Core Course Syllabi of Member Programs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Update 22 November 2017 Best Game Yang Baru Masuk
Downloaded from: justpaste.it/premiumlink UPDATE 22 NOVEMBER 2017 BEST GAME YANG BARU MASUK DAFTAR LIST NieR Automata - (10DVD) Full CPY Releases REKOMENDASI SPESIFIKASI PC PALING RENDAH BISA MAIN GAME BERAT/BESAR TAHUN 2017 SET LOW / MID FPS 30 KURANG LEBIH VERSI INTEL DAN NVIDIA TERENDAH: PROCIE: INTEL I3 RAM: 6GB VGA: NVIDIA GTX 660 WINDOWS 7 VERSI AMD TERENDAH: PROCIE: AMD A6-7400K RAM: 6GB VGA: AMD R7 360 WINDOWS 7 REKOMENDASI SPESIFIKASI PC PALING STABIL FPS 40-+ SET HIGH / ULTRA: PROCIE INTEL I7 6700 / AMD RYZEN 7 1700 RAM 16GB DUAL CHANNEL / QUAD CHANNEL DDR3 / UP VGA NVIDIA GTX 1060 6GB / AMD RX 570 HARDDISK SEAGATE / WD, SATA 6GB/S 5400RPM / UP SSD OPERATING SYSTEM SANDISK / SAMSUNG MOTHERBOARD MSI / ASUS / GIGABYTE / ASROCK PSU 500W CORSAIR / ENERMAX WINDOWS 10 CEK SPESIFIKASI PC UNTUK GAME YANG ANDA INGIN MAINKAN http://www.game-debate.com/ ------------------------------------------------------------------------------------------------------------------------------ -------- LANGKAH COPY & INSTAL PALING LANCAR KLIK DI SINI Order game lain kirim email ke [email protected] dan akan kami berikan link menuju halaman pembelian game tersebut di Tokopedia / Kaskus ------------------------------------------------------------------------------------------------------------------------------ -------- Download List Untuk di simpan Offline LINK DOWNLOAD TIDAK BISA DI BUKA ATAU ERROR, COBA LINK DOWNLOAD LAIN SEMUA SITUS DI BAWAH INI SUDAH DI VERIFIKASI DAN SUDAH SAYA COBA DOWNLOAD SENDIRI, ADALAH TEMPAT DOWNLOAD PALING MUDAH OPENLOAD.CO CLICKNUPLOAD.ORG FILECLOUD.IO SENDIT.CLOUD SENDSPACE.COM UPLOD.CC UPPIT.COM ZIPPYSHARE.COM DOWNACE.COM FILEBEBO.COM SOLIDFILES.COM TUSFILES.NET ------------------------------------------------------------------------------------------------------------------------------ -------- List Online: TEKAN CTR L+F UNTUK MENCARI JUDUL GAME EVOLUSI GRAFIK GAME DAN GAMEPLAY MENINGKAT MULAI TAHUN 2013 UNTUK MENCARI GAME TAHUN 2013 KE ATAS TEKAN CTRL+F KETIK 12 NOVEMBER 2013 1. -
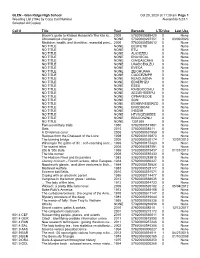
Glen Ridge High School 1 Page Oct 20, 2020 at 11:39 Am Weeding List
GLEN - Glen Ridge High School Oct 20, 2020 at 11:39 am 1Page Weeding List (164) by Copy Call Number Alexandria 6.23.1 Selected:All Copies Call # Title Year Barcode LTD Use Last Use Bloom's guide to Khaled Hosseini's The kite ru... 2009 57820000588429 0 None Chromebook charger NONE 57820000297351 3 03/09/2020 Medicine, health, and bioethics : essential prim... 2006 57820000538013 0 None NO TITLE NONE EEUFET8I 0 None NO TITLE NONE ETU 0 None NO TITLE NONE AUCIEZEU 0 None NO TITLE NONE ENA1GCAL 0 None NO TITLE NONE OIAIQA8CNH5 0 None NO TITLE NONE UAADCEGLZU 0 None NO TITLE NONE EVECA 0 None NO TITLE NONE ZEIOHUAAA 0 None NO TITLE NONE CUOCEZMPE 0 None NO TITLE NONE KEAOUADNA 0 None NO TITLE NONE ED8ERHZU 0 None NO TITLE NONE ESEU 0 None NO TITLE NONE RAIQGCCOAU 0 None NO TITLE NONE AEZJEHSSSPU 0 None NO TITLE NONE CPNARECOE 0 None NO TITLE NONE SON 0 None NO TITLE NONE EEHBVNEUERZO 0 None NO TITLE NONE ENODBOAII 0 None NO TITLE NONE IHBDIIH 0 None NO TITLE NONE HTVUQZUKEEE 0 None NO TITLE NONE BBACCNZNU 0 None NO TITLE NONE 1301309 0 None Famous military trials 1980 57820000517881 0 None Geis 2016 5782000058211 0 None A Christmas carol 2008 57820000587959 0 None Recipes from the Chateaux of the Loire 1998 57820000169873 0 None The burning bridge 2005 57820000520174 7 12/07/2015 Winning in the game of life : self-coaching secr... 1999 57820000157423 0 None The scarlet letter 2006 57820000587991 0 None 20s & '30s style 1989 57820000079437 2 01/31/2013 The kite runner 2008 57820000585433 0 None The Hudson River and its painters 1983 57820000283815 0 None Literary criticism - French writers, other Europea...1984 57820000080427 0 None Napoleon's glands : and other ventures in bioh.. -

Steam Browser Protocol Insecurity (Whenlocalbugsgoremote)
STEAM BROWSER PROTOCOL INSECURITY (WHEN LOCAL BUGS GO REMOTE) Luigi Auriemma1 and Donato Ferrante2 ReVuln http://revuln.com [email protected] http://twitter.com/revuln 15 October 2012 Abstract In this paper we will uncover and demonstrate a novel and interesting way to convert local bugs and features in remotely exploitable security vulnerabilities by using the well known Steam3 platform as attack vector against remote systems. 1S TEAM From Wikipedia: "Steam is a digital distribution, digital rights management, multi- player and communications platform developed by Valve Corporation". With Steam users can buy games, download demos and free-to-play games, find multiplayer matches, communicate with other users, share stats and so on. Steam is the digital delivery platform having the biggest user base (approximately 50 millions users) and supporting several platforms: Windows, MacOS, PS3, mobile devices and Linux. 2S TEAM BROWSER PROTOCOL Steam, like other software, uses its own URL handler to enhance experience by integrating web-based functionality directly in its own platform. Steam uses the steam:// URL protocol in order to: Install and uninstall games • Backup, validate and defrag game files • Connect to game servers • Run games • Reach various pages and sections where it’s possible to buy or activate games, • download tools, read news, check user profiles and so on The Steam Browser Protocol has several commands, most of them are listed on Valve4 website along with a non-updated list5 of games using Steam as platform. The list of commands is not a complete reference of all the commands available 1http://twitter.com/luigi_auriemma 2http://twitter.com/dntbug 3 http://steampowered.com 4 https://developer.valvesoftware.com/wiki/Steam_browser_protocol 5 https://developer.valvesoftware.com/wiki/Steam_Application_ID ReVuln - http://revuln.com page 1 of 10 with the Steam Browser Protocol, as several commands are partially documented or not documented at all on Valve website. -
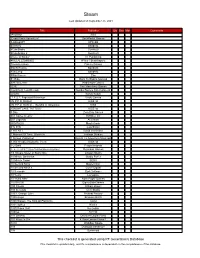
This Checklist Is Generated Using RF Generation's Database This Checklist Is Updated Daily, and It's Completeness Is Dependent on the Completeness of the Database
Steam Last Updated on September 25, 2021 Title Publisher Qty Box Man Comments !AnyWay! SGS !Dead Pixels Adventure! DackPostal Games !LABrpgUP! UPandQ #Archery Bandello #CuteSnake Sunrise9 #CuteSnake 2 Sunrise9 #Have A Sticker VT Publishing #KILLALLZOMBIES 8Floor / Beatshapers #monstercakes Paleno Games #SelfieTennis Bandello #SkiJump Bandello #WarGames Eko $1 Ride Back To Basics Gaming √Letter Kadokawa Games .EXE Two Man Army Games .hack//G.U. Last Recode Bandai Namco Entertainment .projekt Kyrylo Kuzyk .T.E.S.T: Expected Behaviour Veslo Games //N.P.P.D. RUSH// KISS ltd //N.P.P.D. RUSH// - The Milk of Ultraviolet KISS //SNOWFLAKE TATTOO// KISS ltd 0 Day Zero Day Games 001 Game Creator SoftWeir Inc 007 Legends Activision 0RBITALIS Mastertronic 0°N 0°W Colorfiction 1 HIT KILL David Vecchione 1 Moment Of Time: Silentville Jetdogs Studios 1 Screen Platformer Return To Adventure Mountain 1,000 Heads Among the Trees KISS ltd 1-2-Swift Pitaya Network 1... 2... 3... KICK IT! (Drop That Beat Like an Ugly Baby) Dejobaan Games 1/4 Square Meter of Starry Sky Lingtan Studio 10 Minute Barbarian Studio Puffer 10 Minute Tower SEGA 10 Second Ninja Mastertronic 10 Second Ninja X Curve Digital 10 Seconds Zynk Software 10 Years Lionsgate 10 Years After Rock Paper Games 10,000,000 EightyEightGames 100 Chests William Brown 100 Seconds Cien Studio 100% Orange Juice Fruitbat Factory 1000 Amps Brandon Brizzi 1000 Stages: The King Of Platforms ltaoist 1001 Spikes Nicalis 100ft Robot Golf No Goblin 100nya .M.Y.W. 101 Secrets Devolver Digital Films 101 Ways to Die 4 Door Lemon Vision 1 1010 WalkBoy Studio 103 Dystopia Interactive 10k Dynamoid This checklist is generated using RF Generation's Database This checklist is updated daily, and it's completeness is dependent on the completeness of the database. -

Comparing the Literatures: Literary Studies in a Global
David Damrosch Comparing the Lit er a tures Literary Studies in a Global Age PRINCE TON UNIVERSITY PRESS Prince ton and Oxford Copyright © 2020 by Prince ton University Press Requests for permission to reproduce material from this work should be sent to permissions@press . princeton . edu Published by Prince ton University Press 41 William Street, Prince ton, New Jersey 08540 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press . princeton . edu All Rights Reserved ISBN 978-0-691-13499-4 ISBN (e- book) 978-0-691-20128-3 Library of Congress Control Number: 2019956207 British Library Cataloging- in- Publication Data is available Editorial: Anne Savarese and Jenny Tan Production Editorial: Kathleen Ciof Text and Jacket Design: Carmina Alvarez Production: Brigid Ackerman Publicity: Alyssa Sanford and Katie Lewis Copyeditor: Daniel Simon Jacket art: From Discussing the Divine Comedy with Dante, by Dai Dudu, Li Tiezi, and Zhang An (2006). Courtesy of the artists This book has been composed in Charis Printed on acid- free paper. ∞ Printed in the United States of Amer i ca 1 3 5 7 9 10 8 6 4 2 Contents List of Illustrations vii Acknowl edgments ix Introduction 1 1 Origins 12 2 Emigrations 50 3 Politics 84 4 Theories 122 5 Languages 165 6 Lit er a tures 207 7 Worlds 253 8 Comparisons 303 Conclusion: Rebirth of a Discipline 334 Bibliography 349 Index 375 Illustrations 1. Acta Comparationis Litterarum Universarum 36 2. Lin Yutang with Lin Tai-yi demonstrating his typewriter 61 3. “ Great Moments in Lit Crit,” Voice Literary Supplement, 1988 123 4. Paul de Man, before and after 1987 132 5.