Stalking Victims 9
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Philippines's Constitution of 1987
PDF generated: 26 Aug 2021, 16:44 constituteproject.org Philippines's Constitution of 1987 This complete constitution has been generated from excerpts of texts from the repository of the Comparative Constitutions Project, and distributed on constituteproject.org. constituteproject.org PDF generated: 26 Aug 2021, 16:44 Table of contents Preamble . 3 ARTICLE I: NATIONAL TERRITORY . 3 ARTICLE II: DECLARATION OF PRINCIPLES AND STATE POLICIES PRINCIPLES . 3 ARTICLE III: BILL OF RIGHTS . 6 ARTICLE IV: CITIZENSHIP . 9 ARTICLE V: SUFFRAGE . 10 ARTICLE VI: LEGISLATIVE DEPARTMENT . 10 ARTICLE VII: EXECUTIVE DEPARTMENT . 17 ARTICLE VIII: JUDICIAL DEPARTMENT . 22 ARTICLE IX: CONSTITUTIONAL COMMISSIONS . 26 A. COMMON PROVISIONS . 26 B. THE CIVIL SERVICE COMMISSION . 28 C. THE COMMISSION ON ELECTIONS . 29 D. THE COMMISSION ON AUDIT . 32 ARTICLE X: LOCAL GOVERNMENT . 33 ARTICLE XI: ACCOUNTABILITY OF PUBLIC OFFICERS . 37 ARTICLE XII: NATIONAL ECONOMY AND PATRIMONY . 41 ARTICLE XIII: SOCIAL JUSTICE AND HUMAN RIGHTS . 45 ARTICLE XIV: EDUCATION, SCIENCE AND TECHNOLOGY, ARTS, CULTURE, AND SPORTS . 49 ARTICLE XV: THE FAMILY . 53 ARTICLE XVI: GENERAL PROVISIONS . 54 ARTICLE XVII: AMENDMENTS OR REVISIONS . 56 ARTICLE XVIII: TRANSITORY PROVISIONS . 57 Philippines 1987 Page 2 constituteproject.org PDF generated: 26 Aug 2021, 16:44 • Source of constitutional authority • General guarantee of equality Preamble • God or other deities • Motives for writing constitution • Preamble We, the sovereign Filipino people, imploring the aid of Almighty God, in order to build a just and humane society and establish a Government that shall embody our ideals and aspirations, promote the common good, conserve and develop our patrimony, and secure to ourselves and our posterity the blessings of independence and democracy under the rule of law and a regime of truth, justice, freedom, love, equality, and peace, do ordain and promulgate this Constitution. -

Imdb's Ios and ANDROID APPS HAVE NOW BEEN DOWNLOADED MORE THAN 50 MILLION TIMES
IMDb’S iOS AND ANDROID APPS HAVE NOW BEEN DOWNLOADED MORE THAN 50 MILLION TIMES Just-Launched Redesign of IMDb’s Movies & TV App for iPad Includes Discovery Features, Personalized Recommendations and Watchlist Enhancements IMDb’s Portfolio of Leading Mobile Entertainment Apps Achieved Significant Milestones and Garnered Media Acclaim in 2012 SEATTLE, WA. – December 20, 2012—IMDb, the world’s most popular and authoritative source for movie, TV and celebrity content, today announced that its award-winning Movies & TV apps for iOS and Android have each been downloaded more than 25 million times for a total of more than 50 million combined user downloads. Over the last 5 months, IMDb’s mobile-optimized website and apps have received an average of more than 175 million visits per month. Additionally, IMDb just launched a redesigned version of its acclaimed iPad app featuring highly anticipated discovery features, personalized recommendations and Watchlist enhancements. To learn more and download IMDb’s free apps, go to: http://www.imdb.com/apps/ “2012 has been a significant year for innovation and usage of IMDb’s leading mobile apps for iOS, Android and Kindle Fire,” said Col Needham, IMDb’s founder and CEO. “Our mission is to continually surprise and delight our customers with new features that will revolutionize the movie-watching experience such as ‘X-Ray for Movies,’ which we launched in September 2012 exclusively on the new Kindle Fire HD devices. We look forward to raising the bar on behalf of our customers in 2013.” IMDb’s iPad App Redesign Beginning today, an update (available through the iTunes App Store) to IMDb’s popular iPad app includes a complete redesign focused on discovery features, personalized recommendations and Watchlist enhancements. -

STALKERS and Their Victims
STALKERS and their victims Paul E. Mullen Michele Pathé and Rosemary Purcell The Pitt Building, Trumpington Street, Cambridge, United Kingdom The Edinburgh Building, Cambridge CB2 2RU, UK http://www.cup.cam.ac.uk 40 West 24th Street, New York, NY 10011–4211, USA http://www.cup.org 10 Stamford Road, Oakleigh, Melbourne 3166, Australia Ruiz de Alarcón 13, 28014 Madrid, Spain © Cambridge University Press 2000 This book is in copyright. Subject to statutory exception and to the provisions of relevant collective licensing agreements, no reproduction of any part may take place without the written permission of Cambridge University Press. First published 2000 Printed in the United Kingdom at the University Press, Cambridge Typeface Minion 10.5/14pt System QuarkXPress™ [] A catalogue record for this book is available from the British Library Library of Congress Cataloguing in Publication data Mullen, Paul E. Stalkers and their victims/Paul E. Mullen, Michele Pathé, and Rosemary Purcell. p. cm. ISBN 0 521 66950 2 (pbk.) 1. Stalking. 2. Stalkers. 3. Women – Crimes against – Prevention. I. Pathé, Michele, 1959– II. Purcell, Rosemary, 1969– III. Title. HV6594.M85 2000 362.88 – dc21 99-044607 ISBN 0 521 66950 2 paperback Every effort has been made in preparing this book to provide accurate and up-to-date information which is in accord with accepted standards and practice at the time of publication. Nevertheless, the authors, editors and publisher can make no warranties that the information contained herein is totally free from error, not least because clinical standards are constantly changing through research and regu- lation. The authors, editors and publisher therefore disclaim all liability for direct or consequential damages resulting from the use of material contained in this book. -
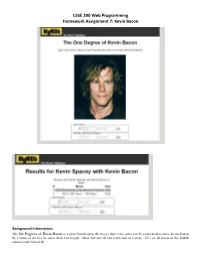
CSSE 290 Web Programming Homework Assignment 7: Kevin Bacon
CSSE 290 Web Programming Homework Assignment 7: Kevin Bacon . Background Information: The Six Degrees of Kevin Bacon is a game based upon the theory that every actor can be connected to actor Kevin Bacon by a chain of movies no more than 6 in length. Most, but not all, can reach him in 6 steps. 12% of all actors in the IMDB cannot reach him at all. Your task for this assignment is to write the HTML/CSS and PHP code for a web site called MyMDb that mimics part of the popular IMDb movie database site. Your site will show the movies in which another actor has appeared with Kevin Bacon. The site will also show a list of all movies in which the other actor has appeared. (If you prefer, you may use another actor rather than Kevin Bacon as the center point, so long as that actor is in our database and has a large number of connections to other actors.) The following provided files are on the course web site to get started: top.html, some common HTML that should appear at the beginning of every page bottom.html, some common HTML that should appear at the end of every page mymdb.php, the initial front page that welcomes the user to the site The front search page mymdb.php contains two forms in which the user can type an actor's name. The user can search for every film the actor has appeared in (which submits to search-all.php), or every film where both the actor and Kevin Bacon have appeared (which submits to search-kevin.php). -

Between Belief and Delusion: Cult Members and the Insanity Plea
REGULAR ARTICLE Between Belief and Delusion: Cult Members and the Insanity Plea Brian Holoyda, MD, MPH, and William Newman, MD Cults are charismatic groups defined by members’ adherence to a set of beliefs and teachings that differ from those of mainstream religions. Cult beliefs may appear unusual or bizarre to those outside of the organization, which can make it difficult for an outsider to know whether a belief is cult-related or delusional. In accordance with these beliefs, or at the behest of a charismatic leader, some cult members may participate in violent crimes such as murder and later attempt to plead not guilty by reason of insanity (NGRI). It is therefore necessary for forensic experts who evaluate cult members to understand how the court has responded to such individuals and their beliefs when they mount a defense of NGRI for murder. Based on a review of extant appellate court case law, cult member defendants have not yet successfully pleaded NGRI on the basis of cult involvement, despite receiving a broad array of psychiatric diagnoses that could qualify for such a defense. With the reintroduction of cult involvement in the DSM-5 criteria for other specified dissociative disorder, however, there may be a resurgence of dissociative-type diagnoses in future cult-related cases, both criminal and civil. J Am Acad Psychiatry Law 44:53–62, 2016 Cults are generally considered to be new charismatic organization. Because of this perception, it can be groups that espouse religious doctrine that differs difficult for an outsider to know whether a belief is from mainstream beliefs. -

Sustainability Baseline Assessment for the City of Dawson Creek
Sustainability Baseline Assessment for the City of Dawson Creek FINAL REPORT Holland Barrs Planning Group December 2007 “Sustainability is nobody’s responsibility… that’s why it’s everybody’s responsibility” - Bryna Casey, Youth Coordinator For Youth Sustainability Development, June 8, 2007. Dawson Creek Sustainability Baseline Assessment December 2007 Holland Barrs Planning Group 2 of 55 Table of Contents Table of Contents...................................................................................................................................................................................................... 3 1.0 Introduction..................................................................................................................................................................................................... 4 2.0 Methodology................................................................................................................................................................................................... 4 3.0 Baseline Results ............................................................................................................................................................................................ 4 3.1 Create Compact, Complete & Dense Communities ................................................................................................................................ 6 3.2 Develop an Environmentally-Friendly, Community-Oriented Transportation System.......................................................................... -

Domestic Violence, Stalking, and Antistalking Legislation
NT OF ME J T US U.S. Department of Justice R T A I P C E E D B O J C S Office of Justice Programs F A V M F O I N A C I J S R E BJ G O OJJ DP O F PR National Institute of Justice JUSTICE National Institute of Justice Research Report Domestic Violence, Stalking, and Antistalking Legislation An Annual Report to Congress under the Violence Against Women Act The studies reported here were mandated by Title IV, the Violence Against Women Act, of the Violent Crime Control and Law Enforcement Act of 1994. The enabling legislation is: SUBTITLE F—NATIONAL STALKER AND DOMESTIC VIOLENCE REDUCTION SECTION 40610, REPORT TO CONGRESS, WHICH STATES THE FOLLOWING: The Attorney General shall submit to the Congress an annual report, beginning one year after the date of the enactment of the Act, that provides information concerning the incidence of stalking and domestic violence, and evaluates the effectiveness of antistalking efforts and legislation. Domestic Violence, Stalking, and Antistalking Legislation An Annual Report to Congress under the Violence Against Women Act National Institute of Justice A Publication of the National Institute of Justice, Office of Justice Programs, U.S. Department of Justice April 1996 U.S. Department of Justice Office of Justice Programs National Institute of Justice Jeremy Travis, J.D. Director This report was edited by Mary Graham, NIJ publications manager, with support from Jolene Hernon, Anne Pritchett, and Patti Schwartz, Cygnus Corporation. The National Institute of Justice acknowl- edges with thanks the contributions of the following reviewers: Office of Policy Development, U.S. -

The Chinese Mestizo in Philippine History
Reprinted from THE JOURNAL SOUTHEAST ASIAN HISTORY (Vol. 5, No. 1) March 1964 (pp. 62-100) The Chinese Mestizo in Philippine History By E. Wickberg East Asian Series, Reprint No. 10 INTERNATIONAL STUDIES CENTER FOR EAST ASIAN STUDIES THE UNIVERSITY OF KANSAS Lawrence, Kansas CENTER FOR EAST ASIAN STUDIES 1. The Patrimonial Thesis and Pre-Modern Japa nese Herrschaft, by Norman Jacobs. 2. The Phantom Slasher of Taipei: Mass Hysteria in a Non-Western Society, by Norman Jacobs. 3. Early Chinese Economic Influences in the Philip pines, by Edgar Wickberg. 4. Some Aspects of Korean Acculturation and Value Orientation Since 1950, by Felix Moos. 5. The Philippine Political Party System, by Carl H. Lande. 6. Religion and Politics in Japan: The Case of the Soka Gakkai, by Felix Moos. 7. Some Aspects of Park Chang No Kyo—A Korean Revitalization Movement, by Felix Moos. 8. The Philippines, by Carl H, Lande. 9. General Artemio Ricarte & Japan, by Grant K. Goodman. 10. The Chinese Mestizo in Philippine History, by E. Wickberg. THE CHINESE MESTIZO IN PHILIPPINE HISTORY E. VVlCKBERG. THE CHINESE MESTIZO IN PHILIPPINE HISTORY* E. WlCKBERG. Students of Southeast Asian history have had little to say about the historical role played by the Chinese mestizo in that region. Although studies of the Chinese in Southeast Asia have devoted some attention to the position of native-born Chinese as opposed to immigrant Chinese, the native-born Chinese of mixed Chinese- native ancestry is rarely singled out for specific treatment. Perhaps this is because in most parts of Southeast Asia the Chinese mestizos (to use the Philippine term for persons of mixed Chinese-native ancestry) have not been formally and legally recognized as a separate group — one whose membership is strictly defined by genealogical considerations rather then by place of birth, and one which, by its possession of a unique combination of cultural characteristics, could be easily distinguished from both the Chinese and the native com munities. -

Philippines, March 2006
Library of Congress – Federal Research Division Country Profile: Philippines, March 2006 COUNTRY PROFILE: PHILIPPINES March 2006 COUNTRY Formal Name: Republic of the Philippines (Republika ng Pilipinas). Short Form: Philippines (Pilipinas). Term for Citizen(s): Filipino(s). Capital: Manila. Click to Enlarge Image Major Cities: Located on Luzon Island, Metropolitan Manila, including the adjacent Quezon City and surrounding suburbs, is the largest city in the Philippines, with about 12 million people, or nearly 14 percent of the total population. Other large cities include Cebu City on Cebu Island and Davao City on Mindanao Island. Independence: The Philippines attained independence from Spain on June 12, 1898, and from the United States on July 4, 1946. Public Holidays: New Year’s Day (January 1), Holy Thursday (also called Maundy Thursday, movable date in March or April), Good Friday (movable date in March or April), Araw ng Kagitingan (Day of Valor, commonly called Bataan Day outside of the Philippines, April 9), Labor Day (May 1), Independence Day (June 12), National Heroes Day (last Sunday of August), Bonifacio Day (celebration of the birthday of Andres Bonifacio, November 30), Eid al Fitr (the last day of Ramadan, movable date), Christmas Day (December 25), Rizal Day (the date of the execution by the Spanish of José Rizal in 1896, December 30). Flag: The flag of the Philippines has two equal horizontal bands of blue (top) and red with a white equilateral triangle based on the hoist side; in the center of the triangle is a yellow sun with eight primary rays (each containing three individual rays), and in each corner of the triangle is Click to Enlarge Image a small yellow five-pointed star. -

Civil Society Briefs: Philippines
CIVIL SOCIETY BRIEFS PHILIPPINES Country and Government Context Civil Society: An Overview The Republic of the Philippines is an archipelago The basis for civil society in the Philippines comes from the of more than 7,000 islands in Southeast Asia. Its Filipino concepts of pakikipagkapwa (holistic interaction with population in 2010 was estimated at 94 million.a others) and kapwa (shared inner self). Voluntary assistance The country was a Spanish colony from 1521 to or charity connotes for Filipinos an equal status between the 1898. Following the Philippine Revolution, provider of assistance and the recipient, which is embodied independence was declared on 12 June 1898 in the terms damayan (assistance of peers in periods of crisis) and the First Philippine Republic was established. and pagtutulungan (mutual self-help). The Western notion It was then claimed by the United States and, of kawanggawa (charity) may have been introduced to the after the Philippine–American War (1899–1902), Philippines by Catholic missionaries.1 became an American colony for nearly half a century. After a brief Japanese Occupation during World War II, the Philippines regained During the Spanish colonial period, the Roman Catholic independence on 4 July 1946. The country was Church and the religious orders established the first welfare placed under martial law from 1972 to 1981 organizations in the Philippines. They founded parochial schools, and formal political democracy was reestablished orphanages, and hospitals that were mostly reserved for the only after the 1986 People Power Revolution. local elite. The church also established foundations and cofradías The president serves for a single 6-year term (brotherhoods), which encouraged neighborly behavior, such as and is chief executive, head of state, and visiting the sick and helping with town fiesta preparations. -
CVWD Enewsletter Feb1521 V1.5 Copy
COACHELLA VALLEY WATER DISTRICT Construction Update for February 15-19 THIS WEEK, the contractor will begin the abandonment process for the old water mains. Crews have been cleared to work on President’s Day on Monday, February 15. They will be breaking up concrete around the valves at intersections and around old fire hydrants along Pineknoll Avenue, Turnberry Isle Drive, Skycrest Road and Wyndham Road. The work is preparation for next week, when the pipes will be emptied of any residual water, capped off and filled with slurry. On Wednesday, February 17, the exit at Avenue 38 and Adams Street will be closed to traffic. Please watch for crews working in streets and follow traffic control signs. Purple Sagebrush Ave Looking ahead Crystal Falls Rd Turnberry Isle Dr Street grinding to prepare for Wyndham Rd paving on Pineknoll Avenue and Waterfall Dr the streets east is expected during the first week of March; Bougainvillea Dr Skycrest Rd paving is tentatively scheduled Abalo ne Wa to begin March 11. Pleasant Dr y Silver Lake Festival Dr T err Golden Pebble Ave a ce Pineknoll Ave Hidden Palms Dr Ta marin d P od C t Autumn Ln Tamarisk Flower Dr ADAMS ST Dancing Waters Rd Tang erine Ct Sandalwood Pl Avenue 38 Signal CT Mimosa Dr Fountain Hills Dr Naranja Dr Rancho Los Coyotes Dr Dr Coyotes Los Rancho Edgebrook Ln ATTENTION! PROPERTY DAMAGE RELEASE FORM Homeowners in areas where construction is complete (Phases 1A and 1B) have been sent a Property Damage Release Form by the contractor, DCI Construction. Those who have not signed and returned the form will be sent another copy by email and/or mail. -

Creating an Effective Stalking Protocol
U.S. Department of Justice Office of Community Oriented Policing Services Creating an Effective Stalking Protocol www.cops.usdoj.gov Creating an Effective Stalking Protocol Submitted by the National Center for Victims of Crime April 2002 This publication was supported through Grant #98CKWXK052 from the Office of Community Oriented Policing Services, U.S. Department of Justice. The opinions expressed herein are the author's and do not necessarily represent the official position of the U.S. Department of Justice. Table of Contents i Table of Contents Section Page Executive Summary . .1 Chapter 1: Introduction . .3 Major Activities . .3 Project Description . .4 Time Line . .5 Chapter 2: The Meaning of Stalking . .7 Defining Stalking . .7 State and Federal Anti-Stalking Laws . .7 Prevalence and Nature of Stalking . .8 Stalking Behaviors . .10 Stalkers and Stalker Classifications . .10 Impact of Stalking on Victims . .10 Chapter 3: Community Policing, Problem-Solving, and Stalking Response . .13 The Challenges of Policing Stalking . .13 Stalking and Community Policing . .14 Translating Theory into Practice . .16 Community Involvement . .16 Examples of Community Involvement in Anti-Stalking Initiatives . .19 Police Leadership and Action . .21 Community Policing and Stalking: Potential Rewards . .22 Chapter 4: A Model Stalking Protocol . .23 Introduction. 23 Purpose. 23 Policy . 23 Definitions . 24 Procedures . 28 Chapter 5: Reflections . .59 The Philadelphia Story . .59 Why Philadelphia? . .59 Getting Started . .60 Building the Team . .61 Training . .63 Keys to Success . .70 Recommendations . .73 ii Problem-Oriented Policing: Reflections on the First 20 Years Appendix I: Summary of Evaluation of the Implementation in Philadelphia . .75 Appendix II: Principal Findings and Recommendations: Adapting and Implementing the Model Stalking Protocol .