All Things Considered: an Analysis of Iot Devices on Home Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Driver Download Instructions
Download Instructions Foxconn Tbga01 Driver 8/13/2015 For Direct driver download: http://www.semantic.gs/foxconn_tbga01_driver_download#secure_download Important Notice: Foxconn Tbga01 often causes problems with other unrelated drivers, practically corrupting them and making the PC and internet connection slower. When updating Foxconn Tbga01 it is best to check these drivers and have them also updated. Examples for Foxconn Tbga01 corrupting other drivers are abundant. Here is a typical scenario: Most Common Driver Constellation Found: Scan performed on 8/12/2015, Computer: Sony SVE15136CNS Outdated or Corrupted drivers:9/21 Updated Device/Driver Status Status Description By Scanner Motherboards Synaptics Synaptics SMBus Driver Corrupted By Foxconn Tbga01 Mice And Touchpads Logitech Logitech USB First/Pilot Mouse+ Corrupted By Foxconn Tbga01 Microsoft HID mouse Corrupted By Foxconn Tbga01 Logitech HID-compliant mouse Corrupted By Foxconn Tbga01 Usb Devices Cypress USB Storage Up To Date and Functioning Logitech Logitech Microphone (Fusion) Corrupted By Foxconn Tbga01 Sound Cards And Media Devices NVIDIA NVIDIA GeForce GTX 675M Up To Date and Functioning Broadcom Audio Bluetooth. Up To Date and Functioning Network Cards Ralink 802.11n Wireless LAN Card Corrupted By Foxconn Tbga01 Keyboards Microsoft HID Keyboard Up To Date and Functioning Hard Disk Controller Intel(R) ICH10D/DO SATA AHCI Controller Up To Date and Functioning Others NEC Generic CardBus-kontroller Outdated Research In Motion BlackBerry Outdated Intel Port racine express PCI -

Adagio for the Internet of Things Iot Penetration Testing and Security Analysis of a Smart Plug
DEGREE PROJECT IN COMPUTER ENGINEERING, FIRST CYCLE, 15 CREDITS STOCKHOLM, SWEDEN 2021 Adagio For The Internet Of Things IoT penetration testing and security analysis of a smart plug RAMAN SALIH KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE Adagio For The Internet Of Things IoT penetration testing and security analysis of a smart plug Raman Salih Supervisor: Pontus Johnson Examiner: Robert Lagerström Abstract— The emergence of the Internet of Things (IoT) Index Terms— Hacking; Wi-Fi; Threat model; IoT security; shows us that more and more devices will be connected to Smart plug the internet for all types of different purposes. One of those devices, the smart plug, have been rapidly deployed because I. INTRODUCTION of the ease it brings users into achieving home automation by turning their previous dumb devices smart by giving them As technology becomes smaller, faster, and more the means of controlling the devices remotely. These IoT connected over time it leads to more and more potential devices that gives the user control could however pose devices to join the internet and exchange data between serious security problems if their vulnerabilities were not carefully investigated and analyzed before we blindly themselves. Everything from coffee makers to blinds for your integrate them into our everyday life. In this paper, we do a windows may one day be connected to the internet and be threat model and subsequent penetration testing on a smart controlled remotely and dynamically. This category of plug system made by particular brand by exploiting its devices is known as the Internet of Things (IoT) and is set to singular communication protocol and we successfully launch reach 20.4 billion connected devices by 2020 according to a five attacks: a replay attack, a MCU tampering attack, a forecast made by Gartner 1 . -
![A Letter to the FCC [PDF]](https://docslib.b-cdn.net/cover/6009/a-letter-to-the-fcc-pdf-126009.webp)
A Letter to the FCC [PDF]
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, DC 20554 In the Matter of ) ) Amendment of Part 0, 1, 2, 15 and 18 of the ) ET Docket No. 15170 Commission’s Rules regarding Authorization ) Of Radio frequency Equipment ) ) Request for the Allowance of Optional ) RM11673 Electronic Labeling for Wireless Devices ) Summary The rules laid out in ET Docket No. 15170 should not go into effect as written. They would cause more harm than good and risk a significant overreach of the Commission’s authority. Specifically, the rules would limit the ability to upgrade or replace firmware in commercial, offtheshelf home or smallbusiness routers. This would damage the compliance, security, reliability and functionality of home and business networks. It would also restrict innovation and research into new networking technologies. We present an alternate proposal that better meets the goals of the FCC, not only ensuring the desired operation of the RF portion of a WiFi router within the mandated parameters, but also assisting in the FCC’s broader goals of increasing consumer choice, fostering competition, protecting infrastructure, and increasing resiliency to communication disruptions. If the Commission does not intend to prohibit the upgrade or replacement of firmware in WiFi devices, the undersigned would welcome a clear statement of that intent. Introduction We recommend the FCC pursue an alternative path to ensuring Radio Frequency (RF) compliance from WiFi equipment. We understand there are significant concerns regarding existing users of the WiFi spectrum, and a desire to avoid uncontrolled change. However, we most strenuously advise against prohibiting changes to firmware of devices containing radio components, and furthermore advise against allowing nonupdatable devices into the field. -
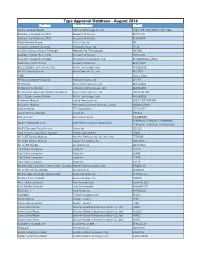
Type Approval Database - August 2014 Product Manufacturer Model Techno Mobile Phones Techno Technology Co
Type Approval Database - August 2014 Product Manufacturer Model Techno Mobile Phones Techno Technology Co. Ltd T331, T25, T501,T607, TV65, T28 Blackberry Smartphone 9520 Research In Motion RCP51UW Blackberry smartphone 9700 Research In Motion RCM71UW Fixed Wireless Phone I-Sirius Pte Ltd NA Personal Computer (Laptop) Panasonic Corp., Ltd CF-31 Unified Communications Exchange Network Eqt Technologies UX2000 BlackBerry SmartPhone 9700 Research In Motion RCN71UW Broadcom Bluetooth Module Broadcom Corporation, USA BCM92070MD_LENO Black Berry Smart Phone Research In Motion REM71UW 802.11a/b/g/n 2TR Combo Card Ralink Technology Corp RT3592BC8 WLAN Combo Module Micro-Star Int'l Co., Ltd MS-3871 PABX Aastra 2065 Personal Computer (Laptop) Panasonic Corp., Ltd CF-19T RF Module Barun Electronics Co., Ltd BM-LDS201 RF Remote Controller OHSUNG Electronics Co. Ltd. AKB732955 Blueconnect Handsfree Telephone Module Barun Electronics Co., Ltd CB2-BLUE11M 802.11b/g/n Combo Module Ralink Technology Corp RT5390BC8 Bluetooth Module Alpine Electronics Inc IAM2.1 BT PWB EU3 Bluetooth Module Panasonic Customer Services, Europe UGNZA/UGNZ4 Mobile Phone ZTE Corporation ZTE-G S217 Canon Wireless Module Canon Inc. WM223 WiFi Module LG Electronics Inc. LGSWF41 3160HMW, 3160NGW, 7260HMW, WLAN + Bluetooth Card Intel Mobile Communications SAS 7260NGW, 7260SDW, 6235ANNGW WLAN Compact Photo Printer Canon Inc. CD1112 Free To Air Terrestrial Set Top Box Vestel Electronik A.S T9300 Wi-Fi /BT Combo Module Hon Hai Precision Ind. Co. Ltd, India T77H506 Wi-Fi /BT Combo Module -

Parker Review
Ethnic Diversity Enriching Business Leadership An update report from The Parker Review Sir John Parker The Parker Review Committee 5 February 2020 Principal Sponsor Members of the Steering Committee Chair: Sir John Parker GBE, FREng Co-Chair: David Tyler Contents Members: Dr Doyin Atewologun Sanjay Bhandari Helen Mahy CBE Foreword by Sir John Parker 2 Sir Kenneth Olisa OBE Foreword by the Secretary of State 6 Trevor Phillips OBE Message from EY 8 Tom Shropshire Vision and Mission Statement 10 Yvonne Thompson CBE Professor Susan Vinnicombe CBE Current Profile of FTSE 350 Boards 14 Matthew Percival FRC/Cranfield Research on Ethnic Diversity Reporting 36 Arun Batra OBE Parker Review Recommendations 58 Bilal Raja Kirstie Wright Company Success Stories 62 Closing Word from Sir Jon Thompson 65 Observers Biographies 66 Sanu de Lima, Itiola Durojaiye, Katie Leinweber Appendix — The Directors’ Resource Toolkit 72 Department for Business, Energy & Industrial Strategy Thanks to our contributors during the year and to this report Oliver Cover Alex Diggins Neil Golborne Orla Pettigrew Sonam Patel Zaheer Ahmad MBE Rachel Sadka Simon Feeke Key advisors and contributors to this report: Simon Manterfield Dr Manjari Prashar Dr Fatima Tresh Latika Shah ® At the heart of our success lies the performance 2. Recognising the changes and growing talent of our many great companies, many of them listed pool of ethnically diverse candidates in our in the FTSE 100 and FTSE 250. There is no doubt home and overseas markets which will influence that one reason we have been able to punch recruitment patterns for years to come above our weight as a medium-sized country is the talent and inventiveness of our business leaders Whilst we have made great strides in bringing and our skilled people. -

Home Automation for Tinkerers
Home Automation for tinkerers Abílio Costa [email protected] Once upon a time... Where it all begun ● I had 3 wireless power sockets! (yay?) ● But I was using only one. Why? ○ Only a single remote: ■ How to use the other two in different rooms? ○ They were dumb. ¯\_(ツ)_/¯ ■ It would be nice to have one of them turn on/off on a schedule? Poor man’s solution ● An Arduino Nano + 433MHz RF transmitter + RF receiver. ○ Total cost: less than 5€. ○ Arduino sketch using the RC Switch library. ○ USB to a Raspberry Pi for the brains. ○ Script on the Raspberry Pi; exposing HTTP endpoints. ● My home was now so very smart! ○ Control each power socket through my phone. ○ Office desk power turns on automatically when I get home. ○ Bedroom lamp turned on automatically after the morning alarm. ○ I could buy more power sockets, even from other brands! ● The same idea can be used to interact with many other things: ○ Alarm sensors; Doorbells; Garage doors; etc. Next step: home automation software Why? ● Better management (my script wasn't going very far). ● Allow integrating other devices besides the power plugs. ● Make devices from different brands / protocols talk to each other. ● UI included! Home automation solutions ● Open-source software: ○ Home Assistant ○ Domoticz ○ OpenHAB ○ Pimatic ● Commercial hardware + software: ○ SmartThings ○ Vera ○ Xiaomi Home Assistant Home Assistant ● Good looking and customizable web UI (uses Google Polymer). ● Lightweight; extra functionality added with a plugin-like system. ● Very powerful automation engine (IFTTT on steroids). ● Autodiscovery: many devices will just show up without any config! ● Local: no cloud dependency! ● REST API available. -

How to Install / Use Custom Firmware (Or CFW) on Any Sony
www.markfixesstuff.co.uk Mark Fixes Stuff ‐ Sony PSP CFW guide V1.0 How to install / use Custom Firmware (or CFW) on any Sony PSP Scope: This document is intended to enable you to use Custom Firmware on you Playstation Portable console. It will work as a permanent install for PSP models in the 1000 and 2000 series, and will also function on later models as a loader that can be initiates at the start of each play session. Notes: ‐ I did not write this firmware! Credit for this goes to DJ Godman! ‐ This process is reversible, although as with any hack there is an unlikely chance you might brick your system. I cannot take responsibility for any issues you might encounter. ‐ I have use this process countless times with no problems. ‐ Although this process will allow the playing of pirated ISO files, I do not endorse nor condone piracy, and this process is described to allow you to use homebrew PSP games, emulators or your own ripped software that you own. Please read the entire document first and then you will be able to use it for reference as you hack your PSP! www.markfixesstuff.co.uk Mark Fixes Stuff ‐ Sony PSP CFW guide V1.0 Process: 1. Determine your current Official Firmware (OFW) Version. From the dashboard select Settings, then System Settings. Then System Information. You will see your PSP's official firmware version. Here it's 6.60. You will need at least 6.20!!! www.markfixesstuff.co.uk Mark Fixes Stuff ‐ Sony PSP CFW guide V1.0 2. -

Aspire 4736G/4736Z Series Service Guide
Aspire 4736G/4736Z Series Service Guide Service guide files and updates are available on the ACER/CSD web; for more information, please refer to http://csd.acer.com.tw PRINTED IN TAIWAN Revision History Please refer to the table below for the updates made to this service guide. Date Chapter Updates II Copyright Copyright © 2009 by Acer Incorporated. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written permission of Acer Incorporated. Disclaimer The information in this guide is subject to change without notice. Acer Incorporated makes no representations or warranties, either expressed or implied, with respect to the contents hereof and specifically disclaims any warranties of merchantability or fitness for any particular purpose. Any Acer Incorporated software described in this manual is sold or licensed as is. Should the programs prove defective following their purchase, the buyer (and not Acer Incorporated, its distributor, or its dealer) assumes the entire cost of all necessary servicing, repair, and any incidental or consequential damages resulting from any defect in the software. Acer is a registered trademark of Acer Corporation. Intel is a registered trademark of Intel Corporation. Pentium and Pentium II/III are trademarks of Intel Corporation. Other brand and product names are trademarks and/or registered trademarks of their respective holders. III Conventions The following conventions are used in this manual: SCREEN MESSAGES Denotes actual messages that appear on screen. -

GTC-ONE-Minute-Brief-117.Pdf
Equity | Currencies & Commodities | Corporate & Global Economic News | Economic Calendar 16 September 2020 Economic and political news Key indices The National Economic Development and Labour Council (Nedlac) As at 15 1 Day 1 D % WTD % MTD % Prev. month YTD % chaired by President Cyril Ramaphosa has agreed to an economic recovery plan for South Africa (SA) and a social compact to mobilise Sept 2020 Chg Chg Chg Chg % Chg Chg JSE All Share 56130.78 -196.27 -0.35 0.08 1.18 -0.44 -1.67 funding to address Eskom's financial crisis. (ZAR) The Matjhabeng Municipality in Free State has agreed to hand over 139 JSE Top 40 (ZAR) 51795.70 -181.12 -0.35 0.16 1.11 -0.28 1.93 farms worth about ZAR2.5bn belonging to the administrative region as FTSE 100 (GBP) 6105.54 79.29 1.32 1.22 2.38 1.12 -19.05 security on the ZAR3.4bn debt it owes to Eskom. DAX 30 (EUR) 13217.67 24.01 0.18 0.11 2.10 5.13 -0.24 According to the Automobile Association (AA), petrol price in SA will CAC 40 (EUR) 5067.93 16.05 0.32 0.67 2.44 3.42 -15.22 drop by between 26 cents and 36 cents per litre and diesel by 88 cents S&P 500 (USD) 3401.20 17.66 0.52 1.80 -2.83 7.01 5.27 per litre in October. Nasdaq 11190.32 133.67 1.21 3.10 -4.97 9.59 24.72 Democratic Alliance (DA) leader John Steenhuisen has requested Composite (USD) President Cyril Ramaphosa to end the curfew imposed in a bid to curb DJIA (USD) 27995.60 2.27 0.01 1.19 -1.53 7.57 -1.90 MSCI Emerging the spread of COVID-19, open all sectors of the South African economy, 1112.62 8.35 0.76 1.91 1.01 2.09 -0.18 and allow for international travel and reintroduce a normal school week. -

COMPLAINT for PATENT INFRINGEMENT Against Asustek Computer Inc., Asus Computer International, Inc., Atheros Communications, Inc
MOSAID Technologies Incorporated v. Dell, Inc. et al Doc. 1 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF TEXAS MARSHALL DIVISION MOSAID Technologies Incorporated, § § Plaintiff, § Case No. 2:11-cv-179 § v. § § Dell, Inc., § Jury Trial Demanded Research in Motion Corporation, § Research in Motion, Ltd., § Datalogic S.p.A., § Informatics Holdings, Inc., § Wasp Barcode Technologies, Ltd., § Venture Research, Inc., § Huawei Technologies Co., Ltd., § Huawei Technologies USA Inc., § Huawei Device USA Inc., § Futurewei Technologies, Inc., § Murata Electronics North America, Inc., § Murata Manufacturing Co., Ltd., § Murata Wireless Solutions, § Sychip, Inc., § Wistron Corporation, § Wistron LLC, § SMS Infocomm Corporation, § Wistron Infocomm (Texas) Corporation, § Wistron Infocomm Technology (America) § Corporation, § Wistron NeWeb Corporation, § ASUSTeK Computer Inc., § Asus Computer International, Inc., § Lexmark International, Inc., § Canon Inc., § Canon U.S.A., Inc., § Digi International Inc., § Intel Corporation, § Atheros Communications, Inc., § Marvell Semiconductor, Inc., § Realtek Semiconductor, § Ralink Technology Corporation, § CSR plc, § § Defendants. § Dallas 320181v1 Dockets.Justia.com ORIGINAL COMPLAINT FOR PATENT INFRINGEMENT Plaintiff MOSAID Technologies Incorporated (“MOSAID”) files this Original Complaint for patent infringement against Defendants Dell, Inc. (“Dell”); Research in Motion Corporation and Research in Motion, Ltd. (collectively, “RIM”); Datalogic S.p.A., Informatics Holdings, Inc., and Wasp Barcode -

Aspire 7738/7738G Series Aspire 7735/7735G/7735Z/7735ZG Series Aspire 7535/7535G/7235 Series Service Guide
Aspire 7738/7738G Series Aspire 7735/7735G/7735Z/7735ZG Series Aspire 7535/7535G/7235 Series Service Guide Service guide files and updates are available on the ACER/CSD web; for more information, please refer to http://csd.acer.com.tw PRINTED IN TAIWAN Revision History Please refer to the table below for the updates made on Aspire 7738/7738G, Aspire 7735/7735G/7735Z/ 7735ZG and Aspire 7535/7535G/7235 Series service guide. Date Chapter Updates II Copyright Copyright © 2009 by Acer Incorporated. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written permission of Acer Incorporated. Disclaimer The information in this guide is subject to change without notice. Acer Incorporated makes no representations or warranties, either expressed or implied, with respect to the contents hereof and specifically disclaims any warranties of merchantability or fitness for any particular purpose. Any Acer Incorporated software described in this manual is sold or licensed "as is". Should the programs prove defective following their purchase, the buyer (and not Acer Incorporated, its distributor, or its dealer) assumes the entire cost of all necessary servicing, repair, and any incidental or consequential damages resulting from any defect in the software. Acer is a registered trademark of Acer Corporation. Intel is a registered trademark of Intel Corporation. Other brand and product names are trademarks and/or registered trademarks of their respective holders. III Conventions The following conventions are used in this manual: SCREEN MESSAGES Denotes actual messages that appear on screen. -

Demystifying Internet of Things Security Successful Iot Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M
Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security: Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Chandler, AZ, USA Chandler, AZ, USA Ned Smith David M. Wheeler Beaverton, OR, USA Gilbert, AZ, USA ISBN-13 (pbk): 978-1-4842-2895-1 ISBN-13 (electronic): 978-1-4842-2896-8 https://doi.org/10.1007/978-1-4842-2896-8 Copyright © 2020 by The Editor(s) (if applicable) and The Author(s) This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Open Access This book is licensed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made. The images or other third party material in this book are included in the book’s Creative Commons license, unless indicated otherwise in a credit line to the material.