Vulnerability Disclosure Best Practice¹ Helps Make This Happen
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DFA INVESTMENT DIMENSIONS GROUP INC Form NPORT-P Filed
SECURITIES AND EXCHANGE COMMISSION FORM NPORT-P Filing Date: 2020-09-29 | Period of Report: 2020-07-31 SEC Accession No. 0001752724-20-200730 (HTML Version on secdatabase.com) FILER DFA INVESTMENT DIMENSIONS GROUP INC Mailing Address Business Address 6300 BEE CAVE ROAD 6300 BEE CAVE ROAD CIK:355437| IRS No.: 363129984 | State of Incorp.:MD | Fiscal Year End: 1031 BUILDING ONE BUILDING ONE Type: NPORT-P | Act: 40 | File No.: 811-03258 | Film No.: 201208198 AUSTIN TX 78746 AUSTIN TX 78746 (512) 306-7400 Copyright © 2020 www.secdatabase.com. All Rights Reserved. Please Consider the Environment Before Printing This Document DFA INVESTMENT DIMENSIONS GROUP INC. FORM N-Q REPORT July 31, 2020 (UNAUDITED) Table of Contents DEFINITIONS OF ABBREVIATIONS AND FOOTNOTES Emerging Markets Portfolio Emerging Markets Small Cap Portfolio Emerging Markets Value Portfolio Emerging Markets Core Equity Portfolio U.S. Large Cap Equity Portfolio DFA Commodity Strategy Portfolio DFA One-Year Fixed Income Portfolio DFA Two-Year Global Fixed Income Portfolio DFA Selectively Hedged Global Fixed Income Portfolio DFA Short-Term Government Portfolio DFA Five-Year Global Fixed Income Portfolio DFA World ex U.S. Government Fixed Income Portfolio DFA Intermediate Government Fixed Income Portfolio DFA Short-Term Extended Quality Portfolio DFA Intermediate-Term Extended Quality Portfolio DFA Targeted Credit Portfolio DFA Investment Grade Portfolio DFA Inflation-Protected Securities Portfolio DFA Short-Term Municipal Bond Portfolio DFA Intermediate-Term Municipal Bond Portfolio -

Blancco Erasure Sw 4.10 Hardware Support
BLANCCO ERASURE SW 4.10 HARDWARE SUPPORT Blancco Ltd Länsikatu 15 FIN-80110 JOENSUU, FINLAND [email protected] Tel. +358-207-433-850 [email protected] Tel. +358-207-433-860 Fax +358-207-433-859 PAGE 1/74 Blancco Erasure SW v4.10 hardware support 30/06/2009 TABLE OF CONTENTS Mass storage controllers ....................................................................................................10 SCSI ......................................................................................................................................10 Adaptec .......................................................................................................................... 10 Advanced Micro Devices [AMD] ..................................................................................... 12 Advanced System Products, Inc..................................................................................... 12 Areca Technology Corp. .................................................................................................12 Artop Electronic Corp......................................................................................................12 BusLogic......................................................................................................................... 12 DTC Technology Corp. ...................................................................................................12 Digital Equipment Corporation ........................................................................................ 12 Future Domain Corp. -

Bluepoint Price List
file:///D|/eshot/2009/week 07/friday/faxshot/faxhtml/faxshot.html bluepoint price list Valid to Friday 27/03/09 Sales: 0870 121 8001 [email protected] Acer Extensa 5230-571G16Mn 15.4" Wide Celeron £ 272.50 Netgear 54G VPN/Fwall ADSL Modem/Router £ 41.50 Mustek PowerMust 424 400VA Line Interactive UPS £ 33.50 USB Brother DCP-350C Multifunction Colour Inkjet £ 36.25 Printer 2" A4 Storage Products CPUs Cases Crucial Gizmo 1GB USB 2.0 Flash Drive 3.75 Akasa AK-675 Intel 478-pin P4 3.4GHz Pre 3.90 Akasa 50x10mm 12V 3 Pin, 1Ball 1 Sleeve 3.19 Kingston Data Traveler USB flash drive 2.95 Akasa Socket 604 CPU Cooler 14.85 Akasa Copper RAM Sink with ShinEtsu for 5.00 Transcend 2GB JetFlash V30 with neckstra 4.15 Akasa AK-875 AMD Cooler Fan for Skt AM2 15.10 Midi Tower Computer Case without PSU 6.55 Kingston 2GB DataTraveler 100 USB2.0 Fla 4.17 AMD Sempron 3000+ 1.8 GHz Processor 17.50 Akasa PAX.mate Noise reduction matting 5.75 Kingston 2GB USB flash drive 4.95 Intel Celeron 420 1.6GHz Processor Socke 20.35 C200 Micro ATX Case USB 2.0 Audio+MIC Po 8.95 2.0GB USB 2.0 Flash Drive 4.81 AMD Sempron LE-1250 2.20GHz 512KB L2 800 23.25 FSC-303 Midi ATX Tower Case 8.45 Kingston 4 GB Data Traveler USB Flash 6.95 Intel Celeron D 2.8GHz 533FSB LGA775 Rtl 22.75 400w LK Mini Tower Black/Silver Snd/USB 13.35 Transcend 4GB JetFlash V30 USB 2.0 6.45 Intel Celeron D 352 3.2 GHz CPU - LGA775 26.35 Trust LE-MD 350W Black Midi Tower Case 14.95 Transcend StoreJet 2.5" ID Hard Disk Enc 6.95 Intel Celeron 430 1.8GHz Processor Socke 26.50 Q-Tec L-MD 350W MIDI Tower -
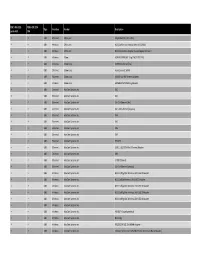
FDE 5.0.0.6123 Patch 4 U1 FDE 6.0.0.1514 GM Type Interface Vendor Description USB Ethernet 2Wire, Inc. Mega 2560 R3
FDE 5.0.0.6123 FDE 6.0.0.1514 Type Interface Vendor Description patch 4 U1 GM USB Ethernet 2Wire, Inc. Mega 2560 R3 (CDC ACM) USB Wireless 2Wire, Inc. 802.11g Wireless Adapter [Intersil ISL3886] USB Wireless 2Wire, Inc. 802.11b Wireless Adapter [Lucent/Agere Hermes I] USB Wireless 3Com 3CRUSB10075 802.11bg [ZyDAS ZD1211] USB Ethernet 3Com Corp. 3C19250 Ethernet [klsi] USB Ethernet 3Com Corp. HomeConnect 3C460 USB Ethernet 3Com Corp. 3C460B 10/100 Ethernet Adapter USB Wireless 3Com Corp. 3CRWE254G72 802.11g Adapter USB Ethernet AboCom Systems Inc XX1 USB Ethernet AboCom Systems Inc XX2 USB Ethernet AboCom Systems Inc DU‐E10 Ethernet [klsi] USB Ethernet AboCom Systems Inc DU‐E100 Ethernet [pegasus] USB Ethernet AboCom Systems Inc XX4 USB Ethernet AboCom Systems Inc XX5 USB Ethernet AboCom Systems Inc XX6 USB Ethernet AboCom Systems Inc XX7 USB Ethernet AboCom Systems Inc RTL8151 USB Ethernet AboCom Systems Inc USB 1.1 10/100M Fast Ethernet Adapter USB Ethernet AboCom Systems Inc XX9 USB Ethernet AboCom Systems Inc UF200 Ethernet USB Ethernet AboCom Systems Inc DU‐E10 Ethernet [pegasus] USB Wireless AboCom Systems Inc 802.11n/b/g Mini Wireless LAN USB2.0 Adapter USB Wireless AboCom Systems Inc 802.11n/b/g Wireless LAN USB2.0 Adapter USB Wireless AboCom Systems Inc 802.11n/b/g Mini Wireless LAN USB2.0 Adapter USB Wireless AboCom Systems Inc 802.11n/b/g Mini Wireless LAN USB2.0 Adapter USB Wireless AboCom Systems Inc 802.11n/b/g Mini Wireless LAN USB2.0 Adapter USB Wireless AboCom Systems Inc USB Wireless AboCom Systems Inc ASM1074 SuperSpeed -

Insight Manufacturers, Publishers and Suppliers by Product Category
Manufacturers, Publishers and Suppliers by Product Category 2/15/2021 10/100 Hubs & Switch ASANTE TECHNOLOGIES CHECKPOINT SYSTEMS, INC. DYNEX PRODUCTS HAWKING TECHNOLOGY MILESTONE SYSTEMS A/S ASUS CIENA EATON HEWLETT PACKARD ENTERPRISE 1VISION SOFTWARE ATEN TECHNOLOGY CISCO PRESS EDGECORE HIKVISION DIGITAL TECHNOLOGY CO. LT 3COM ATLAS SOUND CISCO SYSTEMS EDGEWATER NETWORKS INC Hirschmann 4XEM CORP. ATLONA CITRIX EDIMAX HITACHI AB DISTRIBUTING AUDIOCODES, INC. CLEAR CUBE EKTRON HITACHI DATA SYSTEMS ABLENET INC AUDIOVOX CNET TECHNOLOGY EMTEC HOWARD MEDICAL ACCELL AUTOMAP CODE GREEN NETWORKS ENDACE USA HP ACCELLION AUTOMATION INTEGRATED LLC CODI INC ENET COMPONENTS HP INC ACTI CORPORATION AVAGOTECH TECHNOLOGIES COMMAND COMMUNICATIONS ENET SOLUTIONS INC HYPERCOM ADAPTEC AVAYA COMMUNICATION DEVICES INC. ENGENIUS IBM ADC TELECOMMUNICATIONS AVOCENT‐EMERSON COMNET ENTERASYS NETWORKS IMC NETWORKS ADDERTECHNOLOGY AXIOM MEMORY COMPREHENSIVE CABLE EQUINOX SYSTEMS IMS‐DELL ADDON NETWORKS AXIS COMMUNICATIONS COMPU‐CALL, INC ETHERWAN INFOCUS ADDON STORE AZIO CORPORATION COMPUTER EXCHANGE LTD EVGA.COM INGRAM BOOKS ADESSO B & B ELECTRONICS COMPUTERLINKS EXABLAZE INGRAM MICRO ADTRAN B&H PHOTO‐VIDEO COMTROL EXACQ TECHNOLOGIES INC INNOVATIVE ELECTRONIC DESIGNS ADVANTECH AUTOMATION CORP. BASF CONNECTGEAR EXTREME NETWORKS INOGENI ADVANTECH CO LTD BELDEN CONNECTPRO EXTRON INSIGHT AEROHIVE NETWORKS BELKIN COMPONENTS COOLGEAR F5 NETWORKS INSIGNIA ALCATEL BEMATECH CP TECHNOLOGIES FIRESCOPE INTEL ALCATEL LUCENT BENFEI CRADLEPOINT, INC. FORCE10 NETWORKS, INC INTELIX -

Vista Procedure
Qualified Vendors List – Devices 1. Power Supplies Model ipower90 500W AcBel R88 PC7063 700W Aero Cool STRIKE-X 600W EA-500D 500W EA-650 EarthWatts Green 650W Antec EDG750 750W HCP-1300 1300W TP-750C 750W AYWUN A1-550-ELITE 550W BQT L7-530W Be quiet BQ L8-500W BitFenix FURY 650G 650W BUBALUS PG800AAA 700W MPZ-C001-AFBAT 1200W RS-350-PSAR-I3 350W CoolerMaster RS-450-AMAA-B1 450W RS-750-AFBA-G1 750W RS-850-AFBA-G1 850W 75-002019 (CX750M) 750W AX1500i 75-001971 1500W CS850M 75-010929 850W CX450M 450W RM750-RPS0019 750W Corsair RPS0007 (RM650i) 650W RPS0017(RM850X) 850W RPS0018(RM1000X) 1000W SF450 450W SF600 600W Vengeance 550M Cougar GX-1050 1050W D.HIGH DHP-200KGH-80P 1000W ERV1200EWT-G 1200W EnerMAX ERX730AWT 730W ETL450AWT-M 450W 220-P2-1200-X1 1200W EVGA SuperNova-750-G2 750W HydroX-450 450W PT-650M 650W FSP RAIDER-II 450W RAIDER 650W Huntkey WD600 600W OCZ OCZ-FTY750W 750W Power Man IP-S450HQ7-0 450W HIVE-850S 850W Rosewill PHOTON-1200 1200W Copyright 2016 ASUSTeK Computer Inc. PAGE 1 STRIX Z270F GAMING S12 II SS-330GB 330W SS-1200XP3 Active PFC F3 1200W Seasonic SS-400FL 400W SSR-450RM Active PFC F3 450W PAT-800W Seventeam ST-550P-AD 550W SST-60F-P 600W Silverstone SST-ST85F-GS 850W Super Flower SF-1000F14MP 1000W Smart DPS G 650 650W Toughpower TPX775 775W Thermaltake TPD-1200M 1200W TPG-0850D 850W ZUMAX ZU-500G-JP 500W 2. Hard Drives 2.1. HDD Devices Type Model H31K40003254SA HGST HDN726060ALE610 Seagate ST500DM002 Seagate ST6000NM0024 Seagate Seagate ST2000NX0243 Seagate ST1000NX0303 Seagate ST8000AS0002 WD6001FZWX WD60PURX SATA 6G WD60EZRX WD5000AAKX WD5000AZLX WD10PURX WD WD20PURX WD10J31X WD1002FAEX WD1003FZEX WD2003FZEX WD60EFRX SATA 3G Hitachi HDS721050CLA362 Copyright 2016 ASUSTeK Computer Inc. -

All Things Considered: an Analysis of Iot Devices on Home Networks
All Things Considered: An Analysis of IoT Devices on Home Networks Deepak Kumar, University of Illinois at Urbana-Champaign; Kelly Shen and Benton Case, Stanford University; Deepali Garg, Galina Alperovich, Dmitry Kuznetsov, and Rajarshi Gupta, Avast Software s.r.o.; Zakir Durumeric, Stanford University https://www.usenix.org/conference/usenixsecurity19/presentation/kumar-deepak This paper is included in the Proceedings of the 28th USENIX Security Symposium. August 14–16, 2019 • Santa Clara, CA, USA 978-1-939133-06-9 Open access to the Proceedings of the 28th USENIX Security Symposium is sponsored by USENIX. All Things Considered: An Analysis of IoT Devices on Home Networks Deepak Kumar‡ Kelly Shen† Benton Case† Deepali Garg/ Galina Alperovich/ Dmitry Kuznetsov/ Rajarshi Gupta/ Zakir Durumeric† †Stanford University /Avast Software ‡University of Illinois Urbana-Champaign Abstract vulnerabilities. Leveraging data collected from user-initiated network scans in 16M households that have agreed to share In this paper, we provide the first large-scale empirical anal- data for research and development purposes, we describe the ysis of IoT devices in real-world homes by leveraging data current landscape of IoT devices and their security posture. collected from user-initiated network scans of 83M devices IoT devices are widespread. More than half of households in 16M households. We find that IoT adoption is widespread: have at least one IoT device in three global regions and in on several continents, more than half of households already North America more than 70% of homes have a network- have at least one IoT device. Device types and manufac- connected device. Media devices like smart televisions are turer popularity vary dramatically across regions. -

Company Vendor ID (Decimal Format) (AVL) Ditest Fahrzeugdiagnose Gmbh 4621 @Pos.Com 3765 0XF8 Limited 10737 1MORE INC
Vendor ID Company (Decimal Format) (AVL) DiTEST Fahrzeugdiagnose GmbH 4621 @pos.com 3765 0XF8 Limited 10737 1MORE INC. 12048 360fly, Inc. 11161 3C TEK CORP. 9397 3D Imaging & Simulations Corp. (3DISC) 11190 3D Systems Corporation 10632 3DRUDDER 11770 3eYamaichi Electronics Co., Ltd. 8709 3M Cogent, Inc. 7717 3M Scott 8463 3T B.V. 11721 4iiii Innovations Inc. 10009 4Links Limited 10728 4MOD Technology 10244 64seconds, Inc. 12215 77 Elektronika Kft. 11175 89 North, Inc. 12070 Shenzhen 8Bitdo Tech Co., Ltd. 11720 90meter Solutions, Inc. 12086 A‐FOUR TECH CO., LTD. 2522 A‐One Co., Ltd. 10116 A‐Tec Subsystem, Inc. 2164 A‐VEKT K.K. 11459 A. Eberle GmbH & Co. KG 6910 a.tron3d GmbH 9965 A&T Corporation 11849 Aaronia AG 12146 abatec group AG 10371 ABB India Limited 11250 ABILITY ENTERPRISE CO., LTD. 5145 Abionic SA 12412 AbleNet Inc. 8262 Ableton AG 10626 ABOV Semiconductor Co., Ltd. 6697 Absolute USA 10972 AcBel Polytech Inc. 12335 Access Network Technology Limited 10568 ACCUCOMM, INC. 10219 Accumetrics Associates, Inc. 10392 Accusys, Inc. 5055 Ace Karaoke Corp. 8799 ACELLA 8758 Acer, Inc. 1282 Aces Electronics Co., Ltd. 7347 Aclima Inc. 10273 ACON, Advanced‐Connectek, Inc. 1314 Acoustic Arc Technology Holding Limited 12353 ACR Braendli & Voegeli AG 11152 Acromag Inc. 9855 Acroname Inc. 9471 Action Industries (M) SDN BHD 11715 Action Star Technology Co., Ltd. 2101 Actions Microelectronics Co., Ltd. 7649 Actions Semiconductor Co., Ltd. 4310 Active Mind Technology 10505 Qorvo, Inc 11744 Activision 5168 Acute Technology Inc. 10876 Adam Tech 5437 Adapt‐IP Company 10990 Adaptertek Technology Co., Ltd. 11329 ADATA Technology Co., Ltd. -

Emerging Markets Small Cap Portfolio-Institutional Class As of March 31, 2021 (Updated Monthly) Source: State Street Holdings Are Subject to Change
Emerging Markets Small Cap Portfolio-Institutional Class As of March 31, 2021 (Updated Monthly) Source: State Street Holdings are subject to change. The information below represents the portfolio's holdings (excluding cash and cash equivalents) as of the date indicated, and may not be representative of the current or future investments of the portfolio. The information below should not be relied upon by the reader as research or investment advice regarding any security. This listing of portfolio holdings is for informational purposes only and should not be deemed a recommendation to buy the securities. The holdings information below does not constitute an offer to sell or a solicitation of an offer to buy any security. The holdings information has not been audited. By viewing this listing of portfolio holdings, you are agreeing to not redistribute the information and to not misuse this information to the detriment of portfolio shareholders. Misuse of this information includes, but is not limited to, (i) purchasing or selling any securities listed in the portfolio holdings solely in reliance upon this information; (ii) trading against any of the portfolios or (iii) knowingly engaging in any trading practices that are damaging to Dimensional or one of the portfolios. Investors should consider the portfolio's investment objectives, risks, and charges and expenses, which are contained in the Prospectus. Investors should read it carefully before investing. This fund operates as a feeder fund in a master-feeder structure and the holdings listed below are the investment holdings of the corresponding master fund. Your use of this website signifies that you agree to follow and be bound by the terms and conditions of use in the Legal Notices. -

Symbol Name 1563.TW Superalloy Industrial Co Ltd 3138.TW Auden
Symbol Name 1563.TW SuperAlloy Industrial Co Ltd 3138.TW Auden Techno 3481.TW Innolux Corp 2409.TW AU Optronics 2303.TW United Microelectronics Corporation 2448.TW Epistar Corp 2368.TW Gold Circuit Electronics Ltd 2337.TW Macronix International Co Ltd 2599.TW Le Young Construction Co Ltd 2237.TW RAC Electric Vehicles 2730.TW Miramar Hospitality Co Ltd 9919.TW Kang Na Hsiung Enterprise Co Ltd 2241.TW Amulaire Thermal Technology 2891.TW CTBC Financial Holding Co Ltd 6251.TW Dynamic Electronics Co Ltd 2888.TW Shin Kong Financial Holding Co Ltd 2330.TW Taiwan Semicon 2327.TW Yageo Corp 2492.TW Walsin Technology Corp 2892.TW First Financial Holding Co Ltd 2312.TW Kinpo Electronics Inc 2721.TW Kai Chieh International Investment Ltd 2344.TW Winbond Electronics Corp 3168.TW Data Image 2883.TW China Development Financial Holding Corp 2317.TW Hon Hai Precision Industry Co Ltd 4142.TW Adimmune Corp 2313.TW Compeq Manufacturing Co Ltd 3037.TW Unimicron Technology Corp 2884.TW E.SUN Financial Holding Co Ltd 6116.TW Hannstar Display Corp 1269.TW Kanpai Co Ltd 2885.TW Yuanta Financial Holdings Co Ltd 2886.TW Mega Financial Holding Co Ltd 1314.TW China Petrochemical Development Corp 6176.TW Radiant Opto-Electronics Corp 2741.TW Renjie Oldsichuan Catering Management Consult 2363.TW Silicon Integrated Systems Corp 3545.TW FocalTech Systems Co Ltd 2449.TW King Yuan Electronics Co Ltd 2002.TW China Steel Corp 2618.TW Eva Airways Corp 3017.TW Asia Vital Components Co Ltd 2887.TW Taishin Financial Holding Co Ltd 2834.TW Taiwan Business Bank 5880.TW Taiwan Cooperative -

Vista Procedure
Qualified Vendors List – Devices 1. USB Storage External Enclosures Type Model USB 3.0 PQI Air Bank 1TB SinapisTek M.2 SSD 128GB ADATA SE730 250GB Neutrino Bridge AKiTiO NT2 U3.1 APACER AS720-AP120GAS720 CSS25U31BK Century CROSU31S CFD GW2.5FST-SU3.1 M2 CyberSlim S1-USB3.1 HD-328U3SMB Digifusion USB 3.1 HD-M2U31 M.2 SSD GODO GD25702 HighPoint RocketStor 3122B HORNETTEK HT-219AP3 J2C REMOVABLE HDD Sunrich U-1040 SUPERTALENT PORTABLE SSD 512GB Thunderwing TW-SN802 UNITEK Y-3605 UPTECH EHE207 Vantec NST-270A31 ASUS Wireless Duo 500GB Wifi PQI Air Bank 1TB USB Pen Drives Type Model Kingston HSX3 128GB USB 3.0 PNY V1 TURBO 64GB SUPERTALENT EXPRESS RC4 128GB USB Hubs Type Model Amazon USBN 3.0 10 port HUB USB 3.0 SIIG JU-H40512-S2 Copyright 2017 ASUSTeK Computer Inc. PAGE 1 Devices 2. Audio Audio Decoder Type Model SPDIF PIONEER VSX-1020-K Earphone Devices Type Model Line Out Audio-technica Audio-technica ATH-XS7 BT Sony Sony -Bluetooth Wireless DR-BT200NM Microphone Devices Type Model MIC In Microsoft LX-2000 Sound Adapters Type Model Logitech H340 USB2.0 SOMIC G909 Speaker Type Model Line out Logitech Logitech X530 Copyright 2017 ASUSTeK Computer Inc. PAGE 2 Devices 3. Ethernet 100 BaseTx Networking Cards Type Model USB 2.0 Xiaomi USB2.0 to RJ-45 LAN Card(小米) 1000 BaseTx Networking Cards Type Model USB 3.0 BROWAY BW-L1074A Networking Hubs/Switchs/Routers Type Model Home Plug ZyXEL PLA-5456 Switch TOTO-Link S505G Wireless Ethernet Adapters Type Model USB3.0 ASUS USB-AC68 (AC1900) Wireless LAN Access Point Type Model Buffalo WZR-D1800H AP DrayTek Vigor2110n Copyright 2017 ASUSTeK Computer Inc. -

72 Appendix A: Sample Companies (258 Companies from 20 Industries)
The Impact of SFAS No.35 Application on the Listed Firms’ Stock Performance in Taiwan Appendix A: Sample Companies (258 companies from 20 Industries) Cement: 7 samples 1416 Kwong Fong Ind. Corp. 1716 Yung Shin Pharmaceutical Industrial Co. Code Company Name 1418 Tong Hwa Synthetic Fiber Co., Ltd. 1726 Yung Chi Paint & Varnish Mfg. Co., Ltd. 1101 Taiwan Cement Corp. 1419 Shinkong Spinning Co., Ltd. 1729 Pihsiang Machinery Mfg. Co., Ltd. 1102 Asia Cement Corp. 1434 Formosa Taffeta Co., Ltd. 1730 Farcent Enterprise Co., Ltd. 1103 Chia Hsin Cement Corp. 1440 Tainan Spinning Co., Ltd. 1731 Maywufa Co., Ltd 1104 Universal Cement Corporation 1441 Tah Tong Textile Co., Ltd. 1736 Johnson Health Tech. Co., Ltd. 1108 Lucky Cement Corporation 1446 Hong Ho Precision Textile Co., Ltd. 1737 Taiyen Biotech Co., Ltd. 1109 Hsing Ta Cement Co., Ltd. 1451 Nien Hsing Textile Co., Ltd. Class, Ceramics: 3 samples 1110 Southeast Cement Corp. 1455 Zig Sheng Industrial Co., Ltd. Code Company Name Food: 10 samples 1457 Yi Jinn Ind. Co., Ltd. 1807 United Ceramics Co., Ltd. Code Company Name 1463 Chyang Sheng Dyeing & Finishing Co., Ltd 1809 China Glaze Co.,Ltd. 1201 Wei Chuan Foods Corporation 1466 Acelon Chemicals & Fiber Corp. 1810 Hocheng Corp. 1203 Ve Wong Corporation 1467 Tex-Ray Industrial Co., Ltd. Paper, Pulp: 3 samples 1216 Uni-President Enterprises Corp. 1472 Tri Ocean Textile Co., Ltd. Code Company Name 1218 Taisun Enterprise Co., Ltd. 1473 Tainan Enterprises Co., Ltd. 1904 Cheng Loong Corp. 1219 Fwusow Industry Co., Ltd. Electric, Machinery: 6 samples 1906 Pao Long International Co., Ltd. 1225 Formosa Oilseed Processing Co., Ltd.