Evaluation of Wireguard and Openvpn VPN Solutions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Flexgw Ipsec VPN Image User Guide
FlexGW IPsec VPN Image User Guide Zhuyun Information Technology Co.,Ltd. www.cloudcare.cn Zhuyun Information Technology Co.,Ltd. Contents .......................................................................................................... .................................................................................................................. 1 Introduction 4 1.1 Software Compon.e..n..t.s................................................................................................................... 4 1.2 Login Description ................................................................................................................... 4 1.3 Function Description ....................................................................................................5 1.4 Typical Scenarios Des..c..r..i.p..t..i.o..n......................................................................................................5 1.5 Program Description .................................................................................6 1.6 Software Operation Command Summary ............................... 7 ............................................................................................................... 2 IPSec Site-to-Site VPN User Guide (VPC network scenario) 8 2.1 Start IPSec VPN.s..e..r..v..i.c..e.................................................................................................................8 2.2 Add new tunnel ................................................................................................................. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -
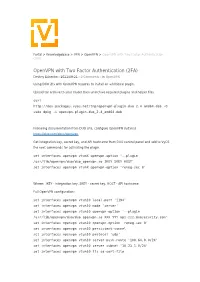
Openvpn with Two-Factor Authentication (2FA)
Portal > Knowledgebase > VPN > OpenVPN > OpenVPN with Two Factor Authentication (2FA) OpenVPN with Two Factor Authentication (2FA) Dmitriy Eshenko - 2021-09-21 - 0 Comments - in OpenVPN Using DUO 2fa with OpenVPN requires to install an additional plugin. Upload tar archive to your router then unarchive required plugins and helper files curl http://dev.packages.vyos.net/tmp/openvpn-plugin-duo_2.4_amd64.deb -O sudo dpkg -i openvpn-plugin-duo_2.4_amd64.deb Following documentation from DUO site, configure OpenVPN instance https://duo.com/docs/openvpn Get integration key, secret key, and API hostname from DUO control panel and add to VyOS the next commands for activating the plugin. set interfaces openvpn vtunX openvpn-option '--plugin /usr/lib/openvpn/duo/duo_openvpn.so IKEY SKEY HOST' set interfaces openvpn vtunX openvpn-option 'reneg-sec 0' Where: IKEY - integration key, SKEY - secret key, HOST - API hostname Full OpenVPN configuration: set interfaces openvpn vtun10 local-port '1194' set interfaces openvpn vtun10 mode 'server' set interfaces openvpn vtun10 openvpn-option '--plugin /usr/lib/openvpn/duo/duo_openvpn.so XXX YYY api-zzz.duosecurity.com' set interfaces openvpn vtun10 openvpn-option 'reneg-sec 0' set interfaces openvpn vtun10 persistent-tunnel set interfaces openvpn vtun10 protocol 'udp' set interfaces openvpn vtun10 server push-route '100.64.0.0/24' set interfaces openvpn vtun10 server subnet '10.23.1.0/24' set interfaces openvpn vtun10 tls ca-cert-file '/config/auth/ovpn/ca.crt' set interfaces openvpn vtun10 tls cert-file '/config/auth/ovpn/central.crt' set interfaces openvpn vtun10 tls crl-file '/config/auth/ovpn/crl.pem' set interfaces openvpn vtun10 tls dh-file '/config/auth/ovpn/dh.pem' set interfaces openvpn vtun10 tls key-file '/config/auth/ovpn/central.key' How to generate cryptographic materials described by the following link https://support.vyos.io/en/kb/articles/using-easy-rsa-to-generate-x-509-certificates-and-keys -2. -

Enabling TPM Based System Security Features
Enabling TPM based system security features Andreas Fuchs <[email protected]> Who am I ? ● 13 year on/off TPMs ● Fraunhofer SIT: Trustworthy Platforms ● TCG-member: TPM Software Stack WG ● Maintainer – tpm2-tss: The libraries – tpm2-tss-engine: The openssl engine – tpm2-totp: Computer-to-user attestation (mjg’s tpm-totp reimplemented for 2.0) 2 The hardware stack ● Trusted Platform Module (TPM) 2.0 – Smartcard-like capabilities but soldered in – Remote Attestation capabilities – As separate chip (LPC, SPI, I²C) – In Southbridge / Firmware – Via TEEs/TrustZone, etc – Thanks to Windows-Logos in every PC ● CPU – OS, TSS 2.0, where the fun is... 3 The TPM Software Stack 2.0 ● Kernel exposes /dev/tpm0 with byte buffers ● tpm2-tss is like the mesa of TCG specs ● TCG specifications: – TPM spec for functionality – TSS spec for software API ● tpm2-tss implements the glue ● Then comes core module / application integration – Think GDK, but OpenSSL – Think godot, but pkcs11 – Think wayland, but cryptsetup 4 The TSS APIs System API (sys) Enhanced SYS (esys) Feature API (FAPI) • 1:1 to TPM2 cmds • Automate crypto for • Spec in draft form HMAC / encrypted • TBimplemented • Cmd / Rsp sessions • No custom typedefs U serialization • Dynamic TCTI • JSON interfaces s • No file I/O loading • Provides Policy e • No crypto • Memory allocations language r • No heap / malloc • No file I/O • Provides keystore S p TPM Command Transmission Interface (tss2-tcti) p a Abstract command / response mechanism, • No crypto, heap, file I/O a Decouple APIs -
Download Secure Vpn for Android Download Secure Vpn for Android
download secure vpn for android Download secure vpn for android. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Cloudflare Ray ID: 6686f3ad9d2384a4 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download secure vpn for android. Password management for Android. Free account authenticator. Free Android private file storage. Free app for extra security. A powerful security tool for Android. Free VPN for mobile devices. Paid VPN service. Free VPN server access app. Free VPN for Android. Security app for mobile. Top Security & VPN. Add Us To Your Social Channels. Subscribe. Upgrade your lifestyle. Digital Trends helps readers keep tabs on the fast-paced world of tech with all the latest news, fun product reviews, insightful editorials, and one- of-a-kind sneak peeks. Digital Trends may earn a commission when you buy through links on our site. Download secure vpn for android. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. -

N2N: a Layer Two Peer-To-Peer VPN
N2N: A Layer Two Peer-to-Peer VPN Luca Deri1, Richard Andrews2 ntop.org, Pisa, Italy1 Symstream Technologies, Melbourne, Australia2 {deri, andrews}@ntop.org Abstract. The Internet was originally designed as a flat data network delivering a multitude of protocols and services between equal peers. Currently, after an explosive growth fostered by enormous and heterogeneous economic interests, it has become a constrained network severely enforcing client-server communication where addressing plans, packet routing, security policies and users’ reachability are almost entirely managed and limited by access providers. From the user’s perspective, the Internet is not an open transport system, but rather a telephony-like communication medium for content consumption. This paper describes the design and implementation of a new type of peer-to- peer virtual private network that can allow users to overcome some of these limitations. N2N users can create and manage their own secure and geographically distributed overlay network without the need for central administration, typical of most virtual private network systems. Keywords: Virtual private network, peer-to-peer, network overlay. 1. Motivation and Scope of Work Irony pervades many pages of history, and computing history is no exception. Once personal computing had won the market battle against mainframe-based computing, the commercial evolution of the Internet in the nineties stepped the computing world back to a substantially rigid client-server scheme. While it is true that the today’s Internet serves as a good transport system for supplying a plethora of data interchange services, virtually all of them are delivered by a client-server model, whether they are centralised or distributed, pay-per-use or virtually free [1]. -

Express Vpn for Windows 10 Download How to Get an Expressvpn Free Trial Account – 2021 Hack
express vpn for windows 10 download How to Get an ExpressVPN Free Trial Account – 2021 Hack. The best way to make sure ExpressVPN is the right VPN for you is to take it for a test drive before you commit and make sure its features fit your needs. Unlike some other VPNs, ExpressVPN doesn’t have a standard free trial. But it does have a no-questions-asked, 30-day money-back guarantee. So you can test out the VPN with no limitations, risk-free. If at any point during those 30 days, you decide that ExpressVPN isn’t right for you, you can just request a refund. This is super simple: I’ve tested it using several accounts, and got my money back every time. ExpressVPN Free Trial : Quick Setup Guide. It’s easy to set up ExpressVPN and get your 30 days risk-free. Here’s a step-by-step walkthrough that will have you ready in minutes. Head over to the ExpressVPN free trial page, and select, “Start Your Trial Today” to go right to their pricing list. Choose your subscription plan length, and then enter your email address and payment details. Note that longer plans are much cheaper. ExpressVPN’s long-term plans are the most affordable. It’s easy to download the app to your device. The set up for the ExpressVPN app is simple, and fast. Request a refund via live chat. Try ExpressVPN risk-free for 30-days. Free Trial Vs. Money-Back Guarantee. The trial period for ExpressVPN is really a 30-day money-back guarantee, but this is better than a free trial. -

An Investigation Into the Security and Privacy of Ios VPN Applications
An Investigation Into the Security and Privacy of iOS VPN Applications Jack Wilson Division of Cybersecurity School of Design and Informatics Abertay University, Dundee A thesis submitted for the degree of Bachelor of Science with Honours in Ethical Hacking 1st May 2018 Word Count: 11,448 Abstract Due to the increasing number of recommendations for people to use VPN’s for privacy reasons, more app developers are creating VPN apps and publishing them on the Apple App Store and Google Play Store. In this ‘gold rush’, apps are being developed quickly and, in turn, not being developed with security fully in mind. This paper investigated a selection of free VPN applications available on the Apple App Store (for iOS devices) and test the apps for security and privacy. This includes testing for any traffic being transmitted over plain HTTP, DNS leakage and transmission of personally-identifiable information (such as phone number, IMEI 1, email address, MAC address) and evaluating the security of the tunnelling protocol used by the VPN. The testing methodology involved installing free VPN apps on a test device (an iPhone 6 running iOS 11), simulating network traffic for a pre-defined period of time and capturing the traffic (either through ARP spoofing, or through a proxy program such as Burpsuite). This allows for all traffic to be analysed to check for anything being sent without encryption. Other issues that often cause de-anonymisation with VPN applications such as DNS leakage can be tested using websites such as dnsleaktest.com. The research found several common security issues with the VPN applications that were tested, with a large majority of the applications tested failing to implement HTTPS. -

Test-Beds and Guidelines for Securing Iot Products and for Secure Set-Up Production Environments
IoT4CPS – Trustworthy IoT for CPS FFG - ICT of the Future Project No. 863129 Deliverable D7.4 Test-beds and guidelines for securing IoT products and for secure set-up production environments The IoT4CPS Consortium: AIT – Austrian Institute of Technology GmbH AVL – AVL List GmbH DUK – Donau-Universit t Krems I!AT – In"neon Technologies Austria AG #KU – JK Universit t Lin$ / Institute for &ervasive 'om(uting #) – Joanneum )esearch !orschungsgesellschaft mbH *+KIA – No,ia -olutions an. Net/or,s 0sterreich GmbH *1& – *1& -emicon.uctors Austria GmbH -2A – -2A )esearch GmbH -)!G – -al$burg )esearch !orschungsgesellschaft -''H – -oft/are 'om(etence 'enter Hagenberg GmbH -AG0 – -iemens AG 0sterreich TTTech – TTTech 'om(utertechni, AG IAIK – TU Gra$ / Institute for A((lie. Information &rocessing an. 'ommunications ITI – TU Gra$ / Institute for Technical Informatics TU3 – TU 3ien / Institute of 'om(uter 4ngineering 1*4T – 1-Net -ervices GmbH © Copyright 2020, the Members of the IoT4CPS Consortium !or more information on this .ocument or the IoT5'&- (ro6ect, (lease contact8 9ario Drobics7 AIT Austrian Institute of Technology7 mario:.robics@ait:ac:at IoT4C&- – <=>?@A Test-be.s an. guidelines for securing IoT (ro.ucts an. for secure set-up (ro.uction environments Dissemination level8 &U2LI' Document Control Title8 Test-be.s an. gui.elines for securing IoT (ro.ucts an. for secure set-u( (ro.uction environments Ty(e8 &ublic 4.itorBsC8 Katharina Kloiber 4-mail8 ,,;D-net:at AuthorBsC8 Katharina Kloiber, Ni,olaus DEr,, -ilvio -tern )evie/erBsC8 -te(hanie von )E.en, Violeta Dam6anovic, Leo Ha((-2otler Doc ID8 DF:5 Amendment History Version Date Author Description/Comments VG:? ?>:G?:@G@G -ilvio -tern Technology Analysis VG:@ ?G:G>:@G@G -ilvio -tern &ossible )esearch !iel.s for the -2I--ystem VG:> >?:G<:@G@G Katharina Kloiber Initial version (re(are. -

Iclab: a Global, Longitudinal Internet Censorship Measurement Platform
ICLab: A Global, Longitudinal Internet Censorship Measurement Platform Arian Akhavan Niaki∗y Shinyoung Cho∗yz Zachary Weinberg∗x Nguyen Phong Hoangz Abbas Razaghpanahz Nicolas Christinx Phillipa Gilly yUniversity of Massachusetts, Amherst zStony Brook University xCarnegie Mellon University {arian, shicho, phillipa}@cs.umass.edu {shicho, nghoang, arazaghpanah}@cs.stonybrook.edu {zackw, nicolasc}@cmu.edu Abstract—Researchers have studied Internet censorship for remains elusive. We highlight three key challenges that must nearly as long as attempts to censor contents have taken place. be addressed to make progress in this space: Most studies have however been limited to a short period of time and/or a few countries; the few exceptions have traded off detail Challenge 1: Access to Vantage Points. With few ex- for breadth of coverage. Collecting enough data for a compre- ceptions,1 measuring Internet censorship requires access to hensive, global, longitudinal perspective remains challenging. “vantage point” hosts within the region of interest. In this work, we present ICLab, an Internet measurement The simplest way to obtain vantage points is to recruit platform specialized for censorship research. It achieves a new balance between breadth of coverage and detail of measurements, volunteers [37], [43], [73], [80]. Volunteers can run software by using commercial VPNs as vantage points distributed around that performs arbitrary network measurements from each the world. ICLab has been operated continuously since late vantage point, but recruiting more than a few volunteers per 2016. It can currently detect DNS manipulation and TCP packet country and retaining them for long periods is difficult. Further, injection, and overt “block pages” however they are delivered. -

Xmind ZEN 9.1.3 Crack FREE Download
1 / 4 XMind ZEN 9.1.3 Crack FREE Download Download XMind ZEN 9.2.1 Build Windows / 9.1.3 macOS for free at ... Version 9.2.1 is cracked, then install the program and click Skip in the Login window.. Adobe Premiere Pro CC 2019 13.1.2 – For macOS Cracked With Serial Number.. Free Download XMind ZEN 9.1.3 Build. 201812101752 Win / macOS Cracked .... 3 Crack + Serial Key Free Download. Malwarebytes 4.2.3 Crack Real-time safety of all threats very effectively. This is a .... ZW3D 2019 SP2 Download 32-64 Bit For Windows. The Powerful engineering ... XMind ZEN 9.1.3 Download. Free Download Keysight .... With this app, you can download online maps, digital maps and even ... Tableau Desktop Pro 2019.4.0 Win + Crack · XMind ZEN 9.2.0 Build .... Download Free XMind: ZEN 9.1.3 Build 201812101752 for Mac on Mac Torrent Download. XMind: ZEN 9.1.3 Build 201812101752 is a .... XMind 8 Pro 3 7 6 Mac Crack Full version free download is the latest version of the most advanced and Popular Mind ... XMind ZEN for Mac 9.1.3 Serial Key ... Download Nero KnowHow for PC - free download Nero KnowHow for ... The full version comes in single user and a family variant with the former costing ... Download XMind ZEN 9.2.1 Build Windows / 9.1.3 macOS for free at .... XMind ZEN Crack 10.3.0 With Keygen Full Torrent Download 2021 For PC · XMind Crack 9.1.3 With Keygen Full Torrent Download 2019 For PC. -

How to Download Torrent Anonymously How to Download Torrent Anonymously
how to download torrent anonymously How to download torrent anonymously. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 66b6c3aaaba884c8 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download Torrents Anonymously: 6 Safe And Easy Ways. Who doesn’t want to know how to download torrents anonymously? The thing is, in order to download torrents anonymously you don’t need to have a lot of technical know-how. All you need to download torrents anonymously is some grit and a computer with an internet connection. The technology world never remains the same. In fact, new development and discoveries come to the surface of this industry every day. They also come into the attention of online users every year. Moreover, this allows us to do much more than we could do in the past, in faster and easier ways. A highly relevant aspect to mention at this stage is that: Now we can also download torrents anonymously from best torrent sites.