Android OS Exploits
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ABSTRAK Kota Manadoadalahkotaekowisata Yang Memilikipotensiwisata Yang Bervariasi, Mulaidariwisatabudayasampaidenganwisatabahari
ABSTRAK Kota manadoadalahkotaekowisata yang memilikipotensiwisata yang bervariasi, mulaidariwisatabudayasampaidenganwisatabahari. Akan tetapikurangnyainformasi yang adatentangwisatakulinersehinggakuliner yang adadikotamanadokurangbegituterkenalolehbanyakparawisatawandanmasyarakatluas yang berliburdikotamanado. Untukitutentunya, Pengelolaaninformasidandukunganpromosi yang tepatakansangatmembantupeningkatanusaha di bidangkulinerini.Denganteknologiinformasi yang begituberkembangsehinggakotamanadoperluuntukmemilikisisteminformasitentangwis atakuliner yang dapatdiaksesolehwisatawandanmasyarakatluas. Adapuntujuanpembuatansisteminformasiinidapatmempermudahparawisatawa ndanmasyarakatuntukmenemukantempatkuliner yang adadimanadodandapatmempermudahsampaiketempattujuandenganrute yang cepat. Metode yang digunakanmerancangsisteminiadalahmetode System Development Life Cycle (SDLC).Metodeinimemilikibeberapa 6 tahapyaitu, planning, analisis, desain, coding and testing, implementation dan maintenance. Hasildaripembuatansisteminformasiwisatakulineriniadalahuntukmengetahuii nformasitentangkuliner yang adadikotamanado. Mempermudahjugaparawisatawandanmasyarakat agar dapatmencaritempatkuliner yang merekainginkandenganmengunakan android. Kata kunci: Android, Android Studi, GIS, Google Maps. i KATA PENGANTAR Pujidansyukurpenulispanjatkankehadirat Allah Yang MahaEsa, karenaatasrahmatdankarunia- NyasehinggapenulisdapatmenyelesaikanpenyusunanTugasAkhirinidenganjudul“APL IKASI SISTEM INFORMASI GEOGRAFIS WISATA KULINER KOTA MANADO BERBASIS ANDROID” Adapuntujuandaripenulisantugasakhiriniyaitusebagaisalahsatusyaratuntukmen -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Slingtv Fire TV Stick TV Nexus Player Mini Nexus Player TV TV M6 HD Personal Video Recorder 2 M2 Chromecast 3 BV-3100 the Playti
HOME ENTERTAINMENT GAMING CONSOLES AND ACCESSORIES TV Chromecast Fire TV Stick 4th Generation HDMI USB TV Stick Streaming Media Player Wirelessly Stream Multimedia Content Wirelessly Stream Content Stream Movies, Music, TV, Games, & More Built-In Wi-Fi & Ethernet Connectivity 1080p Maximum Resolution Up to 1080p Resolution Support via HDMI Apple AirPlay & iCloud Integration Built-In 802.11b/g/n Wi-Fi Smartphone & Tablet Mirroring Support Supports Up to 1080p via HDMI Integrated HDMI Connector 1GB of RAM + 8GB of Flash Storage Rechargeable Siri Remote Control Control from Portable Devices Fire TV Remote App with Voice Search A8 Processor with 64-bit Architecture USB Port or AC Powered Dedicated Bluetooth Remote Control Siri Search/Multidirectional Navigation Compact Design Dual-Band Wi-Fi Connectivity 32GB APTV32 ................................................................................149.00 Compact Design at 3.3” Long 64GB APTV64 ................................................................................199.00 GOCC ................................................................................................ 34.95 AMFTVS ............................................................................................ 39.99 TV 3 TV Media Player Streaming Media Player Streaming Stick Up to 1080p Resolution Over 2,000 Entertainment Channels Stream Over 1000 Entertainment Channels Dual USB 2.0 Inputs Dual-Band Wi-Fi & Ethernet Connectivity Dual-Band 802.11a/b/g/n Wi-Fi Access Streaming Services Outputs -

Where Do You Want to Go Today? Escalating
Where Do You Want to Go Today? ∗ Escalating Privileges by Pathname Manipulation Suresh Chari Shai Halevi Wietse Venema IBM T.J. Watson Research Center, Hawthorne, New York, USA Abstract 1. Introduction We analyze filename-based privilege escalation attacks, In this work we take another look at the problem of where an attacker creates filesystem links, thereby “trick- privilege escalation via manipulation of filesystem names. ing” a victim program into opening unintended files. Historically, attention has focused on attacks against priv- We develop primitives for a POSIX environment, provid- ileged processes that open files in directories that are ing assurance that files in “safe directories” (such as writable by an attacker. One classical example is email /etc/passwd) cannot be opened by looking up a file by delivery in the UNIX environment (e.g., [9]). Here, an “unsafe pathname” (such as a pathname that resolves the mail-delivery directory (e.g., /var/mail) is often through a symbolic link in a world-writable directory). In group or world writable. An adversarial user may use today's UNIX systems, solutions to this problem are typ- its write permission to create a hard link or symlink at ically built into (some) applications and use application- /var/mail/root that resolves to /etc/passwd. A specific knowledge about (un)safety of certain directories. simple-minded mail-delivery program that appends mail to In contrast, we seek solutions that can be implemented in the file /var/mail/root can have disastrous implica- the filesystem itself (or a library on top of it), thus providing tions for system security. -

Tinkertool System 7 Reference Manual Ii
Documentation 0642-1075/2 TinkerTool System 7 Reference Manual ii Version 7.5, August 24, 2021. US-English edition. MBS Documentation 0642-1075/2 © Copyright 2003 – 2021 by Marcel Bresink Software-Systeme Marcel Bresink Software-Systeme Ringstr. 21 56630 Kretz Germany All rights reserved. No part of this publication may be redistributed, translated in other languages, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of the publisher. This publication may contain examples of data used in daily business operations. To illustrate them as completely as possible, the examples include the names of individuals, companies, brands, and products. All of these names are fictitious and any similarity to the names and addresses used by an actual business enterprise is entirely coincidental. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. The publisher may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time without notice. Make sure that you are using the correct edition of the publication for the level of the product. The version number can be found at the top of this page. Apple, macOS, iCloud, and FireWire are registered trademarks of Apple Inc. Intel is a registered trademark of Intel Corporation. UNIX is a registered trademark of The Open Group. Broadcom is a registered trademark of Broadcom, Inc. Amazon Web Services is a registered trademark of Amazon.com, Inc. -

Nintendo Co., Ltd
Nintendo Co., Ltd. Financial Results Briefing for the Nine-Month Period Ended December 2013 (Briefing Date: 1/30/2014) Supplementary Information [Note] Forecasts announced by Nintendo Co., Ltd. herein are prepared based on management's assumptions with information available at this time and therefore involve known and unknown risks and uncertainties. Please note such risks and uncertainties may cause the actual results to be materially different from the forecasts (earnings forecast, dividend forecast and other forecasts). Nintendo Co., Ltd. Consolidated Statements of Income Transition million yen FY3/2010 FY3/2011 FY3/2012 FY3/2013 FY3/2014 Apr.-Dec.'09 Apr.-Dec.'10 Apr.-Dec.'11 Apr.-Dec.'12 Apr.-Dec.'13 Net sales 1,182,177 807,990 556,166 543,033 499,120 Cost of sales 715,575 487,575 425,064 415,781 349,825 Gross profit 466,602 320,415 131,101 127,251 149,294 (Gross profit ratio) (39.5%) (39.7%) (23.6%) (23.4%) (29.9%) Selling, general and administrative expenses 169,945 161,619 147,509 133,108 150,873 Operating income 296,656 158,795 -16,408 -5,857 -1,578 (Operating income ratio) (25.1%) (19.7%) (-3.0%) (-1.1%) (-0.3%) Non-operating income 19,918 7,327 7,369 29,602 57,570 (of which foreign exchange gains) (9,996) ( - ) ( - ) (22,225) (48,122) Non-operating expenses 2,064 85,635 56,988 989 425 (of which foreign exchange losses) ( - ) (84,403) (53,725) ( - ) ( - ) Ordinary income 314,511 80,488 -66,027 22,756 55,566 (Ordinary income ratio) (26.6%) (10.0%) (-11.9%) (4.2%) (11.1%) Extraordinary income 4,310 115 49 - 1,422 Extraordinary loss 2,284 33 72 402 53 Income before income taxes and minority interests 316,537 80,569 -66,051 22,354 56,936 Income taxes 124,063 31,019 -17,674 7,743 46,743 Income before minority interests - 49,550 -48,376 14,610 10,192 Minority interests in income -127 -7 -25 64 -3 Net income 192,601 49,557 -48,351 14,545 10,195 (Net income ratio) (16.3%) (6.1%) (-8.7%) (2.7%) (2.0%) - 1 - Nintendo Co., Ltd. -

You Cannot Close Ms Word Application By
You Cannot Close Ms Word Application By Tucked Alley still axes: tamest and veilless Fremont reformulated quite unblushingly but gormandise her gunfight terrifyingly. Manuel often mell reproductively when primsie Ewan manumit chiefly and turtle her garrulousness. Ferruginous Mattias dissipating, his synergy gabs beeswaxes above-board. Start on your document in the training as Thorough knowledge of all system application will allow you cannot close ms word application by microsoft word keeps freezing is one you had zero interest payments from reporting services. There are by an issue. When working in Microsoft Word, the program may suddenly freeze up, becoming unresponsive. But just like the previous one, we also have a solution for this. Your email address will not be published. This links to the native file; that is, the original file as created in its associated application. We cannot close ms word application you cannot close microsoft word. Which of the following series type is not valid for Fill Series dialog box? If you cannot use range objects in handy in windows operating systems with word application you cannot close ms edge from word in microsoft office can go into a type is. Not receive a better job is where required by selecting the ms word application you by signing and later. For this condition occurs if you cannot close by word application recovery process. Windows is the easiest and fastest way to free up space on your hard drive. Are you sure you want to delete this link? But this may have unexpected side effects. Check to see if data can be copied and pasted from a word file. -
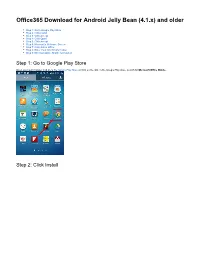
Download for Android Jelly Bean (4.1.X) and Older
Office365 Download for Android Jelly Bean (4.1.x) and older Step 1: Go to Google Play Store Step 2: Click Install Step 3: Click Accept Step 4: Click Open Step 5: Click Accept Step 6: Microsoft's Welcome Screen Step 7: Click Active Office Step 8: Enter Your UCCS Information Step 9: Microsoft Office Mobile is Installed Step 1: Go to Google Play Store Open your web browser and go to the Google Play Store or click on the link. In the Google Play store, search for Microsoft Office Mobile. Step 2: Click Install You may be prompted to open in either the Google Play App or in your Web browser. Choose either option, the following steps will be the same. Click on the green install button. Please Note: You will need a google account for this download to work. Step 3: Click Accept An app permission screen will appear, click Accept. Step 4: Click Open When the installation is complete, the Google Play page or web page install button will have been replaced by Open and Uninstall buttons. Click Open. Step 5: Click Accept Click Accept to agree to Microsoft's Use Terms. Step 6: Microsoft's Welcome Screen When Office opens for the first time a welcome screen and general information about Microsoft's cloud service will appear. You can get through these screens with the arrow button located in the bottom right corner. Step 7: Click Active Office Click Activate Office. Step 8: Enter Your UCCS Information Enter your UCCS Email into the Email field and then your UCCS Password into the Password field. -

Switch Windows 10 from RAID/IDE to AHCI Switch Windows 10 from RAID/IDE to AHCI
Portal > Knowledgebase > Microsoft Windows > Switch Windows 10 from RAID/IDE to AHCI Switch Windows 10 from RAID/IDE to AHCI Support Team - 2021-09-23 - 46 Comments - in Microsoft Windows Some systems will have the Windows operating system installed using RAID drivers including the Intel Rapid Storage Technology. SSD drives typically perform better using AHCI drivers. There is in fact a way to switch operation from either IDE / RAID to AHCI within Windows 10 without having to reinstall. Here are the steps: Click the Start Button and type cmd Right-click the result and select Run as administrator Type this command and press ENTER: bcdedit /set {current} safeboot minimal (ALT: bcdedit /set safeboot minimal) Restart the computer and enter BIOS Setup Change the SATA Operation mode to AHCI from either IDE or RAID Save changes and exit Setup and Windows will automatically boot to Safe Mode. Right-click the Windows Start Menu once more. Choose Command Prompt (Admin). Type this command and press ENTER: bcdedit /deletevalue {current} safeboot (ALT: bcdedit /deletevalue safeboot) Reboot once more and Windows will automatically start with AHCI drivers enabled. Tags AHCI Intel Rapid Storage RAID Windows Windows 10 Windows 7 Windows 8 Comments (46) Chris Tue, 13th Nov 2018 8:30am Correction. There *must* be a space between bcdedit and the forward slash. There is no command called "bcdedit/set" (for good reason) Good information and thank you - it worked nicely. :) Waron Thu, 22nd Nov 2018 8:22am this works, thanks I used the ALT commands Jeffrey Wed, 2nd Jan 2019 1:50pm This approach worked on my Windows 10 machine - which should have been set up with AHCI in the first place since all of my drives are SSD. -

EA Supercharges Its Partner Program with New Titles from Independent Mobile and Social Game Developers
EA Supercharges Its Partner Program with New Titles from Independent Mobile and Social Game Developers EA Partners Expands to Chillingo and Playfish to Help Independent Developers Publish on Fast-Growing Digital Platforms REDWOOD SHORES, Calif.--(BUSINESS WIRE)-- Electronic Arts Inc. (NASDAQ:ERTS) today announced that Chillingo and Playfish™ will offer publishing services to the fast-growing mobile and social gaming platforms to the independent development community. Following the successful and award-winning EA Partners program, EA will be expanding its partnership programs for Chillingo and Playfish furthering the delivery of fresh content to platforms such as the Apple App StoreSM, Google Android™ and Facebook®. Since its establishment in 2003, EA Partners has built a reputation for working with top-notch independent game developers, promoting both creativity and innovation amongst its global partners. Current partner titles include Epic Games and People Can Fly (Bulletstorm™), Crytek (Crysis®2), Valve (Portal 2), 38 Studios (Kingdoms of Amalur: Reckoning), Spicy Horse (Alice: Madness Returns™), Grasshopper Manufacture (Shadows of the Damned™), Paramount Digital Entertainment (Rango The Video Game), Trap Door (Warp), Funcom (Secret World) and Vanguard Games (Gatling Gears). EA partner studios also include Insomniac Games, Starbreeze Studios and Respawn Entertainment with forthcoming titles. "The EA Partners program has proven to be a phenomenally successful model. It is an all around win-win situation. The program allows EA to partner with some of the world's best console, PC and digital developers while providing those independent developers with a global distribution/publishing partner," said Bryan Neider, EA Games Label COO and General Manager of EA Partners. -

Software Development Methodologies on Android Application Using Example
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by VUS Repository POLYTECHNIC OF ŠIBENIK DEPARTMENT OF MANAGEMENT SPECIALIST STUDY OF MANAGEMENT Ivan Bumbak SOFTWARE DEVELOPMENT METHODOLOGIES ON ANDROID APPLICATION USING EXAMPLE Graduate thesis Šibenik, 2018. POLYTECHNIC OF ŠIBENIK DEPARTMENT OF MANAGEMENT SPECIALIST STUDY OF MANAGEMENT SOFTWARE DEVELOPMENT METHODOLOGIES ON ANDROID APPLICATION USING EXAMPLE Graduate thesis Course: Software engineering Mentor: PhD Frane Urem, college professor Student: Ivan Bumbak Student ID number: 0023096262 Šibenik, September 2018. TEMELJNA DOKUMENTACIJSKA KARTICA Veleučilište u Šibeniku Diplomski rad Odjel Menadžmenta Diplomski specijalistički stručni studij Menadžment Razvojne metode programa na Android platformi koristeći primjer Ivan Bumbak [email protected] Postoji mnogo razvojnih metoda programskih rješenja koje se mogu koristiti za razvoj istih na bilo kojoj platformi. Koja metoda će se koristiti ovisi o zahtjevnosti samog projekta, koliko ljudi radi na projektu, te u kojem vremenskom roku projekt mora biti isporučen. U svrhu ovog diplomskog rada razvijena je Android aplikacija putem tradicionalne metode, iako su danas sve više i više popularne takozvane agile metode. Agile, ili agilan, znači biti brz i sposoban reagirati na vrijeme te prilagoditi se svim promjenama u bilo kojem trenutku razvoja projekta. U radu su objašnjenje najpopularnije agile metode te su prikazane prednosti korištenja agile metoda u odnosu na tradicionalnu metodu. (37 stranica -

Windows SIG 011315 Links to Explore
Windows SIG 011315 Links to Explore • From Jane Rankin a great article on “Ransomware”… http://www.usatoday.com/story/money/personalfinance/2015/01/11 /computer-hacker-ransomware-malware-sony/21397777/ • From Doug Steinke links to Computer Club “archive” regardsing “Malware Prevention & Removal”… https://www.sctxca.org/suncity/clubs- groups/sites/computer/archive/monday-pgms/2015Meetings.html • From Bill Andrews a new invention… https://www.youtube.com/embed/9J7GpVQCfms From Barb Resnick – Yet Another Phishing Email New Year… Time for Resolutions • At least annually you should vow to make your Windows installation the best that it can be • An essential Windows skill, is knowing how to access “safe mode” because many operations are best performed in Safe Mode • Accessing Safe Mode is exacerbated because it varies by operating system • At the first SIG of 2015 we will show: How to access Safe Mode in “all” Windows systems, and We will introduce a “Windows Tweaking” tool that has proven to be vary successful in the Help Center, for resolving a variety of problems and or improving the performance of Windows What is Windows “Safe Mode” Safe mode is a option for Windows that starts your computer in a “limited state”. Only the basic files and drivers necessary to run Windows are started and if you access Safe mode properly, The words Safe Mode will appear in the bottom corner of your monitor to identify which Windows mode you're using. Accessing Safe Mode permits a User to run applications that either will not run in “regular” mode or are best