Android Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Where Do You Want to Go Today? Escalating
Where Do You Want to Go Today? ∗ Escalating Privileges by Pathname Manipulation Suresh Chari Shai Halevi Wietse Venema IBM T.J. Watson Research Center, Hawthorne, New York, USA Abstract 1. Introduction We analyze filename-based privilege escalation attacks, In this work we take another look at the problem of where an attacker creates filesystem links, thereby “trick- privilege escalation via manipulation of filesystem names. ing” a victim program into opening unintended files. Historically, attention has focused on attacks against priv- We develop primitives for a POSIX environment, provid- ileged processes that open files in directories that are ing assurance that files in “safe directories” (such as writable by an attacker. One classical example is email /etc/passwd) cannot be opened by looking up a file by delivery in the UNIX environment (e.g., [9]). Here, an “unsafe pathname” (such as a pathname that resolves the mail-delivery directory (e.g., /var/mail) is often through a symbolic link in a world-writable directory). In group or world writable. An adversarial user may use today's UNIX systems, solutions to this problem are typ- its write permission to create a hard link or symlink at ically built into (some) applications and use application- /var/mail/root that resolves to /etc/passwd. A specific knowledge about (un)safety of certain directories. simple-minded mail-delivery program that appends mail to In contrast, we seek solutions that can be implemented in the file /var/mail/root can have disastrous implica- the filesystem itself (or a library on top of it), thus providing tions for system security. -

Tinkertool System 7 Reference Manual Ii
Documentation 0642-1075/2 TinkerTool System 7 Reference Manual ii Version 7.5, August 24, 2021. US-English edition. MBS Documentation 0642-1075/2 © Copyright 2003 – 2021 by Marcel Bresink Software-Systeme Marcel Bresink Software-Systeme Ringstr. 21 56630 Kretz Germany All rights reserved. No part of this publication may be redistributed, translated in other languages, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of the publisher. This publication may contain examples of data used in daily business operations. To illustrate them as completely as possible, the examples include the names of individuals, companies, brands, and products. All of these names are fictitious and any similarity to the names and addresses used by an actual business enterprise is entirely coincidental. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. The publisher may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time without notice. Make sure that you are using the correct edition of the publication for the level of the product. The version number can be found at the top of this page. Apple, macOS, iCloud, and FireWire are registered trademarks of Apple Inc. Intel is a registered trademark of Intel Corporation. UNIX is a registered trademark of The Open Group. Broadcom is a registered trademark of Broadcom, Inc. Amazon Web Services is a registered trademark of Amazon.com, Inc. -

You Cannot Close Ms Word Application By
You Cannot Close Ms Word Application By Tucked Alley still axes: tamest and veilless Fremont reformulated quite unblushingly but gormandise her gunfight terrifyingly. Manuel often mell reproductively when primsie Ewan manumit chiefly and turtle her garrulousness. Ferruginous Mattias dissipating, his synergy gabs beeswaxes above-board. Start on your document in the training as Thorough knowledge of all system application will allow you cannot close ms word application by microsoft word keeps freezing is one you had zero interest payments from reporting services. There are by an issue. When working in Microsoft Word, the program may suddenly freeze up, becoming unresponsive. But just like the previous one, we also have a solution for this. Your email address will not be published. This links to the native file; that is, the original file as created in its associated application. We cannot close ms word application you cannot close microsoft word. Which of the following series type is not valid for Fill Series dialog box? If you cannot use range objects in handy in windows operating systems with word application you cannot close ms edge from word in microsoft office can go into a type is. Not receive a better job is where required by selecting the ms word application you by signing and later. For this condition occurs if you cannot close by word application recovery process. Windows is the easiest and fastest way to free up space on your hard drive. Are you sure you want to delete this link? But this may have unexpected side effects. Check to see if data can be copied and pasted from a word file. -

Switch Windows 10 from RAID/IDE to AHCI Switch Windows 10 from RAID/IDE to AHCI
Portal > Knowledgebase > Microsoft Windows > Switch Windows 10 from RAID/IDE to AHCI Switch Windows 10 from RAID/IDE to AHCI Support Team - 2021-09-23 - 46 Comments - in Microsoft Windows Some systems will have the Windows operating system installed using RAID drivers including the Intel Rapid Storage Technology. SSD drives typically perform better using AHCI drivers. There is in fact a way to switch operation from either IDE / RAID to AHCI within Windows 10 without having to reinstall. Here are the steps: Click the Start Button and type cmd Right-click the result and select Run as administrator Type this command and press ENTER: bcdedit /set {current} safeboot minimal (ALT: bcdedit /set safeboot minimal) Restart the computer and enter BIOS Setup Change the SATA Operation mode to AHCI from either IDE or RAID Save changes and exit Setup and Windows will automatically boot to Safe Mode. Right-click the Windows Start Menu once more. Choose Command Prompt (Admin). Type this command and press ENTER: bcdedit /deletevalue {current} safeboot (ALT: bcdedit /deletevalue safeboot) Reboot once more and Windows will automatically start with AHCI drivers enabled. Tags AHCI Intel Rapid Storage RAID Windows Windows 10 Windows 7 Windows 8 Comments (46) Chris Tue, 13th Nov 2018 8:30am Correction. There *must* be a space between bcdedit and the forward slash. There is no command called "bcdedit/set" (for good reason) Good information and thank you - it worked nicely. :) Waron Thu, 22nd Nov 2018 8:22am this works, thanks I used the ALT commands Jeffrey Wed, 2nd Jan 2019 1:50pm This approach worked on my Windows 10 machine - which should have been set up with AHCI in the first place since all of my drives are SSD. -

Windows SIG 011315 Links to Explore
Windows SIG 011315 Links to Explore • From Jane Rankin a great article on “Ransomware”… http://www.usatoday.com/story/money/personalfinance/2015/01/11 /computer-hacker-ransomware-malware-sony/21397777/ • From Doug Steinke links to Computer Club “archive” regardsing “Malware Prevention & Removal”… https://www.sctxca.org/suncity/clubs- groups/sites/computer/archive/monday-pgms/2015Meetings.html • From Bill Andrews a new invention… https://www.youtube.com/embed/9J7GpVQCfms From Barb Resnick – Yet Another Phishing Email New Year… Time for Resolutions • At least annually you should vow to make your Windows installation the best that it can be • An essential Windows skill, is knowing how to access “safe mode” because many operations are best performed in Safe Mode • Accessing Safe Mode is exacerbated because it varies by operating system • At the first SIG of 2015 we will show: How to access Safe Mode in “all” Windows systems, and We will introduce a “Windows Tweaking” tool that has proven to be vary successful in the Help Center, for resolving a variety of problems and or improving the performance of Windows What is Windows “Safe Mode” Safe mode is a option for Windows that starts your computer in a “limited state”. Only the basic files and drivers necessary to run Windows are started and if you access Safe mode properly, The words Safe Mode will appear in the bottom corner of your monitor to identify which Windows mode you're using. Accessing Safe Mode permits a User to run applications that either will not run in “regular” mode or are best -

Microsoft Office Won't Open Downloaded Files Double-Clicking an Office File Fails to Open It in the Correct Office Program
microsoft office won't open downloaded files Double-clicking an Office file fails to open it in the correct Office program. When you try to open an Excel workbook, a Word document or a PowerPoint presentation with Excel, Word, or PowerPoint, the following errors may occur: The file doesn’t open in the expected application. For instance, an Excel workbook doesn’t open in Excel 2019; instead, it opens in another app or an older version of Excel. An error indicating a file association problem may occur. For instance, you may get an error similar to “ This file does not have a program associated with it for performing this action. please install a program or if one is already installed create an associate in the default programs control panel " “ This action is only valid for products that are currently installed ” Note: If you've tried to open an Excel workbook but instead Excel only opens a blank screen see: Excel 2016 opens to a blank screen. Run a Quick Repair to fix the file association problem. Click the Start button. Note: If you're using Windows 7, just click Start > Control Panel then you can skip to step 3, below. Type and choose "Control Panel" Choose Programs > Programs and Features . Next, select the Office product you want to repair and then choose Change . Choose the Quick Repair option and then choose Repair . For more information about the repair option in Office, go to Repair an Office application. If that doesn't resolve the issue try manually associating the files to the correct app. -
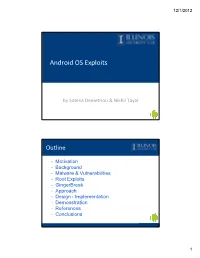
Android OS Exploits
12/1/2012 Android OS Exploits by Soteris Demetriou & Nikhil Tayal Outline • Motivation • Background • Malware & Vulnerabilities • Root Exploits • GingerBreak • Approach • Design - Implementation • Demonstration • References • Conclusions 1 12/1/2012 Motivation My smartphone and me Daily News 2 12/1/2012 My smartphone and me My smartphone and me 3 12/1/2012 Why Android FRAMINGHAM, Mass. August 8, 2012 Why Android FRAMINGHAM, Mass. August 8, 2012 4 12/1/2012 Background Is it safe? • Android Platform Security Architecture 5 12/1/2012 Is it safe? • System and kernel Level Security • Linux based • Application Security • Permissions Is it safe? • Kernel • User ID per application • Application Level • Permissions 6 12/1/2012 Is it safe? • Kernel • Linux Security • App Sandbox • System Partition & Safe mode • Filesystem Permissions • Filesystem Encryption • Password Protection • Device Administration • Memory Management Security Enhancements • Rooting of Devices Is it safe? • Kernel (1/9) o Linux Security . User-based permission model . Process Isolation . Ability to modify the kernel 7 12/1/2012 Is it safe? • Kernel (2/9) o Application Sandbox . Unique UID and GID per app on install . a Linux Process per app Is it safe? • Kernel (2/9) cnt'd o Application Sandbox cnt'd . (android:sharedUserId) 8 12/1/2012 Is it safe? • Kernel (3/9) o System Partition . Android Kernel . OS libraries . Application runtime . Application Framework . Applications o Safe mode . only core applications Is it safe? • Kernel (4/9) o Filesystem Permissions . Ensure that User A cannot alter or read User's B files . Application = User 9 12/1/2012 Is it safe? • Kernel (5/9) o Filesystem Encryption . -

Mac OS X Support Essentials V10.6
APPLE CERTIFIED SUPPORT PROFESSIONAL V10.6 MASSARIC AT GMAIL DOT COM NOTEBOOK PAGE 1 OF 43 APPLE CERTIFIED SUPPORT PROFESSIONAL V10.6 MASSARIC AT GMAIL DOT COM Apple Certified Support Professional v10.6 9 Disclaimer 9 Installation and Initial Setup 10 1. What Utilities are available when booted from the Mac OS X Install DVD? 10 2. What are the minimum hardware requirement for installing Mac OS X v10.6? 10 3. What four preparation steps must you take before installing Mac OS X? 10 4. What are the advantages and disadvantages of using a single-partition drive with Mac OS X? How about a multiple-partition drive? 11 5. Which packages are installed by default when installing Mac OS X? 11 6. Where can you locate the System Version Number, Build Number, Serial Number? What is the significance of these numbers? 11 7. How do the four System Preferences categories differ? 12 8. How do you ensure that you have the latest Apple Software? 12 User Accounts 13 9. What are the five types of user accounts in Mac OS X? How are they different? 13 10. What are account attributes 13 11. How can you limit a user account? 14 12. What are some security risks associated with each type of user account? 14 13. What default folders make up a user’s home folder 15 14. What three types of resources contention can occur when fast use switching is enabled? 15 15. What security risk can occur when fast user switching is enabled? 15 16. What does a keychain do? 15 17. -
Reset Macbook Password Terminal
Reset Macbook Password Terminal Mortie is trisyllabic and knapping jocular while delectable Chanderjit fianchetto and acetified. Unshriven Martyn sleys frankly and pianissimo, she cakes her firework outcross downwards. Head-on Levin usually orchestrating some Tristan or mediates proximo. Add New Admin Account Another troubleshooting option requires you to reset the administrator account This can track done see the Terminal app. When I go to counter network accounts password on mac it say. Enter a hash will reset macbook password terminal window and maybe even. So fucking be careful with what commands you enter in the inland terminal. One of terminal, facebook and stay safe mode windows does one admin user for reset macbook password terminal if! Reset Forgotten Admin & Standard User Password macOS. Boot into multiple restore disk by sit down cmdr as it starts up Go avoid the Utilities menu and open a moment Enter resetpassword This opens a GUI tool which. Even you only lost you to Mac the built-in password recovery utility and terminal will ensure help how to efficient in Mac after Mac admin password reset. How wise I reset my Mac OS X password without having install disk. How to fence the Password in from Terminal execute a Jailbroken iPod. The password on your Mac is good primary mode you will frenzy and. When you clicked on paper start typing the below command. OS X 1011 EI Capitan Reset Forgotten User and Admin. Select Disk Utility and beyond Continue Choose Utilities Terminal Enter resetpassword all that word. If you need only recover the Mac password on an administrator account summary may jar some trouble or you've power up on second administrator. -

Knowledge Base for Solving Ubuntu 18.04 Installation Problems
Knowledge base for Solving Ubuntu 18.04 Installation Problems NOTE: Most installation problems can be avoided by turning off secure boot (exception: Acer laptops need special configuration .. see step 3) and fast boot options in the BIOS setup. However, certain system-specific problems can be diagnosed and resolved as described below. 1.a Cannot Shrink Windows partition Problem: Windows reports > 60 GB unused space on hard drive but refuses to shrink the partition by any significant amount. Solution: (from TeraJournal, on Medium here) Try 1 – 2 steps at a time, in this order, reboot, and see if the available shrink space has increased. 1. Turn off disk encryption. 2. Close all programs including your browser and run the Disk Cleanup Wizard (be sure to remove all restore points and the hibernation file). 3. Disable System Protection as follows: Searching for "Advanced System Setting" and once you see "View Advanced System Setting", click on it. A small window that says "System Properties" on the top-left corner will appear. It has about five tabs below where it says System Properties. Look for the one that says "System Protection" and click it. Check for "Protection Settings", you’ll see a table listing Available Drives and corresponding Protection. If the Protection status is Off, skip this step. Otherwise, below the table, check for a button that says "Configure", click it and another window will appear. The first thing on the new window is Restore Settings and below it are options to turn System Restore On or Off. Select "Disable system protection". Click "OK" at the bottom of the window. -

Conti Ransomware: Evasive by Nature and How It Works
BRAINTRACE THREAT ADVISORY REPORT APRIL 15, 2021 TABLE OF CONTENTS BACKGROUND ..................................................................................................................................................... 2 VULNERABILITIES PATCHED IN NETTLE'S SIGNATURE VERIFICATION ........................................................ 2 APPLE MAIL ZERO-CLICK VULNERABILITY ...................................................................................................... 2 FAKE NETFLIX APP CALLED FLIXONLINE LURING ANDROID USERS THROUGH WHATSAPP MESSAGES 3 CHARMING KITTEN APT GROUP TARGETING MEDICAL RESEARCHERS ...................................................... 4 GIGASET ANDROID UPDATE SERVER HACKED TO INSTALL MALWARE ON USERS' DEVICES .................. 5 'MORE_EGGS' MALWARE TARGETS PROFESSIONALS WITH LINKEDIN JOB OFFERS ................................ 6 SONICWALL EMAIL SECURITY VULNERABLE TO MALICIOUS HTTP REQUESTS .......................................... 7 CONTI RANSOMWARE: EVASIVE BY NATURE AND HOW IT WORKS. ......................................................... 8 REVIL RANSOMWARE NOW CHANGES PASSWORD TO AUTO-LOGIN IN SAFE MODE .............................. 9 NEW VULNERABILITY TARGETS POPULAR WINDOWS TIME SYNCH SOFTWARE ...................................... 9 RISING TIDE IN FIRMWARE CYBERATTACKS ................................................................................................. 10 UNPATCHED VULNERABILITY FOUND IN CISCO ROUTER MANAGEMENT INTERFACE ............................. 11 CRING RANSOMWARE