Penpoint Operating System Overview and Application Development
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Certain Mobile Devices, Associated Software, and Components Thereof
In the Matter of Certain Mobile Devices, Associated Software, and Components Thereof Investigation No. 337-TA-744 Publication 4384 March 2013 U.S. International Trade Commission Washington, DC 20436 U.S. International Trade Commission COMMISSIONERS Deanna Tanner Okun, Chairman Irving A. Williamson, Vice Chairman Daniel R. Pearson, Commissioner Shara L. Aranoff, Commissioner Dean A. Pinkert, Commissioner David S. Johanson, Commissioner Address all communications to Secretary to the Commission United States International Trade Commission Washington, DC 20436 U.S. International Trade Commission Washington, DC 20436 www.usitc.gov In the Matter of Certain Mobile Devices, Associated Software, and Components Thereof Investigation No. 337-TA-744 Publication 4384 March 2013 i UNITED STATES INTERNATIONAL TRADE COMMISSION Washington, D.C. In the Matter of CERTAIN MOBILE DEVICES, Investigation No. 337-TA-744 ASSOCIATED SOFTWARE, AND COMPONENTS THEREOF NOTICE OF A COMMISSION FINAL DETERMINATION OF VIOLATION OF SECTION 337; ISSUANCE OF A LIMITED EXCLUSION ORDER; TERMINATION OF INVESTIGATION AGENCY: U.S. International Trade Commission. ACTION: Notice. SUMMARY: Notice is hereby given that the U.S. International Trade Commission has determined that there is a violation of section 337 of the Tariff Act of 1930, as amended (19 U.S.C. § 1337) by respondent Motorola Mobility, Inc. of Libertyville, Illinois ("Motorola") in the above-captioned investigation. The Commission has issued a limited exclusion order directed to the infringing products of Motorola and has terminated the investigation. FOR FURTHER INFORMATION CONTACT: Michael Liberman, Esq., Office ofthe General Counsel, U.S. International Trade Commission, 500 E Street, S.W., Washington, D.C. 20436, telephone (202) 205-3115. -

Pen Computing History
TheThe PastPast andand FutureFuture ofof PenPen ComputingComputing Conrad H. Blickenstorfer, Editor-in-Chief Pen Computing Magazine [email protected] http://www.pencomputing.com ToTo buildbuild thethe future,future, wewe mustmust learnlearn fromfrom thethe pastpast HistoryHistory ofof penpen computingcomputing 1914: Goldberg gets US patent for recognition of handwritten numbers to control machines 1938: Hansel gets US patent for machine recognition of handwriting 1956: RAND Corporation develops digitizing tablet for handwriting recognition 1957-62: Handwriting recognition projects with accuracies of 97-99% 1963: Bell Labs develops cursive recognizer 1966: RAND creates GRAIL, similar to Graffiti Pioneer:Pioneer: AlanAlan KayKay Utah State University Stanford University Xerox PARC: GUI, SmallTalk, OOL Apple Computer Research Fellow Disney Envisioned Dynabook in 1968: The Dynabook will be a “dynamic medium for creative thought, capable of synthesizing all media – pictures, animation, sound, and text – through the intimacy and responsiveness of the personal computer.” HistoryHistory ofof penpen computingcomputing 1970s: Commercial products, including kana/romanji billing machine 1980s: Handwriting recognition companies – Nestor – Communication Intelligence Corporation – Lexicus – Several others Pioneers:Pioneers: AppleApple 1987 Apple prototype – Speech recognition – Intelligent agents – Camera – Folding display – Video conferencing – Wireless communication – Personal Information Manager ““KnowledgeKnowledge NavigatorNavigator”” -

Encyclopedia of Windows
First Edition, 2012 ISBN 978-81-323-4632-6 © All rights reserved. Published by: The English Press 4735/22 Prakashdeep Bldg, Ansari Road, Darya Ganj, Delhi - 110002 Email: [email protected] Table of Contents Chapter 1 - Microsoft Windows Chapter 2 - Windows 1.0 and Windows 2.0 Chapter 3 - Windows 3.0 Chapter 4 - Windows 3.1x Chapter 5 - Windows 95 Chapter 6 - Windows 98 Chapter 7 - Windows Me Chapter 8 - Windows NT Chapter 9 - Windows CE Chapter 10 - Windows 9x Chapter 11 - Windows XP Chapter 12 - Windows 7 Chapter- 1 Microsoft Windows Microsoft Windows The latest Windows release, Windows 7, showing the desktop and Start menu Company / developer Microsoft Programmed in C, C++ and Assembly language OS family Windows 9x, Windows CE and Windows NT Working state Publicly released Source model Closed source / Shared source Initial release November 20, 1985 (as Windows 1.0) Windows 7, Windows Server 2008 R2 Latest stable release NT 6.1 Build 7600 (7600.16385.090713-1255) (October 22, 2009; 14 months ago) [+/−] Windows 7, Windows Server 2008 R2 Service Pack 1 RC Latest unstable release NT 6.1 Build 7601 (7601.17105.100929-1730) (September 29, 2010; 2 months ago) [+/−] Marketing target Personal computing Available language(s) Multilingual Update method Windows Update Supported platforms IA-32, x86-64 and Itanium Kernel type Hybrid Default user interface Graphical (Windows Explorer) License Proprietary commercial software Microsoft Windows is a series of software operating systems and graphical user interfaces produced by Microsoft. Microsoft first introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces (GUIs). -

An Electronic Chalkboard for Classroom and Distance Teaching
An Electronic Chalkboard for Classroom and Distance Teaching Dissertation zur Erlangung des akademischen Grades eines Doktors der Naturwissenschaften im Fachbereich Mathematik und Informatik der Freien Universit¨at Berlin vorgelegt von Lars Knipping aus Itzehoe 14. Februar 2005 ii Gutachter: Prof. Dr. Ra´ulRojas Prof. Dr. Ruedi Seiler Preface Quis leget haec? Persius, Satires, 1:2 Many people have contributed to the development of the system being de- scribed in this thesis. The project was conceived by Prof. Dr. Ra´ulRojas, who accompanied its development and provided many ideas. The first prototype of the board software was written by Wolf-Ulrich Raffel. The entire audio part is authored by Gerald Friedland, on the basis of the WWR system by Gerald Friedland and Tobias Lasser and its successor WWR2 by Gerald Friedland and Bernhard Fr¨otschl. Gerald Friedland also designed the multimedia editor called Exymen and the video part of the E-Chalk system. Kristian Jantz assisted in the video software development. He implemented the SID plug-in for Exymen, the Maple connection for the board, and a number of tools: one for converting lecture recordings to AVI and QuickTime movies, another for generating board snapshots, one for updating the audio format, and a tool for restoring damaged recordings. Ernesto Tapia developed the mathematical handwriting recognition inte- grated in the board component. Mary Ann Brennan wrote the first version of the PDF generator and the JMF audio plug-in for Exymen. Stephan Lehmann implemented the program to convert E-Chalk recordings to Windows ASF files. Dr. Peter R¨ußman added capabilities for function definition and function plot- ting for the small built-in computer algebra system. -

Towards Document Engineering on Pen and Touch-Operated Interactive Tabletops
DISS. ETH NO. 21686 Towards Document Engineering on Pen and Touch-Operated Interactive Tabletops A dissertation submitted to ETH ZURICH for the degree of Doctor of Sciences presented by FABRICE MATULIC Diplôme d'Ingénieur ENSIMAG Diplom Informatik, Universität Karlsruhe (TH) accepted on the recommendation of Prof. Dr. Moira C. Norrie, examiner Prof. (FH) Dr. Michael Haller, co-examiner Dr. Ken Hinckley, co-examiner 2014 Document Authoring on Pen and Calibri 24 B I U © 2014 Fabrice Matulic Abstract In the last few years, the consumer device landscape has been significantly transformed by the rapid proliferation of smartphones and tablets, whose sales are fast overtaking that of traditional PCs. The highly user-friendly multitouch interfaces combined with ever more efficient electronics have made it possible to perform an increasingly wide range of activities on those mobile devices. One category of tasks, for which the desktop PC with mouse and keyboard remains the platform of choice, however, is office work. In particular, productivity document engineering tasks are still more likely to be carried out on a regular computer and with software, whose interfaces are based on the time-honoured "windows, icons, menus, pointer" (WIMP) paradigm. With the recent emergence of larger touch-based devices such as wall screens and digital tabletops (which overcome the limitations of mobile devices in terms of available screen real estate) as well as the resurgence of the stylus as an additional input instrument, the vocabulary of interactions at the disposal of interface designers has vastly broadened. Hybrid pen and touch input is a very new and promising interaction model that practitioners have begun to tap, but it has yet to be applied in office applications and document-centric productivity environments. -

An Electronic Chalkboard for Classroom and Distance Teaching
Chapter 1 Introduction and Related Work Computers promise the fountains of utopia, but only deliver a flood of information Langdon Winner, Mythinformation, Whole Earth Review, Jan. 1985 1.1 The E-Learning Landscape The history of-computer supported education is rooted in the early era of main- frames. In 1963, the PLATO system [Woo94] (Programmed Logic for Auto- mated Teaching Operations) was developed at University of Illinois. It had custom-built multimedia teaching terminal stations connected to the mainframe. A proprietary language called TUTOR was created for authoring educational software. More than 15,000 hours worth of instruction material were developed for PLATO. Features like online chat and bulletin-board notes were added in the early 1970s, long before the Internet. In 1976 Control Data Corporation (CDC) established PLATO-IV as a commercial educational product, with its successor still around [75]. Recent years have witnessed considerable activity in the field of computer- aided education. With an access to the Internet being almost omnipresent, people envision a new age of learning: the learners will be free to learn when and where they want, learning efficiencies will be heightened by a multimedia- enriched learning experiences, and training costs can be cut by reusing teaching content. Production Costs Unfortunately, creating e-learning material is a laborious process. Production costs are reckoned to be in the range of 50 to 200 man hours for one hour of learning content. [CMMS03] reports on the development of static or dynamic HTML pages: On the average, one can calculate one person working for a half to up to a full year for the preparation of electronic learning content for only one course. -

ESTTA800156 02/08/2017 in the UNITED STATES PATENT and TRADEMARK OFFICE BEFORE the TRADEMARK TRIAL and APPEAL BOARD Proceeding 9
Trademark Trial and Appeal Board Electronic Filing System. http://estta.uspto.gov ESTTA Tracking number: ESTTA800156 Filing date: 02/08/2017 IN THE UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE TRADEMARK TRIAL AND APPEAL BOARD Proceeding 91220591 Party Plaintiff TCT Mobile International Limited Correspondence SUSAN M NATLAND Address KNOBBE MARTENS OLSON & BEAR LLP 2040 MAIN STREET , 14TH FLOOR IRVINE, CA 92614 UNITED STATES [email protected], [email protected] Submission Motion to Amend Pleading/Amended Pleading Filer's Name Jonathan A. Hyman Filer's e-mail [email protected], [email protected] Signature /jhh/ Date 02/08/2017 Attachments TCLC.004M-Opposer's Motion for Leave to Amend Notice of Opp and Motion to Suspend.pdf(1563803 bytes ) TCLC.004M-AmendNoticeofOpposition.pdf(1599537 bytes ) TCLC.004M-NoticeofOppositionExhibits.pdf(2003482 bytes ) EXHIBIT A 2/11/2015 Moving Definition and More from the Free MerriamWebster Dictionary An Encyclopædia Britannica Company Join Us On Dictionary Thesaurus Medical Scrabble Spanish Central moving Games Word of the Day Video Blog: Words at Play My Faves Test Your Dictionary SAVE POPULARITY Vocabulary! move Save this word to your Favorites. If you're logged into Facebook, you're ready to go. 13 ENTRIES FOUND: moving move moving average moving cluster movingcoil movingiron meter moving pictureSponsored Links Advertise Here moving sidewalkKnow Where You Stand moving staircaseMonitor your credit. Manage your future. Equifax Complete™ Premier. fastmovingwww.equifax.com -

Palm (A): the Debate on Licensing Palm's OS (1997)
N9-708-514 MAY 20, 2008 RAMON CASADESUS- MASANELL KEVIN BOUDREAU JORDAN MITCHELL Palm (A): The Debate on Licensing Palm’s OS (1997) Shortly after the acquisition of Palm’s parent US Robotics by 3Com in February 1997, 3Com’s CEO, Eric Benhamou, began applying pressure on Palm executives to open up the Palm OS (operating system) to other handheld computer manufacturers. Benhamou pointed to the PC (personal computer) market as evidence that opening up a platform to other firms spurred on hardware development, grew the size of the market and ensured the dominance of one operating system. Specifically, Apple was trotted out as an example of losing out to Microsoft by refusing to license out the Mac OS operating system to other manufacturers such as Hewlett-Packard (HP), Compaq and Dell. Some of the popular press had even proclaimed the downright demise of Apple; Business Week had declared, “The death of an American icon,” on a cover story about Apple in 1996. In contrast, Microsoft Windows had grown to control over 90 per cent of all OSs on PCs by forming broad licensing agreements with original equipment manufacturers (OEMs). 3Com executives were adamant that Palm’s future should not follow Apple’s downfall in the PC market. The message from 3Com was clear: “[Palm should] license early and license broadly, before Microsoft takes [the] market away.”1 Palm’s co-founders – Jeff Hawkins (Product Technology) and Donna Dubinsky (CEO) – argued fervently against Benhamou and 3Com executives. Hawkins and Dubinsky claimed that the market for handhelds was distinct to the PC market. -

2.2 Panasonic Lumix DMC FZ7
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ ÚSTAV INTELIGENTNÍCH SYSTÉMŮ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF INTELLIGENT SYSTEMS SIMULATOR AND TRAINER OF THE PANASONIC FZ7 CAMERA BAKALÁŘSKÁ PRÁCE BACHELOR‘S THESIS AUTOR PRÁCE BRANISLAV BIELIK AUTHOR BRNO 2009 VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ ÚSTAV POČÍTAČOVÝCH SYSTÉMŮ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF COMPUTER SYSTEMS SIMULÁTOR A TRENAŽÉR DIGITÁLNÍCH FOTOAPARÁTŮ ŘADY PANASONIC FZ7 SIMULATOR AND TRAINER OF THE PANASONIC FZ7 CAMERA BAKALÁŘSKÁ PRÁCE BACHELOR‘S THESIS AUTOR PRÁCE BRANISLAV BIELIK AUTHOR VEDOUCÍ PRÁCE Doc. Ing. JIŘÍ KUNOVSKÝ, CSc. SUPERVISOR BRNO 2009 Abstrakt Bakalářská práce Simulátor a trenažér digitálních fotoaparátů řady Panasonic FZ7 se zabývá návrhem a realizací výukových manuálů a trenažéru pro tento digitální fotoaparát. Aplikace bude sloužit na podporu výuky na Univerzitě třetího věku. Implementace je pomocí Adobe Flash a programovacího jazyka ActionScript. Jsou zde popsány základy fotografování jako aj tvorby aplikací v prostředí Flash. Simulace umožňuje vyzkoušet možnosti zařízení při výuce a manuál přehledným způsobem vysvětlí základní použití fotoaparátu. Abstract The Bachelor’s thesis Simulator and Trainer of the Panasonic FZ7 Camera deals with a design and a realization of the training manual and the trainer for this digital camera. The application will be used to support the education at the University of the Third Age. Adobe -
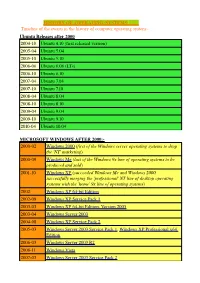
HISTORY of OPERATING SYSTEMS Timeline of The
HISTORY OF OPERATING SYSTEMS Timeline of the events in the history of computer operating system:- Ubuntu Releases after 2000 2004-10 Ubuntu 4.10 (first released version) 2005-04 Ubuntu 5.04 2005-10 Ubuntu 5.10 2006-06 Ubuntu 6.06 (LTs) 2006-10 Ubuntu 6.10 2007-04 Ubuntu 7.04 2007-10 Ubuntu 7.10 2008-04 Ubuntu 8.04 2008-10 Ubuntu 8.10 2009-04 Ubuntu 9.04 2009-10 Ubuntu 9.10 2010-04 Ubuntu 10.04 MICROSOFT WINDOWS AFTER 2000:- 2000-02 Windows 2000 (first of the Windows server operating systems to drop the ©NT© marketing) 2000-09 Windows Me (last of the Windows 9x line of operating systems to be produced and sold) 2001-10 Windows XP (succeeded Windows Me and Windows 2000, successfully merging the ©professional© NT line of desktop operating systems with the ©home© 9x line of operating systems) 2002 Windows XP 64-bit Edition 2002-09 Windows XP Service Pack 1 2003-03 Windows XP 64-bit Edition, Version 2003 2003-04 Windows Server 2003 2004-08 Windows XP Service Pack 2 2005-03 Windows Server 2003 Service Pack 1, Windows XP Professional x64 Edition 2006-03 Windows Server 2003 R2 2006-11 Windows Vista 2007-03 Windows Server 2003 Service Pack 2 2007-11 Windows Home Server 2008-02 Windows Vista Service Pack 1, Windows Server 2008 2008-04 Windows XP Service Pack 3 2009-05 Windows Vista Service Pack 2 2009-10 Windows 7(22 occtober 2009), Windows Server 2008 R2 EVENT IN HISTORY OF OS SINCE 1954:- 1950s 1954 MIT©s operating system made for UNIVAC 1103 1955 General Motors Operating System made for IBM 701 1956 GM-NAA I/O for IBM 704, based on General Motors -

Yelieseva S. V. Information Technologies in Translation.Pdf
The Ministry of Education and Science of Ukraine Petro Mohyla Black Sea National University S. V. Yelisieieva INFORMATION TECHNOLOGIES IN TRANSLATION A STUDY GUIDE PMBSNU Publishing House Mykolaiv – 2018 S. V. Yelisieieva UDC 81' 322.2 Y 40 Рекомендовано до друку вченою радою Чорноморського національного університету імені Петра Могили (протокол № 12 від 03.07.2018). Рецензенти: Демецька В. В., д-р філол. наук, професор, декан факультету перекладознавства Херсонського державного університету; Філіпова Н. М., д-р філол. наук, професор кафедри прикладної лінгвістики Національного морського університету ім. адмірала Макарова; Кондратенко Ю. П., д-р техн. наук, професор, професор кафедри інтелектуальних інформаційних систем факультету коп’ютерних наук Чорноморського національного університету ім. Петра Могили; Бабій Ю. Б., канд. філол. наук, доцент кафедри прикла- дної лінгвістики Миколаївського національного університету ім. В. О. Сухомлинського. Y 40 Yelisieieva S. V. Information Technologies in Translation : A Study Guide / S. V. Yelisieieva. – Мykolaiv : PMBSNU Publishing House, 2018. – 176 р. ISBN 978-966-336-399-8 The basis of the training course Information Technologies in Translation lies the model of work cycle on translation, which describes the sequence of necessary actions for qualified performance and further maintenance of written translation order. At each stage, translators use the appropriate software (S/W), which simplifies the work and allows to improve the quality of the finished documentation. The course familiarizes students with all stages of the translation work cycle and with those components of the software used at each stage. Besides, this training course includes information on working with the latest multimedia technologies that are widely used nowadays for presentations of various information materials. -

Virtualization-Based Architecture for the Operating Systems History Demonstration Anatoliy V
Central European Researchers Journal, Vol.3 Issue 2 Virtualization-based architecture for the operating systems history demonstration Anatoliy V. Gusev, Vladimir Yu. Kovalenko, Dmitriy A. Kostiuk1 Abstract—The universal virtualized infrastructure for embeddable demonstration of mobile and desktop operating systems is presented, with emphasis on live display of the graphical user interface history. Experience of using virtual machines instead of screenshots in a visual timeline of GUI is reviewed. Presented solution provides user control via the Internet or intranet web access, and QEMU-based nested virtualization for the unified interaction with heterogeneous simulated architecture of mobile devices. Availability of materials is considered, as far as approaches used to improve web-based user interaction with virtualized GUI. Internal architecture, deployment and scaling principles are discussed. Keywords—virtualization, history, computer interfaces, live demonstration. I. INTRODUCTION Although technically working with the new information technologies doesn’t demand knowing the history of their development, however specialist who formulates or applies modern theory without knowledge of its history, runs the risk of repeating the mistakes of predecessors personally one by one [1]. Being in the context of spoken above statement we have developed the ostimeline project [2], intended to provide the user (either via network or on a stand-alone workstation) with a set of chronologically-related HTML documents, each one with a description of the specific graphical operating system and its live illustration in the form of built-in frame with the screen of a running virtual machine (thanks to the performance of today’s notebooks and desktop PCs, this task is easy enough), as shown on Fig.