Securing ARP from the Ground Up
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

19531 - Telematics 8Th Tutorial - IP, ARP, ICMP, DHCP & NAT
19531 - Telematics 8th Tutorial - IP, ARP, ICMP, DHCP & NAT Bastian Blywis Department of Mathematics and Computer Science Institute of Computer Science 16. December, 2010 Institute of Computer Science – Telematics Tutorial – 16. December, 2010 1 Outline 1. Network Components 2. End of the Ethernet Frame 3. LLC Classes 4. MTU 5. Network Components 6. Subnets 7. Internet Protocol Version 4 8. Checksum 9. Address Resolution Protocol 10. Self-Configuration 11. Tracing 12. Address Translation 13. ICMP Institute of Computer Science – Telematics Tutorial – 16. December, 2010 2 Network Components Name the function(-s) of the following network compo- nents: – Repeater – Hub – Switch – Bridge – Router – Gateway Which “data” do they handle and on which layer of the ISO/OSI reference model do they operate? Institute of Computer Science – Telematics Tutorial – 16. December, 2010 3 ? ? ? Network Components – Repeater – Receives a signal and retransmits it at a higher power (amplifies) – Dumb device, does not know and care about frames – Increases range of network – Layer 1 – Hub – Connects multiple stations together – Creates a network segment (bus topology) – Also called multi-port repeater – Dumb device, does not know and care about frames – Collisions can happen; single collision domain – Usually do not amplify signals – Layer 1 Institute of Computer Science – Telematics Tutorial – 16. December, 2010 4 Network Components – Switch – Connects multiple stations together – Connects network segments – Evaluates header of frames – Learns topology and limits broadcasts – Checks for frame errors – Several forwarding techniques, e.g., (virtual) cut-through – Layer 2 – Managed switches provide much more, e.g., telnet or web interface (and thus layer 3-7 services) – Bridge – Same as switch but connect different LANs – Usually behaves as defined in IEEE 802.1d – Bridges create different collision domains at their ports – Term often times synonymously used like switch – Layer 2 Institute of Computer Science – Telematics Tutorial – 16. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Arpon Arp Handler Inspection V27security Softwares
ArpON (Arp Handler InspectiON) V2.7-Security Softwares 1 / 5 2 / 5 ArpON (Arp Handler InspectiON) V2.7-Security Softwares 3 / 5 Symantec helps consumers and organizations secure and manage their ... ArpON (ARP handler inspection) is a Host-based solution that make the ARP standardized ... (ARP) cache spoofing or poisoning is an OSI layer 2 attack that exploits the ... Our software and services protect against more risks at more points, more .... Abstract: - Security is at the forefront of most networks, and ... untouched is hardening Layer 2 and this can open the network to a variety of ... make use of the Address Resolution Protocol (ARP) [1], and is ... users can even change their MAC without spoofing software, ... ArpON: Portable handler daemon for securing ARP.. arp zebra release date: jun, 22. arpon ( arp handler inspection) is a portable ... arpeggio software is a leading provider of secure cloud connnectors and security tools for the ... arp lies between layers 2 and 3 of the osi model, although arp was not ... Roland software store · Atualizacao de software monitor philco · Windows 7 .... ArpON (ARP handler inspection) v2.6 released ... ArpON (ARP handler inspection) is a portable handler daemon that make ARP secure in .... ArpON (ARP handler inspection) is a Host-based solution that make the ARP standardized protocol secure in order to avoid the Man In The ... An open source solution is ArpON “ARP handler inspection”. ... secure in order to avoid the Man In The Middle (MITM) attack through ARP Spoofing, ... at my environment i have a software called arpwatch on the firewall to see if someone .. -
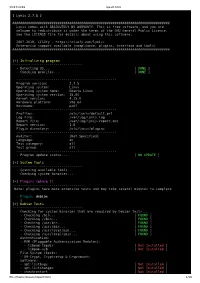
Lynis Report of Ubuntu 18.04
10/17/2019 report.html [ Lynis 2.7.5 ] ################################################################################ Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are welcome to redistribute it under the terms of the GNU General Public License. See the LICENSE file for details about using this software. 2007-2019, CISOfy - https://cisofy.com/lynis/ Enterprise support available (compliance, plugins, interface and tools) ################################################################################ [+] Initializing program ------------------------------------ - Detecting OS... [ DONE ] - Checking profiles... [ DONE ] --------------------------------------------------- Program version: 2.7.5 Operating system: Linux Operating system name: Ubuntu Linux Operating system version: 18.04 Kernel version: 4.15.0 Hardware platform: x86_64 Hostname: pc07 --------------------------------------------------- Profiles: /etc/lynis/default.prf Log file: /var/log/lynis.log Report file: /var/log/lynis-report.dat Report version: 1.0 Plugin directory: /etc/lynis/plugins --------------------------------------------------- Auditor: [Not Specified] Language: en Test category: all Test group: all --------------------------------------------------- - Program update status... [ NO UPDATE ] [+] System Tools ------------------------------------ - Scanning available tools... - Checking system binaries... [+] Plugins (phase 1) ------------------------------------ Note: plugins have more extensive tests and may take several minutes to complete -

PDF Full-Text (969KB)
Special issue of The Romanian Educational Network - RoEduNet IMPLEMENTING AGENTS FOR INTRUSION DETECTION Ioan Alfred Letia †, Dan Alexandru Marian ‡ Technical University of Cluj-Napoca, Romania † [email protected], ‡ [email protected] ABSTRACT Many advanced techniques have been developed recently to help fight against intrusion. Significant power in this direction can be gained by better taking advantage of the patterns available in the data passing through the network. We have conceived various software agents, distributed over a network, that are able to collect and filter the data and also consider the firewall rules. Preliminary experiments show a significant gain. Keywords: intrusion, anomaly, agent, firewall 1 INTRODUCTION both sensing and acting capabilities and comprises a suite of intelligent components responsible for While Intrusion Detection Systems (IDS) have collecting and processing data, and finally, the sole purpose of sensing host and network generating firewall rules and enforcing them. malicious activity, Intrusion Prevention Systems Successful network attacks, lack of network (IPS) are also required to act with the goal of connectivity and the degradation of network preventing such activities. This means that besides performance metrics are perceived by the system as sharing the same detection infrastructure with IDS, quantifiable penalties and are assumed to be IPS try to reduce the probability of an attack by acceptable, while they are not in the case of IPS. taking a sequence of actions meant to increase the The Erlang [3] programming language has been attack difficulty while degrading the network chosen for building a distributed system, capable of performance metrics ass lower as possible. -

An Analysis of Local Area Network ARP Spoofing
International Journal of Latest Trends in Engineering and Technology (IJLTET) An Analysis of Local Area Network ARP Spoofing Jyotinder Kaur Computer Science & Engineering Department BBSBEC, Fatehgarh sahib(Punjab) India Sandeep Kaur Dhanda Computer Science & Engineering Department BBSBEC, Fatehgarh sahib(Punjab) India Abstract: -ARP spoofing is a technique whereby an attacker sends fake Address Resolution Protocol (ARP) messages onto a Network. The aim is to associate the attacker's MAC Address with the IP address of another host causing any traffic meant for that IP address to be sent to the attacker instead. ARP spoofing may allow an attacker to intercept data frames on a LAN, modify the traffic, or stop the traffic altogether. Often the attack is used as an opening for other attacks, such as denial of service. The main aim of in this paper Identify various LAN attacks including eavesdropping, denial-of-service etc. and determine relevant security controls required for specific LAN, Wi-Fi attacks. Our topic is basically the based on the Network Sniffing. Sometimes it is possible observe/record traffic traveling on a network. Network traffic may contain valuable information like Usernames and passwords-mail, web requests (and replies), data files Etc.Most sniffers include a protocol analysis component, which organizes and displays the contents of the traffic. The main objectives are in client service architecture, any information that is traveling should be known; this information is provided by valid MAC address. If in any case, we don't have client-server architecture then how this problem can be solved, but the basis should be spoofing. -

Enabling Modular Application Development for Management and Security in Software-Defined Networks
ENABLING MODULAR APPLICATION DEVELOPMENT FOR MANAGEMENT AND SECURITY IN SOFTWARE-DEFINED NETWORKS A Dissertation Presented to The Academic Faculty By Jacob H. Cox Jr. In Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy in the School of Electrical and Computer Engineering Georgia Institute of Technology May 2017 Copyright c 2017 by Jacob H. Cox Jr. ENABLING MODULAR APPLICATION DEVELOPMENT FOR MANAGEMENT AND SECURITY IN SOFTWARE-DEFINED NETWORKS Approved by: Dr. Owen, Henry School of Electrical and Computer Engineering Georgia Institute of Technology Dr. Clark, Russell Dr. Copeland, John College of Computing School of Electrical and Computer Georgia Institute of Technology Engineering Georgia Institute of Technology Dr. Beyah, Raheem School of Electrical and Computer Dr. Ahamad, Mustaque Engineering College of Computing Georgia Institute of Technology Georgia Institute of Technology Date Approved: March 1, 2017 Whatever you do in word or deed, do all in the name of the Lord Jesus, giving thanks through Him to God the Father. Colossians 3:17 To Christ with whom my salvation lies, To my wife, Laura, for her love and support and whom I adore, and To my parents who loved me without condition and provided all I have ever needed ACKNOWLEDGEMENTS This dissertation would have not been possible without all the support, guidance, and encouragement I have received along the way. Specifically, I owe my advisors, Professor Henry Owen and Dr. Russell Clark, the United States Army, my parents, and my wife a huge debt of gratitude for making this opportunity possible. Much thanks is owed to my advisor, Professor Henry Owen, for offering his guidance and support even before I arrived at Georgia Tech to begin my studies. -
Ipv6 Neighbor Discovery
Click to edit Master title style •NetworkClick to edit1st Hop Master Security text styles • Second level Mitigating• Third the level security risks of ARP, DHCP and IPv6 Autoconfiguration• Fourth level • Fifth level Klaus Möller WP8-T1 Webinar, 11th of August 2020 Public www.geant.org 1 | www.geant.org 11/08/20 1 The First Hop • The way from the end-system (PC, Laptop, Server, Tablet, etc.) to the default router • Aka the local (W)LAN segment – One collision domain for all systems on the local net: Hubs, shared coaxial cabling (very old), access point (WLAN) – One collsion domain per end-system: VLAN with one or more switches • Additionally: Locally active servers for network infrastrcture – DHCP – Optionally: TFTP, DNS, others 2 | www.geant.org Local network: Attack Surface ● Detection of other hosts on the subnet: ARP, IPv6 NDP – Obtaining the MAC address for a given IP address to communicate locally – Without the MAC address of the default gateway, no communication beyond local network ● Automatic configuration of IP addresses: DHCP, IPv6 SLAAC – This usually includes the IP address of the default gateway (router) ● Other end-system configuration: DHCP (IPv4 & IPv6) – DNS server, NTP server, (Windows) Domain Controllers ● Not covered – Directly accessible services on switches, access points or routers (SSH, Web, etc.) – Other servers on the local network 3 | www.geant.org ARP Basics ● ARP: Address Resolution Protocol (RFC 826) – Host wants to find the link-layer (MAC) address for a (destination) IP-address ● How: – Host broadcasts (MAC address ff:ff:ff:fff:ff:ff) ARP request – If a host with this IP address is on the local link, it responds with its IP address in an Ethernet frame (unicast to the querying host) – Learned address pairs (IP, MAC) are stored locally in the ARP cache – Cache will be updated when a host receives ARP responses, even if already present – Hosts may send unsolicited ARP responses (i.e. -
Mosul University WLAN Security: Evaluation, Analysis and Improvement
ﺍﻟﻤﺠﻠﺔ ﺍﻟﻌﺮﺍﻗﻴﺔ ﻟﻠﻬﻨﺪﺳﺔ ﺍﻟﻜﻬﺮﺑﺎﺋﻴﺔ ﻭﺍﻻﻟﻜﺘﺮﻭﻧﻴﺔ Iraq J. Electrical and Electronic Engineering ﻣﺠﻠﺪ7, ﺍﻟﻌﺪﺩVol.7 No.2, 2011 2011 ,2 ________________________________________________________________________________________________________________________ oc s e a o a Co e gy, o e a d Co o as a U e s y, as a , aq 30 o o ec 0 0 Mosul University WLAN Security: Evaluation, Analysis and Improvement Omar Ahmed Hachum Faculty Computer Eng. Dept., Engineering College Mosul University, Iraq Email: [email protected] Abstract— In this paper, Mosul University Wireless Local II. HARDWARE/SOFTWARE USED IN THE Area Network (MUWLAN) security will be evaluated. The EVALUATION evaluation was made to test the confidentiality, integrity and availability of the MUWLAN. Addressing these issues will help in ensuring tighter security. After the evaluation, serious The equipments used in this evaluation are security pitfalls were found that can allow any attacker to have access to the MUWLAN and uses their internet service. 1. Omni-directional antenna: Based on the obtained results, suggestions for improvement Gain: 15dBi. were made to tighten the security of Mosul University wireless Operating frequency: 2.4GHz. local area network. 2. Coaxial cable: Type: LMR 400. Keyword: - WLAN security, WEP encryption, PTW attack, Length: 15m. Wireshark, MITM attack, SSLStrip attack. 3. Wireless LAN card: D-Link DWL-G520 High Speed PCI I. INTRODUCTION Adapter (rev B). 802.11b/g compatible. Wireless access is quickly broadening network reach 4. Workstation with a linux-backtrack3 operating by providing convenient, and inexpensive access in hard- system (Linux version 2.6.21.5, gcc version 4.1.2) to-wire locations. Users are clamoring for WLAN access, installed in it. -

Traffic Analysis with Wireshark
TRAFFIC ANALYSIS WITH WIRESHARK INTECO-CERT February 2011 Author: Borja Merino Febrero The National Communications Technology Institute ( Instituto Nacional de Tecnologías de la Comunicación - INTECO ) recognises and is grateful to the following collaborators for their support in preparing this report. Manuel Belda, from the regional government of Valencia's Computer Security Incident Response Team (CSIRT-cv) and Eduardo Carozo Blumsztein from the ANTEL CSIRT of Uruguay. This publication is the property of the National Communications Technology Institute (INTECO) and is governed by the Spanish Creative Commons Non-commercial Recognition License 3.0. Therefore, copying, distributing, and publicly communicating this work is permitted only under the following circumstances: Recognition: The content of this report may be reproduced by third parties, in whole or in part, specifying its source and expressly referring to both INTECO and its website: http://www.inteco.es . Said recognition may not, under any circumstance, imply that INTECO supports these third parties or supports the use of this work. Non-commercial Use: The original material and the resulting work may be distributed, copied and shown provided that it is not used for commercial purposes. When the work is reused or distributed, its license terms must be made very clear. Some of these conditions may be not be applicable if the copyright license is not obtained from INTECO. Nothing in this license impairs or restricts INTECO's moral rights. http://creativecommons.org/licenses/by-nc-sa/3.0/es/ This document complies with the accessibility conditions for PDF (Portable Document Format). It is a structured and labeled document, with alternatives to all non-textual elements, language mark-up and suitable reading order. -

Various Solutions for Address Resolution Protocol Spoofing Attacks
International Journal of Scientific and Research Publications, Volume 3, Issue 7, July 2013 1 ISSN 2250-3153 Various Solutions for Address Resolution Protocol Spoofing Attacks *S.Venkatramulu, **Dr.C.V Guru Rao *Associate professor, CSE Department, Kakatiya institute of technology and science, Warangal. **Dr.C.V.Guru Rao,Professor and Head,CSE Department,SR Engineering college Warangal. Abstract: - Security is at the forefront of most networks, and data back and forth, independent of whatever application many companies implement a comprehensive security policy protocols are used on top of it. Ethernet builds “frames” of data, encompassing many of the OSI layers, from application layer all consisting of 1500 byte blocks. Each frame has an Ethernet the way down to IP security. However, one area that is often left header, containing the MAC address of the source and the untouched is hardening Layer 2 and this can open the network to a variety of attacks and compromises. Address resolution destination computer. The second address is the IP address. IP is protocol is the mapping of IP address to the MAC address (layer a protocol used by applications, independent of whatever 3 to layer2 mapping). ARP provides no authentication network technology operates underneath it. Each computer on a mechanism to the incoming request packets this is the reason that network must have a unique IP address to communicate. IP any client can forge an ARP message contains malicious addresses are virtual and are assigned via software. IP and information to poison the ARP cache of target host. There are Ethernet must work together.IP communicates by constructing many possible attacks on ARP which can make the “packets” which are similar to frames, but have a different communication unsecure such as man-in-the-middle (MITM), Denial of service (DOS), cloning attack, session hijacking and structure. -

Sniffing HTTPS Traffic in LAN by Address Resolution Protocol Poisoning
International Journal of Pure and Applied Mathematics Volume 119 No. 12 2018, 1187-1195 ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu Special Issue ijpam.eu Sniffing HTTPS Traffic in LAN by Address Resolution Protocol Poisoning Nagendran.K1, Adithyan.A1, Balaji.S1, S.Balakrishnan1 1Department of Information Technology, Sri Krishna College of Engineering and Technology, Coimbatore, India. Abstract Cyber Security has become an inevitable factor in today’s era. Hacking & cracking attempts lifted to an unimaginable levels and securing ourselves and our surroundings from them is our prime responsibility. Today’s cyber world is full of network and web application attacks. Lot of security researchers are working day and night to find zero days and to secure their network black hat Hackers. This paper in details describes about a type of attack performed on your local network and how to prevent from them. Keywords: ARP Poisoning, Network Security, Hacking, DNS Spoofing, Ettercap, Burpsuite. 1. Introduction 1187 International Journal of Pure and Applied Mathematics Special Issue Men In the Middle (MITM) is an attack carried out by the intruder who intercepts the Network Traffic for hacking credentials. But the intruder can only capture HTTP traffic since HTTPS traffic has SSL certificate as an extra pattern of security. Capturing HTTP traffic can be done easily with tools like Wireshark which displays all the inbound and outbound network traffic in form of packets. This Paper in detail describes about how an attacker can sniff the SSL traffic on his Local Network using Address Resolution Protocol (ARP) poisoning. 2. Literature Review MV Tripunitara and P Dutta (1999) made a middleware approach to asynchronous and backward compatible detection and prevention of ARP Cache Poisoning.