Volume 12, Number 4/5 October 1991
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Nextdimension State-Of-The-Art Color Capabilities
NeXT dimension is an accelerated, 32-bit color board that gives the NeXTcube NeXTdimension state-of-the-art color capabilities. NeXT dimension was designed for people who want the most advanced color PostScript system available. It's ideal for high-end publishing, graphics, video, and animation applications. The engineers at NeXT have integrated a 32-bit, true-color display function, a 64-bit RISC-based dedicated graphics coprocessor, video capture and display, and a high-performance JPEG compression coprocessor-all on one board. Its Intel i860 RISC-based microprocessor, operating at 33 MHz, runs full-color PostScript and has been optimized for our coprocessing environment, increas ing drawing speed eight to twelve times. This enables graphics applications to process images in near real time. The JPEG compression capabilities let you compress and play back still- and full-motion video from a hard disk drive. Features Benefits 32-blts-per-pixel NeXTd1mens1on offers 16.7 m Ilion colors .. color to choose from, so 1mages on the screen > have a photographic realism, with color, ( depth, and clanty Accelerated graph1cs The lntei1860 graphics accelerator makes work1ng w1th 32-blt color as fast as-and 1n some cases faster than-worktng on a standard NeXTcube monochrome system. � Video 1nput Lets you connect a NeXTdimens1on and output system to a VCR, laserd1sc player, VHS, S-VHS, H1-8, Beta, Camcorder, or still-v1deo camera w1thout requtring additional boards. Real-t1me Lets you take live v1deo, compress 1t, compress1on and and store 1t on hard d1sk-tn real t1me decompression With compression, you can store up to 60 t1mes more live video on a hard disk. -

Reseller Collateral Guide TM
Reseller Collateral Guide TM This guide was developed to keep you up-to-date on the current collateral and sales tools that are available to you. It will be updated on a regular basis and will be sent to you in NeXTNews. All unit costs include sales tax and shipping. Some of the collateral is pre- packaged (and is the minimum quantity you can order) with a bulk price per pack listed. To Order: NeXT’s corporate literature fullfillment house is The Hibbert Group. To order your collateral, either mail, fax, or e-mail an order form to: The Hibbert Group: NeXT Collateral Orders 1601 Park Avenue West Denver, CO 80216 NeXT Customer Service Rep: Kathy Sanford NeXT Service Center: 303-292-NeXT Fax Number: 303-292-0412 NeXT e-mail address: [email protected] For every order, please make sure you identify the desired method of ship- ment and the appropriate department and project numbers for billing pur- poses (for details, please see the Collateral Ordering section of your “Doing Business with NeXT” binder or “VAR Program Guidebook”). No orders will be processed without this information. If you have any questions, please refer to the Collateral Ordering section of your “Doing Business with NeXT” binder or “VAR Program Guidebook”, or contact Kathy Sanford at Hibbert. * indicates new item since last update to this guide. September 1992 Reseller Collateral Guide TM Collateral Brochures/Catalogs (packs of 25 each) Part #’s Price NeXT Product Brochure 1M4709 $11.25 Higher Ed Brochure 1H4568 $6.56 NeXTedge Brochure 1N4880 $8.44 Software & Peripherals -
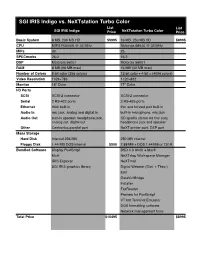
SGI IRIS Indigo Vs. Nextstation Turbo Color List List SGI IRIS Indigoprice Nextstation Turbo Color Price
SGI IRIS Indigo vs. NeXTstation Turbo Color List List SGI IRIS IndigoPrice NeXTstation Turbo Color Price Basic System 8 MB, 236 MB HD $9995 16 MB, 250 MB HD $8995 CPU MIPS R3000A @ 33 MHz Motorola 68040 @ 33 MHz MIPs 30 25 SPECmarks 26.0 16.3 DSP Motorola 56001 Motorola 56001 RAM 8 MB (96 MB max) 16 MB (32 MB max) Number of Colors 8-bit color (256 colors) 12-bit color + 4-bit ! (4096 colors) Video Resolution 1024×786 1120×832 Monitor 16” Color 17” Color I/O Ports SCSI SCSI-2 connector SCSI-2 connector Serial 2 RS-422 ports 2 RS-423 ports Ethernet thick built-in thin and twisted pair built-in Audio In mic jack, analog and digital in built-in microphone, mic jack Audio Out built-in speaker, headphone jack, CD-quality stereo via line outs, analog out, digital out headphone jack and speaker Other Centronics parallel port NeXT printer port, DSP port Mass Storage Hard Disk Internal 236 MB 250 MB internal Floppy Disk 1.44 MB DOS internal $500 2.88 MB + DOS 1.44 MB or 720 K Bundled Software Display PostScript BSD 4.3 UNIX + Mach Motif NeXTstep Workspace Manager IRIS Explorer NeXTmail SGI IRIS graphics library Digital Webster (Dict. + Thes.) Edit DataViz/Bridge Installer FaxReader Preview for PostScript VT100 Terminal Emulator DOS formatting software Network management tools Total Price $10495 $8995 SGI IRIS Indigo vs. NeXTcube Turbo/NeXTdimension List List SGI IRIS IndigoPrice NeXTdimension Turbo Price Base System 8 MB RAM, 436 MB hard drive $14,945 16 MB RAM, 400 MB hard drive $17115 CPU MIPS R3000A @ 33 MHz Motorola 68040 @ 33 MHz MIPs 30 25 -

Nextdimension System Fact Sheet SYSTEM POWER PORTS ADB: 1 Introduced: April 1991 Max
NeXTdimension System Fact Sheet SYSTEM POWER PORTS ADB: 1 Introduced: April 1991 Max. Watts: Video: Sun 13W3 Discontinued: Amps: Floppy: none Gestalt ID: BTU Per Hour: SCSI: DB-25 Form Factor: NeXT Cube Voltage Range: GeoPort Connectors: 1 Weight (lbs.): Freq'y Range (Hz): Ethernet: 10Base-T Dimensions (inches): 12 H x 12 W x 12 D Battery Type: Microphone Port Type: Soft Power Printer Speaker Codename: Monitor Power Outlet Headphone Oder Number: N1000A Modem KB Article #: Airport Remote Control Supported 3 NeXTbus slots 1 VIDEO Built-in Display: Maximum Color Bit-depth At: 512 640 640 640 800 832 1024 1152 1280 VRAM Speed: VRAM Needed: Video Configuration: x384 x400 x480 x8702 x600 x624 x768 x870 x1024 4 MB 1120x832 at 32-bits, 33 MHz 1 1-bit = Black & White; 2-bit = 4 colors; 4-bit = 16 colors; 8-bit = 256 colors; 16-bit = Thousands; 24-bit = Millions 2 The maximum color depth listed for 640x870 is 8-bit, reflecting the capabilities of the Apple 15" Portrait Display. Came with a 11120x832 17" color display with the standard Sun monitor connector. The cube could use a 32-bit video board for 16.7 million colors in Adobe's Display Postscript. LOGIC BOARD MEMORY Main Processor: 68040, 25 MHz Memory on Logic Board: 128 K PMMU: integrated Minimum RAM: 24 MB FPU: 25 MHz 68882 Maximum RAM: 64 MB Data Path: , RAM Slots: L1 Cache: Minimum RAM Speed: L2 Cache: RAM Sizes: Secondary Processor: Install in Groups of: Slots: Speech Recognition Supported Supported Macintosh System Software: SOFTWARE A/UX 1.0 NOS 1.11 ProDOS Addressing Modes: 32-bit ROM -

View 3.0 Releasenextstep.Ps.Gz As
NeXTstep Release 3.0: Strengthening NeXT's Object-Oriented Leadership January 1992 Object-oriented software systems qualify as the first revolution in desktop computing technology since the graphical user interface. While everyone in the industry talks about object-oriented programming, only one object-oriented system Ð NeXT Computer, Inc.'s NeXTstep Ð is shipping today. NeXTstep's object-oriented environment dramatically simplifies the development and delivery of custom and commercial applications, including revolutionary applications never before possible. NeXT created its combined graphical user interface (GUI) and application development environment specifically to speed the development of commercial, "shrink-wrapped" software applications for the NeXT platform. This strategy has worked as planned: More than 240 high-quality productivity applications are currently shipping. The company discovered, however, that corporate and government customers will not switch to NeXT computers simply for off-the-shelf application software, even if it is twice as good as what they currently use, but that large numbers of them have switched to NeXT for its unsurpassed environment for creating mission-critical custom applications. With NeXTstep, in-house programmers are quickly developing sophisticated applications specifically tailored to their company and industry Ð applications that provide a true competitive edge Ð up to 10 times faster than possible with other platforms, and thus with less investment. For example, many Wall Street financial organizations have embraced NeXT and NeXTstep as a competitive weapon in an industry where fast decisions and actions are fundamental to success. (Please refer to the document "Who Buys NeXT Computers?" for more information on specific NeXT customers.) The combination of quickly developed and widely deployed custom NeXTstep Release 3.0 backgrounder, page 2 applications, plus great off-the-shelf productivity applications running alongside the custom applications, provides NeXT's compelling advantage in commercial markets today. -

Apple Computer, Inc. Records M1007
http://oac.cdlib.org/findaid/ark:/13030/tf4t1nb0n3 No online items Guide to the Apple Computer, Inc. Records M1007 Department of Special Collections and University Archives 1998 Green Library 557 Escondido Mall Stanford 94305-6064 [email protected] URL: http://library.stanford.edu/spc Guide to the Apple Computer, Inc. M1007 1 Records M1007 Language of Material: English Contributing Institution: Department of Special Collections and University Archives Title: Apple Computer, Inc. Records creator: Apple Computer, Inc. Identifier/Call Number: M1007 Physical Description: 600 Linear Feet Date (inclusive): 1977-1998 Abstract: Collection contains organizational charts, annual reports, company directories, internal communications, engineering reports, design materials, press releases, manuals, public relations materials, human resource information, videotapes, audiotapes, software, hardware, and corporate memorabilia. Also includes information regarding the Board of Directors and their decisions. Physical Description: ca. 600 linear ft. Access Open for research; material must be requested at least 36 hours in advance of intended use. As per legal agreement, copies of audio-visual material are only available in the Special Collections reading room unless explicit written permission from the copyright holder is obtained. The Hardware Series is unavailable until processed. For further details please contact Stanford Special Collections ([email protected]). Conditions Governing Use While Special Collections is the owner of the physical and digital items, permission to examine collection materials is not an authorization to publish. These materials are made available for use in research, teaching, and private study. Any transmission or reproduction beyond that allowed by fair use requires permission from the owners of rights, heir(s) or assigns. -

Nextstation..Frame
NeXTSTATION NeXTSTATION TURBO NeXTstation Powered by the Motorola 68040, both the 25-megahertz NeXTstation™ and the computers combine 33-megahertz NeXTstation Turbo offer an unprecedented number of features at an affordable price. Each system features two new NeXT-designed VLSI chips, Motorola’s state-of-the-art 56001 Digital Signal Processor, as well as built-in networking capabilities. The result is a technology with class of workstations ideally suited for creating and deploying custom mission-critical an object-oriented applications and running world class productivity applications. operating and The NeXTstation Turbo includes 16 megabytes of main memory, which can be expanded development to an impressive 128 megabytes. A choice of either 250 or 400 megabytes of hard disk environment into storage space is available, both options coming preloaded with NeXT™ system software making NeXTstations productive right out of the box. Also included is a 2.88-megabyte, an easy-to-use, 3.5-inch floppy disk drive capable of reading and writing to 1.44 MB and 720 KB diskettes affordable in UNIX,® MS-DOS,® and 1.44 MB in Macintosh® formats. professional All NeXT computers were designed from the beginning to be part of a connected workstation. workplace. From the true multitasking capabilities of UNIX to the built-in, high- performance Ethernet—including twisted-pair and thin Ethernet—NeXTstations can be easily configured into any network, including IBM® PCs and compatibles, Sun® and Macintosh computers, and DEC® and IBM mainframes. FEATURES AND BENEFITS Motorola 68040 Combined central processing A highly integrated microprocessor design providing excellent computer (CPU), floating-point (FPU), and performance, high data transfer rate, and exceptional reliability. -

Writing Loadable Kernel Servers Next Developer's Library
Writing Loadable Kernel Servers NeXT Developer's Library NeXTstep Draw upon the library of software contained in NeXTstep to develop your applications. Integral to this development environment are the Application Kit and Display PostScript. Concepts A presentation of the principles that define NeXTstep, including user interface design, object-oriented programming, event handling, and other fundamentals. Reference, Volumes 1 and 2 Detailed, comprehensive descriptions of the NeXTstep Application Kit software. Sound, Music, and Signal Processing Let your application listen, talk, and sing by using the Sound Kit and the Music Kit. Behind these capabilities is the DSP56001 digital signal processor. Independent of sound and music, scientific applications can take advantage of the speed of the DSP. Concepts An examination of the design of the sound and music software, including chapters on the use of the DSP for other, nonaudio uses. Reference Detailed, comprehensive descriptions of each piece of the sound, music, and DSP software. ~ NeXT Development Tools A description of the tools used in developing a NeXT application, including the Edit application, the compiler and debugger, and some performance tools. ~ NeXT Operating System Software A description of NeXT's operating system, Mach. In addition, other low-level software is discussed. ~ Writing Loadable Kernel Servers How to write loadable kernel servers, such as device drivers and network protocols. ~ NeXT Technical Summaries Brief summaries of reference information related to NeXTstep, sound, music, and Mach, plus a glossary and indexes. ~ Supplemental Documentation Information about PostScript, RTF, and other file formats useful to application developers. Writing Loadable Kernel Servers We at NeXT Computer have tried to make the information contained in this manual as accurate and reliable as possible. -

Nexttm Hardware Service
• • NeXTTM Hardware Service • • We at NeXT Computer have tried to make the information contained in this manual as accurate and reliable as possible. Nevertheless, NeXT disclaims any warranty of any kind, whether express or implied, as to any matter whatsoever re lating to this manual, including without limitation the merchantability or fitness for any particular purpose. In no event shall NeXT be liable for any indirect, special, incidental,:or consequential damages arising out of purchase or use of this manual or the information contained berein. Copyright "1992 by NeXT Computer, Inc. All Rights Reserved. • NeXT,the NeXT logo, NeXTstation, NeXTdimension, NeXTmail, Digital Librarian, Digital Webster, Lip Service, MegaPixel Display, and Workspace Manager are trademarks of NeXT Computer, Inc. PostScript is a registered trade made of Adobe Systems Incorporated. UNIX is a registered trademark of AT&T. Helvetica and Ttmes are registered trademarks of Linotype AG and/or its subsidiaries. Wreath and Monogram is a registered trademark of Merriam-Web ster, Incorporated aod is used herein pursuant to license. WriteNow is a registered trademark ofT/Maker Co. All other trademarks mentioned belong to their respective owners. NeXT Computer, Inc., 900 Chesapeake Drive, Redwood City, CA 94063 Writing: Terry Wtlliams, Robin Goodwin, Eric Domejean illustrations: Nancy SerpieUo, Terry Williams, Eric Domejean Production Notes: This book was created electronically using FrameMaker, on the NeXT computer. Art was produced using Adobe lllustrator,TopDraw, -

Apple Confidential 2.0 the Definitive History of the World's Most Colorful
vi Reviewers love Apple Confidential “The Apple story itself is here in all its drama.” New York Times Book Review “An excellent textbook for Apple historians.” San Francisco Chronicle “Written with humor, respect, and care, it absolutely is a must-read for every Apple fan.” InfoWorld “Pretty much irresistible is the only way to describe this quirky, highly detailed and illustrated look at the computer maker’s history.” The Business Reader Review “The book is full of basic facts anyone will appreciate. But it’s also full of interesting extras that Apple fanatics should love.” Arizona Republic “I must warn you. This 268-page book is hard to put down for a MacHead like me, and probably you too.” MacNEWS “You’ll love this book. It’s a wealth of information.” AppleInsider “Rife with gems that will appeal to Apple fanatics and followers of the computer industry.” Amazon.com “Mr. Linzmayer has managed to deliver, within the confines of a single book, just about every juicy little tidbit that was ever leaked from the company.” MacTimes “The most entertaining book about Apple yet to be published.” Booklist i …and readers love it too! “Congratulations! You should be very proud. I picked up Apple Confidential and had a hard time putting it down. Obviously, you invested a ton of time in this. I hope it zooms off the shelves.” David Lubar, Nazareth, PA “I just read Apple Confidentialfrom cover to cover…you have written a great book!” Jason Whong, Rochester, NY “There are few books out there that reveal so much about Apple and in such a fun and entertaining manner. -

Macpro Magazine April 2011
1990 2000 2010 NeXTcube Power Mac Mac mini G4 Cube HISTORIEN OM Att utveckla med NeXTSTEP ● iPad 2: Det andra testet ● Macbook Pro 15" ● Synkronisering mellan iOS och iTunes ● Logitech Lapdesk Speaker ● Minimalisternas Kamp ● Hive Desktop NEXT ● Abbyy Business Card Reader ● Övervaka din Xserve RAID 1 MACPRO MAGAZINE April 2011 4 Ledare 7 Historien om NeXT 39 Att utveckla med NeXTSTEP 48 Mac OS X Server 10.6, del 2: Att lösa fildelningsproblem 54 Övervaka din Xserve RAID 59 Allt om synkronisering mellan iOS och iTunes 71 Sender Policy Framework Tester 77 iPad 2 – det andra testet 82 Macbook Pro 15” – Stor eller liten 86 Logitech Ultimate Ears 400vi 89 Trafiken 91 Logiteck Lapdesk Speaker 93 Minimalisternas Kamp 100 Abbyy Business Card Reader 103 Hive Desktop 107 bg5 – Aluminiumfodral för iPhone 109 Krönika 113 Retro: NeXT-propaganda 2 April 2011 6:e sedan start Chefredaktör & ansvarig utgivare Övriga medarbetare Joacim Melin Petri Stenberg, Johan Wanloo, Johan Strömqvist Formgivare Johan Brook Korrektur Olof Hennig Seniorreporter Peter Esse Kontakt Annonsering [email protected] [email protected] Pressreleaser, inbjudningar eller liknande [email protected] Macpro Magazine publiceras av Melin Ord och Media Macpro Magazine är en icke-politisk och icke-religiös fristående publikation. ISBN 978-91-633-7797-6 Copyright 2011. Melin Ord och Media. Made on a Mac. 3 Ledare Kopierade ideér tar inte Kopierade Kopierade produkterna framåt är Steve Jobs för några år sedan upptäckte ett förråd på Apple Nmed en samling modeller ur företagets historia gav han ordern: släng bort grejerna. Alltihop. Motiveringen? Inget företag mår bra av att titta bakåt, att vältra sig i sin historia och tro att det ska lösa några problem. -
Fabien Sanglard
GAME ENGINE BLACK BOOK DOOM FABIEN SANGLARD 1 Copyright In order to illustrate how the DOOM game engine works, a few screenshots, images, sprites, and textures belonging to and copyrighted by id Software are reproduced in this book. The following items are used under the "fair use" doctrine: 1. All in-game screenshots, title screen. 2. All in-game menu screenshots. 3. All 3D sequence textures. 4. All 3D sequence sprites. 5. All screenshots of DOOM. 6. DOOM name. Photographs with "ROME.RO" watermark belong to John Romero and are reproduced with his authorization. DOOM Survivor’s Strategies & Secrets essays are copyrighted by Jonathan Mendoza and reproduced with his authorization. 3 Acknowledgments Many people helped completing this book. Many thanks are due: To John Carmack, John Romero, and Dave Taylor for sharing their memories of DOOM development and answering my many questions. To people who kindly devoted time to the painful proofreading process, Aurelien Sanglard, Jim Leonard, Dave Taylor, Jonathan Dowland, Christopher Van Der Westhuizen, Eluan Miranda, Luciano Dadda, Mikhail Naganov, Leon Sodhi, Olivier Cahagne, Andrew Stine, and John Corrado. To Simon Howard, for not only proofreading but also sending pull requests to the git repo. His efforts saved countless hours at a time where the deadline was concernedly close. To Jim Leonard who once again volunteered his time and encyclopedic knowledge of audio hardware and software (the Roland section was heavily based on his articles). To Foone Turing who volunteered his fleet of 386s, 486s, and ISA/VLB VGA cards to ac- curately benchmark DOOM. To Andrew Stine, founder of doomworld.com, for sharing his encyclopedic knowledge of DOOM and putting me in touch with the right people.