaluation between P phenomenal or neural configurations andX. or fields (12, 13, 15). It has also The purpose of this paper is to been of concern to social psychologists present and develop the consequences and sociologists who attempt to em- of a formal definition of balance which ploy concepts referring to social sys- is consistent with Heider's conception tems (18). and which may be employed in a more Heider (19), reflecting the general general treatment of empirical con- field-theoretical approach, has con- figurations. The definition is stated sidered certain aspects of cognitive in terms of the mathematical theory fields which contain perceived people of linear graphs (8, 14) and makes use and impersonal objects or events. of a distinction between a given rela- His analysis focuses upon what he calls tion and its opposite relation. Some the P-O-X unit of a cognitive field, of the ramifications of this definition consisting of P (one person), 0 (an- are then examined by means of other person), and X (an impersonal theorems derivable from the definition entity). -

Regular Graphs Containing a Given Graph
Regular graphs containing a given graph Autor(en): Akiyama, Jin / Era, Hiroshi / Harary, Frank Objekttyp: Article Zeitschrift: Elemente der Mathematik Band (Jahr): 38 (1983) Heft 1 PDF erstellt am: 03.10.2021 Persistenter Link: http://doi.org/10.5169/seals-37177 Nutzungsbedingungen Die ETH-Bibliothek ist Anbieterin der digitalisierten Zeitschriften. Sie besitzt keine Urheberrechte an den Inhalten der Zeitschriften. Die Rechte liegen in der Regel bei den Herausgebern. Die auf der Plattform e-periodica veröffentlichten Dokumente stehen für nicht-kommerzielle Zwecke in Lehre und Forschung sowie für die private Nutzung frei zur Verfügung. Einzelne Dateien oder Ausdrucke aus diesem Angebot können zusammen mit diesen Nutzungsbedingungen und den korrekten Herkunftsbezeichnungen weitergegeben werden. Das Veröffentlichen von Bildern in Print- und Online-Publikationen ist nur mit vorheriger Genehmigung der Rechteinhaber erlaubt. Die systematische Speicherung von Teilen des elektronischen Angebots auf anderen Servern bedarf ebenfalls des schriftlichen Einverständnisses der Rechteinhaber. Haftungsausschluss Alle Angaben erfolgen ohne Gewähr für Vollständigkeit oder Richtigkeit. Es wird keine Haftung übernommen für Schäden durch die Verwendung von Informationen aus diesem Online-Angebot oder durch das Fehlen von Informationen. Dies gilt auch für Inhalte Dritter, die über dieses Angebot zugänglich sind. Ein Dienst der ETH-Bibliothek ETH Zürich, Rämistrasse 101, 8092 Zürich, Schweiz, www.library.ethz.ch http://www.e-periodica.ch El Math Vol 38, 1983 15 Der Grundgedanke dieses Beweises ist also, zu zeigen, dass diejenigen Paare (a,b), deren Schrittzahl T(a,b) die Abschätzung von Dixon (Lemma 2) erfüllen, den Hauptbeitrag zu dem gesuchten Mittelwert liefern. Zum Abschluss seien noch einige numerische Ergebnisse angegeben, wie man sie mit einem programmierbaren Taschenrechner errechnen kann. -

BEAUTIFUL CONJECTURES in GRAPH THEORY Adrian Bondy
BEAUTIFUL CONJECTURES IN GRAPH THEORY Adrian Bondy What is a beautiful conjecture? The mathematician's patterns, like the painter's or the poet's must be beautiful; the ideas, like the colors or the words must fit together in a harmonious way. Beauty is the first test: there is no permanent place in this world for ugly mathematics. G.H. Hardy Some criteria: . Simplicity: short, easily understandable statement relating basic concepts. Element of Surprise: links together seemingly disparate concepts. Generality: valid for a wide variety of objects. Centrality: close ties with a number of existing theorems and/or conjectures. Longevity: at least twenty years old. Fecundity: attempts to prove the conjecture have led to new concepts or new proof techniques. Reconstruction Conjecture P.J. Kelly and S.M. Ulam 1942 Every simple graph on at least three vertices is reconstructible from its vertex-deleted subgraphs STANISLAW ULAM Simple Surprising General Central Old F ertile ∗∗ ∗ ∗ ∗ ∗ ∗ ∗ v1 v2 v6 v3 v5 v4 G G − v1 G − v2 G − v3 PSfrag replacements G − v4 G − v5 G − v6 Edge Reconstruction Conjecture F. Harary 1964 Every simple graph on at least four edges is reconstructible from its edge-deleted subgraphs FRANK HARARY Simple Surprising General Central Old F ertile ∗ ∗ ∗ ∗ ∗ ∗ ∗∗ ∗ G H PSfrag replacements G H MAIN FACTS Reconstruction Conjecture False for digraphs. There exist infinite families of nonreconstructible tournaments. P.J. Stockmeyer 1977 Edge Reconstruction Conjecture True for graphs on n vertices and more than n log2 n edges. L. Lovasz´ 1972, V. Muller¨ 1977 Path Decompositions T. Gallai 1968 Every connected simple graph on n vertices can 1 be decomposed into at most 2(n + 1) paths TIBOR GALLAI Simple Surprising General Central Old F ertile ∗ ∗ ∗ ∗ ∗ ∗ ∗ ∗∗ ∗∗ Circuit Decompositions G. -

John R. Bowles Thesis A
- Math Goes to Hollywood or: How I Learned to Stop Worrying and Love the Math An Honors Thesis (HONRS 499) by John R. Bowles Thesis Advisor -- Dr. Kerry Jones ~~ Ball State University Muncie, IN May 5,2001 Graduation Date: May 5, 2001 speD!1 The:.;I::::; - Abstract Mathematics doesn't put people in the seats at the movie theater, but recently mathematics can be found more and more in popular films. Though Hollywood has shunned the value of mathematics in the past, a trio of excellent films have recently been made with mathematics as an integral character. This paper examines the math topics discussed in three of those movies: Good Will Hunting, Rushmore, and Pi. The mathematics used in each film is analyzed for validity. Also discussed is how each film's depiction of mathematics might effect society's view of mathematics. -- Acknowedgements Thank you Dr. Jones for your patience and guidance with this paper. Thanks also to Dr. Bremigan for your unexpected help. Also, thank you Nate for being there the first time I saw most of these movies and Erin for helping me stay sane while writing this paper. - Bowles I -- John R. Bowles Honors Thesis 5 May 2001 Math Goes to Hollywood or: How I Learned to Stop Worrying and Love the Math "Tough guys don't do math. Tough guys fry chicken for a living!" These are the words that high school math teacher Jaime Escalante (played by Edward James Olmos) sarcastically exclaims to his students in the film Stand and Deliver (IMDB). He is trying to overcome a common stigma shared by many teenagers that math is not cool. -

Paul Erdos: the Master of Collaboration
Paul Erdos: The Master of Collaboration Jerrold W. Grossman Department of Mathematical Sciences, Oakland University, Rochester, MI48309- 4401 Over a span of more than 60 years, Paul Erdos has taken the art of col laborative research in mathematics to heights never before achieved. In this brief look at his collaborative efforts, we will explore the breadth of Paul's interests, the company he has kept, and the influence of his collaboration in the mathematical community. Rather than focusing on the mathematical content of his work or the man himself, we will see what conclusions can be drawn by looking mainly at publication lists. Thus our approach will be mostly bibliographical, rather than either mathematical or biographical. The data come mainly from the bibliography in this present volume and records kept by Mathematical Reviews (MR) [13]. Additional useful sources of infor mation include The Hypertext Bibliography Project (a database of articles in theoretical computer science) [11], Zentralblatt [16], the Jahrbuch [10]' vari ous necrological articles too numerous to list, and personal communications. Previous articles on these topics can be found in [3,4,7,8,14]. Paul has certainly become a legend, whose fame (as well as his genius and eccentricity) has spread beyond the circles of research mathematicians. We find a popular videotape about him [2], articles in general circulation maga zines [9,15] (as well as in mathematical publications-see [1] for a wonderful example), and graffiti on the Internet (e.g., his quotation that a mathemati cian is a device for turning coffee into theorems, on a World Wide Web page designed as a sample of the use of the html language [12]). -

Anthropology, Mathematics, Kinship: a Tribute to the Anthropologist Per Hage 1 and His Work with the Mathematician Frank Harary
MATHEMATICAL ANTHROPOLOGY AND CULTURAL THEORY: AN INTERNATIONAL JOURNAL VOLUME 2 NO. 3 JULY 2008 ANTHROPOLOGY, MATHEMATICS, KINSHIP: A TRIBUTE TO THE ANTHROPOLOGIST PER HAGE 1 AND HIS WORK WITH THE MATHEMATICIAN FRANK HARARY DAVID JENKINS ROUNDHOUSE INSTITUTE FOR FIELD STUDIES [email protected] COPYRIGHT 2008 ALL RIGHTS RESERVED BY AUTHOR SUBMITTED: MAY 1, 2008 ACCEPTED: JUNE 15, 2008 MATHEMATICAL ANTHROPOLOGY AND CULTURAL THEORY: AN INTERNATIONAL JOURNAL ISSN 1544-5879 1 A version of this paper was prepared for the 105th Annual American Anthropological Association Meeting. Session title: Kinship and Language: Per Hage (1935 – 2004) Memorial Session. San Jose, California, November 14 – 18, 2006. JENKINS: ANTHROPOLOGY, MATHEMATICS, KINSHIP WWW.MATHEMATICALANTHROPOLOGY.ORG MATHEMATICAL ANTHROPOLOGY AND CULTURAL THEORY: AN INTERNATIONAL JOURNAL VOLUME 2 NO. 3 JULY 2008 ANTHROPOLOGY, MATHEMATICS, KINSHIP: A TRIBUTE TO THE ANTHROPOLOGIST PER HAGE AND HIS WORK WITH THE MATHEMATICIAN FRANK HARARY DAVID JENKINS ROUNDHOUSE INSTITUTE FOR FIELD STUDIES Abstract: Over a long and productive career, Per Hage produced a diverse and influential body of work. He conceptualized and solved a range of anthropological problems, often with the aid of mathematical models from graph theory. In three books and many research articles, Hage, and his mathematician collaborator Frank Harary, developed innovative analyses of exchange relations, including marriage, ceremonial, and resource exchange. They advanced network models for the study of communication, language evolution, kinship and classification. And they demonstrated that graph theory provides an analytical framework that is both subtle enough to preserve culturally specific relations and abstract enough to allow for genuine cross-cultural comparison. With graph theory, two common analytical problems in anthropology can be avoided: the problem of hiding cultural phenomena with weak cross-cultural generalizations, and the problem of making misleading comparisons based on incomparable levels of abstraction. -
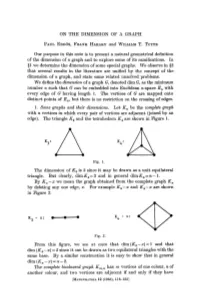
On the Dimension of a Graph
ON THE DIMENSION OF A GRAPH PAUL ERDOS, FRANK HARARY and WILLIAM T. TUTTE Our purpose in this note is to present a natural geometrical definition of the dimension of a graph and to explore some of its ramifications. In §1 we determine the dimension of some special graphs. We observe in §2 that several results in the literature are unified by the concept of the dimension of a graph, and state some related unsolved problems. We define the dimension of a graph 0, denoted dim 0, as the minimum number n such that G can be embedded into Euclidean re-space En with every edge of O having length 1. The vertices of G are mapped onto distinct points of En, but there is no restriction on the crossing of edges. 1. Some graphs and their dimensions. Let Kn be the complete graph with n vertices in which every pair of vertices are adjacent (joined by an edge). The triangle K3 and the tetrahedron Kt are shown in Figure 1. "3* Fig. 1. The dimension of Kz is 2 since it may be drawn as a unit equilateral triangle. But clearly, dimiT4 = 3 and in general dim Kn = n—1. By Kn — x -we mean the graph obtained from the complete graph Kn by deleting any one edge, x. For example K3 — x and Kt — x are shown in Figure 2. - x: - x: Fig. 2. From this figure, we see at once that dim (Ks — x) = 1 and that dim (K4 — x) = 2 since it can be drawn as two equilateral triangles with the same base.