Foundations of Network and Computer Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2009 U.S. Tournament.Our.Beginnings
Chess Club and Scholastic Center of Saint Louis Presents the 2009 U.S. Championship Saint Louis, Missouri May 7-17, 2009 History of U.S. Championship “pride and soul of chess,” Paul It has also been a truly national Morphy, was only the fourth true championship. For many years No series of tournaments or chess tournament ever held in the the title tournament was identi- matches enjoys the same rich, world. fied with New York. But it has turbulent history as that of the also been held in towns as small United States Chess Championship. In its first century and a half plus, as South Fallsburg, New York, It is in many ways unique – and, up the United States Championship Mentor, Ohio, and Greenville, to recently, unappreciated. has provided all kinds of entertain- Pennsylvania. ment. It has introduced new In Europe and elsewhere, the idea heroes exactly one hundred years Fans have witnessed of choosing a national champion apart in Paul Morphy (1857) and championship play in Boston, and came slowly. The first Russian Bobby Fischer (1957) and honored Las Vegas, Baltimore and Los championship tournament, for remarkable veterans such as Angeles, Lexington, Kentucky, example, was held in 1889. The Sammy Reshevsky in his late 60s. and El Paso, Texas. The title has Germans did not get around to There have been stunning upsets been decided in sites as varied naming a champion until 1879. (Arnold Denker in 1944 and John as the Sazerac Coffee House in The first official Hungarian champi- Grefe in 1973) and marvelous 1845 to the Cincinnati Literary onship occurred in 1906, and the achievements (Fischer’s winning Club, the Automobile Club of first Dutch, three years later. -

World Stars Sharjah Online International Chess Championship 2020
World Stars Sharjah Online International Chess Championship 2020 World Stars 2020 ● Tournament Book ® Efstratios Grivas 2020 1 Welcome Letter Sharjah Cultural & Chess Club President Sheikh Saud bin Abdulaziz Al Mualla Dear Participants of the World Stars Sharjah Online International Chess Championship 2020, On behalf of the Board of Directors of the Sharjah Cultural & Chess Club and the Organising Committee, I am delighted to welcome all our distinguished participants of the World Stars Sharjah Online International Chess Championship 2020! Unfortunately, due to the recent negative and unpleasant reality of the Corona-Virus, we had to cancel our annual live events in Sharjah, United Arab Emirates. But we still decided to organise some other events online, like the World Stars Sharjah Online International Chess Championship 2020, in cooperation with the prestigious chess platform Internet Chess Club. The Sharjah Cultural & Chess Club was founded on June 1981 with the object of spreading and development of chess as mental and cultural sport across the Sharjah Emirate and in the United Arab Emirates territory in general. As on 2020 we are celebrating the 39th anniversary of our Club I can promise some extra-ordinary events in close cooperation with FIDE, the Asian Chess Federation and the Arab Chess Federation for the coming year 2021, which will mark our 40th anniversary! For the time being we welcome you in our online event and promise that we will do our best to ensure that the World Stars Sharjah Online International Chess Championship -

Kasparov's Nightmare!! Bobby Fischer Challenges IBM to Simul IBM
California Chess Journal Volume 20, Number 2 April 1st 2004 $4.50 Kasparov’s Nightmare!! Bobby Fischer Challenges IBM to Simul IBM Scrambles to Build 25 Deep Blues! Past Vs Future Special Issue • Young Fischer Fires Up S.F. • Fischer commentates 4 Boyscouts • Building your “Super Computer” • Building Fischer’s Dream House • Raise $500 playing chess! • Fischer Articles Galore! California Chess Journal Table of Con tents 2004 Cal Chess Scholastic Championships The annual scholastic tourney finishes in Santa Clara.......................................................3 FISCHER AND THE DEEP BLUE Editor: Eric Hicks Contributors: Daren Dillinger A miracle has happened in the Phillipines!......................................................................4 FM Eric Schiller IM John Donaldson Why Every Chess Player Needs a Computer Photographers: Richard Shorman Some titles speak for themselves......................................................................................5 Historical Consul: Kerry Lawless Founding Editor: Hans Poschmann Building Your Chess Dream Machine Some helpful hints when shopping for a silicon chess opponent........................................6 CalChess Board Young Fischer in San Francisco 1957 A complet accounting of an untold story that happened here in the bay area...................12 President: Elizabeth Shaughnessy Vice-President: Josh Bowman 1957 Fischer Game Spotlight Treasurer: Richard Peterson One game from the tournament commentated move by move.........................................16 Members at -

A GUIDE to SCHOLASTIC CHESS (11Th Edition Revised June 26, 2021)
A GUIDE TO SCHOLASTIC CHESS (11th Edition Revised June 26, 2021) PREFACE Dear Administrator, Teacher, or Coach This guide was created to help teachers and scholastic chess organizers who wish to begin, improve, or strengthen their school chess program. It covers how to organize a school chess club, run tournaments, keep interest high, and generate administrative, school district, parental and public support. I would like to thank the United States Chess Federation Club Development Committee, especially former Chairman Randy Siebert, for allowing us to use the framework of The Guide to a Successful Chess Club (1985) as a basis for this book. In addition, I want to thank FIDE Master Tom Brownscombe (NV), National Tournament Director, and the United States Chess Federation (US Chess) for their continuing help in the preparation of this publication. Scholastic chess, under the guidance of US Chess, has greatly expanded and made it possible for the wide distribution of this Guide. I look forward to working with them on many projects in the future. The following scholastic organizers reviewed various editions of this work and made many suggestions, which have been included. Thanks go to Jay Blem (CA), Leo Cotter (CA), Stephan Dann (MA), Bob Fischer (IN), Doug Meux (NM), Andy Nowak (NM), Andrew Smith (CA), Brian Bugbee (NY), WIM Beatriz Marinello (NY), WIM Alexey Root (TX), Ernest Schlich (VA), Tim Just (IL), Karis Bellisario and many others too numerous to mention. Finally, a special thanks to my wife, Susan, who has been patient and understanding. Dewain R. Barber Technical Editor: Tim Just (Author of My Opponent is Eating a Doughnut and Just Law; Editor 5th, 6th and 7th editions of the Official Rules of Chess). -

Contents Chess Mag - 21 6 10 21/06/2020 13:57 Page 3
01-01 Cover - July 2020_Layout 1 21/06/2020 14:21 Page 1 02-02 New in Chess advert_Layout 1 21/06/2020 14:03 Page 1 03-03 Contents_Chess mag - 21_6_10 21/06/2020 13:57 Page 3 Chess Contents Founding Editor: B.H. Wood, OBE. M.Sc † Executive Editor: Malcolm Pein Editorial....................................................................................................................4 Editors: Richard Palliser, Matt Read Malcolm Pein on the latest developments in the game Associate Editor: John Saunders Subscriptions Manager: Paul Harrington 60 Seconds with...Maria Emelianova..........................................................7 Twitter: @CHESS_Magazine We catch up with the leading chess photographer and streamer Twitter: @TelegraphChess - Malcolm Pein Enter the Dragon .................................................................................................8 Website: www.chess.co.uk Top seeds China proved too strong in FIDE’s Nations Cup Subscription Rates: How Good is Your Chess?..............................................................................12 United Kingdom Daniel King examines Yu Yangyi’s key win for China 1 year (12 issues) £49.95 2 year (24 issues) £89.95 Dubov Delivers...................................................................................................16 3 year (36 issues) £125 Lindores went online, with rapid experts Carlsen, Nakamura & Dubov Europe 1 year (12 issues) £60 It’s All in the Timing.........................................................................................22 2 year -

Developing Chess Talent
Karel van Delft and Merijn van Delft Developing Chess Talent KVDC © 2010 Karel van Delft, Merijn van Delft First Dutch edition 2008 First English edition 2010 ISBN 978-90-79760-02-2 'Developing Chess Talent' is a translation of the Dutch book 'Schaaktalent ontwikkelen', a publication by KVDC KVDC is situated in Apeldoorn, The Netherlands, and can be reached via www.kvdc.nl Cover photo: Training session Youth Meets Masters by grandmaster Artur Yusupov. Photo Fred Lucas: www.fredlucas.eu Translation: Peter Boel Layout: Henk Vinkes Printing: Wbhrmann Print Service, Zutphen CONTENTS Foreword by Artur Yusupov Introduction A - COACHING Al Top-class sport Al.1 Educational value 17 Al.2 Time investment 17 Al.3 Performance ability 18 A1.4 Talent 18 Al. 5 Motivation 18 A2 Social environment A2.1 Psychology 19 A2.2 Personal development 20 A2.3 Coach 20 A2.4 Role of parents 21 A3 Techniques A3.1 Goal setting 24 A3.2 Training programme 25 A3.3 Chess diary 27 A3.4 Analysis questionnaire 27 A3.5 A cunning plan! 28 A3.6 Experiments 29 A3.7 Insights through games 30 A3.8 Rules of thumb and mnemonics 31 A4 Skills A4.1 Self-management 31 A4.2 Mental training 33 A4.3 Physical factors 34 A4.4 Chess thinking 35 A4.5 Creativity 36 A4.6 Concentration 39 A4.7 Flow 40 A4.8 Tension 40 A4.9 Time management 41 A4.10 Objectivity 44 A4.11 Psychological tricks 44 A4.12 Development process 45 A4.13 Avoiding blunders 46 A4.14 Non-verbal behaviour 46 3 AS Miscellaneous A5.1 Chess as a subject in primary school 47 A5.2 Youth with adults 48 A5.3 Women's chess 48 A5.4 Biographies -

Principles of the Evolution and Extension of the Internet Chess Club, 1995 to Present Mark Ginsburg University of Arizona
Association for Information Systems AIS Electronic Library (AISeL) Americas Conference on Information Systems AMCIS 2001 Proceedings (AMCIS) December 2001 Growing Out of Its Skin: Principles of the Evolution and Extension of the Internet Chess Club, 1995 to Present Mark Ginsburg University of Arizona Follow this and additional works at: http://aisel.aisnet.org/amcis2001 Recommended Citation Ginsburg, Mark, "Growing Out of Its Skin: Principles of the Evolution and Extension of the Internet Chess Club, 1995 to Present" (2001). AMCIS 2001 Proceedings. 293. http://aisel.aisnet.org/amcis2001/293 This material is brought to you by the Americas Conference on Information Systems (AMCIS) at AIS Electronic Library (AISeL). It has been accepted for inclusion in AMCIS 2001 Proceedings by an authorized administrator of AIS Electronic Library (AISeL). For more information, please contact [email protected]. GROWING OUT OF ITS SKIN: PRINCIPLES OF THE EVOLUTION AND EXTENSION OF THE INTERNET CHESS CLUB, 1995 TO PRESENT Mark Ginsburg MIS Department University of Arizona [email protected] Abstract The Internet Chess Club, or ICC, is a highly successful virtual gaming community. This paper examines the evolution from its 1995 inception as a pure gaming community to the present day as a successful business with over 26,000 paid members. We give a particular focus on the underlying qualities the ICC possesses in order to succeed and grow such as utilization of real-world credibility indicators (titles), a robust economic system, and mechanisms for user-contributed feature extensions. As ICC expands in scope and scale, its segmentation strategies are analyzed as well as the impact of these extensions on its business strategy. -

Sticky Cultures: Memory Publics and Communal Pasts in Competitive
CUS7410.1177/1749975512473460Cultural SociologyFine 4734602013 Article Cultural Sociology 7(4) 395 –414 Sticky Cultures: Memory © The Author(s) 2013 Reprints and permissions: Publics and Communal Pasts in sagepub.co.uk/journalsPermissions.nav DOI: 10.1177/1749975512473460 Competitive Chess cus.sagepub.com Gary Alan Fine Northwestern University, USA Abstract Although examinations of social memory have largely focused on societies and large populations, much remembrance occurs within bounded publics. This memory, especially when it is held in common, ties individuals to their chosen groups, establishing an ongoing reality of affiliation. I term this form of memory work as sticky culture, recognizing the centrality of the linkage of selves and groups. To examine how sticky culture operates, I examine the social world of competitive chess with its deep history and rich literature. More specifically, I examine forms through which chess publics are cemented through remembrances of the past, focusing on the hero, the critical moment, and validated styles. Champions, memorable games, and recognized strategies establish a lasting public. Keywords chess, collective memory, communal, community, culture, groups, leisure, memory, tiny publics Chess gives not only contemporary fame, but lasting remembrance. To be a great chess player is to be surer of immortality than a great statesman or popular author . The chess player’s fame once gained is secure and stable. What one of all the countless chivalry of Spain is so familiar a name as Ruy Lopez? What American (except Washington) is so widely known as Paul Morphy? Chess, in fact, has lasted so long that we are sure it will last forever. Institutions decay, empires fall to pieces, but the game goes on. -

The Effect of Percentage of Attack/Defense Value on Chess Computer Performance Kevin Huang
The Effect of Percentage of Attack/Defense Value on Chess Computer Performance Kevin Huang Percentage of Attack/Defense Style on Chess Computer Performance The style at which a chess computer plays affects the move it plays and its relative performance. Kevin Huang studied the performance of different computer settings with different style proportions and their relative strength. The computer (100% Attack, 50% Attack/50% Defense, 100% Defense) along with the control, software default played individual matches against one another through a series of 15 two-game matches. Each variable played against the software default and other variables. No linear regression was found between percent of attack in computer’s style and its performance. The data refutes the hypothesis because 100% Attack did not perform the best. It was clear that 50% Attack/50% Defense performed 30% relatively better than 100% Attack and 100% Defense. 100% Attack was slightly better than 100% Defense, however the data is insignificant to prove the definite relationship. Real-life application of this experiment is in the field of computing. Computers can be improved in the chess community with better-characterized style. Also this impacts on methods computers use to process (chess used as a good example to compare different computers) and their performance. Future research could be to extrapolate the experiment and relate style (in this case, how a computer decides to make move in chess) to search processes in real-life computers, making processing more efficient when the brute-force method may not be logical. This will allow less processing for better results. Review of Literature Chess is a board game in which players take turns to move their pieces. -
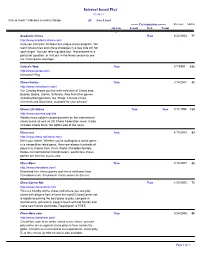
Internet Based Play 01-08-11
Internet based Play 01-08-11 One or more * indicates a recent change. 25 Sites Listed ------- Correspondence------- Revised Mnths On-Lin E-mail Web Postal e Academic Chess True 8/22/2004 77 http://www.academicchess.com/ Here you can learn all about our unique chess program. We teach chess rules and chess strategies in a way kids will not soon forget. You can take a guided tour, find answers to a particular question, or visit our In the News section to see our chess press coverage. Caissa's Web True 7/7/1997 162 http://www.caissa.com/ Interactive Play. Chess Forum True 7/14/2007 42 http://www.chessforum.com/ Our Catalog shows you the wide selection of Chess sets, Boards, Books, Clocks, Software. Also find other games including Backgammon, Go, Shogi, Chinese chess, Checkers and Dominoes, available for your perusal Chess Life Online True True 7/11/1998 150 http://www.uschess.org/clife Weekly news column covering events on the international chess scene as well as US Chess Federation news. It also includes Chess Buzz, the lighter side of the news. Chess.net True 4/11/2003 93 http://www.chess.net/home.html Meet your match. Whether you're looking for a social game or a competitive rated game, there are always hundreds of players to choose from. From World Champion Anatoly Karpov to International Grandmasters, world class chess games are here for you to view. ChessBoss True 7/14/2007 42 http://www.chessboss.com/ Download free chess games and chess softwares from Chessboss.com, the premier chess server on the net. -

My 10 Chess Heroes
The ICC and Coach Dan Heisman present: My 10 Chess Heroes The Internet Chess Club and Coach Dan Heisman present My 10 Chess Heroes The ICC and Coach Dan Heisman present: My 10 Chess Heroes This is a guide that comes with the video course “My 10 Chess Heroes”. We highly recommend you watch the video series AND read this Course Guide to enjoy your product! To watch the videos, click here The ICC and Coach Dan Heisman present: My 10 Chess Heroes Since the beginning of the modern chess era, players like Morphy, Lasker, Keres, Spassky, Fischer, Kasparov, Carlsen and many others have ruled the world of the 64-square board, inspiring and influencing people devoted to the noble game. Studying their games and their life is the fuel that feeds the engines of millions of players. It's almost impossible to become a good chess player without the knowledge that these great artists of the board have given us. In this fantastic video-series, renowned coach Dan Heisman, with his unmistakable and easy- to-understand style, shares with you stories and games of his ten chess heroes. Dan takes you on a journey that will help to discover tactics, positional play, error management, initiative, defense, and all of this presented you by some of the greatest players ever! Here is a list with Dan's 10 chess heroes: Paul Morphy Emanuel Lasker Paul Keres Donald Byrne David Bronstein Boris Spassky Robert J. Fischer John Nunn Garry Kasparov Alexei Shirov In the videos, Dan analyzes and discuss games, showing the style of play, tricks, and nuances that characterize the uniqueness of each of these "monsters.". -

Copyrighted Material
31_584049 bindex.qxd 7/29/05 9:09 PM Page 345 Index attack, 222–224, 316 • Numbers & Symbols • attacked square, 42 !! (double exclamation point), 272 Averbakh, Yuri ?? (double question mark), 272 Chess Endings: Essential Knowledge, 147 = (equal sign), 272 minority attack, 221 ! (exclamation point), 272 –/+ (minus/plus sign), 272 • B • + (plus sign), 272 +/– (plus/minus sign), 272 back rank mate, 124–125, 316 # (pound sign), 272 backward pawn, 59, 316 ? (question mark), 272 bad bishop, 316 1 ⁄2 (one-half fraction), 272 base, 62 BCA (British Chess Association), 317 BCF (British Chess Federation), 317 • A • beginner’s mistakes About Chess (Web site), 343 check, 50, 157 active move, 315 endgame, 147 adjournment, 315 opening, 193–194 adjudication, 315 scholar’s mate, 122–123 adjusting pieces, 315 tempo gains and losses, 50 Alburt, Lev (Comprehensive beginning of game (opening). See also Chess Course), 341 specific moves Alekhine, Alexander (chess player), analysis of, 196–200 179, 256, 308 attacks on opponent, 195–196 Alekhine’s Defense (opening), 209 beginner’s mistakes, 193–194 algebraic notation, 263, 316 centralization, 180–184 analog clock, 246 checkmate, 193, 194 Anand, Viswanathan (chess player), chess notation, 264–266 251, 312 definition, 11, 331 Anderssen, Adolf (chess player), development, 194–195 278–283, 310, 326COPYRIGHTEDdifferences MATERIAL in names, 200 annotation discussion among players, 200 cautions, 278 importance, 193 definition, 12, 316 king safety strategy, 53, 54 overview, 272 knight movements, 34–35 ape-man strategy,