Mac in the Enterprise IT Configuration Guide for Your Mac Evaluation and Deployment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Learn Yosemite OS X from PCM's Apple Experts
Learn Yosemite OS X from PCM’s Apple Experts Yosemite 101: OS X Support Essentials Give PCM the opportunity to train your team to support users of Apple’s Mac OS X Yosemite. Our Apple certified trainers are ready to come to your location and provide PCM’s Apple certified trainers will teach your team Yosemite OS X fundamentals and how to be efficient with you with invaluable Yosemite tools and resources. hands-on instruction. OS X Yosemite Support Essentials is a three-day, Who Should Attend hands-on course that provides an in-depth explo- • Help desk specialists, technical coordinators, ration of troubleshooting on Mac OS X v10.10 Yo- service technicians, and others who support semite. This course is designed to give you a tour Mac users. of the breadth of functionality of Mac OS X v10.10 • Technical support personnel in businesses that Yosemite and the best methods for effectively use Macs. supporting users of Mac OS X v10.10 Yosemite • Technical coordinators or power users who systems. The course is a combination of lectures manage networks of computers running and hands-on case study exercises that provide Mac OS X — such as teachers and technology practical real-world experience. specialists who manage networks or computer labs. At your location For a class at your location, PCM will provide an What You Will Learn Apple Certified Trainer, all the student materials, • The troubleshooting process and how to and an exam voucher for each attendee (up to become more efficient with available tools 6 students included in price). -

Dropdmg 3.6.2 Manual
DropDMG 3.6.2 Manual C-Command Software c-command.com February 16, 2021 Contents 1 Introduction 4 1.1 Feature List..............................................4 2 Installing and Updating 6 2.1 Requirements.............................................6 2.2 Installing DropDMG.........................................7 2.3 Updating From a Previous Version.................................7 2.4 Reinstalling a Fresh Copy......................................8 2.5 Uninstalling DropDMG.......................................9 2.6 Security & Privacy Access......................................9 3 Using DropDMG 13 3.1 Basics................................................. 13 3.2 Making a Bootable Device Image of a Hard Drive......................... 14 3.3 Backing Up Your Files to CD/DVD................................ 16 3.4 Burning Backups of CDs/DVDs................................... 17 3.5 Restoring Files and Disks...................................... 18 3.6 Making Images With Background Pictures............................. 19 3.7 Protecting Your Files With Encryption............................... 20 3.8 Transferring Files Securely...................................... 21 3.9 Sharing Licenses and Layouts.................................... 21 3.10 Splitting a File or Folder Into Pieces................................ 22 3.11 Creating a DropDMG Quick Action................................ 22 4 Menus 23 4.1 The DropDMG Menu........................................ 23 4.1.1 About DropDMG...................................... 23 4.1.2 Software -

Best Practices for Integrating OS X with Active Directory
Apple Technical White Paper Best Practices for Integrating OS X with Active Directory OS X Mountain Lion v10.8 Contents Introduction ........................................................................................................................3 How to Integrate OS X with Active Directory .......................................................4 Enterprise Integration Challenges .............................................................................7 Deployment Strategies ..................................................................................................9 Home Directories ..............................................................................................................10 Conclusion ...........................................................................................................................11 Appendix A: More Information ....................................................................................12 Appendix B: Third-Party Add-on Solutions ............................................................13 2 Apple Technical White Paper Best Practices for Integrating OS X with Active Directory Introduction Apple’s support for Active Directory within OS X enables Mac clients and servers to integrate smoothly into existing Active Directory environments, and provides the option of deploying a single, directory services infrastructure that can support both Mac and Windows clients. Apple’s Built-in Solution Large organizations have a need to manage user identities and access across a variety -

Security Analysis and Decryption of Lion Full Disk Encryption
Infiltrate the Vault: Security Analysis and Decryption of Lion Full Disk Encryption Omar Choudary Felix Grobert¨ ∗ Joachim Metz ∗ University of Cambridge [email protected] [email protected] [email protected] Abstract 1 Introduction Since the launch of Mac OS X 10.7, also known as Lion, With the launch of Mac OS X 10.7 (Lion), Apple has Apple includes a volume encryption software named introduced a volume encryption mechanism known as FileVault 2 [8] in their operating system. While the pre- FileVault 2. Apple only disclosed marketing aspects of vious version of FileVault (introduced with Mac OS X the closed-source software, e.g. its use of the AES-XTS 10.3) only encrypted the home folder, FileVault 2 can en- tweakable encryption, but a publicly available security crypt the entire volume containing the operating system evaluation and detailed description was unavailable until (this is commonly referred to as full disk encryption). now. This has two major implications: first, there is now a new functional layer between the encrypted volume and We have performed an extensive analysis of the original file system (typically a version of HFS Plus). FileVault 2 and we have been able to find all the This new functional layer is actually a full volume man- algorithms and parameters needed to successfully read ager which Apple called CoreStorage [10] Although this an encrypted volume. This allows us to perform forensic full volume manager could be used for more than volume investigations on encrypted volumes using our own encryption (e.g. mirroring, snapshots or online storage tools. -

Open Directory Administration for Version 10.5 Leopard Second Edition
Mac OS X Server Open Directory Administration For Version 10.5 Leopard Second Edition Apple Inc. © 2008 Apple Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS X Server software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid-for support services. Every effort has been made to make sure that the information in this manual is correct. Apple Inc., is not responsible for printing or clerical errors. Apple 1 Infinite Loop Cupertino CA 95014-2084 www.apple.com The Apple logo is a trademark of Apple Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, iCal, iChat, Leopard, Mac, Macintosh, QuickTime, Xgrid, and Xserve are trademarks of Apple Inc., registered in the U.S. and other countries. Finder is a trademark of Apple Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. UNIX is a registered trademark of The Open Group. Other company and product names mentioned herein are trademarks of their respective companies. Mention of third-party products is for informational purposes only and constitutes neither an endorsement nor a recommendation. Apple assumes no responsibility with regard to the performance or use of these products. -

The Apple Ecosystem
APPENDIX A The Apple Ecosystem There are a lot of applications used to manage Apple devices in one way or another. Additionally, here’s a list of tools, sorted alphabetically per category in order to remain vendor agnostic. Antivirus Solutions for scanning Macs for viruses and other malware. • AVG: Basic antivirus and spyware detection and remediation. • Avast: Centralized antivirus with a cloud console for tracking incidents and device status. • Avira: Antivirus and a browser extension. Avira Connect allows you to view device status online. • BitDefender: Antivirus and malware managed from a central console. • CarbonBlack: Antivirus and Application Control. • Cylance: Ransomware, advanced threats, fileless malware, and malicious documents in addition to standard antivirus. • Kaspersky: Antivirus with a centralized cloud dashboard to track device status. © Charles Edge and Rich Trouton 2020 707 C. Edge and R. Trouton, Apple Device Management, https://doi.org/10.1007/978-1-4842-5388-5 APPENDIX A THe AppLe ECOSYSteM • Malware Bytes: Antivirus and malware managed from a central console. • McAfee Endpoint Security: Antivirus and advanced threat management with a centralized server to track devices. • Sophos: Antivirus and malware managed from a central console. • Symantec Mobile Device Management: Antivirus and malware managed from a central console. • Trend Micro Endpoint Security: Application whitelisting, antivirus, and ransomware protection in a centralized console. • Wandera: Malicious hot-spot monitoring, jailbreak detection, web gateway for mobile threat detection that integrates with common MDM solutions. Automation Tools Scripty tools used to automate management on the Mac • AutoCasperNBI: Automates the creation of NetBoot Images (read: NBI’s) for use with Casper Imaging. • AutoDMG: Takes a macOS installer (10.10 or newer) and builds a system image suitable for deployment with Imagr, DeployStudio, LANrev, Jamf Pro, and other asr or Apple Systems Restore-based imaging tools. -

Mac OS X Server in Education Collaboration and Communication Solutions for 21St-Century Academic Environments
Mac OS X Server in Education Collaboration and communication solutions for 21st-century academic environments. Podcasts. Blogs. Wikis. Group calendars. Video chats. Instant access to centralized resources. Welcome to the 21st-century academic environment. With Mac OS X Server version 10.5 Leopard, Apple puts the power of a server into the hands of everyone in your institution. So students, educators, and researchers are always connected and always communicating and collaborating—whether they’re around the globe or just across campus. 10 Reasons for Mac OS X Server in Education 1. End-to-end production of professional-quality podcasts. Podcast Producer in Mac OS X Server is a complete, customizable solution for producing podcasts of lectures, development sessions, research presentations, and campus updates. Starting with the Podcast Capture application in Mac OS X Leopard, it’s a snap for users to capture audio and video, record onscreen actions, or submit existing QuickTime content to the server. Once the content is uploaded, Podcast Producer automatically publishes it to your choice of distribution services—including iTunes U—in formats optimized for playback on almost any device, from HD video to iPod, Apple TV, or any multimedia-enabled cell phone. 2. Group collaboration on wiki-powered websites. Mac OS X Server gives students, educators, and research teams an instant space for collaboration. With their own group wiki—complete with blog, group calendar, and mailing-list archive—authorized users can create entries, tag and cross-reference material, upload files and images, add comments, and perform keyword searches. Best of all, these powerful capabilities are accessible from any modern browser in just a few clicks—there’s no need to learn an arcane markup language. -

Filevault, Choose an Unlock Method, and Set a • Create a Recovery Key
Overview Power and Mac State 8. Choose how to unlock your disk and reset Encryption occurs only while plugged into a your login password if you forget it. If your Mac is eligible, you just need to enable power source and in the Awake Status. • Use your iCloud account OR FileVault, choose an unlock method, and set a • Create a recovery key. Write down the few other options. Once enabled, files are Prevent Your Mac From Sleeping recovery key, or take a photo with your encrypted as they are added. 1. Go to the Apple menu. phone (be sure your phone is set up to 2. Select System Preferences. use a passcode to unlock), and keep it in Macs that are managed by WashU IT 3. Select Energy Saver. a safe place. are encrypted. If you need access to 4. Select the Power Adapter tab and your FileVault key, please contact the then slide the timer to Never. Don’t WashU IT Help Desk. forget to reset it when you are done encrypting. Requirements to Use FileVault Enabling FileVault 9. Select Continue. 10. If your Mac has multiple users, each Correct Mac OS Version If you meet the requirements in 1, 2, and 3, account that needs login access will need to OS X 10.7 Lion or newer and your mac is plugged into a power source, be enabled. You will need to know the follow the steps below. associated password for each account, or Check Your OS Version 1. Go to the Apple menu. have the user enter it during this process. -
1 Welcome to the Superduper!
Welcome to the SuperDuper! User’s Guide! This guide is designed to get you up and running as fast as possible. We’ve taken the most common tasks people perform with SuperDuper!, each placed in its own chapter, and have provided step-by-step guidance (including lots of pictures). In here you’ll find out how to: • Back up your Macintosh for the first time • Update an existing backup • Schedule one or multiple backups • Store a backup alongside other files on a destination drive • Back up your Macintosh over a network • Exclude a folder from a backup • Restore files from a backup • Restore an entire drive in an emergency situation • Troubleshooting We’ve also included a complete program reference, and some more advanced topics, such as: • Creating a Sandbox • Maintaining a Sandbox • Applying (and recovering from) System Updates while running from a Sandbox Note that SuperDuper operates in two different “modes” – registered and unregistered. The unregistered version allows easy, complete and user- specific backup clones to partitions, FireWire drives, and image files. 1 Once registered, SuperDuper allows you to schedule backups, quickly update backups with Smart Update (saving a lot of time), select “copy modes” other than Erase, then copy, create Sandboxes, fully customize the copying process using its unique Copy Scripts, save and restore settings, and avoid authenticating every time you copy. And, on top of that, it allows us to eat. Disclaimer Although SuperDuper! has been carefully tested, and should perform its functions without data loss, you use this software at your own risk and without any warranty. -

Dell Encryption Enterprise for Mac Administrator Guide V10.9
Dell Encryption Enterprise for Mac Administrator Guide v10.9 March 2021 Rev. A02 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2012-2021 Dell Inc. All rights reserved. Registered trademarks and trademarks used in the Dell Encryption and Endpoint Security Suite Enterprise suite of documents: Dell™ and the Dell logo, Dell Precision™, OptiPlex™, ControlVault™, Latitude™, XPS®, and KACE™ are trademarks of Dell Inc. Cylance®, CylancePROTECT, and the Cylance logo are registered trademarks of Cylance, Inc. in the U.S. and other countries. McAfee® and the McAfee logo are trademarks or registered trademarks of McAfee, Inc. in the US and other countries. Intel®, Pentium®, Intel Core Inside Duo®, Itanium®, and Xeon® are registered trademarks of Intel Corporation in the U.S. and other countries. Adobe®, Acrobat®, and Flash® are registered trademarks of Adobe Systems Incorporated. Authen tec® and Eikon® are registered trademarks of Authen tec. AMD® is a registered trademark of Advanced Micro Devices, Inc. Microsoft®, Windows®, and Windows Server®, Windows Vista®, Windows 7®, Windows 10®, Active Directory®, Access®, BitLocker®, BitLocker To Go®, Excel®, Hyper-V®, Outlook®, PowerPoint®, Word®, OneDrive®, SQL Server®, and Visual C++® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. VMware® is a registered trademark or trademark of VMware, Inc. in the United States or other countries. -
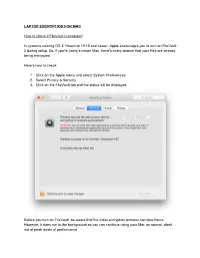
LAPTOP ENCRYPTION for MAC How to Check If Filevault Is Enabled
LAPTOP ENCRYPTION FOR MAC How to check if FileVault is enabled? In systems running OS X Yosemite 10.10 and newer, Apple encourages you to turn on FileVault 2 during setup. So, if you’re using a newer Mac, there’s every chance that your files are already being encrypted. Here’s how to check: 1. Click on the Apple menu and select System Preferences. 2. Select Privacy & Security. 3. Click on the FileVault tab and the status will be displayed. Before you turn on FileVault, be aware that the initial encryption process can take hours. However, it does run in the background so you can continue using your Mac as normal, albeit not at peak levels of performance. Also, FileVault encrypts the entire disk. Any additional users will need to be enabled so that they can unlock the disk by entering their password. How to turn on FileVault disk encryption 1. Click on the Apple menu and select System Preferences. 2. Select Privacy & Security. 3. Click on the FileVault tab, then click the lock in the bottom left corner of the window. 4. Enter your administrator name and password and click Unlock. 5. Click Turn On FileVault. 6. Choose whether you want to link your iCloud account to FileVault to unlock the disk and reset your password or create a recovery key and click Continue. 7. Click Restart to reboot your Mac and begin the encryption process. Choosing a FileVault Recovery Key The FileVault recovery key deserves special mention here. If you choose this option over linking your iCloud account, it’s critical that you make a note of the recovery key and keep it in a safe place that’s not on your hard drive. -

Mac OS X Server Introduction to Command-Line Administration Version 10.6 Snow Leopard Kkapple Inc
Mac OS X Server Introduction to Command-Line Administration Version 10.6 Snow Leopard K Apple Inc. Apple Remote Desktop, Finder, and Snow Leopard are © 2009 Apple Inc. All rights reserved. trademarks of Apple Inc. Under the copyright laws, this manual may not AIX is a trademark of IBM Corp., registered in the U.S. be copied, in whole or in part, without the written and other countries, and is being used under license. consent of Apple. The Bluetooth® word mark and logos are registered The Apple logo is a trademark of Apple Inc., registered trademarks owned by Bluetooth SIG, Inc. and any use in the U.S. and other countries. Use of the “keyboard” of such marks by Apple is under license. Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may This product includes software developed by the constitute trademark infringement and unfair University of California, Berkeley, FreeBSD, Inc., competition in violation of federal and state laws. The NetBSD Foundation, Inc., and their respective contributors. Every effort has been made to ensure that the information in this manual is accurate. Apple is not Java™ and all Java-based trademarks and logos responsible for printing or clerical errors. are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Apple 1 Infinite Loop PowerPC™ and the PowerPC logo™ are trademarks Cupertino, CA 95014 of International Business Machines Corporation, used 408-996-1010 under license therefrom. www.apple.com UNIX® is a registered trademark of The Open Group. Apple, the Apple logo, AppleScript, FireWire, Keychain, Other company and product names mentioned herein Leopard, Mac, Mac OS, Quartz, Safari, Xcode, Xgrid, and are trademarks of their respective companies.