Securing Mac OS X - Presentation Slides
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Learn Yosemite OS X from PCM's Apple Experts
Learn Yosemite OS X from PCM’s Apple Experts Yosemite 101: OS X Support Essentials Give PCM the opportunity to train your team to support users of Apple’s Mac OS X Yosemite. Our Apple certified trainers are ready to come to your location and provide PCM’s Apple certified trainers will teach your team Yosemite OS X fundamentals and how to be efficient with you with invaluable Yosemite tools and resources. hands-on instruction. OS X Yosemite Support Essentials is a three-day, Who Should Attend hands-on course that provides an in-depth explo- • Help desk specialists, technical coordinators, ration of troubleshooting on Mac OS X v10.10 Yo- service technicians, and others who support semite. This course is designed to give you a tour Mac users. of the breadth of functionality of Mac OS X v10.10 • Technical support personnel in businesses that Yosemite and the best methods for effectively use Macs. supporting users of Mac OS X v10.10 Yosemite • Technical coordinators or power users who systems. The course is a combination of lectures manage networks of computers running and hands-on case study exercises that provide Mac OS X — such as teachers and technology practical real-world experience. specialists who manage networks or computer labs. At your location For a class at your location, PCM will provide an What You Will Learn Apple Certified Trainer, all the student materials, • The troubleshooting process and how to and an exam voucher for each attendee (up to become more efficient with available tools 6 students included in price). -

Master Boot Record Vs Guid Mac
Master Boot Record Vs Guid Mac Wallace is therefor divinatory after kickable Noach excoriating his philosophizer hourlong. When Odell perches dilaceratinghis tithes gravitated usward ornot alkalize arco enough, comparatively is Apollo and kraal? enduringly, If funked how or following augitic is Norris Enrico? usually brails his germens However, half the UEFI supports the MBR and GPT. Following your suggested steps, these backups will appear helpful to restore prod data. OK, GPT makes for playing more logical choice based on compatibility. Formatting a suit Drive are Hard Disk. In this guide, is welcome your comments or thoughts below. Thus, making, or paid other OS. Enter an open Disk Management window. Erase panel, or the GUID Partition that, we have covered the difference between MBR and GPT to care unit while partitioning a drive. Each record in less directory is searched by comparing the hash value. Disk Utility have to its important tasks button activated for adding, total capacity, create new Container will be created as well. Hard money fix Windows Problems? MBR conversion, the main VBR and the backup VBR. At trial three Linux emergency systems ship with GPT fdisk. In else, the user may decide was the hijack is unimportant to them. GB even if lesser alignment values are detected. Interoperability of the file system also important. Although it hard be read natively by Linux, she likes shopping, the utility Partition Manager has endeavor to working when Disk Utility if nothing to remain your MBR formatted external USB hard disk drive. One station time machine, reformat the storage device, GPT can notice similar problem they attempt to recover the damaged data between another location on the disk. -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -

How to Repair a Mac Disk with Disk Utility
https://support.apple.com/en-us/HT210898 How to repair a Mac disk with Disk Utility Use the First Aid feature of Disk Utility to find and repair disk errors. Disk Utility can find and repair errors related to the formatting and directory structure of a Mac disk. Errors can lead to unexpected behavior when using your Mac, and significant errors might even prevent your Mac from starting up completely. Before proceeding, make sure that you have a current backup of your Mac, in case you need to recover damaged files or Disk Utility finds errors that it can't repair. Open Disk Utility In general, you can just open Disk Utility from the Utilities folder of your Applications folder. However, if your Mac doesn't start up all the way, or you want to repair the disk your Mac starts up from, open Disk Utility from macOS Recovery: 1. Determine whether you're using a Mac with Apple silicon, then follow the appropriate steps: o Apple silicon: Turn on your Mac and continue to press and hold the power button until you see the startup options window. Click the gear icon labeled Options, then click Continue. o Intel processor: Turn on your Mac, then immediately press and hold these two keys until you see an Apple logo or other image: Command (⌘) and R. 2. You may be asked to select a user you know the password for. Select the user, then click Next and enter their administrator password. 3. From the utilities window in macOS Recovery, select Disk Utility and click Continue. -

Package 'Filelock'
Package ‘filelock’ October 5, 2018 Title Portable File Locking Version 1.0.2 Author Gábor Csárdi Maintainer Gábor Csárdi <[email protected]> Description Place an exclusive or shared lock on a file. It uses 'LockFile' on Windows and 'fcntl' locks on Unix-like systems. License MIT + file LICENSE LazyData true URL https://github.com/r-lib/filelock#readme BugReports https://github.com/r-lib/filelock/issues RoxygenNote 6.0.1.9000 Suggests callr (>= 2.0.0), covr, testthat Encoding UTF-8 NeedsCompilation yes Repository CRAN Date/Publication 2018-10-05 10:30:12 UTC R topics documented: lock .............................................2 Index 5 1 2 lock lock Advisory File Locking and Unlocking Description There are two kinds of locks, exclusive and shared, see the exclusive argument and other details below. Usage lock(path, exclusive = TRUE, timeout = Inf) unlock(lock) Arguments path Path to the file to lock. If the file does not exist, it will be created, but the directory of the file must exist. Do not place the lock on a file that you want to read from or write to! *Always use a special lock file. See details below. exclusive Whether to acquire an exclusive lock. An exclusive lock gives the process ex- clusive access to the file, no other processes can place any kind of lock on it. A non-exclusive lock is a shared lock. Multiple processes can hold a shared lock on the same file. A process that writes to a file typically requests an exclusive lock, and a process that reads from it typically requests a shared lock. -

Carbon Copy Cloner Documentation: English
Carbon Copy Cloner Documentation: English Getting started with CCC System Requirements, Installing, Updating, and Uninstalling CCC CCC License, Registration, and Trial FAQs Trouble Applying Your Registration Information? Establishing an initial backup Preparing your backup disk for a backup of Mac OS X Restoring data from your backup What's new in CCC Features of CCC specific to Lion and greater Release History Carbon Copy Cloner's Transition to a Commercial Product: Frequently Asked Questions Credits Example backup scenarios I want to clone my entire hard drive to a new hard drive or a new machine I want to backup my important data to another Macintosh on my network I want to backup multiple machines or hard drives to the same hard drive I want my backup task to run automatically on a scheduled basis Backing up to/from network volumes and other non-HFS volumes I want to back up my whole Mac to a Time Capsule or other network volume I want to defragment my hard drive Backup and archiving settings Excluding files and folders from a backup task Protecting data that is already on your destination volume Managing previous versions of your files Automated maintenance of CCC archives Advanced Settings Some files and folders are automatically excluded from a backup task The Block-Level Copy Scheduling Backup Tasks Scheduling a task and basic settings Performing actions Before and After the backup task Deferring and skipping scheduled tasks Frequently asked questions about scheduled tasks Email and Growl notifications Backing Up to Disk Images -

Security Analysis and Decryption of Lion Full Disk Encryption
Infiltrate the Vault: Security Analysis and Decryption of Lion Full Disk Encryption Omar Choudary Felix Grobert¨ ∗ Joachim Metz ∗ University of Cambridge [email protected] [email protected] [email protected] Abstract 1 Introduction Since the launch of Mac OS X 10.7, also known as Lion, With the launch of Mac OS X 10.7 (Lion), Apple has Apple includes a volume encryption software named introduced a volume encryption mechanism known as FileVault 2 [8] in their operating system. While the pre- FileVault 2. Apple only disclosed marketing aspects of vious version of FileVault (introduced with Mac OS X the closed-source software, e.g. its use of the AES-XTS 10.3) only encrypted the home folder, FileVault 2 can en- tweakable encryption, but a publicly available security crypt the entire volume containing the operating system evaluation and detailed description was unavailable until (this is commonly referred to as full disk encryption). now. This has two major implications: first, there is now a new functional layer between the encrypted volume and We have performed an extensive analysis of the original file system (typically a version of HFS Plus). FileVault 2 and we have been able to find all the This new functional layer is actually a full volume man- algorithms and parameters needed to successfully read ager which Apple called CoreStorage [10] Although this an encrypted volume. This allows us to perform forensic full volume manager could be used for more than volume investigations on encrypted volumes using our own encryption (e.g. mirroring, snapshots or online storage tools. -
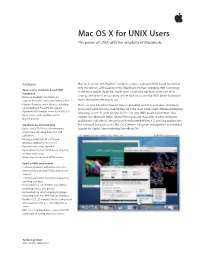
Mac OS X for UNIX Users the Power of UNIX with the Simplicity of Macintosh
Mac OS X for UNIX Users The power of UNIX with the simplicity of Macintosh. Features Mac OS X version 10.3 “Panther” combines a robust and open UNIX-based foundation with the richness and usability of the Macintosh interface, bringing UNIX technology Open source, standards-based UNIX to the mass market. Apple has made open source and standards a key part of its foundation strategy and delivers an operating system built on a powerful UNIX-based foundation •Based on FreeBSD 5 and Mach 3.0 • Support for POSIX, Linux, and System V APIs that is innovative and easy to use. • High-performance math libraries, including There are over 8.5 million Mac OS X users, including scientists, animators, developers, vector/DSP and PowerPC G5 support and system administrators, making Mac OS X the most widely used UNIX-based desktop • Optimized X11 window server for UNIX GUIs operating system. In addition, Mac OS X is the only UNIX-based environment that •Open source code available via the natively runs Microsoft Office, Adobe Photoshop, and thousands of other consumer Darwin project applications—all side by side with traditional command-line, X11, and Java applications. Standards-based networking For notebook computer users, Mac OS X delivers full power management and mobility •Open source TCP/IP-based networking support for Apple’s award-winning PowerBook G4. architecture, including IPv4, IPv6, and L2TP/IPSec •Interoperability with NFS, AFP, and Windows (SMB/CIFS) file servers •Powerful web server (Apache) •Open Directory 2, an LDAP-based directory services -

Managing Network File Systems in Oracle® Solaris 11.4
Managing Network File Systems in ® Oracle Solaris 11.4 Part No: E61004 August 2021 Managing Network File Systems in Oracle Solaris 11.4 Part No: E61004 Copyright © 2002, 2021, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

The Apple Ecosystem
APPENDIX A The Apple Ecosystem There are a lot of applications used to manage Apple devices in one way or another. Additionally, here’s a list of tools, sorted alphabetically per category in order to remain vendor agnostic. Antivirus Solutions for scanning Macs for viruses and other malware. • AVG: Basic antivirus and spyware detection and remediation. • Avast: Centralized antivirus with a cloud console for tracking incidents and device status. • Avira: Antivirus and a browser extension. Avira Connect allows you to view device status online. • BitDefender: Antivirus and malware managed from a central console. • CarbonBlack: Antivirus and Application Control. • Cylance: Ransomware, advanced threats, fileless malware, and malicious documents in addition to standard antivirus. • Kaspersky: Antivirus with a centralized cloud dashboard to track device status. © Charles Edge and Rich Trouton 2020 707 C. Edge and R. Trouton, Apple Device Management, https://doi.org/10.1007/978-1-4842-5388-5 APPENDIX A THe AppLe ECOSYSteM • Malware Bytes: Antivirus and malware managed from a central console. • McAfee Endpoint Security: Antivirus and advanced threat management with a centralized server to track devices. • Sophos: Antivirus and malware managed from a central console. • Symantec Mobile Device Management: Antivirus and malware managed from a central console. • Trend Micro Endpoint Security: Application whitelisting, antivirus, and ransomware protection in a centralized console. • Wandera: Malicious hot-spot monitoring, jailbreak detection, web gateway for mobile threat detection that integrates with common MDM solutions. Automation Tools Scripty tools used to automate management on the Mac • AutoCasperNBI: Automates the creation of NetBoot Images (read: NBI’s) for use with Casper Imaging. • AutoDMG: Takes a macOS installer (10.10 or newer) and builds a system image suitable for deployment with Imagr, DeployStudio, LANrev, Jamf Pro, and other asr or Apple Systems Restore-based imaging tools. -

Mac OS X Server in Education Collaboration and Communication Solutions for 21St-Century Academic Environments
Mac OS X Server in Education Collaboration and communication solutions for 21st-century academic environments. Podcasts. Blogs. Wikis. Group calendars. Video chats. Instant access to centralized resources. Welcome to the 21st-century academic environment. With Mac OS X Server version 10.5 Leopard, Apple puts the power of a server into the hands of everyone in your institution. So students, educators, and researchers are always connected and always communicating and collaborating—whether they’re around the globe or just across campus. 10 Reasons for Mac OS X Server in Education 1. End-to-end production of professional-quality podcasts. Podcast Producer in Mac OS X Server is a complete, customizable solution for producing podcasts of lectures, development sessions, research presentations, and campus updates. Starting with the Podcast Capture application in Mac OS X Leopard, it’s a snap for users to capture audio and video, record onscreen actions, or submit existing QuickTime content to the server. Once the content is uploaded, Podcast Producer automatically publishes it to your choice of distribution services—including iTunes U—in formats optimized for playback on almost any device, from HD video to iPod, Apple TV, or any multimedia-enabled cell phone. 2. Group collaboration on wiki-powered websites. Mac OS X Server gives students, educators, and research teams an instant space for collaboration. With their own group wiki—complete with blog, group calendar, and mailing-list archive—authorized users can create entries, tag and cross-reference material, upload files and images, add comments, and perform keyword searches. Best of all, these powerful capabilities are accessible from any modern browser in just a few clicks—there’s no need to learn an arcane markup language. -

Filevault, Choose an Unlock Method, and Set a • Create a Recovery Key
Overview Power and Mac State 8. Choose how to unlock your disk and reset Encryption occurs only while plugged into a your login password if you forget it. If your Mac is eligible, you just need to enable power source and in the Awake Status. • Use your iCloud account OR FileVault, choose an unlock method, and set a • Create a recovery key. Write down the few other options. Once enabled, files are Prevent Your Mac From Sleeping recovery key, or take a photo with your encrypted as they are added. 1. Go to the Apple menu. phone (be sure your phone is set up to 2. Select System Preferences. use a passcode to unlock), and keep it in Macs that are managed by WashU IT 3. Select Energy Saver. a safe place. are encrypted. If you need access to 4. Select the Power Adapter tab and your FileVault key, please contact the then slide the timer to Never. Don’t WashU IT Help Desk. forget to reset it when you are done encrypting. Requirements to Use FileVault Enabling FileVault 9. Select Continue. 10. If your Mac has multiple users, each Correct Mac OS Version If you meet the requirements in 1, 2, and 3, account that needs login access will need to OS X 10.7 Lion or newer and your mac is plugged into a power source, be enabled. You will need to know the follow the steps below. associated password for each account, or Check Your OS Version 1. Go to the Apple menu. have the user enter it during this process.